22 Abandoned WordPress Plugins with Vulnerabilities
As an interesting research project, Pan Vagenas, one of our researchers, took a closer look at abandoned plugins in the WordPress repository. His work was inspired by a recent post by Isabel Castillo where she lists the oldest abandoned plugins in the WordPress plugin repository.
An abandoned plugin is one that has not been updated for several years. According to Isabel’s post there are several plugins that have a large install base that haven’t been updated for some time:
“Exec-PHP plugin by Sören Weber has over 100,000 active installs despite that it has not been updated since June of 2009. Category Order by Wessley Roche has over 90,000 active installs even though it was last updated in May of 2008. Ultimate Google Analytics by Wilfred van der Deijl has over 80,000 installs even though it was last updated more than nine years ago.”
We took a look at the plugin repository and discovered the following:
- There are currently a total of 37,300 plugins available in theWordPress.org repository
- 17,383 of those plugins have not been updated in the past 2 years.
- 13,655 plugins have a compatibility tag of 3.x. WordPress 4.0 was released in September 2014.
- 3,990 plugins have not been updated since 2010 which is over 7 years ago.
- There are 29,892 additional WordPress plugins in the plugin source code repository that are not listed in WordPress.org in the plugin directory.
Unmaintained Plugins with Vulnerabilities
During our analysis, we found 18 abandoned plugins that are currently available for installation from the WordPress plugin repository that appear to have vulnerabilities that have not been fixed. In each case the plugin has not been updated for 2 years or more. Some of them have thousands of active installs.
We also found 4 plugins (marked with asterisks in the table below) that have fixed a vulnerability, but their fix was released in such a way that existing users are not updated to the newest fixed version. In each case, the author committed a fix to trunk but did not increment the version number and tag it properly in the plugin repository, so their users remain vulnerable.
The following table lists the plugins that we found, along with number of active installs and the details about each vulnerability. Several plugins are listed multiple times because they have had multiple vulnerabilities reported.
Note that all vulnerabilities published here have been publicly known for 2 to 3 years. These are all old vulnerabilities which have been publicly disclosed and have not been fixed by the plugin author. Please see our suggestions after the table on what to do if you are the plugin author or if you are a plugin user.
What to do if you use one of the plugins above
If the plugin is not marked with an asterisk, we suggest you disable the plugin and remove it from your system. Then immediately contact the plugin author and ask for clarification on whether the plugin has a vulnerability or not. You can direct the author to this blog post which includes suggested actions for plugin authors below. You should start with the plugin support forum on wordpress.org for a particular plugin.
If the plugin is marked with an asterisk, you can disable and remove the plugin. Then reinstall it and you should have a newer version. We have not audited individual plugins for security so we can not verify whether a vulnerability has been comprehensively fixed.
What to do if you are the author of a plugin mentioned above
If you are the author of one of these plugins and have not fixed one of the reported vulnerabilities, we recommend you do so immediately and release a fix to your customers. Then follow the steps in the bullet list below.
If your plugin is marked with an asterisk, we suggest you read the section on the WordPress codex on updating your plugin. Create a new version for your plugin so that existing users will be updated to the fixed version, tag the release and follow the additional steps we suggest below.
If you have fixed a vulnerability in your plugin and we included it above, then you did not mention it in your changelog and it has not been recorded on the wpvulndb website, the source of our data above.
We suggest you take the following actions:
- Update your changelog and mention that you fixed a vulnerability and what the vulnerability was that was fixed.
- Contact the wpvulndb project and ask them to update their database to indicate that your plugin has been fixed. Right now their database shows no entry for a version that your vulnerability was fixed in.
- You should also consider visiting the source of wpvulndb’s data which is often a security mailing list. On that list you’ll find the researcher who discovered your vulnerability. You should drop them a note letting them know the vulnerability has been fixed.
Evaluating Plugins
If you are a WordPress site owner, it is important that you evaluate each plugin carefully before you install it. Check how long it has been since the last update. If it has been more than 2 years, you should think twice before installing the plugin because it is no longer actively maintained. You may consider reaching out to the author or posting on the support forum to find out more information.
