WordPress Used as Command and Control Server in 2016 Election Hack
On Friday evening the Department of Homeland Security released a report [PDF link] containing updated and broader analysis of Russian civilian and military intelligence organization’s attempts to interfere with the 2016 US election.
This Wordfence report is an analysis of the new ‘Enhanced Grizzly Steppe Report’ and the data it includes. We show that one of the websites used in the attack was a WordPress website that was (and still is) vulnerable to a SQL injection attack. We describe how it became part of the ‘cyber kill chain’ used in the attack described in the DHS Enhanced Grizzly Steppe report.
Background
‘Grizzly Steppe’ is the name that the United States intelligence community, specifically the FBI and DHS, have assigned to Russian civilian and military intelligence services associated with trying to hack the US 2016 election.
On December 29th, US intelligence released the first Grizzly Steppe report that provided several indicators of compromise or IOCs. These IOCs were indicators of the presence of hacking tools used by the attackers described in the Grizzly Steppe report.
The day after the original Grizzly Steppe report, we released our own analysis of the data in which we shared the actual sample of the PHP malware described in the report, which we had reverse engineered.
On Friday evening, February 10th, DHS released an ‘enhanced analysis’ of Grizzly Steppe with several new IOCs. The report includes 17 PHP malware samples. These all appear to be different variants of P.A.S. which is the malware in the original report which we reverse engineered.
The new report includes some additional data on 9 domain names that were used in the incidents that DHS analyzed and how Windows malware communicated with those domains. In the report below we focus on one domain specifically which is a WordPress site that was used as a command and control (C2) server as part of the attack.
Understanding the Cyber Kill Chain
The term Cyber Kill Chain is a term that Lockheed Martin came up with to describe a sequence of steps that an attacker needs to achieve their objective. It is a way for security analysts to think about and analyze an intrusion.
