Who is Really Behind the Ukrainian Brute Force Attacks?
Last Friday we published a report showing a significant increase in Brute Force Attacks. We showed that most of the attacks are originating in Ukraine and we shared the most active IP addresses with you.
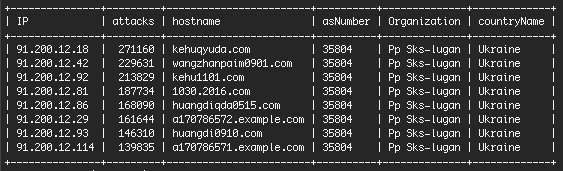
I have chatted via Skype and email with a source in Kiev, Victor P, who sent me some additional info. The company that owns the malicious IP block is “SKS-Lugan”. They are based in Alchevs’k in eastern Ukraine. According to a business guide Victor sent me, they have 16 employees and their CEO is Lizenko Dmitro Igorovich.
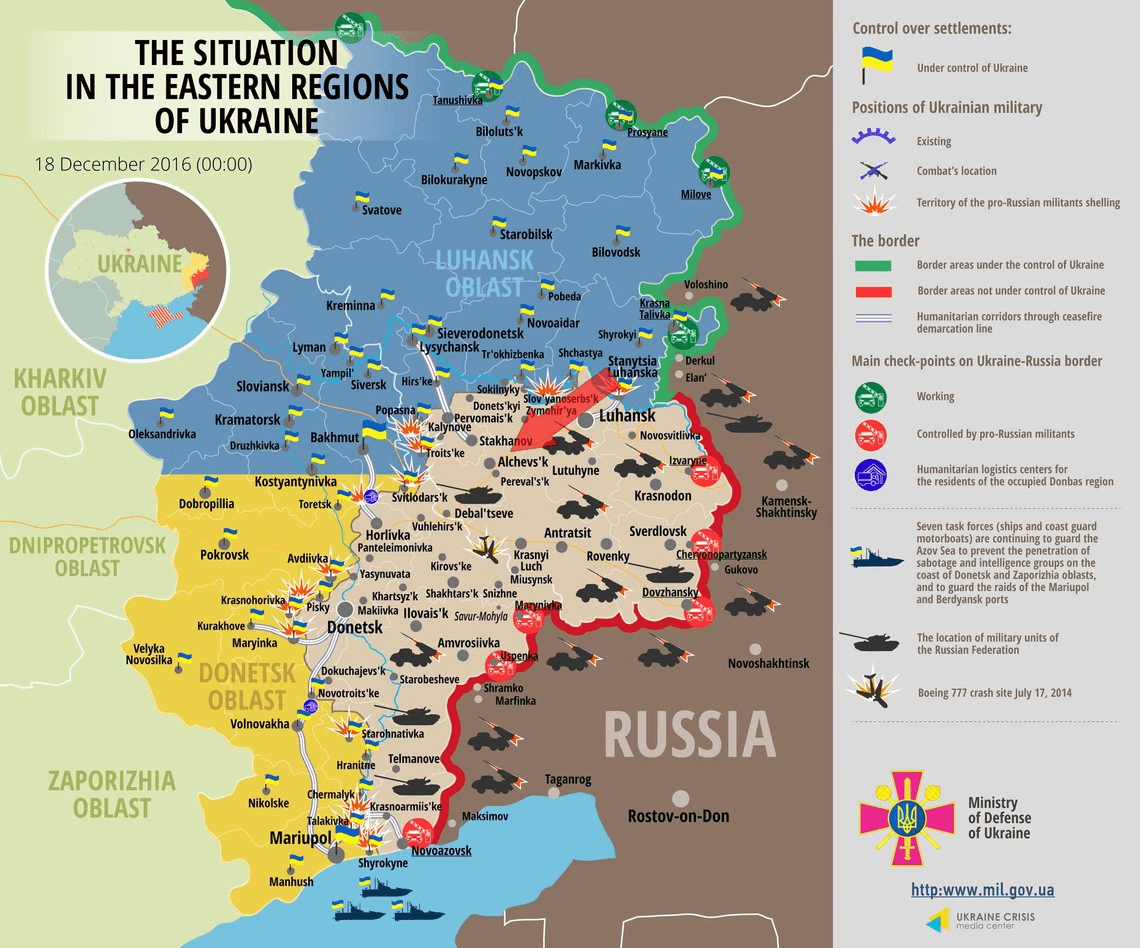
The eastern part of Ukraine is currently occupied by Russia. The map below, dated December 18th (yesterday), is from the Ukrainian Ministry of Defense. It shows which territories within Eastern Ukraine are currently occupied by Russia.