The plugin repository is one of WordPress’s greatest assets because it provides a huge amount of code and a large number of applications that extend WordPress. It is also completely open and anyone can contribute. There is no formal source code auditing process or security analysis done on a plugin when it is submitted. There is also no ongoing auditing process for each subsequent release.
A large number of plugin updates are submitted to the WordPress repository every day. For this reason it is important that you gain at least a basic understanding of who is behind a particular plugin before you install it. Here are a few steps you can take to evaluate whether you should use a plugin:
- Check the average plugin rating.
- Check when it was last updated.
- Check that it is compatible with the current version of WordPress.
- Check the number of active installs the plugin has. Some reliable and useful plugins have low install numbers but you should examine a plugin carefully if it has a low install base (below 1,000 active installs). It may not be maintained.
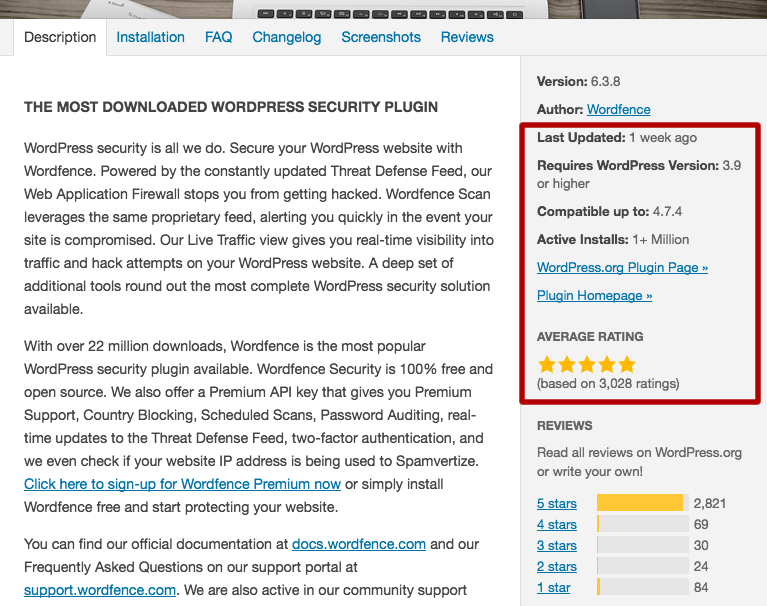
You can find all this information when you add the plugin in WordPress. Simply click on the plugin title and you’ll find the following. We have highlighted the section you should pay attention to below:
Conclusion
Plugins can make adding functionality to your website incredibly easy and are a big part of why WordPress is such a popular platform. The plugin repository on WordPress.org is an incredible resource, but as we have shown above it contains both abandoned plugins and ones with known vulnerabilities. Every plugin you add to your site increases your security risk, and you should evaluate each one to make sure it is being properly maintained.
As always we welcome your comments below. Special thanks to our security researcher Pan Vagenas who compiled the research we included in this post.

Comments
10:20 am
WordFence is on the ball here. I've often wondered why WordPress doesn't clean up the plugin repository and get rid of the outdated, potentially harmful, incompatible-with-current-WP version plugins? Same with Templates. If they are no longer maintained - let's get rid of them. And who uses Hello, Dolly? Junk that one, too.
10:40 am
Agreed, I wish WP would ditch Hello Dolly and add a last updated column in the plugins list to make this easy for us to check out our plugins.
10:50 am
100% agree!!
5:35 am
Agreed
10:26 am
Wordpress.org should make a policy in that if a plugin isn't updated at least once per year, even if no changes are needed for the plugin, should be removed from Wordpress.org plugins pages.
11:12 am
Totally agree, Wordpress must to put a policy of updated plugins and themes to avoid security problems, even if the plugins are free. Regards
4:16 pm
Removing them from the WordPress site is great but that's not the main issue - the problem is that most people never bother to check once their site is completed. So what is more important is some way to alert site owners from within the site that a plugin is way out of date and must be removed. It should be huge flashing banners that terrify the site owner. This could be a feature in WordFence but in reality, I think WordPress has an obligation to deal with this as it affects the reputation of WordPress heavily.
