The October 2017 WordPress Attack Report
This month’s WordPress Attack Report is a continuation of a series we have been publishing since December 2016. Reports from the previous months can be found here.
This report contains the top 25 attacking IPs for October 2017 and their details. It also includes charts of brute force and complex attack activity for the same period, along with a new section revealing changes to the Wordfence real-time IP blacklist throughout the month. We also include the top themes and plugins that were attacked, and which countries generated the most attacks for this period.
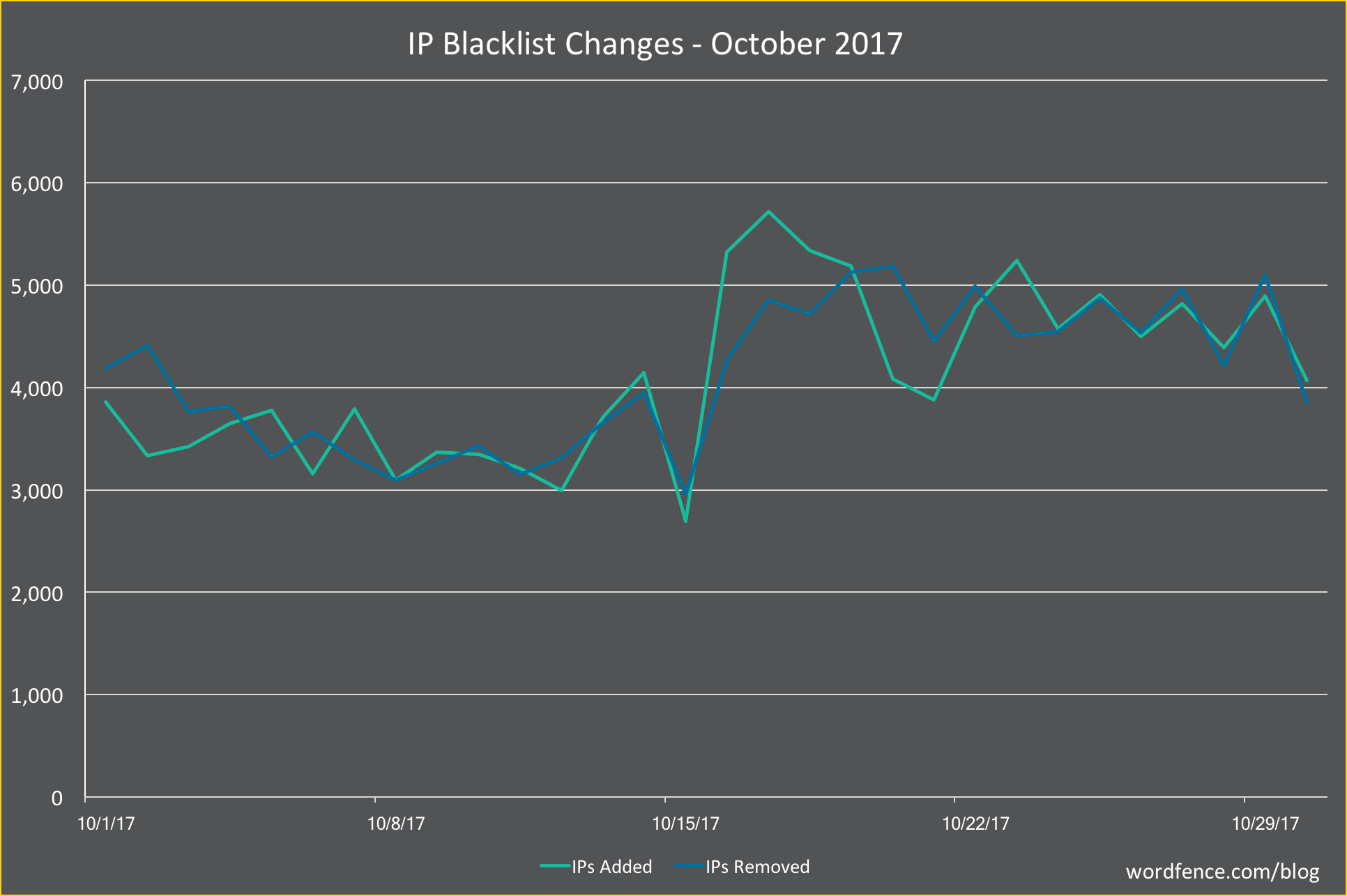
Real-time IP Blacklist
For the second month, we are sharing information on changes to the Wordfence real-time IP blacklist throughout the month. Sites protected by Wordfence Premium block all traffic from the malicious IP addresses that attack WordPress sites at any given time. In an effort to evade blocks by blacklists and manual blocking actions, attackers rotate through IP addresses constantly.
