New WannaCry Ransomware and How to Protect Yourself
This is another Wordfence public service announcement (PSA) that describes new WannaCry ransomware variants that have emerged in the past few hours and describes how to protect yourself against the WannaCry ransomware, also known as the WannaCrypt ransomware. We occasionally send out alerts that are outside the WordPress space when we feel that they are in the interests of our WordPress publishers and the broader global community. This is, unfortunately, one of those alerts.
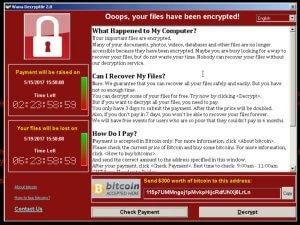 On Friday we alerted you to a global ransomware campaign a few hours after it started. That campaign has now infected over 10,000 organizations and 200,000 individuals in 150 countries. This includes the UK National Health System which saw ambulances divert from affected hospitals.
On Friday we alerted you to a global ransomware campaign a few hours after it started. That campaign has now infected over 10,000 organizations and 200,000 individuals in 150 countries. This includes the UK National Health System which saw ambulances divert from affected hospitals.
On Friday a researcher accidentally stopped the ransomware from spreading by registering a domain that served as a kill switch for the ransomware.
A few hours ago new variants of the WannaCry ransomware started emerging. One of the variants was also stopped today by registering a kill switch domain, the same way the ransomware was stopped on Friday. A second variant is not encrypting infected machines due to an error in programming, but it is spreading.
We expect new variants to emerge all week that continue to exploit the vulnerability in SMB that WannaCry has been using. It is critical that Windows users protect themselves immediately against this threat.
WannaCry Ransomware: How to protect yourself
- If you use Windows, install the patch that Microsoft has released to block the specific exploit that the WannaCry ransomware is using. You can find instructions on this page in the Microsoft Knowledge Base. You can also directly download the patches for your OS from the Microsoft Update Catalog.
- If you are using an unsupported version of Windows like Windows XP, Windows 2008 or Server 2003, you can get the patches for your unsupported OS from the Update Catalog. We do recommend that you update to a supported version of Windows as soon as possible.
- Update your Antivirus software definitions. Most AV vendors have now added detection capability to block WannaCry.
- If you don’t have anti-virus software enabled on your Windows machine, we recommend you enable Windows Defender which is free.
- Backup regularly and make sure you have offline backups. That way, if you are infected with ransomware, it can’t encrypt your backups.
- For further reading, Microsoft has released customer guidance for the WannaCry attacks and Troy Hunt has done an excellent detailed writeup on the WannaCry ransomware.
Get the word out
The second wave of attacks appears to have just started within the past few hours. This is going to be a rough week for Windows users. We recommend you get the word out by sharing this post to help keep friends and family secure.
Additional resources:
- A fact sheet: https://gist.github.com/rain-1/989428fa5504f378b993ee6efbc0b168
- A detailed description of the worm and the exploit it uses to spread: https://blog.malwarebytes.com/threat-analysis/2017/05/the-worm-that-spreads-wanacrypt0r/
- Deep technical analysis: https://blog.comae.io/wannacry-the-largest-ransom-ware-infection-in-history-f37da8e30a58
- Info on new variants detected today (also linked to in the post, above): https://blog.comae.io/wannacry-new-variants-detected-b8908fefea7e
- Coverage analysis on Virustotal. A spreadsheet showing which signatures/files are being detected by anti-virus vendors, when they were first submitted to virustotal and the names of each component each AV vendor is using: https://docs.google.com/spreadsheets/u/1/d/1XNCCiiwpIfW8y0mzTUdLLVzoW6x64hkHJ29hcQW5deQ/pubhtml#
- NoMoreCry: A tool created by the Spanish cyber security center (CCN-CERT) to prevent infection by this ransomware. We don’t recommend you use this tool at this time. Instead, patch your system and use a an anti-virus product or firewall rules. This is merely for academic interest: https://www.ccn-cert.cni.es/en/updated-security/ccn-cert-statements/4485-nomorecry-tool-ccn-cert-s-tool-to-prevent-the-execution-of-the-ransomware-wannacry.html
- A live feed of WannaCry infections on a map: https://intel.malwaretech.com/WannaCrypt.html
- Microsof Customer Guidance: https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
- A tweet by Tal Be’ery describing the root cause of the vulnerability with links: https://twitter.com/TalBeerySec/status/863741929401585664

Comments
1:48 pm
This ransomware is causing a global havoc. Cheers to the researcher who "accidentally" found a temporary solution. I still wonder why big companies (including the affected hospital) ran old versions of these OS that were infected.
Like I always say, if your data is that important, always keep a backup somewhere.
These hackers are going to have a field until the affected organizations start to use current OS. The question comes again: "Why not simply use a Linux Distro?"
