Analyzing a Week of Blocked Attacks
If you’ve never taken a few minutes to look at the information available in the Wordfence Live Traffic feature, I strongly recommend it. It gives you a detailed look at what attackers are trying to do to break into your site, and how Wordfence is blocking them.
For today’s post we analyzed all of the blocked attacks on Defiant.com for a week. In order to see them in Live Traffic, I simply selected “Blocked by Firewall” from the “filter traffic” drop-down above the data table.
What Attackers Were Up To
For the week there were a total of 223 attacks blocked. I was excited to see that all of them were blocked by the Wordfence real-time IP blacklist. We are used to seeing really high percentages blocked by our blacklist – usually in the high 90s. The real-time IP blacklist is a Premium feature that blocks all requests from IPs that are actively attacking WordPress sites.
Attacks originated from 14 unique IP addresses from around the world. Of the countries represented, Germany was the origin for the most attacks at 85. India was second with 61 and France was third with 45. Other countries represented were Ukraine, South Africa, China, Italy and the United Kingdom.
Next we’ll break down what they were trying to do to break in.
Reconnaissance
Five of the IPs appeared to just be performing reconnaissance, as they were simply requesting our home page or some other page on the site. They were likely just checking to see if the site was up and responding to their requests. Since all of the IPs were on the Wordfence real-time IP blacklist, their requests were blocked and they moved on after a couple of blocked page requests.
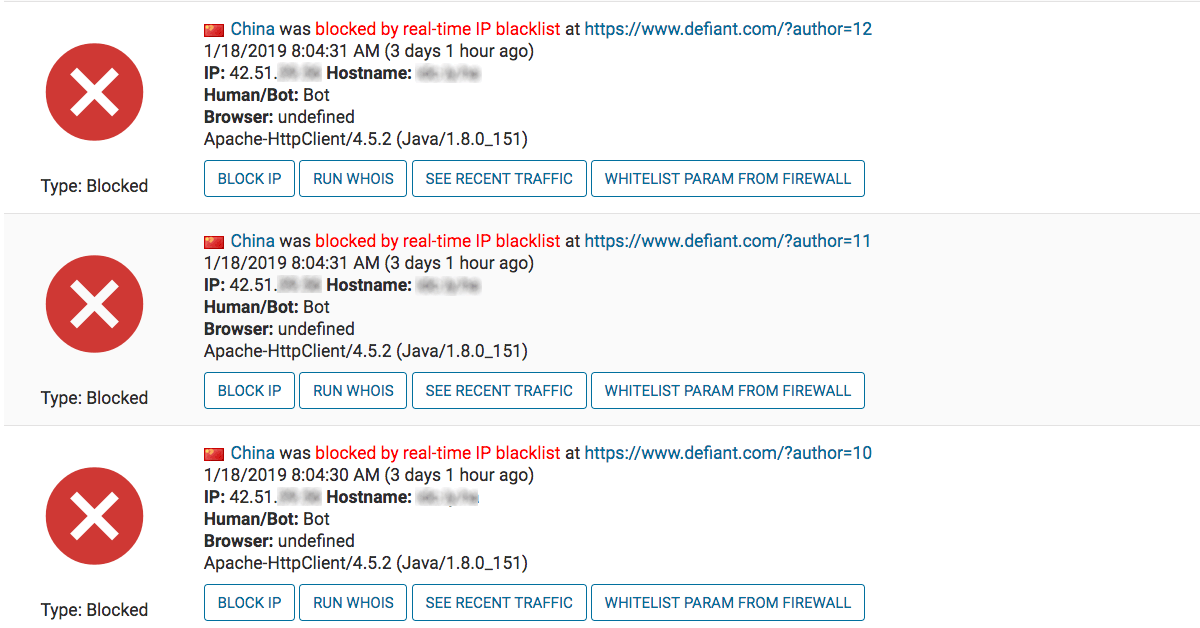
Author Enumeration
A Chinese IP attempted to retrieve a list of author usernames for the site. Since the authors of posts are very often also administrators, this information can significantly improve the odds of success for a brute force password guessing attack. The attacks all look like the following:
https://www.defiant.com/?author=1
The attacker worked through fifteen author numbers before giving up and moving on. In the Wordfence “Brute Force Protection” settings, look for the following option to enable this feature:
“Prevent discovery of usernames through ‘/?author=N’ scans, the oEmbed API, and the WordPress REST API”
Once you enable this, Wordfence will block these scans. This option is enabled by default and is available for both free and premium users.
