PSA: Highly Critical Drupal Core Vulnerability Impacts Over 1 Million Sites
Yesterday the Drupal security team announced a highly critical unauthenticated remote code execution vulnerability in Drupal core. The vulnerability allows an attacker to leverage multiple attack vectors and take complete control of a website. The Drupal team estimates that, at the time of the announcement, over one million sites are affected – about 9% of Drupal sites. They also reported that, to their knowledge, it was not being actively exploited.
We normally don’t cover Drupal vulnerabilities on this blog, but given the nature and scope of the issue, we felt compelled to help spread the word via this public service announcement (PSA).
Site owners should upgrade to a safe version of Drupal core immediately. While the reports of no active exploits are comforting, the announcement will draw a lot of attention from attackers. Given the nature of the vulnerability, there will literally be a race between site owners upgrading and attackers figuring out an exploit.
Here is a high-level summary of the versions impacted and recommended actions:
- Sites running Drupal 8.x should update to version 8.5.1
- Sites running Drupal 7.x should update to version 7.58
- There are patches available for 8.3.x and 8.2.x versions
- Sites running end of life versions will need to upgrade to a supported version of Drupal
A more detailed overview of upgrade recommendations from the Drupal security team is available on Drupal.org. They have also published a detailed FAQ.
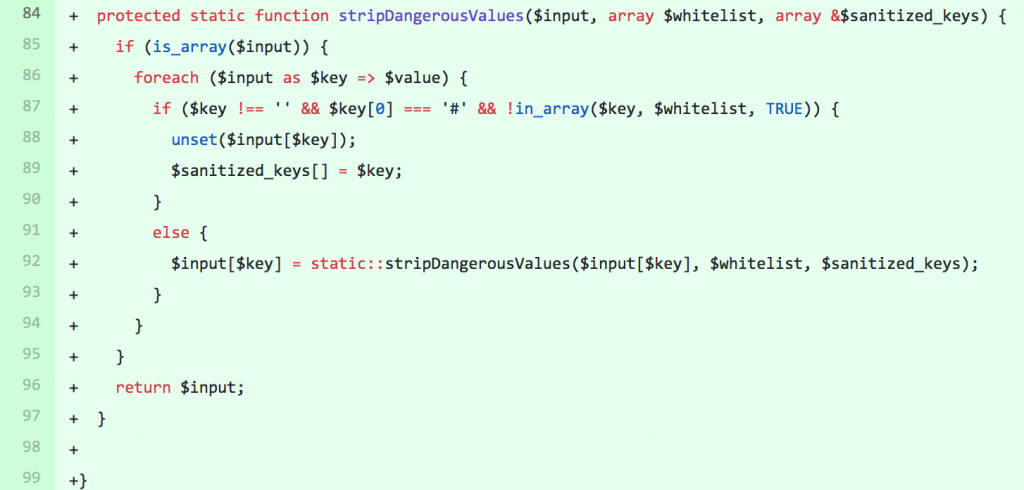
Looking at the diff of the patches provided by the Drupal team, they reveal a new DrupalRequestSanitizer class used to sanitize user input.
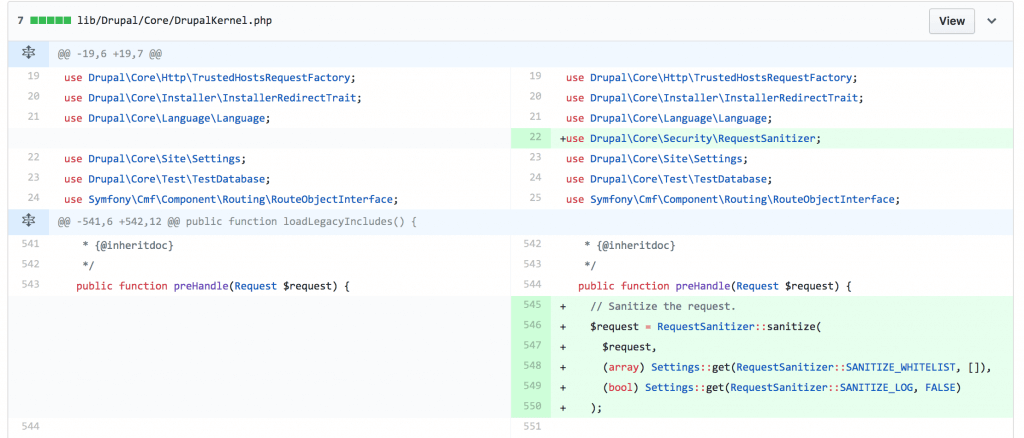
This class is used to filter values from the query string, post body, and cookies that begin with #.
A proof of concept demonstrating the attack has not yet been made public, but we expect that one will be made available soon.
This attack has been nicknamed “Drupalgeddon 2.” The previous Drupalgeddon was as high in severity as this, and had automated attacks against unpatched Drupal sites within a matter of hours after the public announcement of the vulnerability was made.
Please help us spread the word about this potentially nasty vulnerability to other site owners so they can stay a step ahead of attackers.

Comments
9:57 am
Great update, I have used drupal since v5 for certain projects. Drupalgeddon v1 was crazy with how fast it spread. Hopefully this will be updated shortly!
10:18 am
My client which uses Drupal and I were busy this morning looking at the mitigation’s in place. The simpliest was applying Drupal’s patch which you have highlighted. Guess a word to note is the change is very minimal so for companies with Production environments just before Easter this was quite a headache to fix.
My only question and probably good reason it has not been shown was why the ‘#’ has been removed in either a cookie or body/header query was what was the discovered exploit the researcher had found?
11:23 am
My host took the extraordinary measure of sending out a notification to all clients this morning to say that they proactively went through their servers and applied the patch to all sites using Drupal. I think that was a great move.
11:49 am
Excellent! Sure wish there were more hosting vendors that were this proactive.
Yes, perhaps it may affect some of their customers, but just like a preventative shot may cause extra redness and swelling for some, better to protect the larger community from much worse harm.
11:38 pm
Thanks for prompt info, great communication between you and our hosting that informed us. We will immediately update our Drupal versions.
12:59 pm
Thank you so much for getting the word out! I use Drupal in addition to WordPress, and wouldn't have known so quickly. You guys are first class!