6 Million Password Attacks in 16 Hours and How to Block Them
Last week in the President’s cyber security op-ed in the Wall Street Journal he implored Americans to move beyond simple passwords and to enable two factor authentication or cellphone sign-in.
One of the things we monitor at Wordfence is the number of brute force attacks on WordPress websites. Brute force attacks are password guessing attacks, where an attacker tries to sign in as you by guessing your password.
To give you an idea of the level of attacks in the wild, we gathered data on brute force attacks across the sites we protect within a 16 hour Window starting Sunday until Monday (yesterday) at 2pm Pacific time.
Here are the highlights. Remember, this is only over a 16 hour window which is relatively short.
During this time we saw a total of 6,611,909 attacks targeting 72,532 individual websites. We saw attacks during this time from 8,941 unique IP addresses and the average number of attacks per victim website was 6.26.
The total number of attacking IP’s was actually 55,391 but we only counted IP’s that generated more than 10 failed logins across all sites. That way we excluded accidental login failures.
So where are these attacks coming from. The results are not what you would expect. The table below shows the total number of attacks (brute force login attempts in this case) ordered by country:
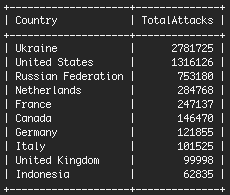
Brute Force Attacks by Country.
The Ukraine is the top offender, but there is a specific reason for this which we explain below. The United States is second. Our hypothesis is that this is where most data centers are based and therefore most compromised sites, from which attacks are launched, will be based in the USA.
You’ll notice that the Ukraine is at the top of the list. Over 86% of those attacks come from just two IP addresses at a Ukrainian hosting provider. These two IP’s generated 2.4 Million attacks between the two of them.
During just 16 hours, they targeted 37,454 unique victims.
The two attackers that we analyzed are based at a Ukrainian hosting provider. They caused their Ukrainian hosting provider to account for more attacks than the next 19 hosting providers, combined.
We currently aggregate attack information at a rate of 114 attacks per second. Analyzing data like this at Wordfence helps us understand the changing attack landscape and how to better protect our customers.
What can you do to protect yourself?
Firstly, make sure you’re running the free or premium version of Wordfence and that you have the “Wordfence security network” feature enabled. It is enabled out of the box in Wordfence. With this feature enabled, if you get a failed login from an IP address, Wordfence will contact our cloud services to find out if that IP is one of the attackers we know about (like the two above). If it is, it will immediately be blocked from signing in, protecting your site from a brute force attack. The attacker won’t even get the standard 3 or 5 tries before they are locked out.
Wordfence also provides login attempt limiting out of the box in the free and premium versions. WordPress does not do this by default, so make sure you have this enabled.
Next, as Obama suggests, enable cellphone sign-in for your WordPress website, also known as two factor authentication or 2FA. This feature is available in the Premium version of Wordfence and is easy to enable. You can learn more about cellphone sign-in on our documentation website.
Perform a Password Audit
Wordfence Premium gives you the ability to securely audit the strength of all your site member passwords, including your administrators. To launch this feature last year, we worked closely with our partners to build a supercomputer with over 40 Terraflops of processing power. That is faster than the fastest computer in the world in 2003.

Wordfence’s custom built password auditing hardware is pictured above. It is based in our data center in Lynnwood, Washington and uses very high performance GPU’s to audit the security of your passwords.
By performing a password audit with Wordfence, you can launch a simulated password cracking attack on all site member passwords including administrators. Wordfence will then provide a report of which accounts suffer from weak passwords.
Password Auditing is completely secure and uses a combination of hashing and public key cryptography to protect your data. Once you receive the results, Wordfence provides a way for you to notify users they have a weak password or to force a password change.
If you haven’t completed a password audit on your website, upgrade to Wordfence Premium and start an audit today.
Go Deep on Password Security
Password security is a big subject. To fully understand why strong passwords are important and how attackers target weak passwords, you need to gain an understanding of hashing, password salts and attack methods like rainbow tables, how salts work and why modern GPU’s give attackers a huge advantage.
