This site uses cookies in accordance with our Privacy Policy.
1.1: Introduction to WordPress Security
If you are new to WordPress administration and WordPress security, this is the first article from our learning center you should read. It covers the basics of WordPress security and the process of administering WordPress securely. It will help you get up to speed with things like regular plugin upgrades, choosing secure passwords for your members and administrators and a variety of concepts that are fundamental to WordPress security.
Signing In
Signing in to your WordPress website is the first thing you do before performing any administrative task. Signing into a WordPress site may seem like an easy and irrelevant task, but there are certain precautions you should take when signing into your site to preserve WordPress security.
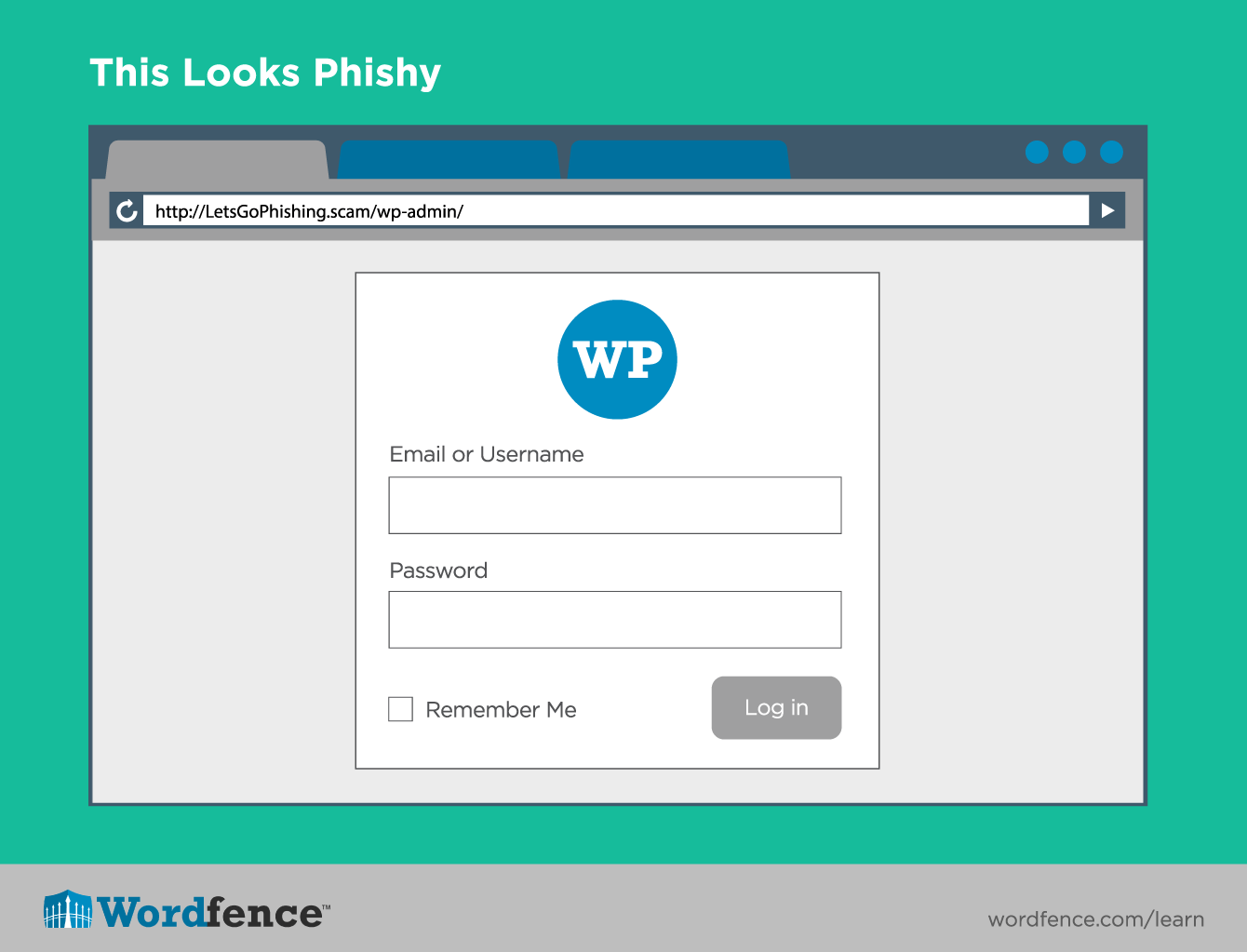
WordPress Security: Don’t get Phished
WordPress security starts the moment you sign into your WordPress site to administer it. Check the domain name you are signing into. A common tactic that hackers use is they will send you an email containing a link to use to sign in to a service. The service may appear to be your own WordPress site, but in fact it is their malicious website.