11:29 pm
Removing from the site i think is not that necessary, its there for important information like last update and the author and the idea, and Mark send us info about this plugins for safety reminder. So we can track where this plugins come from. We don't have yet detailed info about this plugins why its not update or stuck and not fixed the vulnerabilities. Maybe someone or one day they will jump of that idea of plugins and develop it again and will rise again ;)
11:41 am
That's something almost in place. Try to search the repo or install from your own WP site an old plugin like WP Memory Usage (by Alex Rabe). You won't see it coming up. But you can certainly do a search in Google and find it here: https://wordpress.org/plugins/wp-memory-usage/ It's a cool plugin, still works. But it's old an abandoned.
The real problem are those old plugins installed on abandoned, yet published websites. I think WP should send notifications to the admin warning about installed plugins that are too old. I bet this can be done as a plugin, indeed :)
1:46 am
WordPress.org places a label on plugins not updated in over 2 years, to warn users that the plugin may not be compatible. There are actual plugins that are over 2 years old, and even 8 or 10 years, that are compatible and clean. Perhaps the better solution is to see if any other developer would consider adopting.
The Plugin Review team does a good job taking down a plugin when it's become vulnerable. If you find a vulerability, it's not difficult to report it on the WordPress.org Slack channels.
10:33 am
Thanks for this and for a great plugin. Agreed, Wordpress.org should make a bit more of an effort to keep the lists clean.
10:35 am
You guys change the way of Wordpress security. I do use the premium version of Wordfence and it amazing.
10:36 am
I totally agree, I had to hold back on the latest Woocommerce 3.0 version because supporting plugins and themes where slow on the updates and some still require updates.
10:39 am
Thoughts:
- Did you use a tool to scan the plugins?
- If so, could Automattic do the same?
- Did you scan the whole repository?
It does Wordpress' reputation no good to have these vulnerabilities in the repository, which begs the question of why they are there. Is no one in control? It is so strange - it is a big business with pages of detailed explanations of how to harden and protect a site. Jetpack is promoted on its ability to protect - and yet...
12:08 pm
Pan used the WordPress API to get this data. The API endpoint is at: https://api.wordpress.org/plugins/info/1.0/
We imported data from the API into mysql. We also created a separate table and populated it with data from wpvulndb and their data. We then joined the table on the plugin slug and generated a range of reports. We actually have far more data than we published in the above post so we may do a follow-up on this. But as we examined the data it became clear that the plugins above that are still public and have unfixed vulns was the most important message we needed to get out.
Yes, we looked at the entire repository, even plugins that are not publicly available via the directory.
Mark.
10:45 am
Keep it up WordFence team. I have none of these plugins but I think this post will go a long way to help many people. If I may request, I think it will be nice if WordFence plugin can show the list of the plugin within 1 year and above update period on the dashboard. This will also help the site admins to start considering an alternative for such plugins.
10:46 am
Thanks for a post on a topic that often concerns me. My clients are mostly new users, and assume anything they download from WordPress.org is going to be safe to use. Even on my own sites, that plugin that checked out fine when I installed it 5 years ago. Might it occur to me that it's been awhile since I installed an update for that plugin? I manage a lot of plugins on a lot of sites, so maybe, maybe not.
The problem is compounded by the lack of ability to filter by date of last update or compatibility with the current version of WordPress during a plugin search on WordPress.org. I have never understood why that is not an option.
It would also be helpful to see the date of the last update on all installed plugins in the All Plugins panel, since one otherwise has to access each plugin's page individually to access that information.
I wonder if a Wordfence alert could be added for plugins that haven't been updated in the past two years, and/or have not verified their compatibility with the current version of WordPress. That might encourage users to contact the plugin author, which might in turn encourage that author to update.
10:46 am
Thanks #TeamWordFence. You always get our backs on security issues...Thumbs Up guys!