2:39 pm
For a hospital (or any large organisation), changing from one OS to another isn't simply a case of clicking "OK". Most of their software will only run on the OS it was written for, so upgrading is both difficult and costly.
Most private Windows users kick up enough of a stink with each new OS, when their copy of Half Life or whatever stops working. It's just like that for hospitals - though what "stops working" might be the patient database software or even major hardware, like scanners.
One hospital in the UK, which was apparently unaffected by WannaCry, developed its own system. It cost $260,000,000. Not all hospitals can afford to do this.
4:35 am
That's correct, ATM's for instance are know to run on XP and as a consumer there is not much you can do about it.
But what I don't understand is that a firm/hostpital/whatever can not use multiple systems. For instance use accounting and customer databases on an up to date system, and leave the MRI scanner and some other tailer made systems eventually on XP.
Also, nobody is advising users to open their mail in a sandbox? Can be installed in 5 mins, free options available and the stupid secretary can open any 'joke of the day pishing mail' she wants without causing any harm.
2:56 pm
And although it is very fashionable to say "use Linux", Linux has got plenty of holes of its own that could easily be exploited if anyone decided it was worth their while to do so. If large organisations started using it in large numbers, it WOULD become worthwhile to the people who do this.
Cyber security is a never-ending game of cat and mouse, and it is researchers like those at Wordfence who try to make sure the mice always keep ahead of the cats. There is no single, practical, infallible solution to these problems.
4:58 pm
Actually this seems to be targeted at small businesses, but unfortunately some large organisations' IT departments tend not to be run very well in certain industry segments, such as healthcare.
There no reason not to be running Win Server 2012 with at least Win 7. No healthcare org should be on XP. They're putting their patients' lives at risk.
5:46 pm
A recent report says that "more than half of businesses are still rely on Windows XP". While that might not mean that the whole infrastructure is reliant on XP, it's still a heck of a lot.
From what I understand, many UK Hospital Trusts really ARE running their infrastructure on it - and into the bargain the UK government decided not to pay Microsoft for extended support. Then there is the issue of embedded Windows in equipment - MRI scanners and the like. They don't come cheap, and a new OS isn't going to automatically mean a new scanner every time, so many will be based on older Windows versions and may not be upgradeable even if people wanted to.
XP was regarded as the most stable Windows in general and companies built their internal software around it. Taking Addenbrookes as the example - the hospital which paid $260m for a bespoke system - there is no way all those companies on XP could possibly afford that upgrade cost (even if it was a tenth or even a hundredth of that price) - they'd have to have their systems rewritten, remember, even if they stuck with Windows (or Linux). Granted, some of the bigger ones could - and should - have done it, but most couldn't.
I think it's a case of it is what it is, and it has to be dealt with as such.
1:54 pm
So this only affect windows servers? Your update seems to indicate this, but I'd like to be sure.
1:55 pm
Windows only.
2:24 pm
I think the operative part of the question - does this affect windows servers only - was the word "servers."
As I read the writeups, this seems to be an issue for Windows computers, whether they are servers or not. The key appears to be that computers using Homegroups for networking may be ok. However, non-Homegroup sharing in Windows uses Server Message Block (SMB)-based file-sharing, also referred to as CIFS.
If it was a server only issue, we wouldn't see so many individual computers affected.
Correct?
1:56 pm
So, looking at the updates I do not see Win10 listed.
I see everything else, but not Win10. Does that mean that a current and up to date Win 10 installation is protected already?
Asking this for my clients as well, so this will answer quite a few who are wondering this right now.
2:06 pm
Windows 10 is unaffected by this. So they are already safe.
2:43 pm
Thank you Mark,
You guys are great!!!
Bill Frankell
1:57 pm
All this would be have less impact if the users just know about phishing and other the basic of end user security.
2:07 pm
No. The ransomware enters via an SMB exploit. Not via phishing.
2:22 pm
Its the MS17-010? and patched on March 14, 2017? Is one month... They forgot to update?
3:20 pm
I don't think that many home computers expose SMB to the public internet. Most are behind NAT anyways.
The ransomware usually enters via phishing mails, and this new variant uses the SMB exploit to find other victims on the local network.
1:57 pm
I didn't see a patch specifically for Windows 7 - is that version not affected by this issue?
3:16 pm
If you have auto-updates enabled (or if you install them manually) then W7 should have been patched in March. If you check, the update was MS17-010.
My understanding was that W10 also had the same vulnerability, but this was also patched in March.
12:06 pm
There is a security update for Windows 7 issued yesterday 5-14-2017. 8 of them. I discovered this when I did an update yesterday.
I have a screen shot of them from my laptop but I guess we can't post pics here.