When you sign in to what looks like your own WordPress website, they store your username and password and use it to hack your real WordPress site. This technique is called ‘phishing’.
A way to avoid being ‘phished’ is to ensure that when you sign in to a site, you check the domain name in your web browser location bar to make sure it is your own website.
WordPress Security: Try to only use HTTPS
Using a secure connection is an important part of WordPress security. Before you sign in, check your browser location bar to make sure that your site starts with ‘https://’ and is green (in most browsers). It may also have a lock icon indicating it is a secure page. Signing in via HTTPS ensures that your login information is sent encrypted across the Network and that someone listening in can’t steal your username and password.
Many WordPress sites don’t use HTTPS and if yours is one of those, contact your site administrator and ask them to upgrade you to HTTPS. This will usually involve purchasing an HTTPS certificate from a Certificate Authority. They cost anywhere from free to over $1000 dollars depending on what kind of certificate you buy and who you purchase it from.
Password Security
WordPress Security: Choose a Strong Password
It is important that you choose a strong password for several reasons. The first is to avoid a hacker guessing your password through brute-force hacking. The second is to make sure that if your site is hacked, your password is difficult to crack. We cover this topic in great detail in our article on passwords which explains how passwords are cracked.
In general you should choose a password that is at least 12 characters long and consists of letters, numbers and symbols with as few English words as possible. Password strength is one of the cornerstones of WordPress security.
WordPress Security: Two-Factor Authentication
WordPress sites are under constant attack by bots attempting to guess your users’ passwords. A lot of these attacks simply test lists of commonly used passwords along with usernames they think you may have chosen, like ‘admin’ or different takes on your domain name.
More recently we’ve started to see more sophisticated attackers leveraging lists of passwords from data breaches in their attacks. These are referred to as credential stuffing attacks and have a much higher success rate than traditional password guessing attacks.
Two-factor authentication (2FA) provides an additional layer of security in the event a password is ever breached. Wordfence has login security features to allow you to use 2FA. Learn about Wordfence’s login security features.
WordPress Security: Store your Password Securely
One problem with choosing a strong password is that they are hard to remember. Here are several methods you can use to store your passwords and each one of them has advantages and problems associated with them. Choose which one works for you and know that none of them are perfect:
- Use a password wallet service like 1password which stores your passwords encrypted and uses a master password to access them. These services can also be hacked which compromises all of your passwords at once. The advantage of using them is that you never have to remember another password.
- Write your password down. Easy to do, but if someone gains physical access to your office your passwords are compromised.
- Memorize your passwords. Very secure, but if you forget your passwords you have a lot of work to recover them.
- Use a password formula. For example: Take letters from the domain name you are signing into, add them to the beginning and end of a password you have memorized using some formula and you have a unique password for every site you sign into with a way of remembering each one. This can be very secure if the formula you come up with produces strong passwords.
Choose a password storage mechanism that works for you and ensure that you choose strong passwords for your WordPress site, especially for your WordPress administrative level accounts.
Creating New Posts and Pages Securely
Publishing new pages and posts using WordPress may seem like a trivial task with very few security risks, but there are a few things you need to be aware of to avoid compromising your site security.
WordPress Security: Don’t Embed Untrusted Code
Embedding javascript or other code on your site gives the code owner access to very sensitive data. They can steal your visitor cookies, including your own site cookies when you sign in as administrator. This can give the code owner admin level access to your website.
Before you grab some code and add it to a page or post so that you can include a video or Javascript widget, first consider the source. Do you trust the company that is providing you with the code? If it is YouTube.com or Vimeo, you can probably trust them. If it is weStealCookies.com or knownBadGuys.com, perhaps you should reconsider. Carefully evaluating code before embedding it on your site is an integral part of WordPress security.
WordPress Security: Beware of the Guest Poster
Once your site starts getting traffic from the search engines, you may be approached by someone offering to do a guest post. If you choose to allow them to guest post, we recommend having them publish the post using a third-party platform like Google Docs. Then you can copy and paste the content into a post and publish it, giving credit to the guest poster if you choose to.
If you allow the guest poster to edit a post or page directly on your site, you need to give them a higher level of access to create a draft document. You also need to view the source of the post or page by clicking the “Text” tab at the top of the article to ensure they did not embed any code in the post or include links to websites that you might not approve of.