11:15 am
I am DELIGHTED that you wrote this post. I've asked developers to update their plug-ins and let them know I won't use it until it's updated. Others have told me that's not necessary. That a plug-in doesn't need to be kept up-to-date and if it still works, why worry? Your post is spot on as to why it really is important to not use outdated plug-ins. THANK YOU!
11:20 am
Always best to research any plugin before installing. If it is not actively maintained, do not install it. You do not even want it as "inactive" on your site(s).
11:21 am
I think that rather than remove them, both plugins and themes should be categorised with the info that the Word Fence team have highlighted. So, Number of uses, Last Updated, Version Compatibility and so forth. If there is a list of vulnerabilities as well then list those as well.
Then, people can make informed choices.
12:19 pm
Great, but what do you do if your site depends on the plugin you use and there is no simple fix? Just disabling a plugin might be wise advise, but it doesn't take into account why the plugin has been installed in the first place - because it benefits the site in some crucial way. Some sites are based around a particular plugin, it's not like choosing an alternative font for example. This is precisely why I steer customers away from Wordpress sites unless they really need one (most customers don't) and those designers that only provide Wordpress sites should have a think - and maybe brush up on their coding.
12:25 pm
I don't think a few outdated plugins is any reason to throw WordPress under the bus. There are thousands of well maintained and secure plugins that are completely free, take 30 seconds to install and save WP site owners thousands of dollars on custom development.
I would also point out that custom code is not peer reviewed to have vulnerabilities discovered the way popular open source is. Being widely used and open has distinct advantages when it comes to security.
Mark.
12:28 pm
A well written plugin (using WordPress API) could continue to work forever and not need to be updates, so it would be wrong to remove such a plugin.
"potentially harmful" would have to be clearly defined before being applied.
12:44 pm
Just because the plugins are out of date though doesn't mean they have vulnerabilities. A brand new plugin could easily have a vulnerability. Some of them are so simple they don't need any further updates. This may be obvious but many of the comments so far seem to be calling for all older plugins to be removed. It's bad if your developer has made poor judgements in picking plugins. If a casual user has done it then well, respectfully this is why we are professionals in the industry, you can only dumb it down so far for non-technical people.
Somebody raised the "what do you do if your site depends on these plugins" the answer is that you should sell your services to clients as an ongoing basis. If they aren't paying you a retainer for security updates and maintenance of this type then you are stitching up your clients. They need to be educated that their website is not a static product and needs to be maintained over time. Most businesses make money through their website in some way or the other, be it generating leads or e-commerce. In my experience they jump at the chance to have this kind of ongoing protection but they were completely unaware it was needed until it was explained to them.
A developer should create a plugin which checks if you have any of these plugins installed and alerts you if it finds them. I guess WordFence will be busy building this into their firewall product.
1:24 pm
This is a fantastic post. I have learned a lot about outdated plugins and I'm sure others have too. Thanks for teaching us more about our security.
2:04 pm
I think one of the worst offenders is W3TC cache
It has more users than any other caceing plugin.
However it has only been updated once in the last 3 years and that was about 6 months ago.
Dev's have updated copies of it and uploaded them to the stack so people could use them.
Dev's have tried to communicate with the vendor for the last 3 years and he never replies. They have tried to take it over and fix it but Wordpress won't let them. There is a process to overtake and fix abandoned plugins and these dev's have applied for that and WP keeps denying. The update fixed a major security flaw that allowed hackers to attack websites. I personally think the only reason why the vendor did the bug-fix was to avoid litigation.
Don't know what his problem but he's actually got more paid users out there than free so you'd think he'd care about people that have bought his product. I would consider 1 upgrade in 3 years to be abandoned. Use W3TC caching engine with care. I personally stopped using it after it caused a new website to crash without even doing hardly any settings yet and it was the only plugin I had at the time I had barely set any parameters.
You can forgive a plugin vendor that has all free users, but one that has paid users is kind of scummy in my humble opinion.
2:10 pm
Mark I agree about Word Press
While I get frustrated with WP from time to time over some of their boneheaded decisions, I love the WP platform. It went from being a dull - low imagery mundane blogging platform to being full of beautiful brite and creative website of high professional quality.