As part of our free WordPress Security Learning Center, we have created a comprehensive lesson that explains all of this and much more, including emerging improvements in password algorithms. The lesson is designed to be a place that teachers and university professors can send their students to get a primer on password security and password authentication.
If you invest the time to read this lesson, you will come away with a complete understanding of many fundamental security concepts that you will use throughout your career as a systems administrator.
Be warned, we don’t pull any punches. So if you do decide to dive in, make sure you make yourself a cup of something warm and allocate at least an hour to read the entire lesson.
Once complete, you will have a well grounded understanding of password security, password authentication and modern attack techniques. We even throw in some number theory to help you understand what makes a password strong.
You can find the full lesson on Password Authentication and Password Cracking by clicking here.
As always, please share your thoughts below and thanks for being part of Wordfence and our community.

Comments
9:20 am
I noticed a higher than usual volume of attempted logins Monday morning for one of my clients sites which uses the free WordFence. As you stated the majority came from the Ukraine. There were about 30 attempts in an 8 hour window of time. I've since had our hosting company block all IPs from outside of the US and Canada. The timing of this article and the information contained within has been very valuable. Thanks for creating this plugin and for being so diligent in keeping WP sites protected!
9:32 am
Happy to help. We include country blocking in our Premium version FYI.
9:26 am
My logs show the attacks coming from the US amazon aws servers. Auto blocked and locked =)
Thanks, your plugin rocks!
Hey quick question in regards to cloudflare integration..
I have cloudflare hooked up to my site along with this wordfence plugin. Shouldnt cloudflare flag attacks like these before it actually reaches my site or am i missing something here?
9:30 am
I can't speak for cloudflare, but yeah it is surprising that they're not blocking brute force attacks on your site. As far as I know they basically tail logfiles from nginx and consolidate them on a central server. Then they parse those logs for attack signatures and block based on that. It all happens in virtually real-time. I'm just going on what their blog posts have said. So it's difficult to block stuff that is session based at the application layer if you're looking at individual HTTP requests - so perhaps they don't block brute force attacks? It'd be interesting to test this.
And yes, AWS is one of our top offenders, it's important to note that it's not Amazon's fault. Someone likely installed something vulnerable on those servers that got hacked and then they became an attack platform.
Mark.
8:00 am
We actually use the combination of Cloudflare and Wordfence for all our clients. The free version of Cloudflare doesn't have the web application firewall. What we do is setup two special page rules (you get 3 free rules) one on wp-login.* and one on wp-admin* with a rule set of: I'm under attack and browser security check. Across 30+ sites this has reduced the number of failed login attempts to around 5 a day.
1:04 pm
Thanks Mark for the insights!
Jamas, gonna setup those special page rules for my sites.. Never payed attentioned to that feature until ur comment. Thanks for tip!!
1:49 pm
It's extremely disappointing that Amazon Web Services (AWS) do not take these attacks seriously. We've sent hundreds of log details to them - showing their (probably free tier) servers are being used to attack our sites and all we get is a canned response email.
On a positive note - the WordFence plugin is installed on every site we set up. Your plugin is excellent.
Thank you
Mike
p.s. great content on your site too
1:58 pm
Thanks Mike.
9:36 am
You also should enable two factor authentication. On all WP sites I manage for my company 2FA is on and required. So good luck bots on brute forces because you need additional information besides just passwords that are really long strings too.
9:50 am
What are the top two IP's from the Ukraine?
9:53 am
At this point we have a policy of not sharing that data. The reason is because in some cases the servers still have a security hole that an attacker used to compromise it in the first place. So we don't want to provide targets. We may change this policy in future.
11:30 pm
Is this brute force attack legal? If you contact the hosting provider in Ukraina and inform them about the case what will happen? They should take responsibility about these attack or someone else. I want to thank to all the team behind the Wordfence security, you save sooo much time to the admins!
10:18 am
Ukraine and Russia definitely top over the last few days. Did you inform the Ukrainian hosting provider, and are they willing to co-operate?
10:55 am
Hi Richard. Yes we have informed them. No response as yet.
10:26 am
Is anyone notifying the hosting company in the Ukraine? Is there any system to hold them responsible? Does their govt have any laws against it?
