Panama Papers: Email Hackable via WordPress, Docs Hackable via Drupal
The Mossack Fonseca (MF) data breach, aka Panama Papers, is the largest data breach to journalists in history and includes over 4.8 million emails. Yesterday we broke the story that MF was running WordPress with a vulnerable version of Revolution Slider and the WordPress server was on the same network as their email servers when the breach occurred.
Today we will release new information describing how the attackers may have breached the MF email servers via WordPress and Revolution Slider. We will also summarize below how they probably gained access to client documents via Drupal. We are breaking the story today about the link between WordPress and MF’s email server. The Drupal story has already been covered earlier this week in the media by Forbes (see below), but we are providing some data to support it.
How they hacked email
According to Süddeutsche Zeitung, the German publication that originally received the Panama Papers leak, this is the breakdown of the data structure of the Panama Papers:
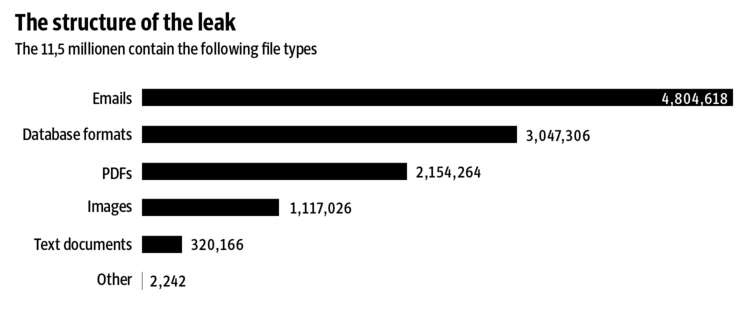
Source: Süddeutsche Zeitung
Email is by far the largest chunk of data in the MF breach. Last week MF sent an email to its clients saying that it had experienced unauthorized access of its email servers, confirming that the servers were compromised and making it clear this was in fact a hack.
Yesterday we showed how trivially easy it was to hack into the MF WordPress website via the vulnerable version of Revolution Slider that they were running.
Once you gain access to a WordPress website, you can view the contents of wp-config.php which stores the WordPress database credentials in clear text. The attacker would have used this to access the database.
Our analyst’s research shows that www.mossfon.com is running two plugins in addition to Revolution slider:
MF are running the WP SMTP plugin which gives you the ability to send mail from your website via a mail server. This plugin stores email server address and login information in plain text in the WordPress database. The login information stored is a mail server SMTP login for sending email. Here is a screenshot showing the login information for this plugin appearing in a database as plain text on one of our test servers:
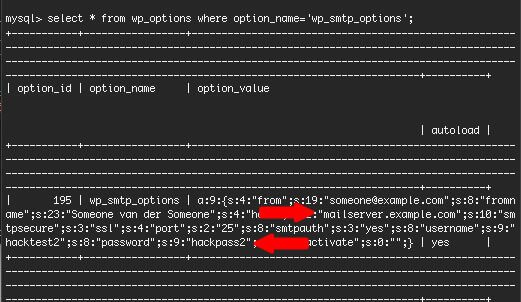
As you can see above, once an attacker had access to WordPress, the wp-config.php file which contains the database credentials and then the WordPress database, they can see the mail server address and a username and password to sign-in and begin to send email. They would also have had whatever other privileges were conferred on that account.
MF are also running the ALO EasyMail Newsletter plugin which provides list management functionality. One of the functions it provides is to receive bounced emails from a mail server and automatically remove those bounced mails from the subscriber list. To do this, the plugin needs access to read emails from the email server. This plugin also stores email server login information in the WordPress database in plain text. In this case the login information provides the ability to receive mail via POP or IMAP from the mail server. The screenshot below shows how this plugin stores email server login information:

Once the attacker also had access to this data, after gaining access to the WordPress database via Revolution Slider, they would have been able to sign-into the email server and would be able to read emails via POP or IMAP.
To summarize the attackers movement
We think it is likely that an attacker gained access to the MF WordPress website via a well known Revolution Slider vulnerability. This vulnerability is trivially easy to exploit as we demonstrated in our research released yesterday.
This would have given them access to the WordPress database. The research we released today shows that MF are running two additional plugins that store login information for their email server in plain text in the database. The attacker would have read this information from the WordPress database and used it to gain access to the email server.
Did they enforce the principle of least privilege?
