PSA: Replace Your SSL/TLS Certs by Symantec, Thawte, VeriSign, Equifax, GeoTrust and RapidSSL
This is a public service announcement and a reminder to site owners. Google’s Chrome browser has already started the process of ending support for Symantec SSL/TLS certificates. This includes companies owned by Symantec including Thawte, Verisign, Equifax, GeoTrust and RapidSSL.
Chrome 66 is ending support for Symantec certificates issued before June 1, 2016 on the following schedule:
- The ‘Canary’ release already ended support for these certificates. It was released on January 20th, 2018.
- The Beta release for Chrome 66 will be released on March 15th.
- The Stable release for Chrome 66 will be released on April 17th.
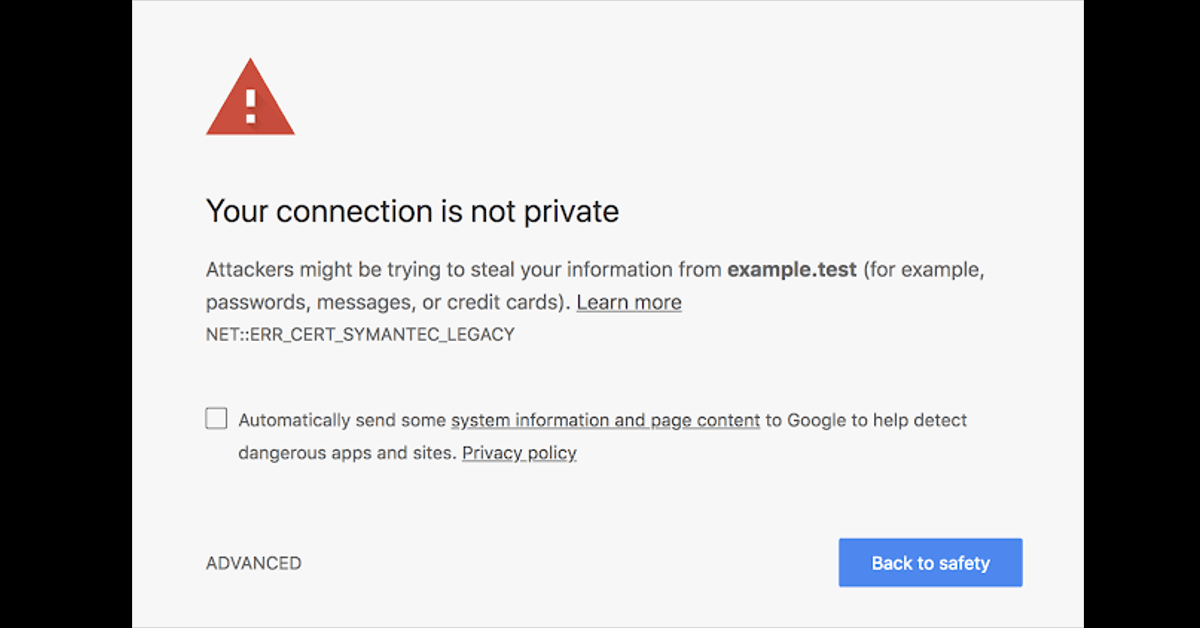
If you are running a Symantec certificate issued before June 1, 2016, and you do not replace that certificate, then from April 17th onwards this is what your site will look like to site visitors:
As you can see, the error is described as NET::ERR_CERT_SYMANTEC_LEGACY, meaning that your site is using a legacy Symantec certificate that is no longer supported.
Starting with Google Chrome version 70, all remaining Symantec certificates will stop working, including those issued after June 1, 2016. Chrome 70’s release schedule for Canary, Beta and Stable is July 20th, September 13th and October 16th respectively.
To check if your certificate will be affected by this change, you can visit this page and enter your website’s hostname in the form provided: https://www.websecurity.symantec.com/support/ssl-checker.
If your site will have an issue, the page should give you a warning. Make sure you just enter the hostname and remove the https:// prefix and the ending slash.
An alternative way to check if your website will have a problem is to download Chrome’s bleeding edge ‘canary’ version and visit your website. Then check the DevTools in Chrome for any warning message regarding your SSL/TLS certificate.
You can find more info on the official Google Security Blog.
Please help spread the word so that site owners are not caught by surprise when this change goes live next month.

Comments
5:52 pm
Why is Chrome/Google taking the step of distrusting the Symantec certificates? What's suddenly happened - the acquisition by DigiCert? - that prompts Google to say "these people cannot be trusted"? That's a rather forceful step to take, surely?
Thank you for the heads-up!
7:40 pm
Good informational article overall, however you neglected to explain any substantial background. In other words, why is this even happening? What is the problem with Symantec? Are other browsers not addressing the issue or is there a commercial problem between Google and Symantec?
Thanks.