12:08 pm
See my comment to Dooad below. There were 8 security patches issued yesterday 5-14-2017 for Windows 7. Do an update and they should show up.
2:04 pm
Do these type of attacks rely on the Windows users having admin rights? In other words, besides doing updates regularly and having good anti-virus software does using a non-admin account help prevent intrusions?
2:10 pm
I don't think so in this case. This is an exploit that comes in via the SMB ports and does not rely on exploiting a logged in user and their level of access. It exploits a running service.
8:18 am
This is true - however I wanted to add
Im not sure SMB is the initial vector of the malware, but its still safe to ensure that people are aware of links and dont click on anything that they dont know and trust.
Once the malware is established is spreads through SMB vulnerability
The encryption component uses the users credentials to access the files it encrypts so for the actual damage done, it does use the users access - which of course is much higher (typically) than the non-admin user.
9:23 am
I'd suggest you read the additional technical resources we've linked to above.
2:08 pm
So if I'm understanding this, it's a server issue, not an home office machine issue, correct?
By the way, I love [sarcasm] the "kindness" of the hackers in their message on the screen shot you shared, "We will have free events for users who are so poor that they couldn’t pay in 6 months."
2:13 pm
No this affects home and business workstations too. Please see the articles we linked to on Microsoft's website.
2:10 pm
Many Hospitals in Indonesia are attacked by this malware. Thank you for the information.
2:12 pm
You're welcome. Thanks for the info.
2:17 pm
Great post thanks!
2:21 pm
Dear,
Can mcintosh laptops eg. macbook pro also beiing effected by the ransomware ..?
kindly regards Eddy
2:27 pm
No.
3:21 pm
They can if you have installed Windows on them.
2:36 pm
Excellent article and advice. In the eventuality that one of my friends does not heed the advice, is there a way to get the files decrypted and the ransomware off the computer?
Or is it: re-image and reload files from backup.
Gerrit
2:50 pm
I'm away from my computer but Europol has a project that can help. See the comments in our Friday post for the website link.
3:09 pm
If one of my systems was compromised, there is no way I'd be happy just "cleaning" it and trusting that any backdoor/trojan software had gone. I'd only be happy with a complete wipe followed by installation of a clean image.
Just my opinion.
2:46 pm
Hello, I generally don't lift content, but in this case (given the scope of the threat), I deemed it an exception. http://sooke.pocketnews.info/randsomeware-alert-new-wannacry-ransomware-and-how-to-protect-yourself/ Please let me know if you want me to remove this and I will do so immediately. I've provided a link back, and promoted WordFence as a tool utilized by SPN. I hope that is sufficient.
3:26 pm
If I have Microsoft Security Essentials runnign Windows 7, will Microsoft have updated the patch?
3:34 pm
I have Windows 7 and am trying to check the updates listed in my Control Panel's "Installed Updates" section. All of the updates are named in a "KBXXXXXXX" format (they all start with KB then 7 or so digits).
But all of the articles you point us to have a naming system of MSxx-xxx, so it's impossible to see if I have the correct update. I probably do, since I have auto updates on, but it would be nice to know that I can see that specific required update listed, just to be safe and know everything is ok.
So my question is: How do I find it in my Win7 "Installed Updates" area of the Control Panel?
Thanks,
Doug
5:52 pm
I think it should be KB4012212 and KB4012215.
10:45 pm
Thanks for that info. Unfortunately, I have neither and yet I have update set on auto. So how do I know if I am protected?
Seems like THIS is the weak link in this whole process. If one cannot verify they have the update that protects them, and yet they auto updates on auto, how do they know they are protected, if they can't confirm the fix is on their PC?
If anyone knows, please fill me in...
Thanks!
Doug
1:04 am
Use the links in the above article - the patches are in there.
5:57 am
The Microsoft link, that is. This is the one:
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
5:59 am
I just noticed, but the cumulative patch might be logged as KB4013389.
12:17 pm
I did an update for Windows 7 yesterday and there were 8 patches dated yesterday. Yes, they all start with KB, I have a screen shot. My husband had to do a google search for each one and download because for some reason the updates wouldn't show on his computer.
Looks like we can't post pics here but I will list them.
KB3156019
KB3108371
KB3045685
KB3031432
KB3004375
KB3004361
KB3035126
KB3097989
3:43 pm
Thank you for the information. I only work on macs so am glad of that right now, however the servers that hold my databases, and the companies that provide the backend software and various platforms that I operate on, will they be secure or could I face some disruption as a result of this attack?
4:09 pm
Hi I am also planning to share this public announcement on my website. Is there any permission for that?
4:35 pm
Please go ahead. We are working to get the message out.
4:36 pm
The ransomware writers should be thrown into a volcano.
6:13 am
No, they should receive a reward for opening many people's eyes. You can tell people a thousand times to update and be carefully opening mail, but they will not listen. Maybe this helps. And if you are infected, just pay the 300 bucks and consider it as learning money.