One of the key concepts in information security is the principle of least privilege. For example: User accounts should only have the access they need to do their job. Did MF configure those WordPress plugin email accounts so that they could only receive bounces and send web based emails?
It’s easy to imagine in a company with high powered clients, the same account that a customer relationship manager uses is also used to send list emails. This would ensure that the manager sees all replies in his or her inbox. If that was the case, the attacker would have gained access to a senior staff member’s email account when they stole these email server credentials.
How attackers probably gained access to client corporate documents
I’m going to briefly summarize how attackers probably gained access to client corporate documents like PDF’s. According to the Mossfon client portal website at https://portal.mossfon.com/, “The Mossfon Client Information Portal is a secure online account that enables to access your corporate information anywhere and everywhere, with real time updates of your ongoing request.”.
The MF client portal that provides clients access to data was running (and continues to run) a version of Drupal that has over 23 vulnerabilities. This version was responsible for “Drupageddon“, a mass hacking of Drupal sites. This link to mossfon.com’s drupal changelog shows they are still running an old vulnerable version of Drupal. Here’s a screenshot:

Breaking into this system wouldn’t even tax a beginner security analyst. Once an attacker compromised the client login permissions system which is Drupal powered, they would have defeated any access control and could access any client corporate information. We think this is a likely vector used to steal client PDF’s and other documents. The weakness in MF’s Drupal website was first covered by Fortune earlier this week.
Conclusion
Yesterday we demonstrated that Mossack Fonseca had a Revolution Slider vulnerability in their WordPress site which probably gave an attacker initial access to their systems including their WordPress database. Today we demonstrated how the attacker could move from their WordPress installation into MF’s email systems and begin to compromise email which formed the bulk of the data breach in the Panama Papers.

Comments
3:48 pm
So user who have installed ALO EasyMail Newsletter plugin are also vulnerable?
4:07 pm
An attacker would have to compromise your server via something like Revolustion Slider to get access to your email server credentials that ALO stores in the database.
8:33 pm
Yes, your site have to be compromised first, but... I bet ALO Easymail and WP Mail SMTP developers, along with any other plugin developers who already are storing passwords in plain text in the database, should do something to encode it, but, at the same time, is this possible? even if you use salts, a hacker with access to the db would have access to the salts too, and hence be able to decrypt the pass. Am I wrong? Any idea for plugin developers to improve this and make these plugins a bit more bullet-proof?
1:29 pm
Unfortunately, there is no 100% secure way to encrypt password that needs to be decrypted for use later. Plugin stores both encryption and decryption method, and if someone gets access to the system, they will get access to data and plugin. It might take them some time, but they will figure it out. Website needs to be protected from hackers, once they are in, they have access to everything.
11:40 am
No, only Rev slider. They were saying that once in , those other plugins have credentials.
4:04 pm
So the email creds gave them access to a single account? How does that compromise other accounts on that mail server?
Sounds like the leaks came from Drupal, not Wordpress. Can you clarify?
(not arguing that there were vulnerabilities, it just doesnt sound like they yielded much in this case).
4:09 pm
Yes. Either one account that had both IMAP or POP and SMTP access. Or two accounts, one with SMTP and one with IMAP/POP. They would have been able to do what that account had access to. In our writeup we include a scenario where it would have given them widespread access. Another possibility is they could have used a mail server privilege escalation vulnerability to gain further access. What we've established is a clear path to transition from WordPress to the mail server.
11:48 am
If the credentials are to the email boxes admin, then that user has the ability to access other email accounts. Seems like both websites were running outdated code though. but the main hack was the Rev slider vulnerability, which has been vurnable for soooooo long. Moral of the story is ALWAYS update your sites and research your plugins and themes before you choose them. Don't skimp on a good web dev and don't fire them without getting info from them.
4:19 pm
Great write up Mark. Is Revolution Slider not patched/actively maintained, or was this simply sloppiness on MF's part?
4:28 pm
It's active. https://revolution.themepunch.com/. The maker seems to use Revolution Slider and Slider Revolution interchangeably. Most of the infosec community knows it as (the infamous) revslider.
4:36 pm
As mentioned yesterday, the slider plugin had not been updated in a while and therefore was vulnerable..
4:29 pm
Any suggestions on how to prevent these security issues besides not using these particular plugins? Or how to further secure a site?
8:57 pm
Generally speaking, the formula is: Always keep WP, plugins and themes current. Install Wordfence and, if possible, go Premium. If you're using plugins that become unmaintained, replace them with other plugins that are actively developed so that you are better protected from previously undiscovered vulnerabilities.