10:57 am
Hi there,
Got a few questions about this. Much has been written on the subject. A few other commenters have provided links as background. Our goal with this post was to get the word out so that customers know they need to take action.
Mark.
7:45 pm
@Brad:
From Digicert'ss own website:
"New Chain of Trust
"DigiCert took over validation and issuance for all Symantec Website Security SSL/TLS certificates. This includes certificates for Symantec and its subsidiary CAs: Thawte, GeoTrust, and RapidSSL. Going forward, all new and reissued Website Security certificates are issued by DigiCert (using one of our trusted roots) and are trusted by Google Chrome.
"The new certificate chain DigiCert created does not interfere with your current certificate trust among browsers. The chain also establishes trust for your replacement certificate with Google Chrome (and other browsers) going forward.
Step 1: Make Plans to Replace Affected Certificates
To avoid Google Chrome browser security warnings about your SSL/TLS certificates not being trusted or secure, replace your affected Symantec Website Security SSL/TLS certificates before the appropriate date: March 15, 2018 or September 13, 2018, depending on when your certificates were issued. Make plans now and make sure to allow enough time for certificate issuance and for certificate installation.
"No Charge Certificate Replacement
"DigiCert will replace all affected certificates at no cost. Additionally, you don’t need to switch to a new account/platform. Continue to use your current Symantec account to replace and order your SSL/TLS certificates."
8:36 pm
Thanks for bringing light to the issue. Have several clients utilizing Symantec certs.
8:43 pm
The sale of their certificate infrastructure to DigiCert is a RESULT of them having been caught so badly managing their infrastructure that their certificates could no longer be trusted, Brad. They seriously screwed up and decided they couldn't recover trust properly themselves (and didn't seem to want to do the work) so they sold to a trusted infrastructure company instead. The decision to distrust all the certes was made by a consortium of browser and vendor companies, not just Google.
Quick note - you can test your own certificates simply by going into the current Chrome dev tools on your site. That already contains the warnings without having to download Canary. DO note though - you'll also potentially see warnings for certs for third-party sites whose assets you are loading. Nothing you can do about those except pressure the 3rd party and keep an eye on it.
8:48 pm
Brad, it's because Symantec delegated SSL issuing authority to other organizations, didn't have the necessary auditing controls in place, and basically, allowed the SSL issuing process to be abused by its delegates. And it wasn't the first time Symantec dropped the ball. The Chrome team finally threw in the towel on them and said "no more."
The SSL issuance process has to be trustworthy, or it's meaningless. If the issuing authority can't police itself, their certificates can't be trusted.
9:53 pm
You can follow the links in the article, but basically they (not for the first time) issued a bunch of bogus certificates. See https://groups.google.com/forum/m/#!msg/mozilla.dev.security.policy/fyJ3EK2YOP8/yvjS5leYCAAJ
12:52 am
I'm really puzzled by this sudden news too, Mark Maunder... I've followed you for a very long time - and I have a great deal of respect for the efforts and hard work you've applied to our field.
What gives here? Why did you NOT elaborate on the 'why's' and 'what happen's' here?
I know there are plenty more that would like to know - and while I'm very busy and haven't kept up on all the tech tabloids - I follow the ones that I find critical to my efforts - and you're in that list.
What gives? There's no stupid question - and I'm sure many more have the same question...
NOTE: Our hosting infrastructure is actually large enough that we issue and distribute our own SSL's - and the trend is appearing to move in this direction as a requirement for hosting service providers. So - for the 437K+ clients that have sites - we know they have certificates not impact by this. But what gives?
Thanks...
Hamilton...
10:54 am
There is quite a bit of background politics involved. Another commenter has provided a few links. I'm not really interested in the politics that much. We mainly wanted to get the word out that this is happening and if you don't react, you will be affected.
Mark.
1:20 am
Yes, that's my question too: WHY would Google end support for Symantec certificates? What does it mean and should people be encouraged to abandon Chrome?
1:43 am
Brad, If I remember correctly, there was a bit of a spat between Google ad Symantec, where Google accused Symantec of not following good secure practice with issuing certificates. For this reason they decided to remove the trust of the root certificates, but give long enough for anyone using one of the certificates to replace it with a newer one.
2:54 am
The reason for this distrust is well summarized in this post:
https://security.googleblog.com/2017/09/chromes-plan-to-distrust-symantec.html
In short, they had issues certificates that didn't comply with agreed-upon requirements, and certificates had been able to be issued without oversight.
3:09 am
Google is not taking the step because of the takeover, the takeover happened because of the Google taking steps.
Google is taking these steps because in the past, several severe incidents happened that proved that Symantec didn't take the necessary steps to ensure the sites they were issuing certificates for really belonged to the people requesting the certificates.
