BabaYaga: The WordPress Malware That Eats Other Malware
 Recently, Defiant’s analysts have been tracking a particularly sophisticated malware infection responsible for generating spam links and redirection, while still remaining relatively difficult for victims to detect.
Recently, Defiant’s analysts have been tracking a particularly sophisticated malware infection responsible for generating spam links and redirection, while still remaining relatively difficult for victims to detect.
Dubbed “BabaYaga” by our team, this infection is notable for containing code capable of removing its competition. BabaYaga actually has the ability to remove other malware.
While this malware isn’t brand new, it caught our attention with a wide array of features conducive to persistent infection. None of these countermeasures are groundbreaking individually, but taken as a whole they comprise a suite of functionality unusually comprehensive and effective for spam droppers.
In today’s post we are publishing a comprehensive white paper on the functioning and detection of BabaYaga. The paper includes a breakdown of the functions the malware provides, including its ability to maintain WordPress and detect and remove other malware variants. For our industry peers, we have included indicators of compromise in the form of YARA signatures, IPs and hostnames, in an appendix.
This accompanying blog post provides a summary of our findings for WordPress site owners.
The Payload
BabaYaga’s primary function is to generate spam content to be hosted on the victim’s site. These pages are loaded with keyword-heavy and meaningless word salad, designed to attract search engine traffic based on those keywords.
In the sample case we studied, the target market was a common one for spammers: essay writing services.
The payoff for these spammers comes in the form of affiliate marketing services. When a human visitor reaches an infected page of the site after following a link from a search, embedded JavaScript executes a malicious redirect to an affiliate site. Any purchases made at the destination site generate income for the attacker, and at that point it becomes a numbers game.
While the majority of our readers are probably savvy enough to identify a malicious redirect to a suspicious site and leave, a modest number of less-observant individuals would result in a respectable payout for the adversary.
Persistent Infection
As noted above, BabaYaga’s novelty stems from the use of a number of countermeasures, each with the intention of ensuring that it remains active on its host.
The infection’s primary files, responsible for generating spam content, each contain identical copies of the same code but obfuscated (hidden) with different techniques. This redundancy affords the attacker with some level of insurance that if one or more infected files are caught and remediated, there may still be more that went undetected.
These files feature a number of backdoor functions that can facilitate launching a complete reinfection if a single infected file is still present.

BabaYaga features a number of built-in backdoors, including this file uploader stripped from WSO Shell.
Some of the persistence features present in the BabaYaga infection include:
- “Phone-home” features, which allow the script to pull down new, potentially updated copies of itself from a control server.
- Two distinct file uploaders, used by attackers to manually upload arbitrary files to victims’ sites.
- Shared-directory spreading, automatically infecting multiple sites within the same parent directory structure typical to shared hosting accounts.
- WSO Shell, a popular and full-featured PHP web shell which gives an attacker access to a file manager, shell command execution, and more.
- Several instances of placeholder index files — the “Silence is golden.” files commonly found in theme and plugin directories — have arbitrary remote code execution functions injected into them.
Together, all of these measures give the attacker plenty of options to choose from to reestablish an infection, or make changes to the functionality of the infection itself.
Symbiosis
Because so much of the primary functionality of BabaYaga executes alongside WordPress on page load, it requires the application to be working properly. If something breaks WordPress, then the malicious scripts don’t get executed when a page is visited.
To this end, BabaYaga employs two features which would actually be helpful were it not for the malicious intent:
First, the malware includes features which the attacker can use to repair or upgrade the WordPress application software itself. It even handles the creation and cleanup of backup files, in the event that an upgrade fails.
Second, BabaYaga features more than one block of code used for rudimentary malware identification and removal. In other words, BabaYaga contains its own anti-malware feature to remove other malware that may break a site it occupies.
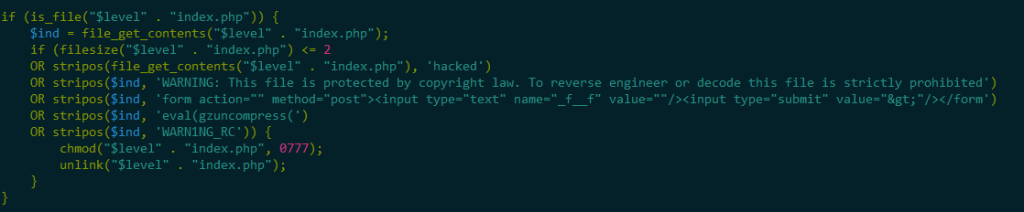
One example of code present in BabaYaga which can perform basic identification and removal of competing malware.