Make sure that you analyze any guest post articles carefully for spam links and embedded code.
Comment Spam and Malware
WordPress Security: Automatic Spam Filtering
It may surprise you to learn that we consider spam to be a WordPress security function. Almost immediately after you launch your first WordPress site, you’ll notice comments appearing that are garbage, with links to websites that are filled with junk. Welcome to ‘comment spam’. To help filter out comment spam, we recommend Akismet – this plugin does a great job of helping filter out comment spam automatically and will reduce your workload.
Once you have automatic spam filtering set up, you will unfortunately discover that some spam still gets through the filters and you need to manually filter it.
WordPress Security: Develop a Manual Spam Filtering Policy
We recommend following these guidelines:
- Don’t allow comments that include any embedded code or javascript. Usually this is not allowed and will be filtered out by WordPress, but vulnerabilities sometimes appear that allow code like this through. If you see code, just flag it as spam unless you are running a developer website and want to allow your commenters to include code samples.
- Trust comments that don’t include a site URL more than those with a URL. In general, spammers will always include their site URL with the comment. Real commenters do the same thing, but in general when you see a comment with no URL, it means that whoever posted it is not at all interested in self-promotion and you’ll rarely find spammers that aren’t interested in that.
- Don’t allow comments in a language you don’t understand. For some reason we have a problem with Japanese comments getting through our spam filter. We don’t know what the comment is saying, if it contains politically sensitive speech or if it contains adult content. Filter these out.
- Consider carefully a comment with many URLs. Usually these are typical of spam comments and there are few legitimate reasons to include a large number of URL’s in a comment.
WordPress Security: Check your Comment Settings
In WordPress, go to “Settings > Discussion” and you will find the settings that govern your comment policy. Here are a few helpful suggestions:
- You may want to disable pingbacks and trackbacks. This can be a common source of spam, and unless you want links automatically added to sites that link to you, disable this feature.
- Enable allowing people to post comments on new articles. This keeps things lively.
- Require that the comment author fill out name and email.
- The feature to “automatically close comments” more than a number of days old is great to reduce your spam-filtering workload. Most comments on a post or page will appear within the first few days and then trickle down to nothing. However, watch how your site visitors behave. We have seen pages that become a kind of ‘forum’ about a particular subject and if you don’t mind filtering out spam comments on older posts, this can be a great way to have your user community keep contributing valuable content to your site.
- You probably want to receive an email whenever a comment is posted, unless your comment traffic is very heavy and you are signing in daily.
- Holding a comment if it contains one or two links is a useful feature because spammers usually include links in the comment body.
Review your comment settings carefully, develop a policy that matches your website and community needs and that helps limit spam.
Finding and Installing Themes
A Theme on your WordPress sites creates your site look and feel. You install a new theme under the Appearance > Themes menu.
WordPress Security: Avoid Malicious Nulled Themes
Nulled themes have had a wide impact on WordPress security. When choosing a theme for your WordPress site, avoid downloading themes from untrusted sources. Unfortunately there are many websites on the Web that distribute malicious themes. These themes are called “nulled” themes and they contain malicious code pre-installed. Only install themes from trusted sources.
The most popular source for WordPress themes is the official WordPress theme repository which you can find at WordPress.org. These are themes contributed by the community. They are open source and are generally reliable and infection free.
Commercial themes can be found at well known sites like Themeforest.net and ElegantThemes. When using a theme from a source you don’t recognize, try Googling the site domain name in quotes and you may find reports indicating whether the site is reliable or engaged in a malware campaign.
WordPress Security: Upgrade your Theme Regularly
Occasionally a security vulnerability may be discovered in your site theme that allows hackers to gain access. Any reliable theme maker will distribute fixes for vulnerabilities in the form of new theme releases. Make sure that you upgrade to the newest version of your theme if one is released after reviewing the changes. This will ensure that any fixes are incorporated into your theme.
Note: It is common practice among WordPress developers to customize themes. If you upgrade your theme, you may lose some changes that a developer has made. If you are using a theme that has been customized and you notice a new version has been released, work with your site developer to ensure that you don’t lose any customizations to your site when you upgrade. An option to preserve your customizations is to use child themes.
Finding and Installing Plugins
WordPress plugins are very useful and one of the most powerful features of WordPress. There are tens of thousands of open source plugins available at WordPress.org in the official WordPress plugin repository. You can easily install new plugins by signing into your WordPress administrative interface, going to Plugins > Add New and using the search feature to find plugins that match your needs.
