Critical Vulnerability Patched in 301 Redirects – Easy Redirect Manager
Affected Plugin: 301 Redirects – Easy Redirect Manager
CVSS Score: 9.0 (Critical)
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:H
CVE ID: CVE-2019-19915
Affected Versions: <= 2.40
Patched Version: 2.45
On Friday December 13th, our Threat Intelligence team discovered vulnerabilities present in 301 Redirects – Easy Redirect Manager, a WordPress plugin installed on over 70,000 websites. These weaknesses allowed any authenticated user, even subscribers, to modify, delete, and inject redirect rules that could potentially result in a loss of site availability. We privately disclosed the issue to the plugin’s developer, who was incredibly quick to respond and release a patch.
Though this vulnerability required the attacker to be authenticated, numerous WordPress sites allow for registration as a subscriber. For these sites, exploitation of this vulnerability would be quite simple.
This is considered a critical security issue, and websites running 301 Redirects – Easy Redirect Manager 2.40 or below should be updated to version 2.45 immediately. On the same day we discovered the vulnerability, Wordfence Premium customers received a new firewall rule to protect against exploits; free users will receive the rule after thirty days, on January 12, 2020.
Unprotected AJAX Actions Gone Awry
301 Redirects – Easy Redirect Manager is a simple plugin used to set up 301 redirects on WordPress sites. In order to save new redirects and modify old redirects, the plugin registers several AJAX actions using a seemingly safe is_admin() function to prevent unauthorized access.
if (is_admin()) {
…
// Ajax funcs
add_action('wp_ajax_eps_redirect_get_new_entry', array($this, 'ajax_get_entry'));
add_action('wp_ajax_eps_redirect_delete_entry', array($this, 'ajax_eps_delete_entry'));
add_action('wp_ajax_eps_redirect_get_inline_edit_entry', array($this, 'ajax_get_inline_edit_entry'));
add_action('wp_ajax_eps_redirect_save', array($this, 'ajax_save_redirect'));
Trac: eps-301-redirects.php
However, is_admin() only checks to see if the “dashboard or the administration panel is attempting to be displayed.” As per the WordPress.org Codex, “this function does not verify whether the current user has permission to view the Dashboard or the administration panel.” In addition, the same goes for the admin-ajax function: it only verifies that the request is coming from the administration panel and does not verify any permissions.
Therefore, due to the lack of capability checks on the AJAX actions, any user authenticated as a subscriber or above can use these AJAX actions to delete redirect entries, create new redirects, and view the form to add or edit inline entries. Because many attackers compromise sites with the hopes of redirecting traffic to spammy or malware-infested sites, this is an attractive and easy method of exploiting a vulnerable site.
The unprotected AJAX actions are where the vulnerabilities begin; a deeper look found more problems.
Lack of Proper Input Validation
Investigating further, we found that the ID parameter, which is used to create an ID for new rules and identify existing rules, lacked any input validation or sanitization and was later reflected on the page. This led to a reflected XSS vulnerability that could not only be exploited on its own, but also in conjunction with a new redirect injection. Fortunately, the Wordfence firewall’s built-in XSS protection blocks this vulnerability for both our free and premium users.
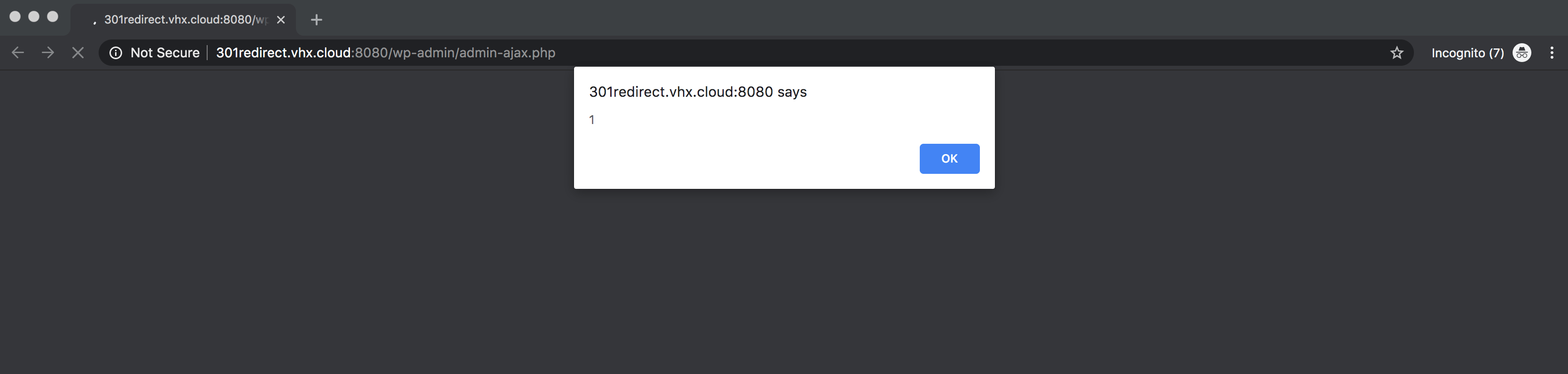
XSS being exploited in 301 Redirects – Easy Redirect Manager plugin using <BODY ONLOAD=alert(1)> payload.
Missing CSRF Protection
The vulnerable version of the plugin also failed to use a nonce for any of the AJAX actions that were used to modify and create new rules. This created a CSRF weakness that could be exploited if an attacker could not gain subscriber level privileges. In addition, the attack surface for CSRF to be exploited was much larger due to the lack of permissions checks on the AJAX actions. As such, any user with subscriber or above permissions could be targeted to exploit this vulnerability, creating a more worrisome issue.
The End Result
Each independent vulnerability was significant. As a group, the vulnerabilities in the 301 Redirects plugin created a significant risk to the WordPress site owner with a vulnerable version installed. An attacker exploiting these weaknesses could create havoc for site visitors who could have been redirected to malicious sites. These sites could have collected credentials via phishing pages or infected vulnerable computers with malware, amongst other things.
Even if a site did not have subscriber registration open, the CSRF vulnerability might allow a social engineering attack to succeed in injecting new redirects or deleting old ones.
If one exploit attempt failed, there was another exploit that could possibly succeed.
Disclosure Timeline
December 13th, 2019 – Initial private contact with developer and notification of security issue. Firewall rule is released to premium members.
December 14th, 2019 – Developer responds.
December 16th, 2019 – Full details sent to developer.
December 16th, 2019 – Developer acknowledges vulnerabilities and starts working on patches
December 17th, 2019 – Developer releases patch.
January 12th, 2020 – Free users receive firewall rule.
Conclusion
In today’s post, we detailed several vulnerabilities present in the 301 Redirects – Easy Redirect Manager plugin, that led to one very severe issue. Fortunately, the plugin developer was incredibly quick to respond and release a patch for the vulnerable endpoints. These flaws have been patched in version 2.45 and we urge users update to the latest version available as soon as possible.
Sites running Wordfence Premium have been protected from attacks against this vulnerability since December 13th, 2019. Sites running the free version of Wordfence will receive the firewall rule update on January 12th, 2020 and should update the 301 Redirects plugin immediately.


Comments
12:16 pm
Well said, i've been hacked this way a month ago, and already deleted the plugin.
6:33 pm
Does it also affect their sister plugin? https://wordpress.org/plugins/301-redirects/
8:07 am
Hi Jan!
These vulnerabilities do not affect their sister plugin, 301 Redirects, as far as we are aware.