I’ve marked the location of Alchevs’k on the map with a red arrow. Victor is familiar with the reputation of the attacking IP block. He says that the company is being controlled by Russia and is being used to launch cyber attacks globally.
“Gabriele”, one of our readers, pointed out in the comments on our earlier post that the full IP block is 91.200.12.0/22. If you aren’t familiar with CIDR notation, that is an IP block that starts at 91.200.12.0 and ends at 91.200.15.255. It contains 1024 addresses (1022 usable addresses).
The network block is known for “Spammer & cybercriminal hosting”. The range of activities that are listed for this IP block are:
- Botnet controller
- Spam email leading to domains hosted on this block
- Spammer hosting
- Citadel botnet controller
- Neurevt botnet controller
- Smoke Loader botnet controller
- Locky botnet controller
- Canadian Pharmacy Botnet spam
- Tinba bonet controller
- Carding fraud site
- Madness botnet controller
- FindPOS botnet controller
- Pony bonet controller
- DDoS botnet controller
- Forum/Comment spam source
- Vawtrack botnet controller
- Necurs botnet controller
- Russian botnet drug spammer server
- Andromeda botnet controller
- Cutwail botnet controller
- KINS botnet controller
- Vawtrak botnet controller
Those are just some of the spam and botnet activities logged from this network. The list is long.
Russia has staged a military intervention in Ukraine that started in 2014. It wasn’t until December 2015 when Putin first admitted that Russian military intelligence officers were operating in the country.
In cyber security, attributing attacks to an individual or state is very difficult, sometimes impossible. Attackers on the Internet can route their traffic through as many servers in as many countries as they like before they reach their target.
The Russian intervention in Ukraine makes attribution of attacks even more complex. Using a Ukrainian Internet service provider gives Russia the ability to launch attacks globally with plausible deniability.
It makes sense that disputed areas like eastern Ukraine and Syria are a hotbed of malicious activity because they provide attackers with means, motive and opportunity. Occupying forces have the means to launch their attacks by using local ISP’s. They have several motives: They want to benefit from the attack itself and also discredit local businesses or government. And they have plenty of opportunity as these regions are usually occupied for years.
What to do about these attacks
Wordfence blocks these attacks by default. It will handle any brute force attacks and our firewall does a great job of blocking more sophisticated attacks. The free version of Wordfence receives our ‘community’ firewall and scan rules which are 30 days old. The Premium version of Wordfence receives real-time updates, so if we release a new rule for the firewall or malware scan, you receive it in real-time.
To combat these attacks, we recommend you simply install the free version of Wordfence if you haven’t already. Wordfence will lock down your site and protect your investment against these attacks.
Mark Maunder – Wordfence Founder/CEO.
Feedback: As always please share your thoughts in the comments below. I will be around to reply. If you would like to send a tip or data related to this story, you can email us at feedback@wordfence.com.
Thanks to Matt Rusnak and Kerry Boyte for their assistance editing this post.
Update at 1:50PM PST: A Note on Political Comments
I have received several comments regarding the perceived political nature of this post. I’ve published several of them. A few I’ve had to delete because they were personal attacks.
It seems that by sharing one Ukrainian citizen’s point of view in this post, I’ve become involved in a tense political debate and I have, unwittingly, taken a side.
Let me be absolutely clear: I don’t have any political agenda either in the United States or with regard to the Ukraine/Russia conflict. This post is merely continuing a conversation we started on Friday about where a certain kind of WordPress attack originates from and who might be behind the attacks, either human, corporate or government.
At this point I’m closing comments. I don’t want this to become a forum for opposing parties to debate politics. Our focus here is WordPress security.
Thanks again to everyone who participated in the discussion. As always I value and have taken note of your feedback.
Kind (non-political) regards,
Mark Maunder – Wordfence Founder/CEO

Comments
12:22 pm
Fascinating stuff, Mark. Thanks for you and your team's research, as well as Wordfence keeping cnqr.co safe.
12:26 pm
You're insane, guys. With all the respect, don't make political posts and match brute force attacks with politics and even Putin.