The diagram below is from Lockheed Martin and is an illustration of each of the steps in the Cyber Kill Chain. [Source: Lockheed Martin]
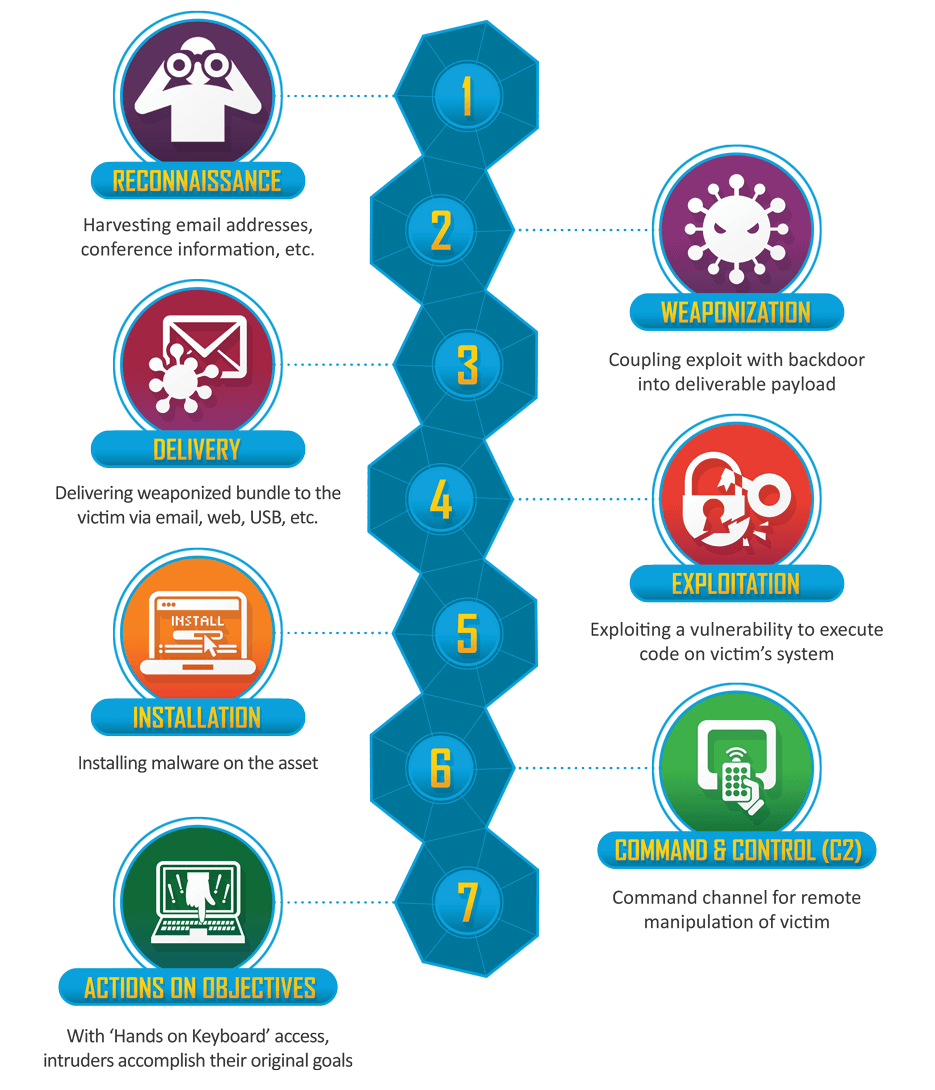
This metaphor is used widely in the intelligence community as a way to think about intrusions. It is also used in the latest DHS Grizzly Steppe report. So we will use it here to analyze how WordPress was part of a kill chain targeting an individual or group.
How WordPress Became Part of the Attack Chain
One of the malware samples included in the Enhanced Grizzly Steppe report is a Windows DLL.

The malware provides a range of capabilities to an attacker. According to the report:
“The program provides an operator access to a reverse shell on the victim system. Additionally, the malware provides an operator the capability to enumerate the victims Windows Certificate Store, and extract identified digital certificates, including private keys. The application also allows an operator to enumerate all physical drives and network resources the victim system has access to.”
The malware is relatively new in the security community and only appeared in VirusTotal on December 29th when the original Grizzly Steppe report was released.
This malware falls into the Installation step in the kill chain above. To be useful, it needs to be able to communicate with its operator. That is where a command and control or C2 server comes in.
WordPress as the Command and Control Server for Windows Malware
According to the enhanced Grizzly Steppe report, the malware above communicates with a website called cderlearn.com. The report goes on:
The application attempts to download data from a C2 server and write it to a randomly named .tmp file within the users %TEMP% directory. Some of the file names used to store this downloaded data within our lab environment are displayed below:
-—Begin Sample File Names—-
TEMP\Cab5.tmp
TEMP\Tar6.tmp
TEMP\Cab7.tmp
TEMP\Tar8.tmp
-—End Sample File Names—-
Our Analysis of ‘cderlearn.com’ – How it was Compromised and Used
The website this malware is communicating with is a WordPress site. Looking at archive.org, it has been a WordPress website at least since 14 March 2016.