In the graph below, we show the number of IPs added to the blacklist each day in green and the number removed in blue. We added a total of 123,277 IPs during October, an average of just over 4,000 per day, up 5% from last month. That means that, on average, we added three new IPs per minute throughout the month. The number of IPs we removed was nearly identical.
The Top 25 Attacking IPs
The next section is our standard explanation of how the table below works. If you are familiar with our attack reports, you can skip down to the table below this section, which contains the data for October along with some commentary.
Brief Introduction (If You Are New to Viewing These Reports)
In the table below, we’ve listed the most active attack IPs for October 2017. Note that the “Attacks” column is in millions, and is the total of all attacks that originated from each IP. Farther right in the table (you may have to scroll right) we break down the attacks into “brute force” attacks and “complex” attacks.
Brute force attacks are login-guessing attacks. You can learn more about how brute force attacks work in our Learning Center article about them. What we refer to as “complex attacks” are attacks blocked by a rule in the Wordfence firewall.
We have also included the netblock owner, which is the organization (usually a company) that owns the block of IP addresses that the attack IP belongs to. You can Google the name of each owner for more information. A Google search for any of these IP addresses frequently shows reports of attacks.
The hostname included is the PTR record (reverse DNS record) that the IP address owner created for the IP, so this is not reliable data, but we still include it for interest. For example, we have seen PTR records that claim an IP is a Tor exit node, when, based on traffic, it is clearly not.
We also include the city and country, if available. To the far right of the report, we show the date in August when we started logging attacks and the date the attacks stopped.
The Top Attacking IPs
The total attacks from the top 25 attacking IPs were down 3% from September.
Brute force attacks made up 95% of total attacks for October, up slightly from September.
With 13 of the top 25 IPs, Turkey dominated the list for the second consecutive month. PP SKS-Lugan from the Ukraine once again dominated the very top of the list, hosting four of the most active malicious IPs.
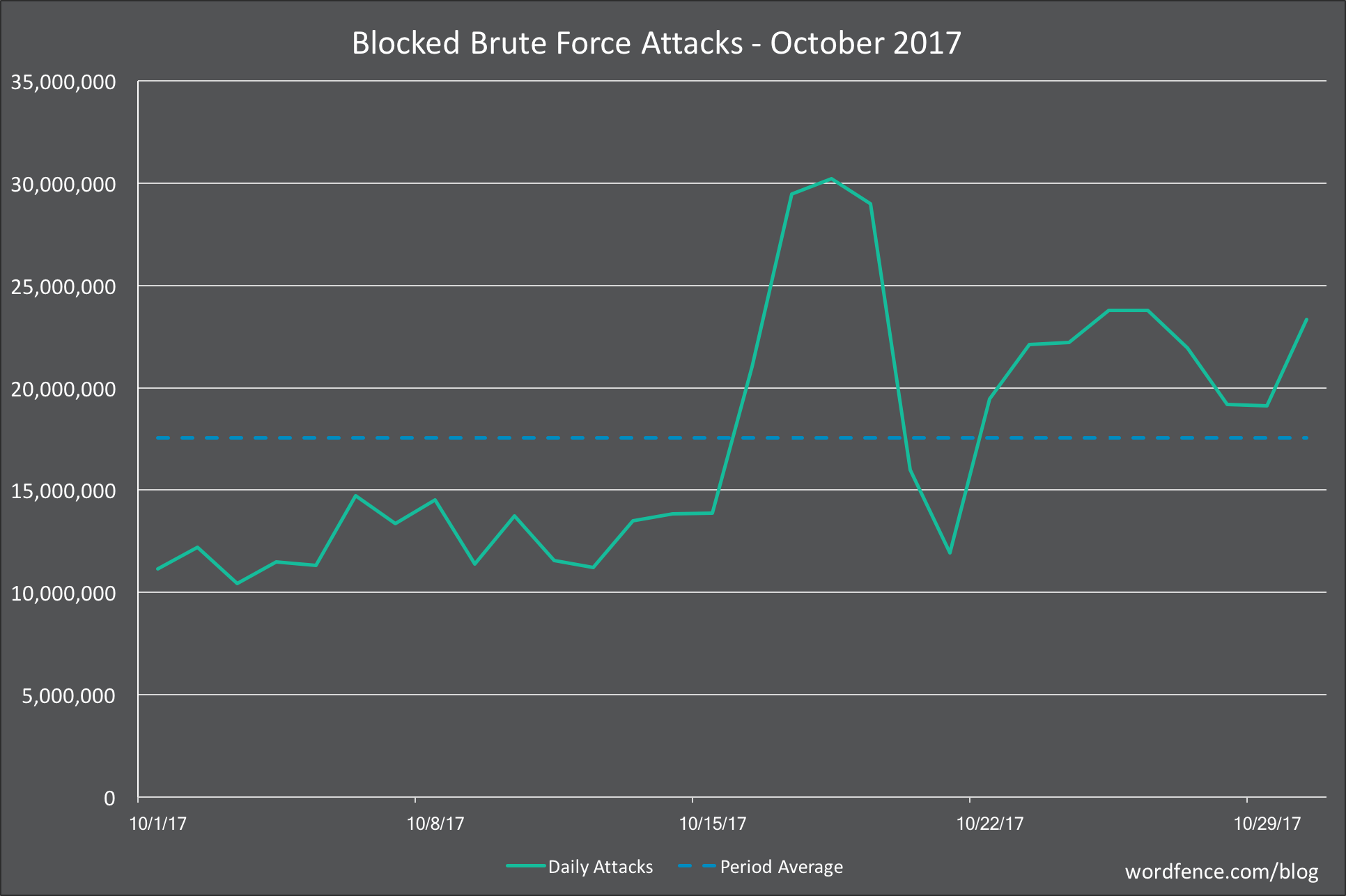
Brute Force Attacks on WordPress in October 2017
In the chart below, we show the number of daily brute force attacks on the sites we monitor for the month of October.
The average number of daily brute force attacks was down 9% from September. Daily attack volumes grew toward the latter half of the month, but remain very low relative to earlier in the year.
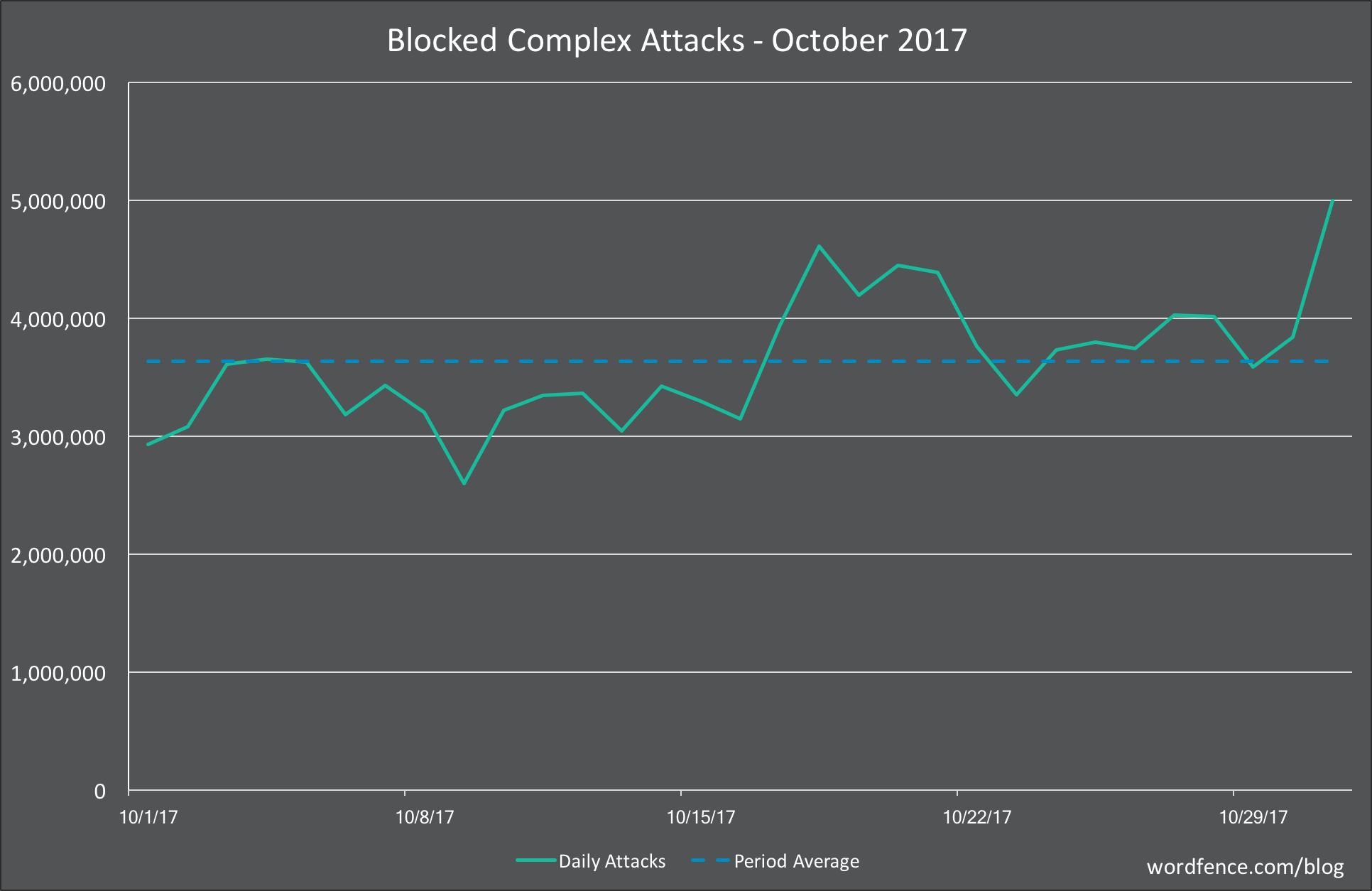
Complex Attacks on WordPress in October 2017
In the graph below, we show the daily complex attacks (attacks that attempt to exploit a security vulnerability) for the month of October.
