A Tale of Two Vulnerabilities: Using Commercial Plugins Responsibly
As the most popular CMS on the market, one of the major draws of WordPress is a rich ecosystem of plugins made available by the community. The WordPress.org plugin repository makes the process of installing and updating plugins a seamless experience in the dashboard of a site, and a team of volunteers works to maintain the repository as new plugins are submitted and abandoned ones fade away.
The official repository is just one of many places where a site owner can find plugins, though. Since any plugin made available in the WordPress.org repository must be free, third-party marketplaces are a common source of commercial plugins and themes that don’t need to follow the same rules. Some plugin developers even choose to sell their software from their own sites, without involving a marketplace in the transaction.
These third-party sources can be an excellent way to find well-supported commercial plugins for a new WordPress site, offering features that may not be common among free alternatives. However, these sources lack some advantages inherent to the official WordPress.org repository that can cause issues for unaware site owners over time.
In the following post, we’ll be taking a look at two recent examples of security issues in plugins sourced from outside the official plugin repository that are currently being exploited. We’ll also go over some best practices for using commercial plugins responsibly in order to keep your sites secure in the long term.
UserPro Plugin Flaw Allows Administrator Registration
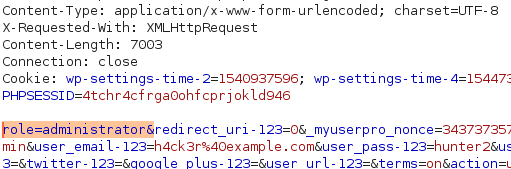
In a proof of concept exploit published this month, it was revealed that versions older than 4.9.21 of the commercial plugin UserPro contain a security flaw allowing new users to register themselves with Administrator permissions, granting them control of affected sites.
By manipulating the account registration form on a site, or by intercepting and editing requests from a standard form, attackers can add a role parameter to their registration submission. The plugin will accept this input and assign the chosen role to the newly created user. With a newly created administrator account, an attacker can upload a malicious plugin or undergo other nefarious activity freely.
This flaw was patched in March of 2018, but we’re still seeing active exploitation of vulnerable versions. This highlights one major concern with introducing off-repository commercial plugins: updates.
When a plugin is available on the official repository, WordPress is able to keep track of the version present on your site and compare that to the latest available version. When an update is available, users receive notifications in their dashboard and can issue the update directly from there. In extreme cases of critical vulnerabilities, the repo’s maintainers can even flag vulnerable plugins to automatically update.
Commercial plugins generally lack these protections, as it would rely on the developer to maintain their own repository for all installed copies of their plugins to test against. Updating a commercial plugin often involves manually uploading a new copy, which less-savvy users can be hesitant to do. This also assumes users are periodically checking in on the development process of each of their installed plugins to even become aware that an update is necessary. Since many sites are built by a developer and handed off to the owner to maintain, these owners may not have any idea these extra steps are necessary at all.
In the case of this UserPro vulnerability, we’ve developed a firewall rule to prevent attackers from defining their own role when registering an account.
Social Network Tabs Plugin Leads To Twitter Hijacking
In a full disclosure published on Twitter and later reported by TechCrunch, security researcher Baptiste Robert detailed a flaw in Social Network Tabs which leaks private access tokens associated with a site’s Twitter account.
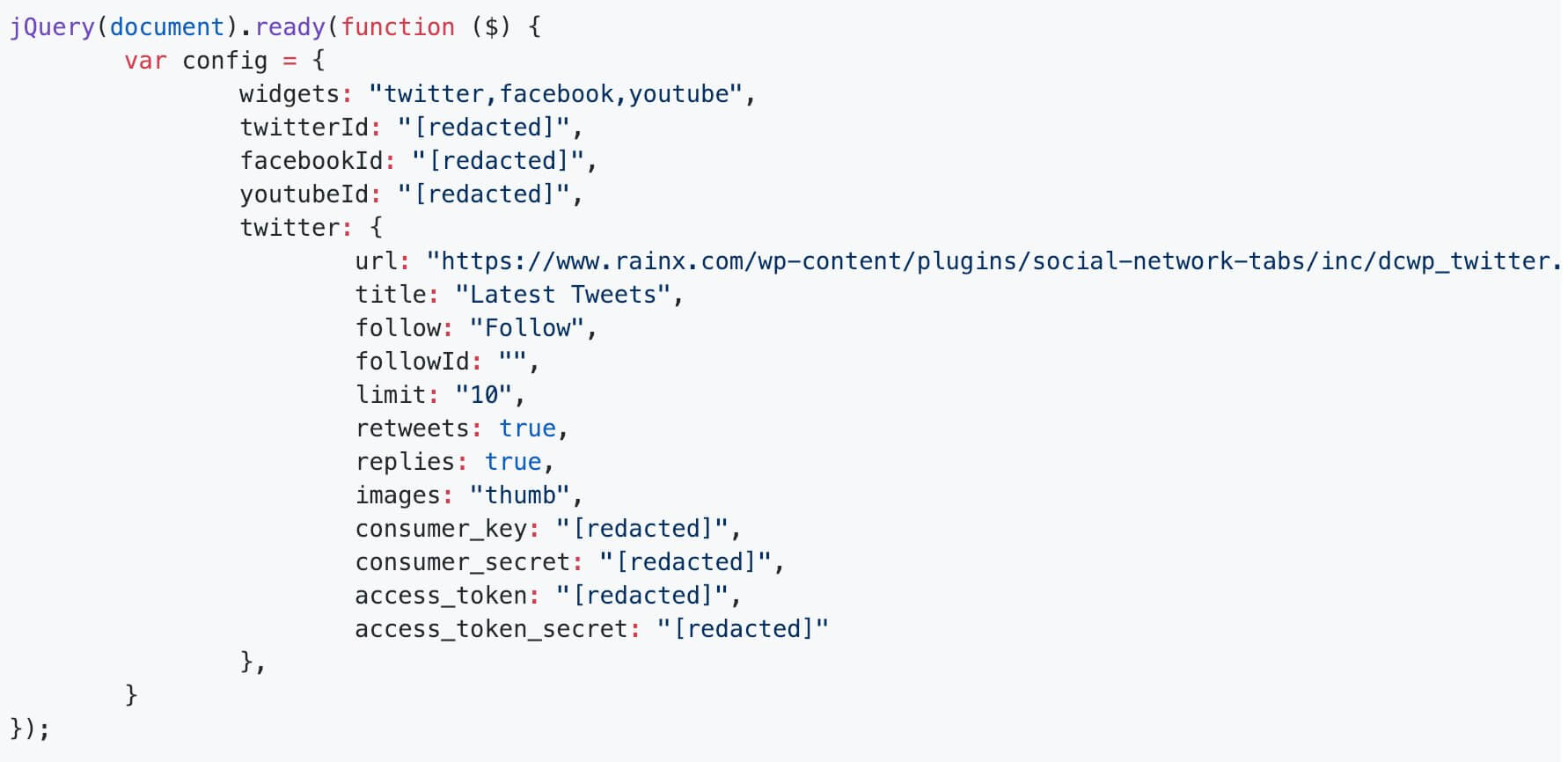
jQuery snippet from an affected site. Source: https://twitter.com/fs0c131y/status/1085828997013954560
This flaw has not been patched and its latest available version remains vulnerable. In this case, it’s possible a patch isn’t coming. Neither the plugin itself, nor the developer’s blog, have been updated in over five years. On the bright side, Robert has worked with Twitter to identify as many affected accounts as possible in an attempt to mitigate the impact of this data exposure.
