The September 2017 WordPress Attack Report
This edition of the WordPress Attack Report is a continuation of the monthly series we’ve been publishing since December 2016. Reports from the previous months can be found here.
This report contains the top 25 attacking IPs for September 2017 and their details. It also includes charts of brute force and complex attack activity for the same period, along with a new section revealing changes to the Wordfence real-time IP blacklist throughout the month. We also include the top themes and plugins that were attacked and which countries generated the most attacks for this period.
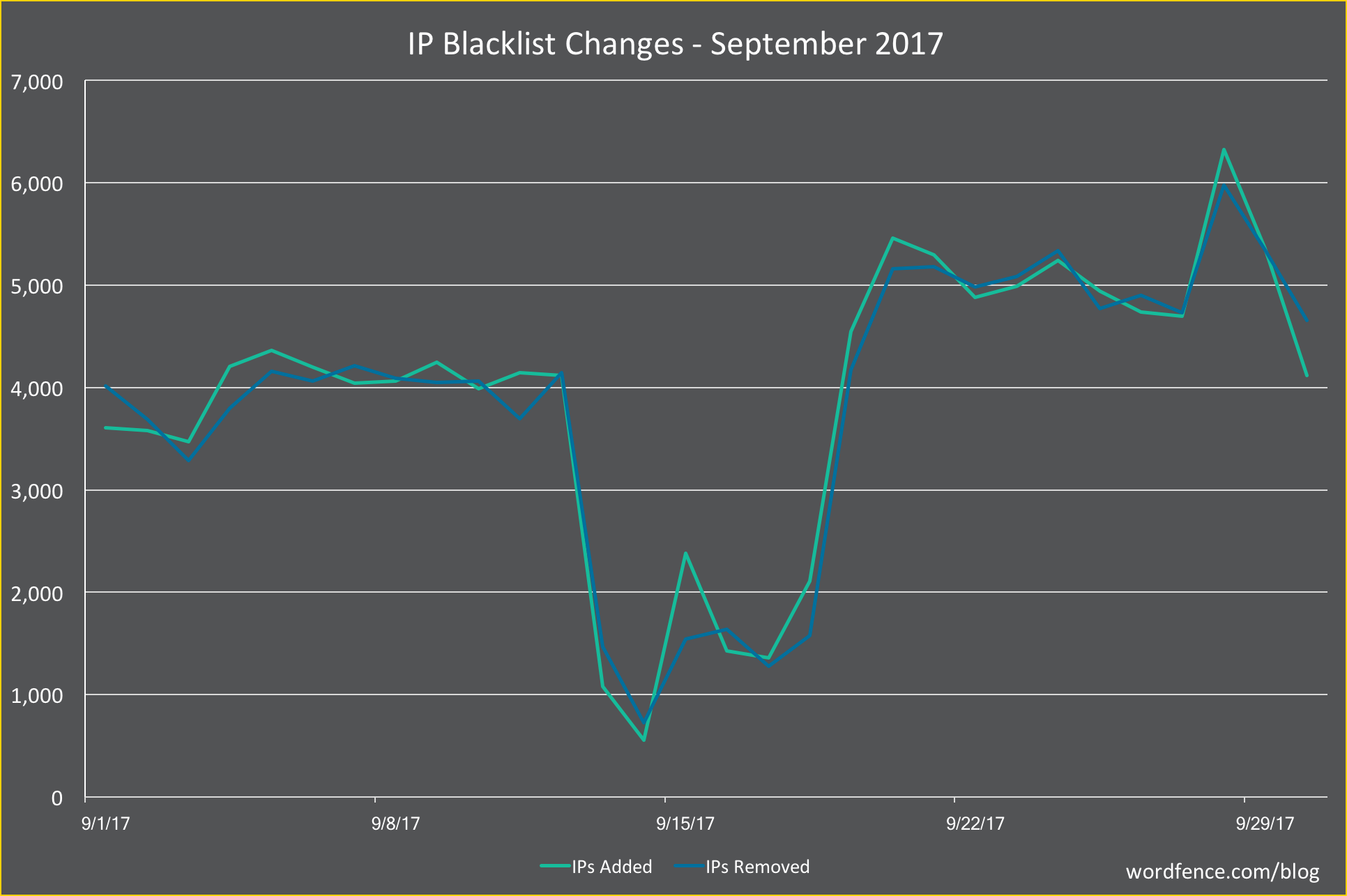
Real-time IP Blacklist
The Wordfence real-time IP blacklist protects our Premium customers from attacks originating from the most malicious IP addresses. Two weeks ago we shared a deep dive on how how the blacklist changed throughout the month of August. The post was well-received, so we decided to include some of that information in these monthly attack reports going forward.