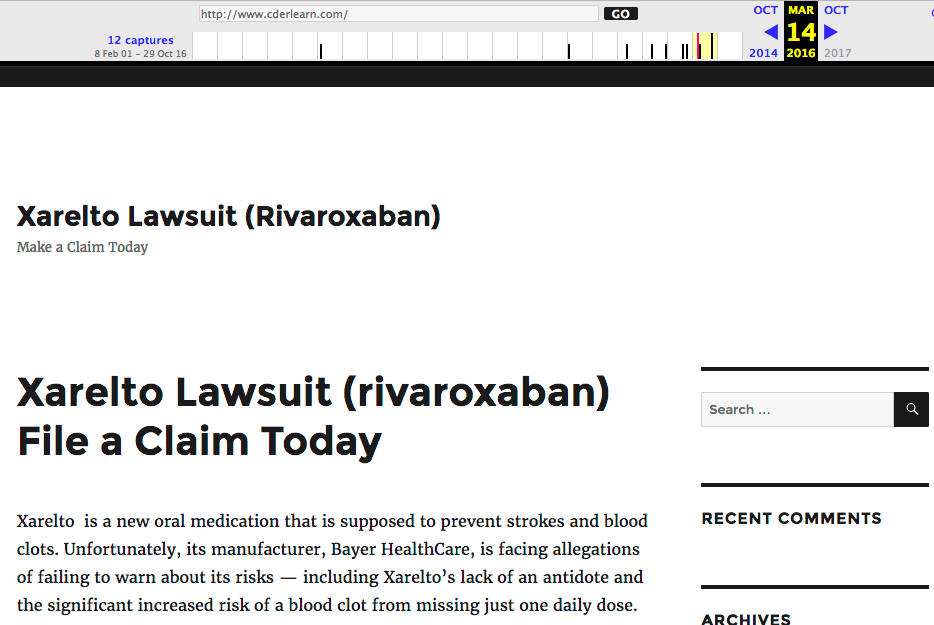
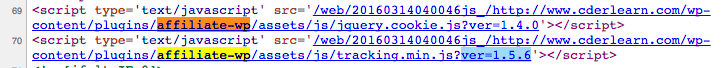
On that date, if you view source on the archive.org snapshot of cderlearn.com, you can see that it was running a plugin called affiliate-wp, version 1.5.6.
On March 16th, 2015, one year earlier, the vendor of Affiliate-WP announced that there was a serious SQL injection vulnerability in the plugin.
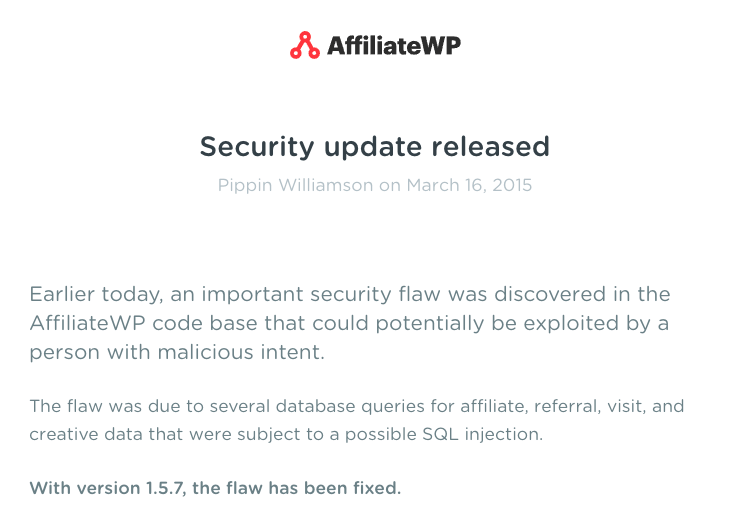
cderlearn.com was running a vulnerable version of Affiliate-WPin March of last year, which may have been used to compromise the site.
cderlearn.com was then used as a command and control server for malware that was designed to give an attacker remote control over a windows workstation. The DHS report provides a few samples of the network traffic between the Windows malware and cderlearn.com:
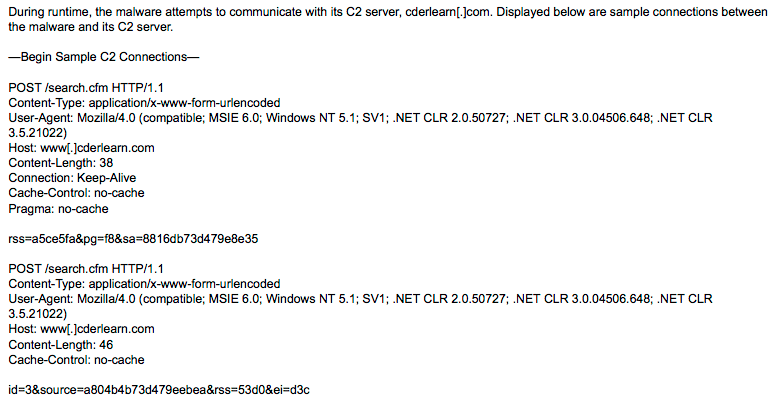
The malware appears to be sending POST requests to a ‘search.cfm’ script which is part of the command and control malware installed on cderlearn.com and is disguising itself as a Cold Fusion search script.