Russian sites suffer from those attack too.
Peace.
12:32 pm
Hi,
This is in no way political. We're just sharing data that has been shared with us. The ISP that owns the IP's is based in eastern Ukraine. Eastern Ukraine has been invaded and is being currently occupied by Russia. I've also shared that this data came from a source in Kiev who was happy to chat with me and share his thoughts on what might be happening.
If you have any additional data you'd like to share, I'd love to see it. You're also welcome to share your own thoughts on what kinds of attacks you're seeing on sites hosted in Russia and the origins of those attacks.
Thanks for your comment.
Mark.
12:48 pm
While I appreciate you are just providing your own speculation on the matter, there are many customers such as myself that would appreciate if tech companies would stop with the insertion of politics into topics. While you may not believe the post is political in nature, there is plenty of speculative guessing going on here and it is inherently political in nature, regardless if you are attributing blame to either side of the conflict, when you start trying to attribute blame to a country. Customers are already inundated with pseudo-journalism and don't need it intruding into every sphere of their activities.
1:08 pm
Hi Andrew. We need to be able to mention country names in our reporting. If we omitted data to avoid offending anyone, these posts would be dry indeed.
Mark.
1:33 pm
This was not necessarily a political post. It's a simple statement of fact. He's not ascribing blame or responsibility but describing what is reliable and confirmable facts.
In fact, he's revealing more here than what I've heard about other accusations of Russian involvement in other, definitely political situations.
1:41 pm
Your plugin is great and I have been using it for many sites for quiet some time, but this post kind of makes me want to leave you. I'd say you do more than just mention country's names: "Using a Ukrainian Internet service provider gives Russia the ability to launch attacks globally with plausible deniability." You do not know who is behind the attacks and for what reason. Not that I especially love Russians, but you are using fear mongering and speculation to widen your user-base. This is just bad form.
1:40 pm
But your article is highly political and it is clear and unambiguously so. Why talk about Putin and the so-called invasion of Ukraine if you don't see the reasons for the increase in attacks as being of a political bent? If you don't think it is relevant then why mention it? I think the writer is confused actually.
1:42 pm
@Russian Vatnik: I don't see any political statements here. Besides this, the fact that Russian websites are being targeted is not a valid argument though. Remember how many U.S.-based servers were infiltrated by the NSA. Of course the NSA has probably not planned to be purely destructive or to build a bot net, but this has nevertheless been a highly criminal act.
I wouldn't suppose that Mr. Putin is directly behind such kind of childish attacks, but I might as well misoverestimate (sic!) his smartness. However, let the people have their David (Marc) vs. Goliath (Vladimir P.) scenario, and let's get back to work. Greetings from Germany.
12:26 pm
I love these updates. Your plugin (both the free version and the paid version) take a lot of the worry and guesswork out of security issues for those of us who build and host wordpress sites for our clients. Keep up the good work, I feel as if I learn something new with each blog entry.
12:27 pm
I just started blocking all access from Ukraine a few months ago due to the large number of hackers attempting to break into my site. This eliminated 99% of the hacking activity, but a small amount still persists out of Brazil, China, France, Germany, Holland, Latvia, Mexico, Romania, and the Czech Republic. It is interesting to how much time so many people have to waste with attempting to disrupt the legitimate business activities of other people.
12:45 pm
I've been monitoring live tracking on one of my websites for a few weeks and blacklisted the most attacked urls in the Wordfence options. This provides a daily catch of about 20-30 newly blocked ip's, which I then add to the .htaccess of this site. It is an experiment. Funny thing is that I notice no decrease in the number of blocked ip's, while I gathered over thousand ip's which are now intercepted in the .htaccess stage and never reach the WordPress site. So it seams there is a rather constant stream of attacking ip's that is also constantly refreshing. I wonder if this makes any sense or am I just trying to fill a bottomless hole?
1:33 pm
The thing is it's not people even wasting time to perform these attacks. Majority of them are entirely automated just trying to attack known vulnerabilities. Open source makes for an easy target. I just had a client who had me migrate a very old custom PHP based CMS to WordPress. The VPS they were on, which had absolutely no problems running the site the past 10 years, was completely crippled after migrating to WordPress solely because of automated attacks and the fact WP uses more memory. Even with Wordfence installed, the server was being crippled from a combination of bot attacks, regular user traffic, and legit search engine indexing. I had to move them to a dedicated.