As with themes, it is important to avoid installing “nulled” plugins that are distributed by a malicious website and contain malicious code pre-installed. Plugins from the official plugin repository are generally safe to install. The WordPress team keep a close eye on the plugin repository for malicious code. The plugin repository is also visible to the larger WordPress community who report vulnerabilities and malicious activity.
WordPress Security: How to Avoid Plugin Vulnerabilities
Understanding plugin vulnerabilities is a critical part of WordPress security because vulnerable plugins are the most common way a WordPress site is hacked.
While a very powerful and useful resource, plugins are one of the things that can lead to serious security vulnerabilities in a WordPress website. They contain significantly more PHP code than themes and the code is more complex. This creates more opportunities for vulnerabilities to creep into code.
It’s important to note here that WordPress is not an inherently insecure platform. It is simply a very popular platform and has a huge number of plugins available. WordPress has over 40,000 plugins available (with over 1 billion downloads) which makes it an attractive target for hackers. Because of this it is important that you follow a few guidelines when choosing, installing and maintaining your WordPress plugins. Here are a few important tips:
- Only install plugins from a reputable site. The official plugin repository is a great start.
- Only install the plugins you need. The fewer plugins you have available, the smaller the “attack surface” that hackers have access to because you have less code to attack on your site.
- Do not leave deactivated plugins on your site. Delete them. Deactivated plugins can still provide a way for a hacker to gain entry because the code may still be publicly accessible.
- Only install well-maintained plugins. If a plugin has not been updated in a year or more, it is probably not being maintained. That means if a researcher reports a security problem (a vulnerability) to the developer, they might not fix it.
- When a new version of a plugin is released, review the changes and upgrade to the newest version as soon as possible, especially if it includes a security fix.
Keeping your plugins up-to-date and secure is one of the most effective ways to ensure that your WordPress website stays secure.
Avoiding Dangerous Widgets and Code
In the section above discussing posts and pages, we mention avoiding installing untrusted code. WordPress includes a useful feature that lets you install “widgets” which are items that appear in your sidebar or footer.
You can access this feature by visiting Appearance > Widgets.
Most widgets are helpful and provide useful features. Some sites and services offer javascript code or other code that you can embed as a widget on your site. Usually you will add a text widget and include the code they provide.
Choose carefully when embedding code from another website or source on your site. If you install someone else’s code, you give them access to sensitive data on your site including your site visitor cookies and your own administrative cookies.
If the code you are loading in the widget loads from your own website, then you have the ability to maintain that code. If the code loads from someone else’s website, they can change the code whenever they want.
For example, lets say your site is example.com. If you load the code you include as a widget from http://example.com/mycode.js then you control what code is being loaded on your site. The only way the mycode.js file can change is if you change it.
However if example.com is owned by someone else and you are loading that code on your own site, they can simply go in and edit mycode.js, change it so that it steals your site cookies and create a serious security problem for you.
Some javascript code that loads from an external site can be trusted. Google Analytics and Google AdSense are examples of javascript code that loads from another website (Google’s servers in both cases). So if you do choose to install a widget on your site that loads code from somewhere else, make sure it is a reputable website.
Creating New Users Securely
To create a new user in WordPress, go to Users > Add New.
Besides manually creating users, there is another way that users are created in WordPress. Unfortunately many WordPress site owners don’t realize this. If you visit Settings > General in your WordPress admin interface, you can enable the option for “anyone can register”. This allows users to create new accounts with ‘Subscriber’ level access. See below for what this role gives you access to.
When “anyone can register” is enabled, your list of users may get long and you may encounter spam accounts being created. This setting is off by default. Don’t enable it unless you specifically need your site visitors to be able to register themselves.
WordPress Security: New User Passwords
WordPress security depends on all user accounts remaining secure. When creating a new user, WordPress will assign a password to the user automatically. You can also choose to manually specify a password.
We recommend you allow WordPress to choose the password for you. The current version of WordPress uses a random sequence of upper and lower case letters, numbers and symbols and generates a password of approximately 16 characters in length. This is a very strong password.
When WordPress automatically assigns a password to the user, as you create the account the system will email a link to your new user’s email address. The email includes a ‘password reset’ link that will bring the new user to the site and provide them with the option to choose the strong password WordPress created, or to specify their own password.