See https://security.googleblog.com/2017/09/chromes-plan-to-distrust-symantec.html
and https://groups.google.com/forum/#!msg/mozilla.dev.security.policy/fyJ3EK2YOP8/yvjS5leYCAAJ
5:44 am
Hello Brad,
Symantec can no longer be trusted and in my opinion this is long over due action.
You see Symantec has repeatedly, on multiple instances, issued SSL certificates to non owners of domains. This means people who wanted to spoof legitimate sites could acquire certificates for a domain not owned by them.
For example getting a SSL certificate for Wordfence.com when you don't own that domain. Then with phishing or other malicious actions one could trick people. Plus this whole action totally undercuts the system when a Certificate Authority (CA) is issuing rouge certs. It makes the whole SSL really TLS trust system suspect.
Google repeatedly warned Symantec and that company ignored Google. Then after several different occurrences Google said no more! Your certs will no longer be trusted. Right on Google!!! I just wished they moved faster.
Below is a link to an Arstechnica.com article titled: "Google takes Symantec to the woodshed for mis-issuing 30,000 HTTPS certs" that covers just ONE incident.
https://arstechnica.com/information-technology/2017/03/google-takes-symantec-to-the-woodshed-for-mis-issuing-30000-https-certs/
5:58 am
Brad, this has been announced for a while. It is the result of repeated cases of certificate mis-issuance incidents at Symantec and its partners/resellers over the years. Read more here: https://security.googleblog.com/2017/09/chromes-plan-to-distrust-symantec.html
6:17 am
@Brad:. Other way around. Symantec sold off their CA due to being distrusted.
Google announced their final plan almost a year ago, beginning the distrust process due to a constant and ongoing pattern of issues at Symantec, culminating in an incident that led to the misissuance of around 30k certs.
See https://security.googleblog.com/2017/09/chromes-plan-to-distrust-symantec.html?m=1 for Google's plan, and the link below for the list of CA problems brought up by the CA forum.
https://wiki.mozilla.org/CA:Symantec_Issues
For the same reasons as Chrome, Firefox is also distrusting Symantec certs, with final removal by October 2018.
6:18 am
Ummmm....and so what do we DO about this? Did I miss the answer to the problem you presented here?
10:49 am
Hi Angela,
Simply buy a new certificate. It's unlikely you'll find a company selling SSL/TLS certificates that are about to be revoked. So you can pretty much buy from whoever you like. But you do need to replace those legacy certificates.
Mark.
6:27 am
This is not sudden. It has been coming for some time now (at least June 2016 hence the start date). It is not the purchase by Digicert that is prompting this, its the other way around. This prompted the sale of Symantec cert business. Symantec had several partners that where not following proper procedures and where issuing certs that should not have been issued to the people they where issued to. There is another date coming in October when these will be distrusted entirely, not just pre June 2016 certs.
8:00 am
If we got our SSL certificates through our hosting, and the hosting company is not offering new certificates, how do we go about making sure that our new certificates are compliant?
10:51 am
Hi Brooke,
Now that the revocation schedule has been announced, it's highly unlikely that any company is going to be selling certs that are about to be revoked. Even Symantec/DigiCert have provided a tool to check if their own certs are going to be revoked.
So just go ahead and buy a new certificate from whoever you like and replace the legacy certificate and you should be fine.
Mark.
12:17 pm
As another resource, here’s a DigiCert page to help Replace Your Symantec SSL/TLS Certificates For Symantec, Thawte, GeoTrust, and RapidSSL: https://www.digicert.com/replace-your-symantec-ssl-tls-certificates/
Also, here's a Symantec/DigiCert FAQ about the whole situation: https://www.websecurity.symantec.com/en/us/digicert-and-symantec-faq
Hope this helps!
1:52 pm
Awesome, thanks Jarad. I've made those links clickable.
2:58 pm
I was wondering the same thing. Seeing as Symantec has historically been one of the leaders in internet security, it seems odd that certificates from them would no longer be trusted.
11:31 am
So I'm using 1and1 that issued me 25 GEoTrust certificates (which I guess are Symantec's?) which are recently installed and am told by the link Mark provided for checking them to "Upgrade by September 13, 2018". Hoping my server will not charge me again for this upgrade.
12:39 pm
There's no need to "buy" a new certificate as was stated in the comments above. DigiCert is replacing the certificates free of charge. For free replacement, use Jarad's links above.
2:36 pm
FWIW, The Electronic Frontier Foundation and LetsEncrypt are pushing an initiative to encrypt the entire World Wide Web, and it's been pretty successful so far. LetsEncrypt is issuing free SSL certs which are widely trusted. See https://letsencrypt.org/docs/certificate-compatibility/ for a list of browsers which will come with trust for these certs, and the few (mostly legacy) http clients which don't. Their list of sponsors, which you can view at https://letsencrypt.org/, is pretty impressive, and includes Google Chrome.