I had to fix a hacked site for someone else recently too due to the common Slider Revolution vulnerabilities. I don't know why this still occurs, but I'll blame Theme Forest and lazy devs. There still seems to be a VERY large botnet behind it. After cleaning the site, I was monitoring and modifying Wordfence config to block requests and it blocked over 6k IPs overnight for requests specific to the attack based on files it originally created on the server. It was primarily just sending out spam. Many of these IPs were based in the U.S. and coming from mobile Android devices. Unless forged, I think there may be some bad apps in the market that are being used for attacks or something is exploiting some other vulnerabilities on Android. Looking at logs, what looked like the main payload requests were coming from an IP on SharkServers and they supposedly allow this behavior. In my experience many attacks come from other hacked sites which keep replicating and building the botnets.
12:29 pm
You're probably right, but I'd get a second independent source on who's really behind the company. The good side in that war also have an agenda :)
12:34 pm
Thanks for the feedback Nils. Yes, it's quite possible the Ukrainian owners are the ones perpetrating the attacks. I'll let you know if we're contacted by other sources wanting to share what is really going on.
Mark.
1:08 pm
@Russian Vatnik: Well, we already have more than one additional source as we have this interesting long list of fails at spamhaus.org (and probably at all other anti spam organisations).
Just let make this thing real and short, block all those sources where ever it is possible!
12:35 pm
Fantastic Mark! I applaud your efforts and the update provides a very visual aspect to this IP attack and it origins.
Thanks again Mark for your great work and the team at Wordfence.
12:36 pm
Thanks Brian. Much appreciated.
12:37 pm
Thanks again for all your efforts with Wordpress in keeping the community safe and protected. Your analysis is first class and reliable. Thanks again Geoff
12:39 pm
Mr. Scott Best:
Holland does not exist as a country. It is the Netherlands with 12 provinces.
Two are called South-Holland and North Holland.
12:42 pm
Thanks so much for keeping us informed and for protecting our WP sites! Is there a way for us completely block the Ukraine on the free version?
12:43 pm
Unfortunately not June. Country blocking is only available on the Premium version of Wordfence because we have had to license a commercial database to provide that feature.
Regards,
Mark.
12:47 pm
I am receiving these attacks on my servers from Ukraine, India, Pakistan ... but that does not mean anything. What is clear is that Russia likes to play dirty at the government level, have made it clear in the last Olympic Games.
12:47 pm
Thanks for the very useful follow-up. I appreciate the additional detail.
12:51 pm
Wordfence is doing great protecting my sites... But I'm still under attack from ips outside of that range. It is clearly one attack as they hit all sites on the network with the same strategy. I'd be dead without wordfence, but I'm still concerned by how aggressively they are attacking.
12:52 pm
6 of my WP sites got hacked badly yesterday. It's scary that I have to be "that on top" of every possible area of my wordpress sites.
12:52 pm
Kudos for this awesome update. Do you happen to know of any other IP ranges or hostnames from Ukraine that we should pay attention to?
12:55 pm
Mark,
Since there's a known block of IP addresses involved in the aforementioned Ukraine cyberattacks, will WordFence simply block that entire range from this point forward? Should we Blacklist them in the settings of WF on our end?
I realize that the firewall is automatically defending against these attacks, but it seems to me that there's sufficient evidence/reason to just block these IPs entirely in order to avoid EVERY possible issue related to them. Thoughts?
- Rich
1:09 pm
We have a real-time list of known bad IP's that are blocked automatically from brute force attacking your website. It's enabled by default.
mark.
12:57 pm
"The eastern part of Ukraine is currently occupied by Russia." - i'm live in Ukraine end i want to tell, this is fu**n lies! Lugansk and Donetsk, unwilling to accept the dictatorship power Poroshenka! No evidence of the presence of Russian troops in the East! Shoots the Ukrainian army by Decree Poroshenka, it is beneficial to war! For two years this bastard, brought the country to the horrible bankruptcy!
1:06 pm
I get this completely. I am truly grateful for WordFence's protection and vigilance. My Webmaster and I both agree that you guys are awesome!
1:06 pm
#Russiansdidit
1:23 pm
Great techy reporting..
