The May 2017 WordPress Attack Report
Today’s post is a continuation of the WordPress Attack Report series we’ve been publishing since December 2016. Previous versions can be found here: April 2017, March 2017, February 2017, January 2017 and December 2016.
This report contains the top 25 attacking IPs for the month of May and their details. It also includes charts of brute force and complex attack activity for the same period. We also include the top themes and plugins that were attacked, and which countries generated the most attacks for this period.
The Top 25 Attacking IPs
The next section is our standard explanation of how the table below works. If you are familiar with our attack reports, you can skip down to the table below which contains the data for May along with my commentary.
Brief Introduction (If You Are New to Viewing These Reports)
In the table below, we’ve listed the most active attack IPs for May 2017. Note that the “Attacks” column is in millions, and is the total of all attacks that originated from each IP. Farther right in the table (you may have to scroll right) we break down the attacks into “brute force” attacks and “complex” attacks.
Brute force attacks are login-guessing attacks. What we refer to as “complex attacks” are attacks that were blocked by a rule in the Wordfence firewall.
We have also included the netblock owner, which is the organization (usually a company) that owns the block of IP addresses that the attack IP belongs to. You can Google the name of each owner for more information. A Google search for any of these IP addresses frequently shows reports of attacks.
The hostname included is the PTR record (reverse DNS record) that the IP address owner created for the IP, so this is not reliable data, but we still include it for interest. For example, we have seen PTR records that claim an IP is a Tor exit node, when, based on traffic, it is clearly not.
We also include the city and country, if available. To the far right of the report, we show the date in April when we started logging attacks and the date the attacks stopped.
The Top Attacking IPs
The total attacks from the top 25 attacking IPs increased from 137 million in April to 144 million in May.
Brute force attacks made up 72% of total attacks for May, up from 68% in April. Complex attacks accounted for 28%.
Turkey and Ukraine continued to dominate the top 25 list, accounting for 16 of the IPs on the list.
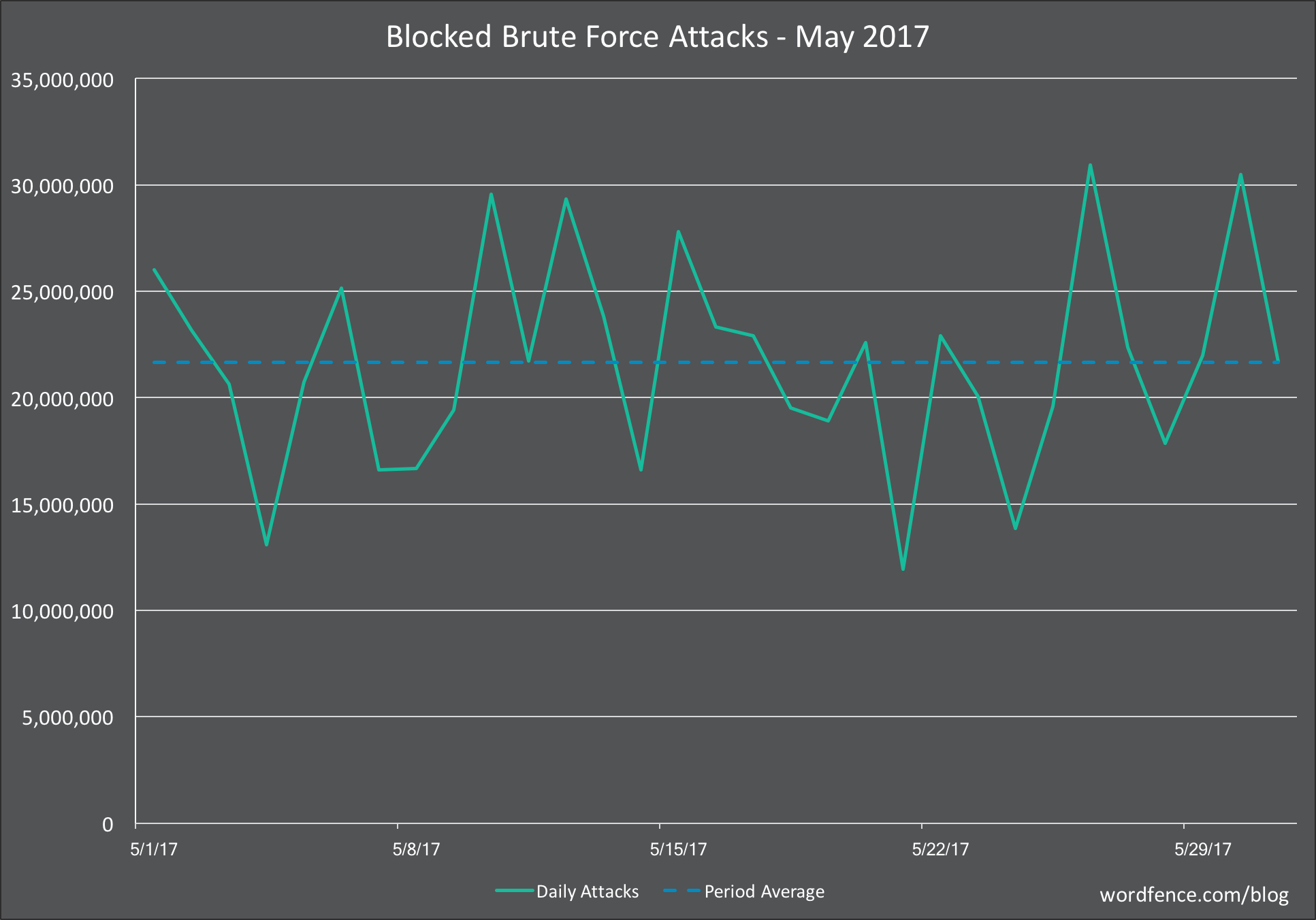
Brute Force Attacks on WordPress in May 2017
In the chart below, we show the number of daily brute force attacks on the sites we monitor for the month of May.
The average number of daily brute force attacks dropped by almost 39% this month – a massive drop in volume after two months of much higher volume. As we wrote about on May 2nd, a home router botnet shut down which had previously been performing brute force password-guessing attacks on WordPress sites. The peak day for the month was also much lower, at just over 30 million versus over 46 million the previous month.
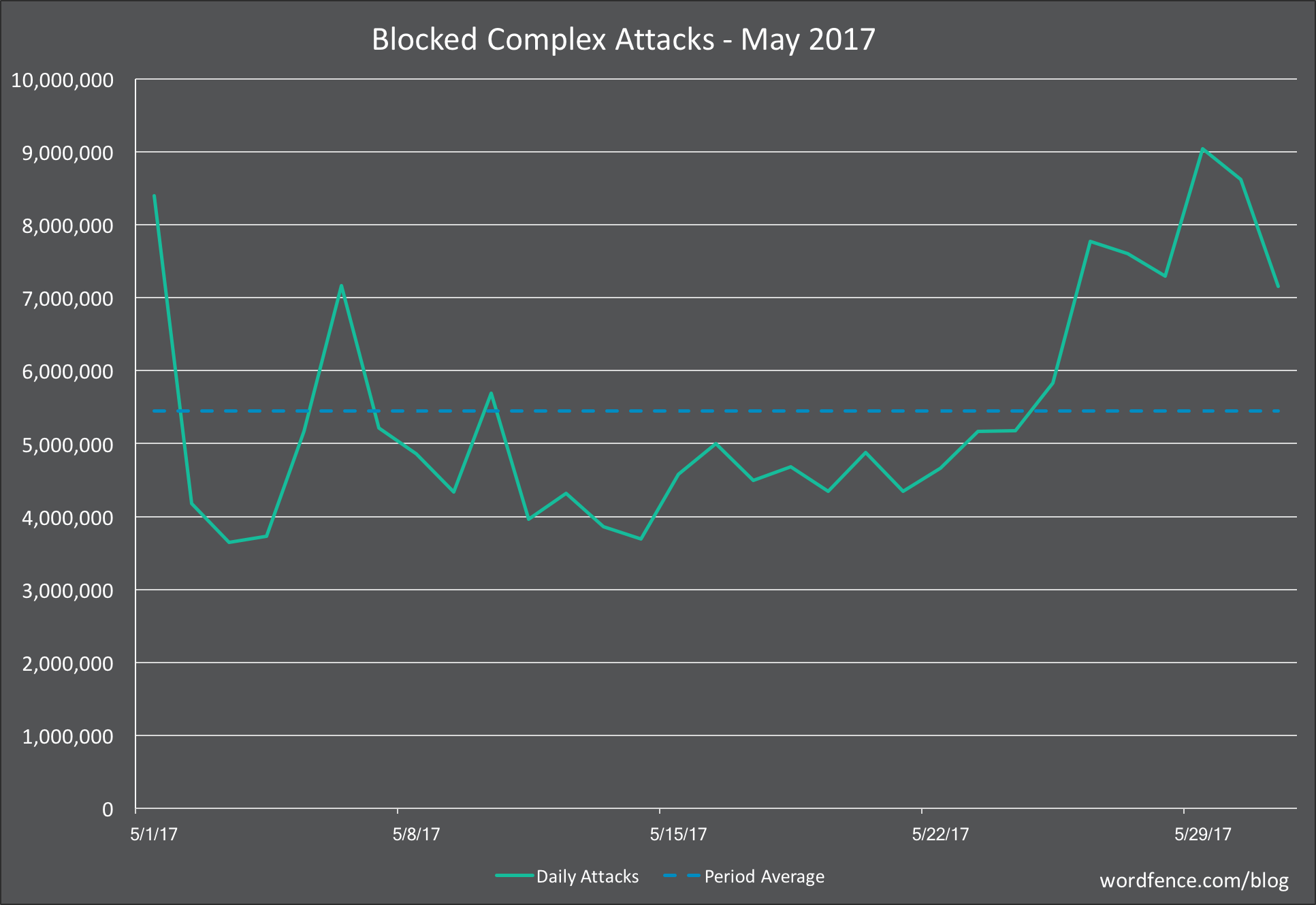
Complex Attacks on WordPress in May 2017
In the graph below, we show the daily complex attacks (attacks that attempt to exploit a security vulnerability) for May.
Average daily attack volume for May was down was down just 6% from April for the sites that Wordfence protects at 5.4 million.