This method of user creation is secure and provides your new site members with strong passwords. We don’t recommend that you manually assign them passwords based on english words. These passwords are easier to guess and to crack.
You can learn more about WordPress passwords, password cracking and how to choose strong passwords in our article on Passwords and Password Cracking.
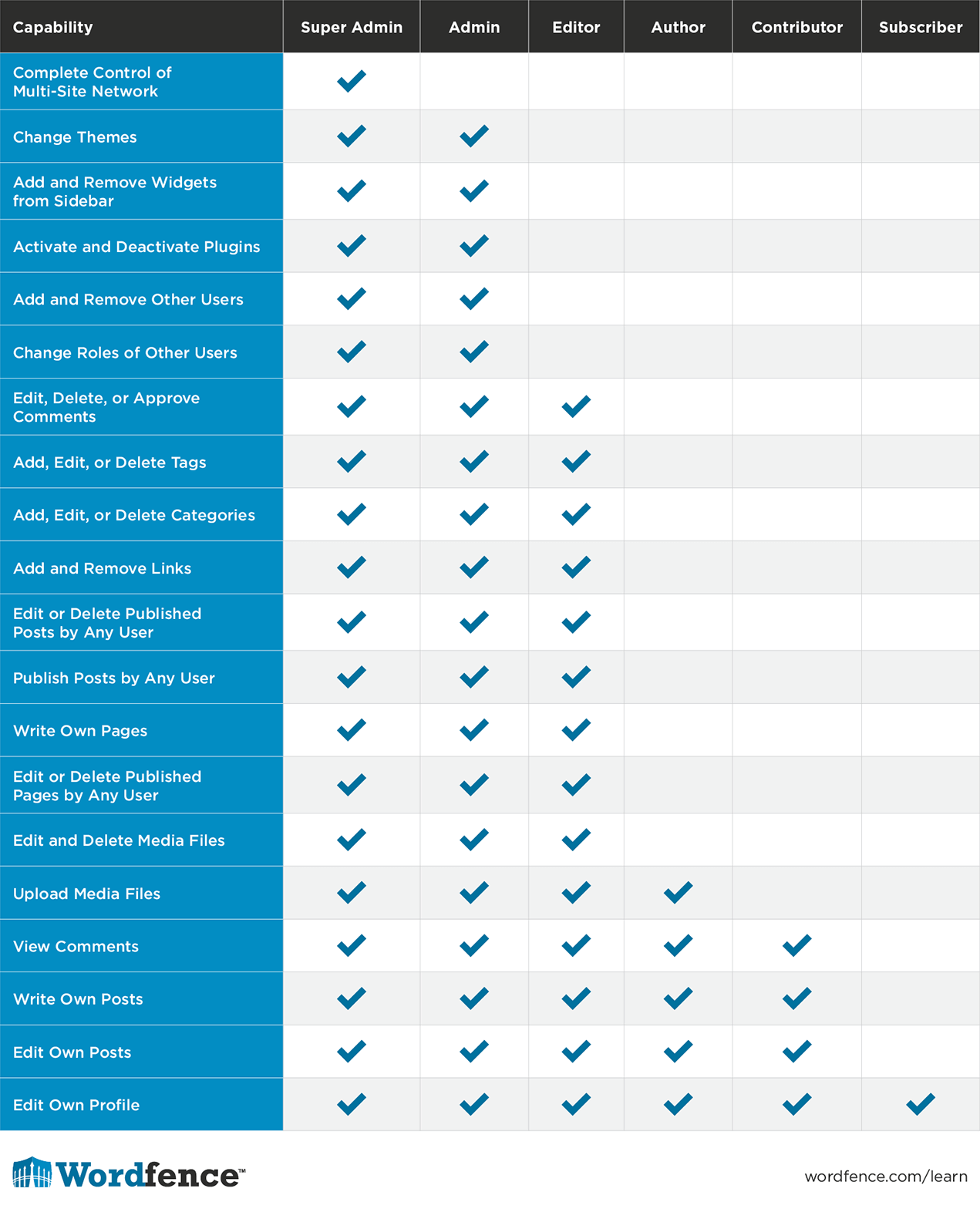
WordPress Security: WordPress User Access Levels
WordPress uses the concept of “roles” to assign security access levels to site members. This is helpful because the security level you have access to reflects the role you play within your organization.
When assigning security roles to your users, it may be tempting to give them higher levels of access “just in case”. Don’t do this. In information security, it is good practice to provide the minimum level of access needed for a user to fulfill their duties. If they need more access, let them ask you for the access required. That way you ensure that people don’t have a higher level of access than they need.