7:34 pm
There really is little excuse for not keeping WordPress, its plugins and themes up-to-date. For those who are lazy and want it as automatic as possible, just add this to the bottom of your wp-config.php:
/** Set automatic updates */
define( 'WP_AUTO_UPDATE_CORE', true );
add_filter( 'auto_update_plugin', '__return_true' );
add_filter( 'auto_update_theme', '__return_true' );
As for Drupal, there is a shell app called 'drush' that makes updating Drupal Core and modules very easy.
12:17 am
This can break your website without notice. And you can't do this on corporate enviroment. Updates are sandboxed and tested before production.
10:09 pm
Thanks for this informative blog, would recommend people not use rev slider? or is it fine if its maintained?
12:17 am
Great work Mark!
12:44 am
How is it possible to read in plain text a .php (wp-config.php) file hosted on a web server?
You should have access to the root folder of the web site and this is possible in three ways:
- through a ftp account
- through the File manager of the CPanel of the web host account
- through the technical team of the web hosting company.
9:22 am
Once an exploit like this is run, through code, an attacher can read php files as plain text. The quickest way would be to run code that simply reads the text of the wp-config.php file and outputs it, or reads through it to get the database passwords, then logs into the database and dumps all the database content out. So, as the post says, the original vulnerability would allow the hacker to read the config file, which contains the DB login, which they could then use to get the database information, which contains the passwords for the email server, which are in database settings for the SMTP plugins listed.
2:11 am
The way WP SMTP plugin allows plain text entry of mail password in it's settings has always been a cause of concern for me.
The general rule is Any plugin that puts your life at risk should be disabled and deleted no matter how many stars or downloads it has.
Thanks @Mark for the detailed info.
4:39 pm
Great analysis, hacking reverse engineering and forensic at its best.
5:50 am
Great work as always Mark! Don't know what I would do without Wordfence.....
4:03 am
Thank you Mark. Good Work !
9:16 am
It just goes to show that anyone is vulnerable to an attack. You should always scan your sites and keep all plugins and themes up to date. It's part of routine maintenance. The tough part is when you run multiple sites and have to go in and do this on a regular basis. Thanks for putting the word out about this!
11:52 am
This is a really interesting article which I've been sharing as widely as possible.
One of my contacts, a top-flight investor, asked me "Is there a way that an investor could satisfy themselves about the security of a firm's online platform before using them?"
What do you think? My gut feeling is there is no way you can tell for sure...but are there some basic checks one could do before committing private info to a company's site?
What about doing a DNS lookup and seeing if they are running through CloudFlare? If they were, that might indicate a concern for security, although if they were not, you couldn't assume the reverse, of course.
Any ideas, anyone?
4:23 pm
Hi Steve,
You'd need to get an external company to do a security audit on the business you're planning on investing in. Unfortunately we don't offer that service.
Mark.
4:37 am
Hi Mark,
I wasn't expecting you to offer a service :) And I don't think most companies would take kindly to someone saying "before I deal with you I want to send in someone to check out your IT security".
I just wondered if anyone had any thoughts on signs that a company's web security was weak or strong. Of course, even if their site was well secured, it doesn't mean that there are not weaknesses in their other systems, and it only takes a rouge employee to compromise them.
So I think the answer to my investor friend is something like "No, there is no way you can tell in advance"!
4:41 am
...a rogue employee, even :)
7:55 am
I think you can tell in advance if you do your homework.
12:14 pm
Rev Slider is awesome. I saw a site, in 1 min (1st attempt) I had a shell uploaded, changed theme files and sent my acquaintance (whose partner chose some other dev), a few screenshots, that is his brandnew site was already compromised.
web noobs..web noobs everywhere
6:17 am
Their site seems to have been cleaned up now and they're being protected by Incapsula - who interestingly also protects the ICIJ Panama papers website. I wonder if Incapsula understand that they are potentially protecting companies with sanctions, and that they also have a major conflict of interest.
11:23 pm
Good article! Drupal security issues are fixed pretty quick in core, if you are a good developer then you also check up on the security and fix possible issues. Us from Cooper Webdesign desided many years ago to go with Drupal. Best choice ever!
Drupal are maybe more difficult to use at first look, but a good themer/designer can always create a user-friendly interface. Drupal is the most flexible CMS so far, thats why we all love it.