PSA: Petya Ransomware Affecting Critical Systems Globally: Here’s What to Do.
Updated 3:19PM Pacific Time: A method to ‘vaccinate’ yourself against this ransomware variant has been found. I have posted details towards the end of the post along with a batch file you can run. It is as simple as creating the file C:\Windows\perfc and marking it read-only.
Update 2 at 7pm PST on Tuesday: It appears that the initial infection many have come from a company called MeDoc that was breached. Their systems were infected and they then pushed out an update, spreading the infection. MeDoc are disputing the allegation. Sources: Talos quoted on ZDNet, Forbes and FireEye.
This is a public service announcement from Wordfence due to the widespread and severe nature of this attack. A major ransomware attack targeting Microsoft Windows systems is affecting companies and systems, many of them critical, on a global scale.
What We Know
A new ransomware variant is spreading quickly across the globe at the time of this writing. There is no consensus yet in the security research community, so the following information is provisional in nature:
The ransomware has been dubbed “Petya.” It likely spreads by using two separate exploits. You don’t need to click on anything or take any action. This can spread into your system through the network. That is why it is having such a wide impact and why it is important that you update your system to protect yourself.
For the technically minded: This ransomware is exploiting a vulnerability in Microsoft Office when handling RTF documents (CVE-2017-0199). It also exploits a vulnerability in SMBv1 which is the Microsoft file-sharing protocol. This second vulnerability is described in Microsoft security bulletin MS17-010.
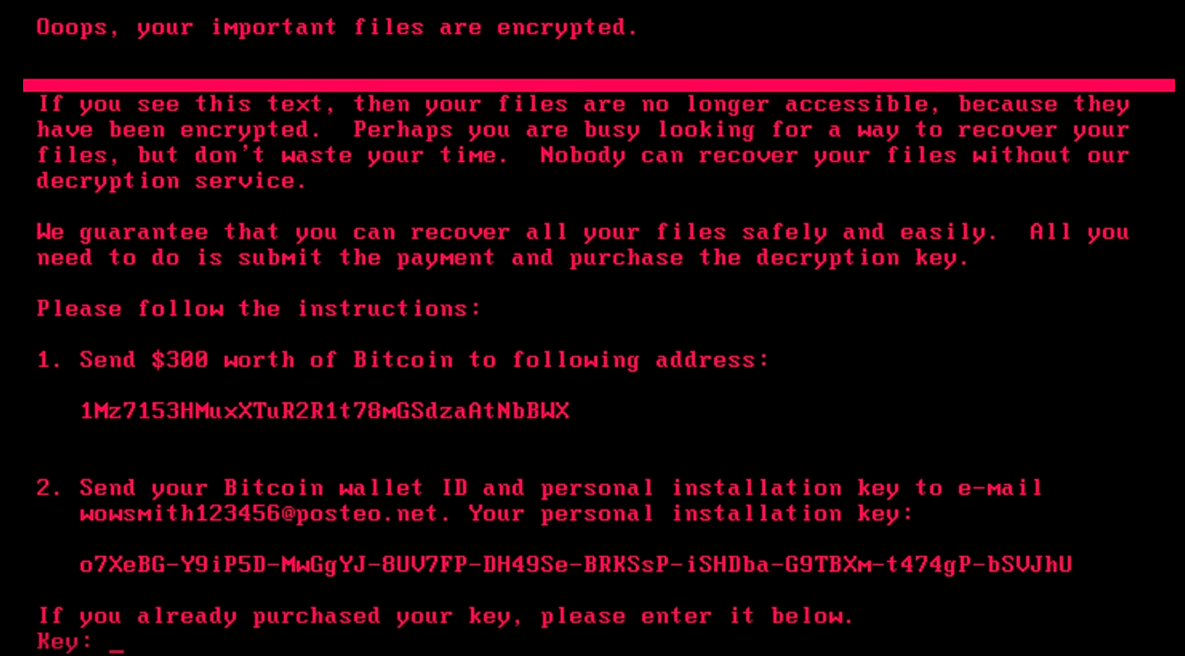
The ransomware has affected a large number of companies, organizations and government entities on an international scale. The following is a screenshot of the ransomware page you are confronted with once your files are encrypted:
Colin Hardy has provided a behavioral analysis of Petya, which includes a video demonstration of the malware in action:
What To Do
If you have not done so already, you should immediately install the MS17-010 patch from Microsoft.
If you currently run an unpatched Windows system, you may not have time to patch it before you are infected. Consider shutting down your machine, if feasible, and leaving it off the network until there is consensus in the research community on what this exploits and how to protect against it.
If you are technically able to, we recommend you block network access to port 445 on your Windows workstations. You may also want to monitor traffic to that port if you are a security professional.
Keep an eye on the Microsoft Security Response Center where they will hopefully release formal guidance soon.