Similar to April, we saw an uptick in volume toward the end of the month, peaking at over 9 million attacks in a single day.
Attacks on Themes in May 2017
The table below shows the total number of attacks on WordPress themes. We identify each theme using its slug, which is the directory where it is installed in WordPress.
There was quite a bit of change in the rankings from last month. Most notably, ypo-theme jumped 30 places in the rankings, going from number 34 to 4.
Based on a quick Google search, that theme doesn’t appear to be available for download anymore. There was quite a bit of content published in 2016 about an Arbitrary File Download vulnerability, so we took a closer look at the attacks to try to figure out what’s behind the spike in attack volume and to see if the two were related.
The first thing we noticed is that the attacks do appear to be attempting to exploit the Arbitrary File Download vulnerability we referenced above. Attackers attempt to download the wp-config.php file from the targeted sites. Secondly, the vast majority of attacks are originating from a small list of IP addresses. Almost 57% of the attacks are coming from 31.184.194.90, an IP from Saint Petersburg, Russia. Over 92% of all attacks are originating from just 10 IPs. We think it’s likely that the surge in attacks on this particular plugin vulnerability can be attributed to a single attacker.
Attacks on Plugins in May 2017
The table below shows the total number of attacks on WordPress plugins. As with themes, we identify each plugin by its unique slug, which is the unique installation directory where the plugin is installed.