6:27 pm
What is the actual attack vector here?
7:03 pm
Please see the additional links added a few minutes ago to the footer of the blog post. It contains as many technical resources and analysis as you can stand.
7:02 pm
Hi Mark.
Thanks so much for your blog and notifications. When there is total silence from the AV and AntiMalware companies, it is refreshing to be informed by professionals like yourself.
Thanks again
Linn
6:01 am
Linn
I was informed by Malwarebytes Friday evening. They were a few hours behind wordfence but certainly not silent. Their premium software protects against this exploit. Their free and demo products do not.
10:48 pm
With reference to:
"If you are using an unsupported version of Windows like Windows XP, Windows 2008 or Server 2003, you can get the patches for your unsupported OS from the Update Catalog. We do recommend that you update to a supported version of Windows as soon as possible."
Not that the link is currently unavailable. Besides I tried to install KB4012598 directly but it says it is for Windows XP. What patch do I need to check for for Windows Server 2008?
2:51 am
Maybe it's time for hospitals and the like to start moving to hosted desktop type platforms where they can. This would make things easier all round and could be a less costly exercise than fully maintaining individual computers. Certainly strict virus and anti-malware policies could be enforced, recovery times reduced etc.
4:16 am
This is a crazy question but I have a client that sometimes runs an old laptop with Vista on it ... is Vista affected by this? Thank you for all your hard work on this !
8:42 am
It will be affected if it's not patched, but it should have been patched automatically back in March since it is still supported.
However, from what you said, it sounds like your user may not be updating so you might want to make sure. The patches are here:
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
6:45 am
How is it being spread?
8:10 am
We've included links to detailed technical analysis above.
6:53 am
Windows XP is no longer supported by Microsoft, which is their mistake. It happens to be the most stable version but is unsafe now. I've noticed a lot of hackers use Windows XP or Windows 7 and Firefox to attempt hackings. Its time Microsoft started fixing their security holes no matter what version for public safety.
8:49 am
XP is also 16 years old and technology has moved on.
Microsoft IS patching holes when they are found. Patches have been made freely available for XP, even though it is effectively obsolete and unsupported. All other versions have been patched (assuming people haven't been preventing those patches from installing).
I remember donkey's years ago when a magazine I subscribed to for the Atari computers switched from a cover-cassette to cover disks. People went nuts and said they'd boycott it. I often wonder if they're still using cassettes even now.
XP's day is over except in legacy situations. They've got to end eventually - maybe this is the wake-up call people needed.
7:47 am
One of my customers was infected by this. The infection spread through the backup and the cloud backup "iBackup". I was surprised that the cloud backup service offered no protection but this conversation is for another talk show. I had an offline backup that was a couple days old but i did not want my users to lose a days work. I was able to clean the virus with traditional methods and restore all the files from the day before using shadow copy. Thank goodness for shadow copy. Never leave home without it.
7:49 am
I am sure Linux does have its own vulnerabilities but until very recently a default installation was a lot more secure than a default MS installation.. However perhaps I should stop encouraging all my friends to use it so as not to contribute to it becoming popular enough to attract the attention of malware writers.
8:58 am
Linux isn't the solution. The last thing hospitals need is an OS which can be freely modified by almost anyone (and which has people at the helm as acerbic as Mr Torvalds was wont to be). Linux would have to go commercial to attract big business en masse (my opinion).
The only reason Linux (or Mac OSes) isn't attacked more is that there's more profit going for Windows. People used to say there were no Mac viruses, but that changed. Linux may not have viruses due to how it works, but it sure has malware. If everyone was using Linux, the hackers would soon find a way of cashing in on that instead.
8:32 am
No offense, but Windows Defender is s***. It provides nearly no protection compared to 30 other AVs. The other tips help, but this one doesn't.
9:22 am
It's worth pointing out that it does detect this infection. It'a also worth noting that if you have any other AV installed, Defender is automatically disabled by Windows.
12:19 pm
The download Microsoft lists on the catalog for Vista is only for XP. My daughter still uses Vista and it wouldn't download, gave an error only for XP. Ive done a Google search and can't find one for Vista.
1:27 pm
But Vista is still supported, so if she has been getting regular updates the patch ought to already be there on her machine.
4:48 pm
Does anyone know why there is no patch for windows 7?
9:29 am
I have Windows 8 and none of Windows 8 updates are working for me. I keep getting a message that its not the correct one.
11:04 am
Does anyone know if there is a simple Windows based utility that can scan your LAN network(s) and tell you which IP's or machine names are missing the patch or have the SMBv1 vulnerability?
4:35 am
Excellent information, which is good to know to prevent and inform us more about the world of viruses, cyber attacks and more, we can find more information.