Surprisingly, the website in question appears to still be using the same vulnerable version of the Affiliate-WP WordPress plugin, even today.
Conclusion
In the example above, a vulnerable WordPress site was used in the ‘Command and Control’ step in the kill chain to provide a command channel for remote manipulation of a victim’s workstation. As you can see, this is a sophisticated attack that requires several distinctly separate hacks to achieve its objective. Compromising a WordPress site and using it as a C2 server is only one of those steps, but is a critical part of the kill chain that the attacker needs to achieve their objective.
When we think about securing our WordPress sites, we usually think about the personal impact that a hacked site might have on us, our business and our customers. The story above illustrates how a compromised WordPress site can be used as part of a sophisticated kill chain, used by a nation state actor to attempt to change the outcome of an election.
Securing your website by using a firewall and malware scanner like Wordfence is important, not just to protect your own interests and your customer data, but to help secure the wider Internet as a whole.
Final note regarding comments: Please note that due to the political nature of this issue, we won’t be publishing any comments with political overtones. Our focus is simply on the data that DHS released and the data we are seeing ourselves and our analysis of it. Thank you.

Comments
10:12 am
Dear Mr. Maunder, I’m a NYS licensed psychologist, forensic consultant and author of the dark side of cyberspace construct called iPredator. Although I’m a technology idiot, your article helped to clarify this type of cyber attack. I may have to read it a couple more times, given the complexity, but appreciate your work. Respectfully, Dr. Nuccitelli New York, USA
10:32 am
Thanks for the update Mark. Glad your team is on it when it comes to site security.
John A,
IT
Pacific Coast HVAC
10:37 am
I thought your original analysis said it didn't point to Russia as they had reported. Has that changed?
11:23 am
Attribution when it comes to cyber security is incredibly difficult and may actually be impossible. The data that is used for attribution is when the attacks took place (in this case they were GMT+3 during office hours, which indicates it may have been Russia), language used in source code, where the IOCs have been seen before and in which attack campaigns, and who would benefit from a particular attack. Even if you have all of those things, you still can't 100% attribute an attack to anyone. Perhaps that's why in the intelligence community they speak in terms of 'level of confidence' rather than absolutes. You won't find an intelligence professional anywhere that will give you a 100% certain answer on anything.
The PHP malware sample doesn't appear to point to Russia. It is Ukrainian in origin. The original report and this report are positioned in the media and I think to a certain extent by DHS as attribution showing that Russia attempted to hack the election. I don't see anything in either report that makes it 100% clear that Russia attempted to hack the election.
So really in the report above I'm just echoing what DHS, FBI and their partners are saying. We certainly haven't added any data that attributes this hack to Russia. And the only data we've seen that attributes anything to any country is the PHP malware sample which we reverse engineered, which is Ukrainian in origin. But that could have been a 'false flag' operation where Russia wanted to make it look like it was Ukraine - but of course having evidence that points to another country doesn't attribute it to Russia either.
Mark.
11:29 am
Thank you for taking the time to answer and clarify!
10:43 am
I might have missed it, but I didn't catch the ultimate objective of the hacks. Since USA elections are decentralized state by state, what did this ultimately accomplish to result in saying that our elections were hacked?