Similar to what we saw with themes, the top 25 list for plugins had quite a lot of change. Ten plugins in the top 25 this month weren’t on the list last month. Most of those 10 jumped dramatically in the rankings this month. We took a look at the highest ranked plugin of the 10 newbies, sell-downloads, to see if we could figure out what is behind the increase in “popularity.”
According to WordPress.org, the Sell Downloads plugin has roughly 900 active users. There was a security vulnerability published in December of 2015 that impacts versions 1.0.16, but the current version of the plugin is 1.0.42, so we assume that vulnerability has been fixed for a long time.
We then looked at where the attacks were originating and discovered quite a coincidence: the same IP that was responsible for the surge in attacks on ypo-theme – 31.184.194.90 – was responsible for over 71% of the attacks on this plugin in the month of May. The top 10 IPs were responsible for over 95% of attacks on the plugin.
Attacks by Country for May 2017
The table below shows the top 25 countries from which attacks originated in the month of May on WordPress sites that we monitor.
Country rankings were very stable at the top of the list this year, as is frequently the case. There was quite a bit of movement toward the bottom of the list, but at relatively low volumes.
Conclusion
That concludes our May 2017 WordPress attack report. It was really nice to see the volume of brute force attacks down for the month. We hope that trend continues.

Comments
9:49 am
Thank you for the detailed presentation and analysis. Would it be advisable to place the list of IPs into the htaccess file as a list of arrivals to block?
Cemal
10:20 am
You're very welcome, Cemal! Glad you found it useful. To answer your question:
If you're a Wordfence Premium customer, there's no need to add the IP address anywhere - we've already blocked these IPs for you via the IP blacklist.
If you use the free version of Wordfence, these IP addresses will also be automatically blocked for you within 30 days of our adding them to the IP blacklist. However, you can add them manually (and permanently) right away by navigating to Wordfence > Blocking in your WP admin dashboard, and then entering the IP addresses one by one in the "You can manually (and permanently) block an IP by entering the address here:" field.
Either way, there's no need to do so via .htacess. Hope that helps!
12:15 pm
Thanks Andie, that is indeed an easier way than going into the htaccess. I am using the free version of WordFence and appreciate the service you are all providing. Thank you.
Cemal
10:26 am
Hi, thanks for giving us a wonderful information related to May 2017 WordPress Attack Report. this is really a good and knowledgeable article. Before reading it, I was not aware of these kind of attack.
Regards.
11:57 am
Whilst I understand the data in most of the tables, can I ask why the ISP's are not informed of the abuse and therefore stop them. Or are most of theses attacks working though a VPN and consequently hiding their true location.
12:53 pm
Great question, Geoff - it's one we get a lot, actually :) The reality is that thousands of IP addresses around the world are used to attack WordPress sites at any given time. The list of malicious or compromised IPs is ever-changing, and many of the ISPs are far from responsive when contacted about it. As we have limited resources, it's just not practical for us to report abusive IPs to ISPs on a continuous basis. Instead, we continue to invest our time and energy into improving the Wordfence product and educating the community on the size and scope of the threat and how to protect themselves. Hope that makes sense!
2:13 am
1. As a Premium customer I know that wordFence will block the IPs you list. Would it nonetheless be advisable for users to also block IPs thru cPanel to reduce the over-all hosting resource load BEFORE allowing the packet to reach the WordPress site?
2. It would be helpful to list the Theme & Plugin names in addition to their slug names.
Thanks for your good work.
8:41 am
Thanks Oran, and that's a good question. We don't really advocate blocking IP addresses through the cPanel or htaccess for a variety of reasons: it's largely redundant; it can (and frequently does) easily break websites; and most critically, that list of IP addresses needs to be managed by someone (e.g., you!) We have thousands of IP addresses on our blacklist at any given time, but they cycle on and off that list frequently because IP addresses change owners on a regular basis. Hence, an IP address that was blocked for exhibiting problematic activity last week may not have any problems this week.