In the graph below we show the number of IPs added to the blacklist each day in green and the number removed in blue. A total of 117,516 IPs were added during the month, an average of just under four thousand per day. An almost identical number was removed.
The Top 25 Attacking IPs
The next section is our standard explanation of how the table below works. If you are familiar with our attack reports, you can skip down to the table below this section, which contains the data for September along with some commentary.
Brief Introduction (If You Are New to Viewing These Reports)
In the table below, we’ve listed the most active attack IPs for September 2017. Note that the “Attacks” column is in millions, and is the total of all attacks that originated from each IP. Farther right in the table (you may have to scroll right) we break down the attacks into “brute force” attacks and “complex” attacks.
Brute force attacks are login-guessing attacks. You can learn more about how brute force attacks work in our Learning Center article about them. What we refer to as “complex attacks” are attacks blocked by a rule in the Wordfence firewall.
We have also included the netblock owner, which is the organization (usually a company) that owns the block of IP addresses that the attack IP belongs to. You can Google the name of each owner for more information. A Google search for any of these IP addresses frequently shows reports of attacks.
The hostname included is the PTR record (reverse DNS record) that the IP address owner created for the IP, so this is not reliable data, but we still include it for interest. For example, we have seen PTR records that claim an IP is a Tor exit node, when, based on traffic, it is clearly not.
We also include the city and country, if available. To the far right of the report, we show the date in August when we started logging attacks and the date the attacks stopped.