Most of the dev's and designers and seo people i know won't touch a project unless they're working in WP.
There are a lot of good quality vendors out there in both the theme and plugin market. I don't know a stitch of programming, other than simple or basic html or css but I can create some websites that the best developer of even 5 years ago would be jealous of.
2:48 pm
I just want to thank you guys for the outstanding work that you do for the Wordpress community.
4:08 pm
Wow. A blank list. Are you engaged in unnecessary use of JavaScript here? or is there something else amiss?
4:45 pm
Sounds like the table didn't appear for you?
7:43 pm
Yup. Out of curiosity, I checked why that would be the case. And, indeed, you're using Javascript for something that should be done with XHTML and CSS.
As JavaScript has been a recurring source of security issues, your visitors who are aware of such issues don't blithely have it enabled.
10:24 pm
JS is an integral part of the web. If you're not using it you're having a fairly miserable experience online.
4:29 pm
Thank you for this. It's easy to check installed plugins/themes that need updates, but it isn't as obvious when one hasn't had an update in quite a while. I ran into that with one of my favorite plugins. While it's not on the list, and I don't *think* it would do anything that left a vulnerability, I still went in search of a new one.
6:14 pm
Wow, thank you for letting the community aware of these vulnerabilities so users can take actions necessarily.
I've not used any of these plugins but would be helpful to others. it is really recommended to ONLY install plugins which are up to date.
Keep it up.
3:23 am
Oh god. i am using some plugins which you listed. And thanks for the info now going to delete and install trusted ones...
Peace \/
4:14 am
Thanks for this.
Do you have any advice on how we can check a plugin is safe to use before we install? Like is there a good scan that checks for vulnerabilities or anything in the code that may hijack our installation before we install?
Kind regards,
Mike
7:12 am
I think one of the big things here is making sure that you evaluate your plugins before installing them. Plugins with a high usage and pro version are more likely to be supported and updated over time. Keeping WordPress and the plugins you install updated will help to keep your website secure against attacks.
8:27 am
It has excellent plugins in Wordpress that are already obsolete ... you need to encourage donations to its creators so they can devote more time to updates ...
11:42 am
I have several sites that I created and maintain. Plugins are a big part of the success of each page. All components within each website need to be evaluated, and it is the webmaster (i.e. MY OWN!) responsibility to make sure that I am using the tools and properly maintaining my website's security with products like Wordfence.
Would it be nice if WordPress eliminated old, abandoned plug-ins? Yes, of course, and a protocol should be in place by them to notify the plug-in creator/s and advise that they have x-amount of time to review, revise and update their plug-in based upon the vulnerabilities or it will be permanently shut down by WordPress. But they (the creators) should also be required to notify plug-in users if they are closing down their operation and moving on. WordPress might have a responsibility to oversee this, in order to protect all of us clients, but legally, I would imagine that they are not *required* to do so, despite the obvious danger it presents to websites and webowners. Perhaps WordPress could shut down the plug-in and maintain it within the repository as "inactive", and if the owner ever reestablishes contact, it could be made "live" again.
Ultimately (I will say it again), the responsibility is ours and ours alone - as site owners and webmasters - to preserve and protect the integrity of our websites and the consumers and individuals who visit them.
So, I always pay attention to Wordfence notifications when I get my emails about my websites. I review the plug-ins and update them. And if one seems like it should have updated and doesn't, I'll review my own usage of that product and determine if there is another plug-in tool that might be more effective and current, and more properly maintained. Who needs the headache of Google blacklisting?
Besides Wordfence, I always add a login changer plugin. I view these as my first best option to protect my websites from being compromised. And, from the information Wordfence provides me, I'd say it is well worth it. (and thank you Mark! You have my appreciation and loyalty!)
Once upon a time, I used another security protocols services plugin, but I spent more time reviewing and revising my settings than working on my website. Wordfence is simplicity and peace of mind, all in one.
2:48 pm
Have trusted Wordfence for my security needs for several years now. I am going to have to remove a favorite plug in because the owner has health issues and is not able to keep it updated.