When a plugin on the official WordPress.org repository is abandoned, there are policies in place to allow new developers to pick up where the former ones left off. Even when they’re not taken over, solutions like Wordfence can identify when a plugin has been abandoned and alert site owners of the problem so it can be addressed.
Unfortunately because this sensitive data exposure requires no input from abusers, it’s not possible to protect affected sites with a firewall rule. For affected users, it’s highly recommended to discontinue use of the Social Network Tabs plugin and look into alternatives. Twitter has been made aware of a number of leaked access tokens and has revoked them for the safety of their users. but affected users should immediately change their Twitter passwords and review their accounts for suspicious activity.
Conclusion
Third-party marketplaces, as well as developers who self-publish commercial plugins, can be a great source of software for people to add to their WordPress sites. When using these unofficial sources, though, site owners need to remain mindful. These plugins often won’t alert users when an update is available, so even vulnerabilities patched by the software vendor can remain present on sites for a considerable amount of time. Also, when checking your commercial plugins for updates, remain aware of how long it’s been since the last patch. If a plugin hasn’t seen an update in a year or more, consider finding a better-supported alternative.
The UserPro plugin vulnerability has received a firewall rule to block attacks on sites behind the Wordfence WAF. Wordfence users with Premium licenses will have received this new rule by the time this post is published. Free users will gain access to the rule after a standard thirty-day delay.
Thank you for reading, and please consider sharing this article to raise awareness of these vulnerabilities as well as the best practices for using commercial WordPress plugins.


Comments
9:34 am
Another issue that has happened on wordpress plugins is a plugin developer has a well established plugin with several 5 star reviews and then sells it to a hacker and now the hacker is inside your site. This has happened to 2 different plugins I used. Fortunately I was able to catch it quickly and remove the plugin.
2:32 pm
Wow!
5:29 pm
Perhaps if you name the developer, we can avoid any of his/her future plugins? If a plugin developer is going to sell their products, they should check what's it will be used for? Or Wordpress could set up a user accessible database of products that has had a change of ownership? Of course, privately sold products (non Wordpress repository) will need to be regularly checked by the user for change of ownership.
6:25 am
PLS name them so we can stay away.Thank You
9:47 am
Many thanks for the important informations
9:49 am
Good article! Best advise - due diligence when choosing a plugin - especially when it's outside of the WP repository. Look at reviews, prior works of the author and (very important) lag time on support requests.
11:38 am
Good points in this article, but I have to say that commercial vendors generally do their utmost best to deliver safe plugins. After all, they are responsible for the product they sell, unlike free stuff. Secondly, support is generally much better than on free plugins.
I agree with Jimmy B that a long standing reputation and response time of support questions is a good indicator of a trustworthy plugin developer.
11:03 pm
Always check the complete plugins no matter where you get them from but especially if you get them from sites like Envato and their daughters or other "seller" sites. Often those plugins also send data without asking for permissions which is a general GDPR issue. Beside that we realized that many plugs and especially Theme developers leave tons of their private emails and even login details in their sites which will make your site after you have imported i.e. demo content - always check those xml.s and replace @ with @something as a small precaution.
2:12 am
Thank you for this information. I always check the reviews of other users before deciding whether to use a plugin or not. The disadvantage of this is missing out on a really good plugin that hasn't gathered enough reviews.
3:51 am
Great article! Thank you for sharing these points as they have helped me understand your blog better. Your writing skills make things extremely clear, while I was reading the article I felt as if someone was teaching me, everything is explained very well. Kindly share more write-ups as these help us a lot and such articles add on to our knowledge. Thank you!