The rationale is simple: a good parasite wants to keep its host alive. If everything is up and working properly, the owner of an affected site can go without knowing anything is wrong indefinitely. However, if a less stealthy attacker finds their way in, or the site goes down for any number of other reasons, the site’s administrator will be forced to take a closer look at what is happening.
An admin investigating the site’s filesystem may stumble across an indicator of compromise, which obviously isn’t ideal for BabaYaga, so it does some housekeeping to avoid detection.
Further Reading
Due to BabaYaga’s complexity, this post serves as an overview of the infection. We have published a white paper containing a full report with indicators of compromise, written by Defiant Inc Senior Security Analyst Brad Haas.
Credits: BabaYaga whitepaper authored by Brad Haas. Editing by Sean Murphy and Michael Veenstra. Blog post authored by Michael Veenstra and edited by Mark Maunder. Design by Syndel Klett.

Comments
9:46 am
Never ending..!
I tried various plugins to protect my Wordpress sites when I started more than 10 years ago. I got hacked a few times but since I installed Wordfence I never had problems again.
Thanks to all for keeping our sites protected..
James
10:12 am
We detected yesterday an infection in WordPress of BabaYaga:
The attackers created a directory in wp-content/plugins/apikey with the files
apikey.php
header.php
login.php
newsleter.php
wp-layouts.php
wp-nav-menus.php
with malware code.
There were also other files in the WordPress root:
wp-domain.php
wp-main.php
wp-uti.php
wp.php
Do we send it to you to analyze it?
Thank you very much.
Best Regards
10:13 am
Thanks Jose. Yes, you can send it to samples@wordfence.com.
Regards,
Mark.
10:35 am
Thanks Mark:
I have sent an email with the attachments to samples@wordfence.com
Google blocks them, so I've sent you a link to download it. The link contains several zip files with php malware.
Regards.
10:47 am
Thank you!
11:36 am
Whoa! Two days ago, the song Hut of the BabaYaga from Emerson, Lake & Palmer's Pictures at an Exhibition popped into head while leaving work. I hadn't heard it in 20+ years, so I played it.
Hmmm, I better go check my website!
This is an ingenious malware that mimics some things in nature.
11:50 am
We are avid users of Wordfence, both paid and free. Thanks for sharing this article. Love the art that accompanies it but only one negative, please kern the Y. :-) If it makes it easier, we fixed it and feel free to grab/replace. Hope this doesn't rub anyone the wrong way, not the intention. https://www.stellarstudios.com/wp-content/uploads/2018/06/baba-yaga.gif
2:02 pm
LOL! Thanks Bill!!
3:15 pm
Way to go Team Wordfence.
I had a siteclean and upgrade to WF Premium 2 months back. I have used the free site for many years, BUT; for 2 bucks a week, why would anyone risk not having Wordfence Premium?
Keep up the amazing work. :-) Mike
6:41 pm
Thanks Mike!
12:11 am
So does the WF plugin protect again this threat?
9:08 am
Yes it does. Please see my reply to Daniel.
12:58 pm
We have the premium... does this insure we are not infected?
I check the live traffic and the blocked and the warnings regularly, and have blocked suspicious attempts... have blocked countries... some use VPNs though, and get through to attempt anyway.
Is there a way to prevent VPN users from other countries... or just block them like any other suspicious attempts???
9:07 am
Hi Daniel,
Premium has the newest firewall rules, released in real-time, that blocks any exploits that drop this malware - in addition the malware scanner for Premium has the newest signatures that detect every indicator of compromise mentioned in this report.
Our IP blacklist for WF Premium is continuously updated. New IPs are added and IPs that are no longer attacking are removed. If a VPN exit node is known for attacks, it'll be on our blacklist.
Mark.
7:05 pm
Thanks always for the great service and keeping an eye. redirections can be nasty when using 301 redirect. I was glad to move to a nginx server. I wonder what hackers think of wordfence, Have you detected any countermeasure attempts?