Widespread Attacks Continue Targeting Vulnerabilities in The Plus Addons for Elementor Pro
Over the past 10 days, Wordfence has blocked over 14 million attacks targeting Privilege Escalation Vulnerabilities in The Plus Addons for Elementor Pro on over 75% of sites reporting attacks during this period. By April 13, 2021, this campaign was targeting more sites than all other campaigns put together.
Number of sites attacked per day
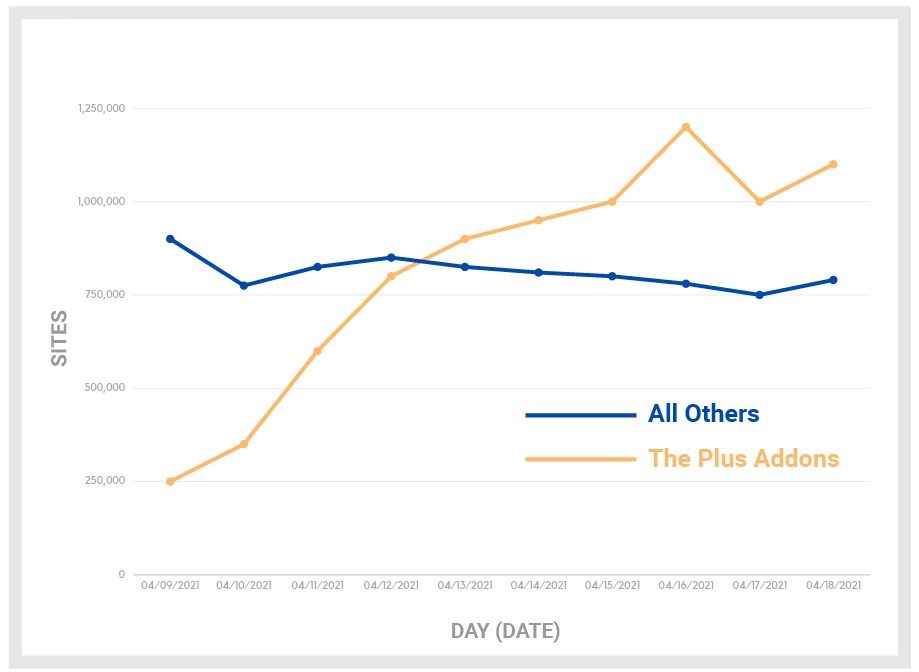
Despite only having an estimated install count of roughly 30,000 sites, nearly 60% of which should now be running a patched version of the plugin, over 2.8 million sites protected by Wordfence have been targeted by this campaign since April 8, 2021. It is likely that these numbers are reflected by the larger WordPress ecosystem as a whole and that millions of sites that are not protected by Wordfence are also being attacked.
The original vulnerability was already being actively attacked when it was reported by hosting company Seravo, making it a 0-day at the time. This vulnerability allowed attackers to login as an administrator or to create new administrative accounts on any site with the plugin installed. While analyzing the plugin, the Wordfence Threat Intelligence team found additional vulnerabilities and notified the plugin’s developer. A firewall rule protecting against these vulnerabilities was released to our premium users on March 8, 2021, and became available to free users on April 7, 2021.
Note that this is not the same vulnerability as the widespread Contributor+ XSS vulnerabilities in various Elementor Addon Plugins that we recently reported on, though this plugin was impacted by those vulnerabilities as well.
A Familiar Attacker Ramping Up For Spring
These attacks are part of a broader pattern we’ve seen of attacks ramping up during the spring. The vast majority of recent attacks appear to be brute force campaigns or campaigns targeting older vulnerabilities. The second most widespread attack campaign in the past week is targeting a vulnerability in Slider Revolution that was patched in 2014, as well as a few more attempts to extract sensitive information from website wp-config.php files. More and more recent attacks appear to be unfocused, which may indicate that the infrastructure used to perform attacks has become less expensive for attackers to operate.
This campaign is notable in that it is targeting a recent vulnerability and, therefore, has a higher chance of success than the other campaigns we’ve seen recently. We estimate that at least 10,000 sites are still vulnerable. It is also unusual in that it is a set of sustained attacks, whereas attack spikes we’ve seen in the past have typically only lasted a few days before subsiding. This may indicate that attackers are maintaining control of the hosts used to perform attacks for longer, or they are less worried about maintaining a low profile.
Especially troubling is the post-exploitation addition of JavaScript performing malicious redirects. We believe that the threat actor attacking these vulnerabilities is the same one that we reported on last year due to the scale of the attacks and the post-exploitation MO. While other attackers with similar capabilities have emerged since then, the redirect chain and fake “statistics” patterns used in the redirect domains are strong indicators that this is the same attacker.
Indicators of Compromise
We have been closely monitoring the attack data associated with the ongoing campaign along with monitoring our site cleanings that come in as a result of this vulnerability. If your site has been compromised, and you know you have the plugin installed, the following are some of the common indicators of compromise that we are seeing.
