AWS Attacks Targeting WordPress Increase 5X
The Wordfence Threat Intelligence team has been tracking a huge increase in malicious login attempts against WordPress sites in our network. Since November 17, 2021, the number of attacks targeting login pages has doubled.
We’ve seen a global increase in attacks against WordPress sites during the past week, and more than a quarter of all of the malicious login attempts we’re tracking are now originating from AWS EC2 instances, as shown in the chart below:
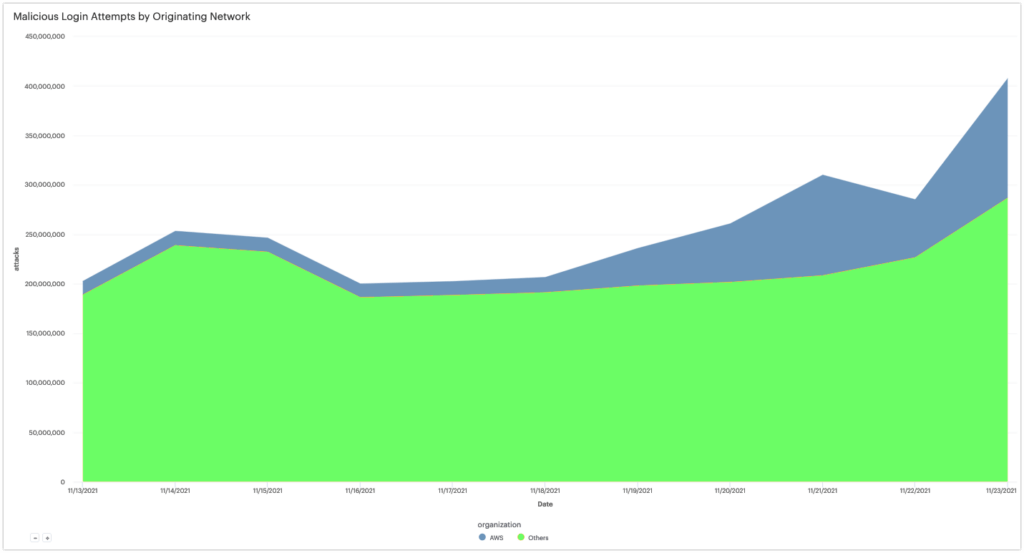
More than 77,000 IP addresses in this IP space have sent out malicious login attempts since November 17, 2021, but the vast majority of attacks are originating from roughly 5,000 EC2 instances.
Most of these IP addresses have only started attacking enough sites to be added to our blocklist in the last week.
The following 40 IP addresses, however, have been on the Wordfence blocklist since the end of 2020 and have each sent out over 1 Million malicious login attempts since November 17, 2021:
35.183.60.188
54.176.188.51
52.60.189.115
52.52.190.187
52.65.15.196
18.231.94.162
34.209.105.222
34.215.69.55
18.221.206.247
52.64.20.252
13.124.222.242
35.181.87.238
18.229.73.207
13.233.73.212
13.209.28.104
52.42.79.222
13.232.96.15
52.15.212.3
13.58.56.77
18.136.72.135
52.30.16.188
35.178.16.1
18.194.196.202
13.48.53.51
13.53.64.97
34.241.77.13
54.250.87.247
3.8.68.2
18.197.125.181
34.251.241.226
18.184.155.204
35.180.147.121
52.192.73.251
3.8.12.221
35.181.112.20
3.0.115.255
13.228.104.57
13.53.208.18
54.178.182.46
13.211.126.30
While AWS makes it easy for businesses to move to the cloud, attackers are also utilizing the scale provided by cloud services, including AWS, in increasing numbers.
As IPs that are no longer sending out attacks are removed from our blocklist, the persistence of these IPs may also indicate that attackers are paying for services in addition to relying on compromised sites. As such, it is important to have mitigations in place to protect your site, since it has never been easier to inexpensively attack millions of sites at once.
Stop Login Attempts Before They Happen
Wordfence Premium customers are protected by our IP blocklist. IP addresses that have recently attacked other WordPress sites are quickly added to our blocklist and are blocked from accessing sites protected by Wordfence Premium. The size of this blocklist ranges from 25,000 to 60,000 IP addresses.
All Wordfence users, including sites using Wordfence Free, receive best-in-class protection against malicious login attempts. Attacking IPs are automatically blocked from a site after a user-configurable number of unsuccessful login attempts.
Many site owners still reuse the same password in multiple locations, and data breaches, such as the recent GoDaddy breach, are frequently a source of compromised passwords. These compromised passwords are used by attackers to attempt to login to even more sites and services. Using this technique, attackers may guess your login correctly on the first try.
We also recommend that everyone use 2-factor authentication wherever possible, as it is an incredibly effective way of protecting your site even if an attacker has your password. The free version of Wordfence includes 2-factor authentication as a feature.
This article was written by Ramuel Gall, a former Wordfence Senior Security Researcher.


Comments
12:57 pm
Why do you write abbreviated instead of stating that these attacks are from Amazon ?! This is how you destroy competition when you go unpunished like Amazon
1:59 pm
Does wordfence have contacts at AWS to let them know this is happening? I suspect many of those EC2 instances have been hacked. Both AWS and the real owner is likely to be very interested in stopping the behavior.
10:52 pm
I noticed this up-tic yesterday so I redirected anything from AWS on the login/register page, back to AWS
If WF did this I'm sure AWS would have something to say about it.
```
if (in_array($GLOBALS['pagenow'], ['wp-login.php', 'wp-register.php'])) {
$ip = get_client_ip();
$host = gethostbyaddr($ip);
if($host!=''){
$kill_hosts = ['compute.amazonaws.com'];
foreach ($kill_hosts as $kill_host) {
if (strpos($host, $kill_host) !== false) {
header('Location: ' . $host, true);
exit;
}
}
}
}
```
4:24 pm
I've been seeing a lot of these too on a site that I have to monitor quite closely. Very recently though, it seems to have swapped from AWS to Digital Ocean servers. Maybe the attackers saw your post!