Malware: 139,000 WordPress Sites Saved in 30 Days
Wordfence provides two core security capabilities to the websites we protect. Our firewall prevents your WordPress site from getting hacked. Our malware scanner detects if you have been hacked or if malware has somehow been installed on your system.
Today I’d like to share a few malware statistics, how we put new malware detection into production and a story about one prolific piece of malware we’re seeing.
139,766 Unique WordPress Sites Saved in 30 Days!
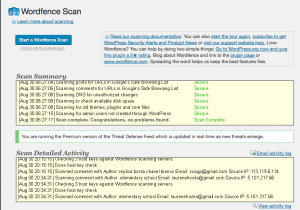 During the past 30 days, 139,766 unique websites have detected malware of some kind using Wordfence scan. That’s an incredible number. I like to think of it in terms of baseball stadiums. Our local Safeco Field, home of the Seattle Mariners, can fit just under 50,000 people. If each website belongs to a person, we could fill the stadium almost three times with website owners we’ve helped protect in the last 30 days alone! That’s incredible.
During the past 30 days, 139,766 unique websites have detected malware of some kind using Wordfence scan. That’s an incredible number. I like to think of it in terms of baseball stadiums. Our local Safeco Field, home of the Seattle Mariners, can fit just under 50,000 people. If each website belongs to a person, we could fill the stadium almost three times with website owners we’ve helped protect in the last 30 days alone! That’s incredible.
At Wordfence we provide a free community version of our plugin for WordPress and a paid version. We send out threat intelligence to the plugin via our Threat Defense Feed. This includes new scan ‘signatures’ for new malware that we have discovered during our forensic research. It also includes new firewall rules to protect you against new kinds of attacks.
Wordfence Premium receives the updates in real-time. Our community edition is delayed by 30 days. So new scan signatures only become available to the free users of Wordfence 30 days after they are released.
During the past 30 days the malware signatures that our Premium customers have early access to detected malware on 5.2% of our Premium customer websites.
How many free and premium scan signatures do we currently have?
Wordfence currently has 364 free scan signatures that each detect a different kind of malware. In some cases a signature will detect many different kinds of malware because it’s designed to detect common malware patterns.
When you do a scan with the free version of Wordfence, you are checking every file you scan against all 364 of these signatures to try and detect the most common malware we’re seeing. It’s worth noting that we actually retire some malware signatures because sometimes, a piece of malware just isn’t seen anymore or we improve our detection capability.
For our Premium customers we have an additional 118 signatures (sigs) currently in production. We continue to add to those sigs and the older sigs become available to our free customers 30 days after they are released.
Those 118 Wordfence Premium sigs were added at different times, so they become available to the free community at different times.
- Thu Sep 08 2016: 38 new Premium sigs will be released to our free customers
- Sun Sep 25 2016: 24 Premium sigs will be released
- Wed Sep 28 2016: 15 Premium sigs will be released
- Thu Sep 29 2016: 41 Premium sigs will be released
How does Wordfence develop, test and release scan signatures?
The way Wordfence adds new scan signatures is we develop and then test them internally. The testing involves running each sig against the top 5,000 WordPress themes and plugins along with multiple versions of WordPress core to ensure there are no false positives. We have developed internal tools to do this very quickly.
Then we add them to our ‘beta’ feed. If you are a Wordfence Premium customer you can enable the Beta Threat Defense Feed which includes our beta scan signatures by going to the ‘Diagnostics’ menu, scrolling to the bottom and checking the ‘beta’ checkbox. This is only available for Premium customers.
Once we’ve verified the new sig is not creating problems for our beta community, we flag the sig as ‘production’ and it enters production for our Wordfence Premium customers. Those customers receive the new sig automatically and don’t need to upgrade or take any action. 30 days later the sig enters the community version of Threat Defense Feed.
Wordfence currently has 112 scan signatures in ‘beta’ and they will enter production for our Wordfence Premium customers over the next few days and weeks. We tend to release scan sigs in batches, as you can see from the date schedule above.
The Premium Threat Defense Feed gets the newest scan signatures which means that those signatures have an unusually high detection rate. The detection rate is high because the new sigs we add are things we have recently seen in the wild.
What does “In the Wild” actually mean? Where do Wordfence scan signatures come from?
So what does it mean when we say we saw an infection ‘in the wild’ and we added it to the Threat Defense Feed as a scan signature?
At Wordfence we have built a team of some of the finest cyber forensic investigators in the industry. We have two major efforts that help us find new WordPress malware samples and threats.
The first is our site cleaning service. Wordfence offers site cleaning at a very reasonable price and one of the things we get from providing that service is on the ground intelligence of what is infecting real WordPress sites. Our site cleaning team has a very efficient process to turn the samples they find on infected sites into scan signatures in production. The process ensures we remove any duplicates and are able to prioritize samples where we’re seeing a widespread infection.