The Top Attacking IPs
The total attacks from the top 25 attacking IPs decreased by 8% from August.
Brute force attacks made up 91% of total attacks for September, the same as August. Complex attacks accounted for 9% of the volume.
Turkey topped the list this month with 11 of the top 25 IPs after having disappeared from the list last month. The four most active IPs were from Ukraine, with PP SKS-Lugan hosting three of them.
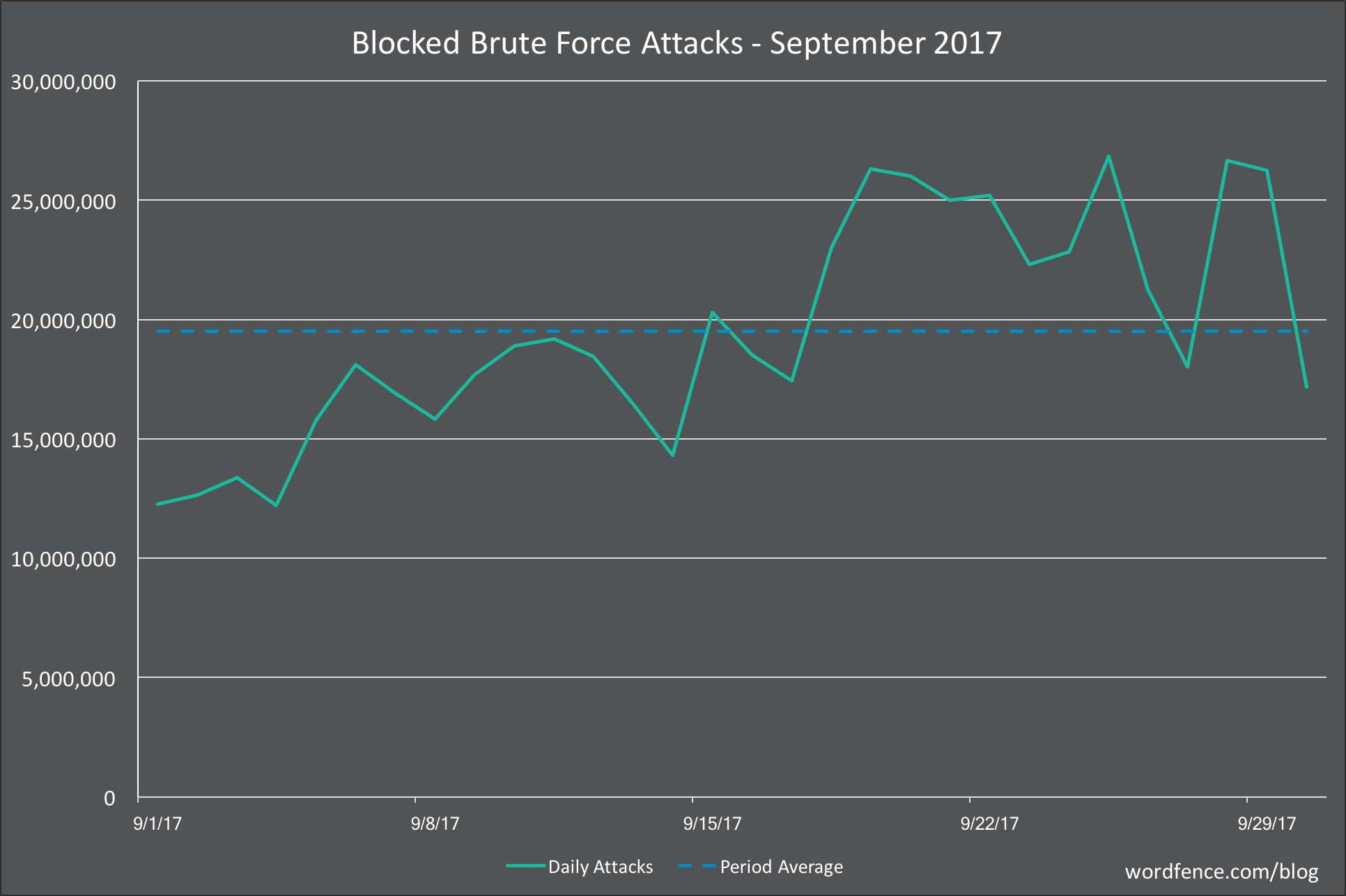
Brute Force Attacks on WordPress in September 2017
In the chart below, we show the number of daily brute force attacks on the sites we monitor for the month of September.
The average number of daily brute force attacks was down a massive 45%. Daily attack volumes grew toward the later half of the month, but were still very low relative to normal months.
Complex Attacks on WordPress in September 2017
In the graph below, we show the daily complex attacks (attacks that attempt to exploit a security vulnerability) for September.
Average daily attack volume for September was down 39% from August for the sites that we protect at 4.7 million. With the exception of a single spike on the 29th, daily volume was significantly lower in the back half of the month.
Attacks on Themes in September 2017
The table below shows the total number of attacks on WordPress themes. We identify each theme using its slug, which is the directory where it is installed in WordPress.
As usual we saw a lot of movement in the top 25 attacked themes. The biggest move on the list moved up 1,382 spots to number 9. We have redacted the theme name as it appears to be contain an unpatched vulnerability. We will attempt to reach out to the author to share what we’ve discovered. It is a premium theme with extremely low lifetime sales quantity. Over 98% of the attacks on this theme originated from just 5 IP addresses, suggesting the attacks are likely the work of a single attacker.