Common Email Addresses used for Registration
test@example.com – Nearly all of the attempts we’ve seen are using this email address for newly generated admin users. We have blocked over 14 million attempts to register with this email address while attempting to exploit the vulnerability.
Top IP Addresses we have blocked trying to exploit these vulnerabilities
These attacks have been surprisingly concentrated, with only 38 IP addresses collectively responsible for the majority of the attacks. Each of the following IP addresses have attacked more than 10,000 sites on our network.
208.110.85.68173.208.246.46173.208.246.43198.204.240.24251.15.146.61192.151.156.18863.141.251.237107.150.59.245208.110.85.70107.150.52.19669.30.225.10169.197.185.132192.151.156.190107.150.52.198192.151.156.189107.150.63.173107.150.63.17269.197.185.13369.30.225.98198.204.240.246107.150.52.197107.150.59.24363.141.251.238107.150.59.230192.151.156.18763.141.251.23569.197.185.131107.150.59.246107.150.59.229107.150.60.36107.150.60.37198.204.240.244173.208.246.45107.150.59.244198.204.240.245198.204.240.243
Domain Names we have found injected in infected site databases.
hXXps://store.dontkinhooot[.]tw/stat.js
Code sample we are seeing injected into JavaScript files.
Common Malicious plugins we are seeing installed.
/wpstaff/wpstaff.php/wp-strongs/wp-strongs.php
Please note that you may not be able to see these installed plugins listed on the plugin page as they may include code that hides them from your site’s wp-admin dashboard. It is important you check for the presence of these plugins by accessing your sites file system under the /wp-content/plugins directory.
What Should You Do
If you haven’t already updated The Plus Addons for Elementor Pro, then we highly recommend doing that immediately to ensure your site is protected from compromise.
If your site has been compromised due to this vulnerability then you have a few options to restore your site.
Option #1: Restore from Backup
This is the simplest way to restore your site if it has been compromised. By reviewing your site’s logs and Wordfence Live Traffic, you may be able to determine the initial date and time of the infection. Once you have determined the initial date and time of the infection, you will want to choose a back-up that is older than the time of infection.
If you are unable to determine the initial date of compromise to choose a viable back-up to restore from, then we recommend restoring your site from that back-up older than March 1st, 2021. Once you have restored your site from the back-up, then run a high sensitivity Wordfence scan to verify that no remnants of malware remains on your site. In addition, once you have finished restoring from a back-up, be sure to update all of your plugins and themes immediately after restoring a clean copy so that your site doesn’t get reinfected by the same vulnerability.
Option #2: Manually conduct the cleaning of your site
If you do not have a back-up of your site, then you may need to manually conduct the site cleaning yourself.
We covered how to clean a site that has been compromised by The Plus Addons Elementor hack on Wordfence Live, Tuesday March 16th. You can watch this video for a step by step guide to recover your WordPress site.
Option #3 Hire a Professional
If you do not feel comfortable conducting the site cleaning on your own, or have the ability to restore from a back-up, then that is perfectly okay. In that case, we recommend hiring a professional to conduct the site cleaning. Wordfence offers an excellent site cleaning service for $490 that includes a free year of Wordfence premium to enhance the protection of your site. You can learn more about that service here.
Conclusion
In today’s post, we covered an ongoing attack campaign against a set of critical vulnerabilities in The Plus Addons for Elementor Pro. These vulnerabilities were patched in version 4.1.7, and all sites running Wordfence, including the free version, are protected against these attacks. Nonetheless we urge you to update this plugin if you have it installed on your site, and to reach out to any friends or colleagues that may be using this plugin as this vulnerability is being actively attacked and can be used to completely take over a site with minimal effort on the attacker’s part.
Special Thanks to Threat Analyst Chloe Chamberland for her help writing and providing data for this article.
This article was written by Ramuel Gall, a former Wordfence Senior Security Researcher.


Comments
1:15 pm
Hello, is this another attack form the last one they hard?
7:10 am
Hi Frank,
Most recent critical vulnerabilities are attacked constantly, just not necessarily at this scale. It's likely that this is an attacker pouring resources into an existing attack rather than a completely distinct or new attack.
4:38 pm
My last Wordfence report said it blocked an Elementor attack, even though my site doesn't have Elementor. Anyone else had that happen?
5:33 pm
Yes, same thing on a couple of our sites. Blocked attacks even though Elementor, nor any plugins for Elementor, are on those sites.
3:51 am
This is because these are automated attacks. In many cases, it's not easy (often impossible, actually) to tell if you even HAVE a plugin installed, much less if it's a version that's known-vulnerable.
The easiest way to test this... is to just run the attack. If your site is vulnerable, the attack will succeed. If not, the automation will just try a different attack instead.
This is also why it's important to block these attacks, even if your site is not vulnerable to a particular one -- it could be vulnerable to a different attack the bot has in its arsenal, so catching an attack that theoretically wouldn't work against your site is a great OPPORTUNITY to block this particular attacker early, before they deploy an attack that IS effective.
4:30 pm
Exellent. Thanks so much!