Update your anti-virus definitions and run a scan on your system. You can find out which anti-virus products are detecting the current variant of Petya on this VirusTotal page. I’ve linked to one of the files involved in the infection. The page shows which AV vendors are currently detecting this file. The green check marks mean the file is not detected by that AV vendor (it’s counterintuitive).
Who This Has Affected So Far
- A Ukrainian state power company and Kiev’s main airport were among the first to report issues.
- The Chernobyl nuclear power plant has had to monitor radiation levels manually after they were forced to shut down the Windows systems that their sensors had been using.
- Antonov aircraft has reported being affected.
- Copenhagen-based shipping company Maersk is experiencing outages in multiple IT systems and across multiple business units.
- Food giant Modelez, which makes Oreo and Toblerone, has also been hit.
- Netherlands-based shipping company TNT was also hit.
- French construction company St. Gobain has been affected.
- Pharmaceutical company Merck says they have systems affected.
- Law firm DLA Piper was hit.
- Heritage Valley Health System, a US hospital operator, has also been hit.
- Kiev’s metro system has stopped accepting payment cards because they were affected.
The list is long and growing; the above just a snapshot.
Strong Incentive for Attackers
Many are reporting the belief that the South Korean hosting company that paid attackers a $1M ransom a week ago to recover their data have created a huge incentive for future ransomware attacks.
That has resulted in this new spate of attacks affecting systems globally.
Coverage of This Story
- Symantec analysts have confirmed Petya is similar to WannaCry.
- The BBC is providing excellent coverage.
- Catalin Cimpanu is, as usual, providing excellent coverage. He is reporting that Posteo, the email provider where Petya’s author is hosting an inbox to handle ransom responses, has just shut down that inbox. That means that if you have been hit, you can no longer contact the ransomware author to pay the ransom and your data may be permanently lost.
- Dan Goodin over at Ars Technica is also covering the story.
- Info is emerging in real-time on Twitter from security researchers.
- Thanks to TruStar for providing additional analysis.
Update 3:19pm PST: A Vaccine has been Found
In the past couple of hours researchers have found a ‘vaccine’ against having your files encrypted by this new variant of Petya. They discovered that if a file exists, the encryption routine will not run.
Amit Serper who found this had their findings confirmed by other security researchers.
To vaccinate a machine against this ransomware, simply create a file called perfc in the C:\Windows folder and mark it read only. The following batch file courtesy of BleepingComputer will do the job for you:
https://download.bleepingcomputer.com/bats/nopetyavac.bat
This post in BleepingComputer also includes instructions on how to create the file manually if you would prefer to do that. Once this file is created, the encryption routine for this specific ransomware variant will not run and encrypt your files.
Help Keep the Community Safe
We recommend you let your friends and family know about this fast spreading campaign as a matter or urgency to help them stay safe.

Comments
1:57 pm
I would also recommend reviewing this information as well https://kc.mcafee.com/corporate/index?page=content&id=KB89540
2:10 pm
Thanks Tom, great to hear McAfee is on top of this. Looks like you folks updated that article today and have detection for new IOCs related to this campaign.
2:00 pm
Most news articles I've read on this are calling it 'NotPetya' as it looks similar but isn't the same (coined by Kaspersky).
Not sure if that makes any difference but something that can protect against petya might not be effective against what's going on at the moment.
2:09 pm
Agreed Rob. I included that and then edited it out for some reason. Analysis on this is still ongoing which is why I'm nervous about giving specific advice other than applying the sensible patches and where possible shutting systems down.
2:02 pm
What about Mac systems?
2:08 pm
They are not affected.
5:56 pm
I have windows 10 | 64 bit and after reading this, I am still unsure what I need to do to protect my PC. You note that Windows 10 is not affected? Appreciate any help.
6:51 pm
It is affected. First line of the section titled "What to do?": If you have not done so already, you should immediately install the MS17-010 patch from Microsoft.
Link above.
8:14 am
I was confused about that - that patch is dated March 14 2017, and my Windows 10 tablet is up to date with updates. Does that include the patches, or are they extra installations?
2:06 pm
Is this affecting machines running Windows 10? My system is up to date and the patch was released in March. I don't see Windows 10 listed but I want to make sure.
2:06 pm
If anyone is interested in the address listed in the screenshot, here is the link:
https://blockchain.info/address/1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX
At time of writing, they have already made over 8k USD in less than a day, on this single address. It is probable, as with other ransomeware, that they have multiple addresses.
2:08 pm
Thanks WordFence. Always good to know you have our backs.
The easiest fix is to get a Mac. Done.
2:11 pm
LOL. Way to rub salt in the wound.
2:50 pm
Well, in the grand scheme of things, $300 is less than $2500, so I'm not sure about the whole "just get a Mac" thing. =)
2:54 pm
True that.
8:58 pm
Sadly in this case spending $300 won't buy access to any encrypted data, because even if the attacker had intended to unlock the data they no longer have access to email account they provided.