I guess you know of the work of Brian Krebs?
https://krebsonsecurity.com/
Between the two of you - some interesting information comes out. Which goes beyond the realms of the 'techy world'
You do realise that Wordfence is going to become a target because of your outspokenness?
I guess that's why we trust you guys!
1:24 pm
"The eastern part of Ukraine is currently occupied by Russia"
Please dont bring US Military-Industry complex neocon horsesh*t to my inbox via your newsletter.
It would be idiotic for Ethnic russians in Eastern ukraine to not set up their own militia and save their lives after US State Department organized what Stratfor called "The most blatant coup in history" and put neonazis on top of Ukraine after having them raid their parliament.
Apparently the prospect of being burned alive like how Neonazis did to those ethnic russians and trade unionists in trade union building in Odessa, did not look appealing enough.
Your 'source in kiev' is apparently someone aligned with the now desperate Neocon-appointed government of Ukraine. Who was recently abandoned even by neocons, and seeking a way out.
One wonders what would happen if China staged a nationalist coup in Mexico and Mexican ultranationalists started burning Americans who live in mexico alive. Leave aside start arming for a war against US...
1:28 pm
While your TECHNICAL information is superb, it sounds to me like POLITICALLY you've been unwittingly used by one of the sides in the Ukrainian conflict. Russia IS NOT occupying Eastern Ukraine--that's a ridiculous statement. Russia IS providing a level of support to some Eastern Ukrainian provinces that are in conflict with Western Ukraine. The level of support is an open question, and you'll get very different opinions about it depending upon who you talk with.
Re the "several motives":
"They want to benefit from the attack itself": Sure, of course. That's why anyone launches these attacks.
"They want to discredit local businesses or government": Why would they want to discredit the businesses and government in the East that they're in political agreement with? This is largely an East-vs-West Ukraine conflict.
"And they have plenty of opportunity as these regions are usually occupied for years": Totally meaningless statement. There is no "usually" here. This is a very specific and tragic situation.
Again, I think you've gotten caught up in a conflict where there is tremendous animosity between the two sides, and unwittingly been used for propaganda by one of the sides. If you're going to go beyond the technical arena where you have expertise, you should do your research first--and that means understanding the complex history involved, and talking to both sides before drawing conclusions.
1:31 pm
Classic, but false! I don't "buy it". This is just an Ukrainian guy blaming Russia.
With all due respect, I'm not Russian, I'm not Ukrainian, but we all know the conflict between those two. You can tell for sure that all these info stand true. Except if you called this company and they admit to it...
Can be either Russia or Ukraine.
Still, thanks for sharing this!
G.
1:41 pm
I think it's just a political post.
1:43 pm
Now that's what I call investigation!
Where are the servers located? In Ukraine.
Who's "occupying" Ukraine? Russia.
So who's behind the attacks? Putin!
Thanks for connecting the dots and making it clear for us ignorant folks. Kudos!
1:45 pm
I got few login attempts from USA over last days
1:55 pm
Difficult not to see this as a politically influenced article. The relentless negative pr about Russia in the West is becoming tiresome as the average person can see right through the agenda. The data available can be easily misinterpreted. Wordfence doesn't need to wade into undignified diplomatic mudslinging contests and speculation. Here's hoping 2017 brings more peace and prosperity for all.
2:03 pm
Thanks Pat. Yours is the last comment I'm approving. I've posted an update about this in the footer of the article. I completely agree - we definitely don't want to wade into any political debate. Our focus is purely securing WordPress websites.
Regards,
Mark.
1:56 pm
Do you know whether they have an equivalent IPv6 block and if so what it is? I'm seeing lots of attempts from Ukraine, but mostly from IPv6 addresses. I'm inclined to firewall them out of the servers altogether (i.e. iptables, rather than wordfence)
2:00 pm
You lucky to be attacked just from this Ukraina range of ip.
I blocked them since 2 YEARS AGO, for their attacks.
One month ago or less, i had to face a brutal force attack, directly from Russia, hundreds of ip, and has been long an entire week.
So if someone have doubts about origin of attacks, no have anymore.
Actually i'm keeping blocked many dozens of ranges of ip from Russia, even attacks are over from time, don't know if zombies has been shutted off or not.
Well, thanks Mark, confirm i was searching.
Just to ask,
did someone noticed that google analytics tracker stop to work and register visits after those attacks, if not blocked permanently ?
I'm living this from 2 years...