We have blocked 382,131 attacks from that IP in the last 7 days across all of our customers. It seems quite likely that had the attempt to retrieve usernames been successful, attempts to log in using lists of common passwords would have followed.
Login Attempts Via XML-RPC
Sixty Three of the blocked attacks were attempts to log in to the site via the XML-RPC interface, which is an API developers can use to communicate with WordPress sites. We see a high percentage of brute force password guessing attempts hit this interface.
In our case we saw a single IP from Chennai, India attempt 61 login attempts in the period of just over an hour. Two other IPs, one in Hong Kong and another in Italy, made just one attempt each. They most likely moved on because they were blocked.
Login Attempts Via wp-login.php
We had just one IP attempt to login via the interface you use to login your site. The first attempt to login was followed immediately by an attempt to access our home page. The script was most likely checking to see if they were only being blocked from accessing the login page or the entire site. A second attempt following the same pattern occurred just two minutes later. We didn’t see additional attempts from that IP. I assume the attacker’s bot is programmed to move on if it’s blocked twice in a row.
A French IP Probes for Opportunities
A single French IP sent 43 requests in a 33 second burst. The first was a simple home page request, which I assume was an attempt to verify the site was up and accepting requests. Surprisingly the attack continued despite being consistently blocked by the Wordfence firewall. The following are a few examples of what the attacker was up to.
One request was checking for the existence of a known malicious file, commonly used by attackers to upload files to hacked websites. The request looks like this:
https://www.defiant.com/wp-upload-class.php
Another interesting request was looking for opportunities to exploit fresh WordPress installs, which we wrote about in July of 2017. Here’s what the request looks like:
https://www.defiant.com/wp-admin/setup-config.php?step=1
We also saw two attempts to find a copy of searchreplacedb2.php laying around. In July of 2017 we wrote about how hackers use the searchreplacedb2.php script to make malicious database changes. Here’s an example request:
https://www.defiant.com/searchreplacedb2.php
A German IP Probes for Opportunities
A single IP from Hirschfield, Germany attacked our site 85 times in just under two minutes. Most of the attacks were repeats of what we saw from the French IP. So it’s possible that it was a different bot at work for the same attacker. However, this IP also attempted to exploit a number of known theme and plugin vulnerabilities.
All of these attempts to exploit known vulnerabilities were trying to download the wp-config.php file, which is a WordPress file that includes the database credentials for the site. If successful, these attacks would give the attacker an easy route to obtaining administrative control of target website.
In one example, the attacker is attempting to exploit an arbitrary file download vulnerability in the “Epic” theme that was disclosed way back in 2014.
https://www.defiant.com/wp-content/themes/epic/includes/download.php?file=wp-config.php
In another, the attacker is trying to exploit a different arbitrary file download vulnerability – this time in the WP Hide & Security Enhancer plugin. The vulnerability was disclosed less than six months ago.
https://www.defiant.com/wp-content/plugins/wp-hide-security-enhancer/router/file-process.php?action=style-clean&file_path=%2Fwp-config.php
It’s important to note that we are not running any of the themes or plugins this attacker is attempting to exploit on Defiant.com. Many of the attacks on WordPress sites are what we often refer to as “spray and pray” attacks, where the attacker simply tries hundreds or thousands of exploit attempts hoping to get lucky. It’s likely that attack volumes are lower for Defiant.com because it’s protected by the Wordfence real-time IP blacklist. Like you, attackers don’t want to waste resources. If all of their attacks are being blocked they will move on to an easier target.