10:55 am
Hi Evelyn,
We have contacted them and reported the IP's. No response as yet.
Regards,
Mark.
10:36 am
I fully trust and depend on Wordfence and one other security plugin. Since I started using them I have not had one infiltration or hack... WF has so far helped block literally thousands of brute force attacks on the many WP installations I monitor and maintain. THANK YOU Wordfence for your high quality (even at the Free level), your diligence in always being up to date and ready for new styles of attack but especially for your communications such as that last email, which helps us better understand the vicious and aggressive online world we live in today. Passing on this type of information only makes us all smarter, better equipped and ready to deal with hacks and attacks.
10:44 am
Regarding AWS and their responsibility. I humbly somewhat disagree that it isn't their fault. With the volume of attack activity coming off their servers, there are several tool sets and protocols available to better manage this. It's ironic since they consider themselves the best at hosting services. I know my hosting services at Rackspace and A2 are very good about catching this early.
10:45 am
Thank you for you diligent work in the area of security. You really take it to the next level! I will be going premium soon, I just restarted my website.
I do have a question
Do you think a captcha on the login, is almost as good as a second sign in? I don't use my cell phone much.
Thanks for you incredible work. It really is cutting edge!
10:50 am
Hi Mary,
I'd say simply adding brute force protection and cellphone sign-in (Wordfence provides both) are enough because you're trying to stop people making multiple login attempts as they try to guess your password, and those two techniques protect against this attack very effectively.
mark.
11:15 am
Nothing new to add to the comments already made other than that you may think your website isn't going to attract that kind of attention but you're wrong.
When you install Wordfence you'll find out exactly why you should have installed it sooner.
Keep up the great work.
Sean Durrant
11:18 am
I've been watching these attacks with various plugins (which is how I found Wordfence) for a year or so. Once in a while I get a site getting multiple attacks per minute! Hundreds over an 8 hour period. They kind of come and go.
Best advise is don't use 'admin' as your admin login for one. That seems to be the most tried login name. (as well as the URL sometimes)
11:43 am
Another thing is to change your administration name to something other than "admin" and in the options check "Immediately lock out invalid usernames".
11:51 am
150 failed logins in 3 hours!!! This was my sitiation
12:16 pm
I love 2 factor, I hate that Obama says to use it...
12:39 pm
LOL! I have a strict policy of staying completely politically neutral and so I almost didn't post the link to the op-ed. But it's relevant because it's public policy on cyber security so I threw that in. I'm definitely not a political creature. It's obviously top-of-mind for many being an election year. I was actually in DC last week for a conference so perhaps I was channelling that. :)
~Mark
12:16 pm
Another great post, sad as it might sound I have been keeping record of the bad login attemt emails that I get from Wordfence from 44 sites that I manage. For the month of January 2016 there were over 5500.
12:32 pm
We have noticed an increase across our sites and moved to the Premium package to block by country and tighten up a few things but still not a large number appear to be block before hitting us. When being blocked, does that mean they are blocked before they get to us or the Premium is package is working overtime?
If the Ukraine and Russia are not playing ball why cannot you get together with other major companies and together block their servers and IP range, they may decide to co operate more quickly (if they are not involved???)
12:36 pm
Hi Brian,
You'll see requests in your web logs but they aren't able to sign in.
We're looking at ways to automate getting these IP's taken offline.
Regards,
Mark.
1:32 pm
Horrible statistics. I'm always amazed that with the info available, these nasty pieces of work can't be hunted down And, should the average number of attacks per victim website is 91.15 not the 6.26 given?
3:32 pm
Wordfence is absolutely great. Gonna have to look into that 2FA.. =) I have used clef for 2FA before though.
6:07 pm
I'm getting a lot from Republic of Lithuania. Managed to block that country, as well as Russia at the server level using WHM control panel.
9:17 pm
Thanks for the plugin - love the revert feature. We have been getting hammered by Ukraine and Russia lately as well as France.
12:20 am
Hope you folks here at Wordfence (WF) don't mind me posting this. Feel free to delete.