2:08 pm
Hmm...
Guess maybe incremental backups are too costly?
2:10 pm
If you have Windows 10 and auto updates, since this patch came out in March, should we be OK?
2:14 pm
I can't 100% confirm that you will be OK. As I said, analysis on this is still unfolding, but I'd say if you haven't installed the patch at this point, you're probably up the creek.
For Windows 10 users you can also turn off SMBv1 with the following steps. Turning off SMBv1 removes one of the main ways that this ransomware variant and WannaCry spread.
2:12 pm
If the kill switch being reported on Twitter is legit, you may want to update this post with that info.
2:18 pm
Looks like some progress was made, but it's not a @MalwareTechBlog style domain kill switch like the one in WannaCry. It's file based so is only a local kill switch which makes it not really that useful.
https://twitter.com/0xAmit/status/879806452818468864
2:22 pm
Except for the notion that some virus scanners have been updated, this kind of info is directed at techs who get excited about detecting such things. For us consumers, I suggest the following:
1. BIG emphasis on how it gets into one's system, the behaviors (clicking on socially engineers stuff, etc.) that allow this thing entry. Also a list of virus checkers that have been updated to catch/block this thing. This should be about 80% of your coverage.
2. Everything else you have here, such as what it looks like and what it asks for and if there is a known decrypt program/approach available.
Saying "Oh, oh, look there is a virus! See the screens! See how many are infected! ...." is not useful to the vast majority of customers. Ages ago, Subway put on all its sandwich wrappers to its customers: "1000 stores by 2000" or something like that. Wrong thing to the wrong audience.
2:36 pm
Thanks Bruce. We do our best. This was written by my co-author and I as fast as we could get the message out because it's time critical and I think we did a fair job all things considered.
Having said that, I added a link to VirusTotal where you can monitor which AV products detect this infection. The page is updated in real-time.
I've also added notes on how it spreads for a less technical reader and split out some of the more technical stuff.
Thanks for your feedback.
Mark.
2:47 pm
Appreciate this! Thanks for your efforts :)
2:50 pm
Thanks so much for the heads up -- much appreciated.
2:52 pm
I'll never understand the minds that create such evil. Sickening.
9:45 pm
Thank you for this. Your post made me take action to protect myself and others that are in my communities. Even though I knew about it early this morning because my wife got a text message from her company's IT dept not to boot up, I wasn't sure what to do until I got your email this afternoon. I really appreciate being a part of your list.
10:45 pm
Antivirus detect it and delete this ransomeware virus, but people still pay:
https://bitaps.com/1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX
Last transaction 15 minutes ago.
11:09 pm
Surely win10 auto updating with a decent endpoint security auto updating + 'cryptoguard' to point blank prevent any encryption even occurring is all thats needed to safeguard against this?
1:10 am
Hi All,
Thank you so much for posting nice articles. Is there any specific Inbound/Outbound TCP/IP protocols to be blocked to prevent this virus on Network?
5:08 am
Thanks, Mark and team. Great work. Your emails are incredibly helpful.
6:06 am
Hi - that perfc file - Wired is saying it should be a perfc.dat read only file - which is correct?
Thanks for your awesome coverage.
7:02 am
I do not understand the why of what they are doing in that article.
If they were creating a new blank text file and calling it "perfc" that would make sense to me.
However, creating a dupilcate of an executable file notepad.exe (any executable file) and calling it perfc makes me ask why?
The batch file seems to just create text files that have reminder text that it's a vaccination file in case you forget.
I haven't used a batch file since years began with 198_ so am I missing something?
The relevant part of the directions to do it manually currently say :
Once you see the notepad.exe program, left-click on it once so it is highlighted. Then press the Ctrl+C ( Ctrl+C Button) to copy and then Ctrl+V ( Ctrl+V Button) to paste it. When you paste it, you will receive a prompt asking you to grant permission to copy the file.
Press the Continue button and the file will be created as notepad - Copy.exe. Left click on this file and press the F2 key on your keyboard and now erase the notepad - Copy.exe file name and type perfc as shown below.
Now that the perfc file has been created, we now need to make it read only. To do that, right-click on the file and select Properties as shown below.
7:32 am
I'm not a big techie, but geek enough to try my best to keep an eye on it all. Your info is important to anyone who wants a secure computer, website and internet, for that matter. And that should mean everyone.
What I am most curious about is what security was in place at the alleged location of origin? What firewall and AV was already in place, if known. Not to cast aspersions but out of curiosity to see what they - the security software organization - is doing to prevent future occurrences. I should think they would take the lead to prevent it happening again.
My 2 cents.
8:53 am
Thanks! Did as suggested:
Turning off SMBv1
But do not understand what this really does. Can I just leave it disabled?
2:21 pm
So am correct in assuming that if you're windows updates are up to date that you are safe for this threat?
4:25 pm
It looks that way.