Conclusion
As you know, WordPress sites are under constant attack. There are many attackers, all of whom deploy different tactics. The free version of Wordfence includes protection for all of the attacks outlined above. For even better peace of mind, and likely lower attack volumes, consider upgrading to Wordfence Premium. For only $8.25 per month (billed annually) you can put the Wordfence real-time IP blacklist to work protecting your site around the clock.

Comments
9:55 am
Thank you for your valuable and accurate work. I use free version of your service. I am really happy in using your products in other 3 my owned web sites. I understand that upgrade to premium is a good investment for the site secutiry. I really MUST take care of your recommendations. Best regards Bernini Mentore
9:58 am
Hi Dan,
Thanks for walking me through this important post. Ever since I started using Wordfence to protect my website, I have seen marked improvement. I would like to ask if it is safe to block IP addresses that I find suspicious in the Live traffic panel. I usually get IP addresses that are blocked by Wordfence for trying to access non-existent pages on my website and the same IP addresses keep appearing from time to time.
Some of the pages include
/wp-json/wp/v2/users
/wp-content/uploads/2015/09/class-wp-upgrade.php
Thanks and looking forward to hearing from you.
10:54 am
Hi Abrokwa, we wrote a post focused on this question a little over a year ago: https://www.wordfence.com/blog/2017/11/should-permantly-block-ips/.
10:14 am
Hi, I had thousands of attempts to exploit a contact form in a website I manage from these IP: 80.240.26.205 / 80.240.21.91 / 104.168.201.2 / 104.168.201.236 / 104.168.203.122.
I also reported them to their ISP but hadn't any answer...
Did you also spot them?
Regarding the Wordfence network, I think you should not list dynamic IP of mobile users cause they create too many false positives. How long do you keep that kind of IP in your blacklist?
11:12 am
Hi Gabriele, if those IPs were just trying to submit spam submissions to a form on your site we would not pick up on that. If mobile IPs are actively attacking WordPress sites we will indeed block them. IPs roll off of our blacklist very quickly once they stop attacking.
10:20 am
Hello! Thanks very much for your work, appreciate it! My question is: what should I do to secure my website, if for example several people who had worked on the site probably still have wp-config.php file from it?
12:48 pm
Hi Alex!
The answer depends on what sort of custom configurations you may have added to that wp-config file. For any case, you'll want to change the credentials for your database connection and generate new salts with this tool.
As far as other custom changes go, the most common would be hard-coded FTP_USER and FTP_PASS definitions, which would allow someone to upload potentially malicious files to your site. Those credentials would need to be changed immediately when someone is removed from the project.
Mikey
11:04 am
I have Wordfence Premium and love it. I see a weekly email filled with lists of thwarted attackers. Compared to the cost of sorting out a hacked site, the fee is negligible. The support techs are genuinely good people who care about both my website health and ensuring their product performs on it. I have absolutely no technical knowledge but they don't treat me like a moron. I'm sticking with them.
11:13 am
Thanks Katie! :-)
1:37 pm
Thanks for the great work you do. We use your product in our site. The amount of attacks has gone to the minimum, given that attackers have realized that their efforts are futile!
3:38 pm
Have always wondered why these people don't go offer their services on Fiverr and make a living doing productive work. Thanks to Wordfence for keeping our sites safe.
1:26 am
Hi,
I use Wordfence for some years now and for every web project, I have to do with. It is great and the peace of mind is worth the Premium fee.
Also, the support is great, these guys implemented a weird functionality into the Premium license which I use for my staging sites.
Keep up the good work and don't get the idea to sell the business.
Best regards
5:11 am
Thank you for being a firewall of the WordPress for years. WordPress without wordfence is nothing for me. Thank you once again.