Here's a great way to block a "bunch of brutes" with a single word or two...
After setting up the website I make sure that I get notifications. When I get an attack I take a note of what "brute name" their using for my login username. I copy that and go to my site > WP > Options > scroll to "Login Security Options", the last line: "Immediately block the IP of users who try to sign in as these usernames" I paste the "brute" name in the box. This seems to block a number of attackers at once that tend to use the same "brute name".
Really love this option. I do have premium, which gives me more of a surgical way of cutting out the "brutes".
3:56 am
I had a problem with people from the Ukraine over Christmas. Blocking and redirecting them to the most obnoxious You Tube video I could find has kept them away along with the the bots from China, Russia, ect...
I have a question that may be far-fetched, if not impossible to do, but it has been rolling around in the back of my mind since Christmas.
Is it possible to have a plugin that checks IP addresses even before a person / bot can get to a site? i.e- Somebody or a bot from a universal blacklisted IP address tries to enter a website. With this fictional plugin in place, the person / bot would be denied automatically before they could try to do something stupid. I asked my host about this and didn't get a answer.
I don't mind putting the time and energy into my site, but I've spent many hours blocking IP addresses ( this was before I had premium and country blocking) and even then, it wasn't enough. Just when I thought I had a handle the Yandex spider out of Russia, they'd appear again. The same with the Baidu spider out of China.
This may be a dumb idea, but it would make things a bit easier and I would pay for such a thing if it existed.
4:00 am
"The Ukraine is the top offender, ...The United States is second. Our hypothesis is that this is where most data centers are based and therefore most compromised sites, from which attacks are launched, will be based in the USA."
or maybe there are a lot of crackers in the Usa. nothing to be ashamed of.
9:29 am
LOL! Thanks, good point.
4:45 am
Thanks for your awesome plugin! I got a lot of traffic from ukraine this month too, so my top blocked ip addresses are from there.
Keep up the good work, im gonna think about the premium soon!
3:43 pm
The main reason for these attempts no has mentioned!
From my research, I have found it all has to do with Google!
Most of these IP's attacks also keep hammering xmlrpc, at the time Google bots are scanning your site. The result is google cannot scan your site, resulting you cannot be found on the google search!
SO MY QUESTION IS WHO ARE THE PEOPLE ? My speculation is the people are SEO providers for Wordpress!
3:10 am
Hi Mark
Nowadays there are so many people who are trying their hard to crack WordPress passwords. From last few days, I had also getting so many failed login attempts.
Someone trying to access my WordPress again and again.
I had already installed Wordfence security plugin but I don't know where to block them.
Now would follow what you said in this article. Let me see If it worked.
Thanks for sharing this article with us. :D
10:44 am
I currently have the free version but I'm considering upgrading to the premium. One concern/question. So then with the 2-factor sign in you get a text on your cell you have to respond to? If so, that means if you don't have your cell, left it at home while you're out, battery is dead etc, you won't be able to sign into your site?
11:00 am
Yes, that's correct, you need your cellphone to sign in.
9:50 am
Thanks for all you do Wordfence, I'm a happy premium customer. Regarding your brute force attacks coming from mainly the Ukraine on 2 ip addresses, what are the ip addresses, we will certinaly make sure they are blacklisted on our server? Thanks.
10:47 pm
Did you get reply to your ? For IP addresses so you could block?
6:42 am
I have had 50 brute force attempts in one day.! Thought it was personal. It's was so ridiculous that the site was in maintenance mode and they still tried. Mainly from Ukraine, Russia and US. Thanks to Word Fence I have paid more attention to security. Upgrading the the paid version.
Thank you guys for the awesome work you do!
6:12 am
Hi, I get hit twice a week for 2 years now, mostly from Ukraine, Turkey and Korea. Do you have an idea how they target the wordpress sites ? Randomly scanning the internet for Wordpress sites and trying to login ? In some cases, they tried to be clever in guessing the id, using words from the site name or names from the posts comments. Is it a software running or is there an army of hackers trying to force entry ?
Thanks for your plugin!
2:13 pm
Wow, that is an amazing number of attacks! Thankful that you are around to help with security and education!