The second biggest mover was the ‘revelance’ theme, moving up 1103 spots to number 18. The attacker is attempting to exploit the very well-known TimThumb vulnerability. ‘Revelance’ is a premium theme that has been around since 2014, so we assume that at one time it included a vulnerable version of TimThumb.
The ‘rightnow’ theme was our third biggest mover for the month. The attacks on this theme are attempting to exploit an arbitrary file upload vulnerability from 2014. The theme appears to be abandoned, as we were unable to find any trace of it online. If you’re using this theme, we recommend that you replace it immediately.
Attacks on Plugins in September 2017
The table below shows the total number of attacks on WordPress plugins. As with themes, we identify each plugin by its unique slug, which is the unique installation directory where the plugin is installed.
As usual the top 25 list for plugins was pretty stable at the top, with quite a bit of movement toward the bottom. There were 9 plugins on the list that weren’t in the top 25 in August. We looked into the details behind the first big mover toward the top of the list, Zen Mobile App Native. Attacks on this plugin are trying to exploit a remote file upload vulnerability that was publicly disclosed on February 28th of this year. The plugin has been removed from the WordPress.org plugin directory, so we assume that a fix has not been released. If you are running this plugin we recommend that you remove it from your site immediately.
We have redacted the details for the next big mover on the list, number 14, because the attack vector may not have a fix yet, so we don’t want to call attention to it and turn it into a much larger problem. (Note: We regret we can’t answer questions about this privately or in the comments.) We were unable to find a reputable source of information on either plugin or the vulnerability. It isn’t listed in the WordPress.org plugin directory, and doesn’t appear to ever have been. We are attempting to reach out to the plugin author to share what we’ve discovered.
Attacks by Country for September 2017
The table below shows the top 25 countries from which attacks originated in the month of September on the WordPress sites that we monitor.
The top of the list was pretty stable, with the United States and Russia trading places at the top and the Ukraine holding at number 3. Turkey jumped into the number 4 spot from 7 with a significant increase in overall volume.
Conclusion
That concludes our September 2017 WordPress attack report. We find the dramatic drops in the complex and brute force attack volumes encouraging, though not necessarily indicative of an ongoing trend. Regardless of the volume of attacks, WordPress website owners should not let their guard down, but instead stay vigilant about their site security with up-to-date firewalls and other security best practices to keep their sites safe.


Comments
10:00 am
Seeing a plugin or theme in the attack tables that I know is used on a site I host is "stressful". Reading the report as currently designed, I have no clear idea how to make use of that information, what action to take, or whether I need to be concerned at all.
It would be very helpful if the "Attacks of Plugins" and "Attacks on Themes" tables had a "Details" column with a URL link that describes what versions of the theme or plugin are believed vulnerable, and any other info known about what the attack is trying to do/how to protect against it. This would turn the monthly report into something webmasters could actually use to improve WP security. If providing this info for the entire Top 25 is too much work, maybe at least include this info for the Top 10 plugins and Top 10 themes?
11:03 am
Hi Jonathan, thanks for the suggestion. We'll consider adding that in the future.
11:13 am
Strongly agree with @Jonathan Marsden on having a column in the table detailing plugin versions that are vulnerable, and what known steps can be performed to mitigate things, if any.
11:35 pm
I love this plugin and recommend to all, even the companies I do work for.
I'd like to see the IP blacklist as a Free feature and as Wordfence are in the know, create an RCA or SSL plugin for data or forms. The most common option which could weaken a site and most users require.
I would be happy to have an auto blog on my site for Wordfence for additional features like that. A report to that tells me for my website this data for affected plugins and themes automatically would be awesome.
Understand it all costs money, but when people start out, budgets are tight. An auto blog and WebLink or ad on my site for Wordfence would not bother me for what this brilliant software does.
It's a must for anyone with WordPress.
3:08 am
I am not very technical to recognize all the Data you are giving; but it is sure comforting to know that you are trying to keep us safe by keeping the thieves at bay, and naming the.
Ira