Average daily attack volume for October was down 23% from September for the sites that we protect at 3.6 million. This marks the second month of declining attack volumes. Daily activity was relatively consistent throughout the month, with a slight increase in daily volumes toward the back half of the month.
Attacks on Themes in October 2017
The table below shows the total number of attacks on WordPress themes. We identify each theme using its slug, which is the directory where it is installed in WordPress.
There was a lot of change in the top 25 attacked themes in October as usual. The biggest mover was the ‘sketch’ theme, moving up 161 spots to number 22. None of the attacks that we looked at were attempting to exploit a security vulnerability in a theme. Instead, they appear to be either probing for the existence of malicious files that had been added to the theme or attempting to send commands to them.
The next two big movers on the list were the ‘twentyfifteen’ and ‘twentysixteen’ themes. The attacks on these themes follow the same pattern we saw with the ‘sketch’ theme.
Coming in at number 7 on the list is ‘template-parts’, which isn’t even a valid theme. Over 99% of the attacks originated from a single Latvian IP address. Based on the requests, it appears that attacker is attempting to probe for or send commands to malicious files in a directory that sounds like a legitimate theme file.
Attacks on Plugins in October 2017
The table below shows the total number of attacks on WordPress plugins. As with themes, we identify each plugin by its unique slug, which is the unique installation directory where the plugin is installed.
As usual, the top 25 list for plugins was very stable at the top, with almost no movement in the top 10. There were 8 plugins on the list that weren’t in the top 25 in September. We looked into the details behind the first big mover toward the top of the list, ‘Wp-LayerSlider’. As far as we can tell, this is not even a real plugin. It appears to be a name that attackers are using for a web shell that they are disguising as a slider plugin.
The next biggest mover on the list was ‘easyrotator-for-wordpress’. The majority of attacks on this plugin appear to be attempts to upload malicious files via any backdoor files that may already exist on a site.
The next to big movers on the list were ‘shortcodes-ultimate’ and ‘wp-filemanager’. The large majority of attacks on both plugins are attempts to exploit an old vulnerability in timthumb.php. Any sites that are running updated versions of these two plugins should be immune to these attempts.
Attacks by Country for October 2017
The table below shows the top 25 countries from which attacks originated in the month of October on the WordPress sites that we monitor.
The top of the list was pretty stable, with Russia and the United States holding their spots at first and second place, respectively. China, Ukraine and Turkey all remained in the top 5, though in different spots than the previous month. Latvia was the biggest mover on the list, climbing 52 spots to number 16 overall.
Conclusion
That concludes our October 2017 WordPress attack report. We were very pleased to see drops in complex and brute force attack volumes once again, potentially marking a trend. Regardless of the volume of attacks, WordPress website owners should not let their guard down, but instead stay vigilant about their site security with up-to-date firewalls and other security best practices to keep their sites safe.

Comments
11:52 am
Thank you for this, it is great information. I have taken the 25 top IPs and added them to my blocked IP's list. For the ones in Kansas City, do you report them someplace? I thought this was considered illegal in the US. Thank you again.
12:30 pm
I notice that the The Top Attacking IPs are all IPv4. Are IPv6 addresses not included in the data?
12:43 pm
Hi Dan, we do include IPv6 addresses but none made the top 25 list this month.