This principle of granting the minimum access required to perform their duties is called the Principle of Least Privilege or the Principle of Least Authority. It is a well established principle in information security theory that provides a more secure environment by avoiding granting access where access is not required.
This is a brief summary of roles within WordPress and what each role allows you to do or have access to:
- Super Admin – A user with super admin access can do everything on a WordPress website. This is the highest level of access. On a multi-site installation where a single WordPress installation manages many sub-sites, a super admin has access to the Network Administration Panel which allows them to administer all sites. You should only have one or two super-admin’s on a site.
- Administrator – On a single-site WordPress installation (which describes most WordPress sites) the administrator role is the same as super admin. It gives a user access to everything. On a multi-site installation, the administrator has admin access to a single site whereas super admin provides access to the network admin panel. As with super admin, administrator roles should only be assigned to one or two administrators who absolutely need this access level.
- Editor – An Editor can publish posts and pages and can also manage posts and pages published by other authors. They have the ability to create and save draft posts and pages and also publish.
- Author – An author can publish their own posts and pages, but can not manage or publish posts or pages belonging to others.
- Contributor – With Contributor access, a user can create draft posts and pages but can not publish them. This is a useful role for guest posters on your site. You can give a guest poster Contributor access, they can create a draft, and you can then review the post with a higher level of access and publish it when you are ready.
- Subscriber – This is the role with the lowest access level in WordPress. When you have “Anyone can register” enabled under WordPress Settings > General, new users that register will have Subscriber level access. (This setting is off by default) A Subscriber can manage their own profile and they can also post comments (if you have comments enabled) as a signed-in user.
To run a secure site, use the Principle of Least Privilege. Your users can always ask for more access and that is an easier problem to solve than a malicious user or compromised account that has too much access.
Using FTP Securely
FTP stands for File Transfer Protocol, and it is simply a way to transfer files to and from a server on the Internet. It has become a standard way for WordPress developers and site administrators to manage their sites.
A website is mostly files, and since FTP provides a great way to manage files, it’s perfect for managing WordPress websites.
WordPress Security: sFTP, FTPS and plain old FTP
Your WordPress security depends on you not just securing WordPress itself, but all other access methods to your website. FTP is used to transfer files to and from your site and needs to be secure too.
FTP was originally a plain-text protocol. That means that it sent your username and password as plain unencrypted text across the network. This is a very bad idea because if anyone is listening in, for example on the WiFi at the coffee shop you’re visiting, they can grab your website username and password and gain access to your site.
If a hacker gains access to your FTP credentials, they can do a lot more damage than simply getting access to a lower privileged WordPress account. They effectively have access to your entire website, even the files and directories outside your WordPress installation. For this reason it is important to protect your FTP credentials.
sFTP is an improvement on FTP because it sends your username and password across the network encrypted. It uses a secure encryption protocol that works via the SSH (or secure shell) service.
An alternative protocol exists called FTPS which is also secure. It works a little differently to sFTP because it uses TLS for encryption and works via an FTP server rather than via SSH. Both sFTP and FTPS are secure.
We have created the video included below to demonstrate how insecure it is to use plain old FTP to administer your WordPress website.
WordPress Security: Securing Your Files Transferred with FTP
As part of your day-to-day operations with FTP, you will probably download a copy of some or all of the files on your website. These files contain sensitive information and in some cases contain usernames and passwords. The wp-config.php file, for example, contains the username and password for your database server.
For this reason it is important that you treat the security of your WordPress website files as seriously as the security of your website itself. These files include ZIP files that may contain backups of your site or the individual files themselves. If you store these files on your workstation, make sure you don’t lose your workstation or laptop. You should consider encrypting your hard drive or at the very least password protecting access to your workstation.
Don’t leave website files lying around on thumb drives or on portable drives that are insecure.
Be careful where you store your website files online. Make sure you know who has access to the storage devices and services you use and don’t store unnecessary copies of your site.
Conclusion
This article has given you an introduction to WordPress security as a site administrator or WordPress publisher. We have discussed several common pitfalls that confront WordPress administrators, introduced you to the principle of least access and user roles or access levels. We have also discussed comment spam, avoiding malicious code and how to store your backups safely.
At this point you have gained introductory knowledge of how to securely administer a WordPress website. We encourage you to read the next in our 1.X series of WordPress security articles which will introduce you to intermediate and advanced concepts related to securing your WordPress website.