The second way we gather threat intelligence is by mining attack data. When an attack occurs on a WordPress site, that attack is reported to us. Some of those attacks include malware payloads. We are able to aggregate those malware samples into a database and prioritize them by the malware we are seeing most frequently. This has become a huge source of new malware signatures for us which has accelerated the pace at which we are able to add new signatures to our scan engine.
What is the most widespread new malware Wordfence is seeing?
To illustrate how powerful it is to have the newest malware signatures in your scan feed, lets take a look at a specific example. Below we have a scan signature that was added on the 27th of July, last month.
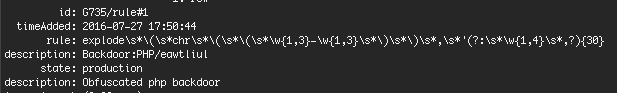
The image above shows selected database fields for this signature’s record.
Internally at Wordfence this signature has the codename Backdoor: PHP/eawtluil. Not very attractive sounding. Our more technical audience will recognize the scan ‘rule’ as a regular expression or ‘regex’.
During the past 30 days this signature has detected over 1 million infected files across all Wordfence customers. This infection has a habit of infecting a lot of files when it hits a WordPress site. That is more malware infected files than the next 10 signatures combined.
This signature was added on the 27th of July last month. That means it was in our Premium feed for 30 days and only recently became available to the free community users of Wordfence on the 27th of August, 4 days ago. Now that it’s running in our free feed, it is detecting a huge number of malware infected files across the WordPress ecosystem. And that’s just one signature!
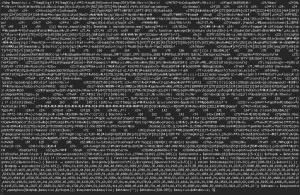
So what does this sig actually detect? This is what the malware actually looks like: (click to open a larger image in a new tab)
As you can see the malware is heavily obfuscated (encoded to hide the meaning of the code).
As attackers realize we are detecting their malware, they will use new obfuscation, or code hiding techniques. This signature will become less effective and new signatures we add will have a higher detection rate. That is why we refer to our scan signatures as a ‘feed’ or the Threat Defense Feed. Our forensic work is ongoing and we are continually adding to the feed and optimizing what is in it.
In closing…
I hope this has given you some insight into a small part of our operations at Wordfence – specifically our forensic efforts into gathering threat intelligence and how we turn part of that data into the scan signatures that provide you with early detection of a hack or malware on your WordPress website.
If you would like to install Wordfence free on your WordPress website, simply go to the Plugins menu and use the search box on the top right to search for Wordfence. To upgrade to Wordfence Premium and get your scan and firewall rules in real-time, 30 days earlier than everyone else, you can visit our home page to learn more about the Threat Defense Feed and how to get Wordfence Premium.
As always I welcome your questions or comments. Thanks for using Wordfence and stay safe.

Comments
9:39 am
You saved my client's website yesterday, thank you! His site is on an older GoDaddy server that can't be upgraded beyond PHP 5.4, and it was hacked through the server. Wordfence found more than 20 infected files and alerted us. It was easy to remove the infected files with Wordfence, too. We advised GoDaddy about the breach, and we're making some upgrades now. Thanks, Wordfence!
10:54 am
Kimberly, can you please say how PHP 5.4 was the cause of the hack please. And exactly how the server was hacked. You just worried a lot of people who run security patched versions of PHP.
10:02 am
I love WordFence. You guys do an amazing job protecting web sites from hackers. All of my sites use WordFence and it is a standard install I recommend to all my clients.
Thank you so much!
10:26 am
You guys have done a great service for the Internet in general and for website owners in particular with this plugin. Your company will surely be successful. Thanks
10:44 am
Thanks alot for the great work you are doing .
3:24 pm
Hi All! You truly are amazing.
2 questions
1) I was wondering what these hacks do to the site. Do they redirect links or spy or....? I am not a "behind the scenes" techy person.
2) Also, how much danger are visitors in if it is hacked if they click on links?
Still using the free version. I want to start an email list and was going premium then. Or is this problem too critical to wait? (I guess that is 3)
Your service and technology, is really godsend! Thanks for being YOU!
Mary
6:38 pm
Always great to see you guys on top of the security game. It has been many times over the years that we owe thanks to the WordFence team for being the first to find hacks and vulnerabilities. This continues to be the case year after year. So glad to have such a talented and dedicated team on the job. Thank you for all you do.
7:22 pm
You know, if it wasn't for the Wordfence team, I don't know if it was possible to run a WordPress site, you guys have saved my behind in a couple of my blogs, good job guys,
Thank you guys.!
5:13 am
How about open beta version to Community version users? Isn't the more testers the better?