11:25 am
DHS describe what Russia (or whoever is running these ops) is doing as a 'campaign of influence'. They are leaking emails and data that will hopefully influence the outcome of the election. So it's not a direct hack of voting machines or vote counts, but instead a long term campaign of influence designed to alter voter decision making and other outcomes.
Mark.
11:22 am
Hi there,
Did the hacked wordpress site have Wordfence on it?
A couple of my sites have had multiple hack attempts just today, I've really seen an increase recently.
Many thanks
Cathy
11:26 am
No it did not and still doesn't. If it did, it would not have been vulnerable to a SQL injection attack. Wordfence is very good at protecting specifically against that kind of attack. Our firewall has a SQL language parser that is able to intelligently determine if SQL in a request is part of an attack or is friendly.
Mark.
11:37 am
It is the DNC's website that was hacked and still not properly protected or the site of another player.
11:48 am
Mark,
Every time you post about the intricacy of these exploits, and the manner in which bad actors work to compromise websites, it just keeps reminding me why we use Wordfence on all the websites we manage. But, I also tell my colleagues here that we can't just sit back and let you all do this for us ("Look Ma, no hands!"). We have to do some of the heavy lifting by using strong UACs, regularly update WordPress and website plugins, and check our Wordfence scans and alerts you send us.
While most of us in the WordPress community are not NSA-grade security experts (like many members of your team no doubt are), it's comforting to know that you are doing everything you can to protect us, while also working to inform us of things we need to know.
Thanks again for unpacking this entire Grizzly Steppe scenario. It reads like a fictional spy thriller. Unfortunately, it appears to all too real.
Chief Digital Officer
Communication Links
Scottsdale, AZ
12:21 pm
This has been a really interesting set of posts. What I'm wondering about is how whoever hacked cderlearn.com found that that specific site had that specific vulnerability and knew that it could exploit it. Do hacker organizations, especially big ones like Grizzly Steppe appears to be, continually scan the web looking for any and all known vulnerabilities, then build a database of the sites they find with them? Do they target specific vulnerabilities because of the opportunities they provide?
What's clear is that there's a tremendous level of sophistication behind these attacks, more than a single individual "sitting on his bed" is likely to be able to muster.
12:47 pm
Thanks for this Mark, it's a very interesting article and made it easy for even us non techy types to understand
2:26 pm
Does this get us any nearer to knowing who was behind the hack?
7:43 am
I don't think so.
11:29 pm
Very informative article. Thank you Mark.
I ran a couple of client sites and there always a time lapse between the announcement of a plugin vulnerability and when we finally apply a patch. Does Wordfence provide temporary protection; for instance if an SQL injection attack is launched against a vulnerable plugin?
7:43 am
Yes that's one of the main benefits of using our firewall.
3:48 am
My clients always ask me "why would someone bother to hack my little site". Your blog gives fantastic answers to those questions and is a big reason why I always recommend installing Wordfence on their Wordpress sites. Thanks a lot and keep up the good work!
7:44 am
Thanks Reine.
11:32 am
It's interesting to read all the WHOIS records in the 2/10/17 report (stuff from all over including US and UK), and to look at the Wayback Machine history of the compromised site. In 2001 it was used for an online class for FDA training. The current owner picked up the domain Feb 2016 and the site set up well after the AffiliateWP plugin had been patched (Mar 2015). There is another plugin installed designed to optimize conversions (Thrive Visual Editor) and yet the site has no form or anything to convert. Odd. The mystery fan in me would say it was set up that way on purpose, but the reality is probably not that incendiary. More likely set up from an old VM Wordpress set and then abandoned.
1:50 am
Thanks, Mark for this article. Articles like these help me to really appreciate Wordfence in keeping my site safe. It also underscores the importance of updating vulnerable versions of plugins.
4:41 pm
I was wondering, if this were to occur with a WordPress site directly due to not keeping plugin etc up to date, could the owners of the site be held legally liable in any way?
6:54 am
Good question. I'm not a lawyer so I can't answer that.