WP-VCD Evolves To Remain Most Prevalent WordPress Infection
Early last month we released a comprehensive paper covering WP-VCD, the most prevalent malware campaign affecting the WordPress ecosystem in recent memory. In this paper we examined the campaign from a number of angles, such as the behavior of the malware itself, its method of distribution, and its evolution over time.
The presence of threats like WP-VCD demands that WordPress users remain vigilant about the security of their sites in the long term. Scams like these are prolific for a reason: They’re effective. Our data shows that WP-VCD is still infecting more new sites per week than any other active malware campaign. Even after publishing a paper on the campaign, we have yet to identify any meaningful change in the rate of new infections.
This lack of impact suggests an issue of user demographics. Simply put, it’s unlikely that security is a priority for the WordPress user who downloads pirated content from back-alley websites. Neither the whitepaper itself, nor reports from popular security news sources on the subject, would ever have been on that user’s radar. This reinforces an important point: Awareness is your most valuable security tool.
In today’s post, we’re going to look at what’s changed with WP-VCD between last month and today, and share some tips for staying vigilant against this threat and other scams like it.
Recap: What is WP-VCD?
WP-VCD is a malware infection designed to target WordPress sites by hiding in nulled, or pirated, plugins and themes. Its controllers exploit their victims to boost search engine rankings for the sites that distribute the infected code. The attackers then monetize the campaign with malvertising scripts, which trigger potentially dangerous popups and redirects for the victim sites’ visitors.
It’s a sophisticated campaign. It preys on unaware WordPress users looking for a way to get free access to paid content. Then, by using newly infected sites to draw more victims in, it can maintain a reliable base of compromised sites even as earlier victims clean up the mess. Lastly, the campaign is resilient. In the event that one of WP-VCD’s command and control (C2) domains are taken down, it can quickly rotate in a new one.
Some details were still unclear when we wrote the report, however. We hadn’t been able to identify where the campaign hosted its infrastructure. All domains used in the campaign, from the malware’s C2 sites to the SEO-boosted sites distributing the infected content, had DNS routed through Cloudflare’s content delivery network (CDN). This abstraction allowed the campaign to run without revealing the IP addresses behind it all.
Intervention From Cloudflare
Cloudflare acted quickly when we published our report. Less than twenty-four hours after the paper went live, access to WP-VCD’s C2 domains had been limited by the addition of a warning page.
While a human visitor could click through to see the content behind the warning page, a call from an infected website wouldn’t make it through. This prevented WP-VCD’s victim sites from accessing the /code.php and /o.php endpoints, which distributed instructions and registered newly infected sites.
The campaign’s C2 domains were the only ones affected by this intervention. Cloudflare did not add warnings to the sites responsible for distributing the infected plugins and themes.
DNS Exposure
Since the malware scripts could no longer access their C2 sites, WP-VCD’s controllers were forced to pull those domains from Cloudflare’s services.
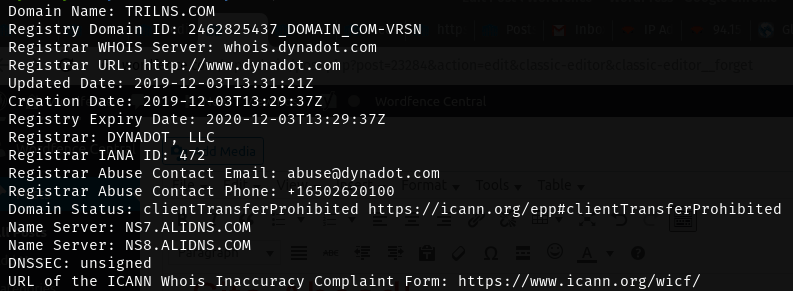
Beginning November 5th, less than a day after the campaign’s exposure in our whitepaper, WP-VCD moved its command and control DNS away from Cloudflare. The new DNS provider is AliDNS, a service associated with Alibaba, the Chinese tech conglomerate.
While Cloudflare provided CDN services which concealed the primary server behind the campaign, AliDNS did not. The C2 domain’s DNS records were now pointing directly at a single address: 94.156.175.170.
Researching The Host
The IP address 94.156.175.170 points to a cPanel server belonging to Verdina LTD, a company ostensibly based in Belize but with servers in Bulgaria.
This isn’t the first time hackers used Verdina’s servers to perform criminal activity without reprisal. In 2016 it was revealed that DDoS-for-hire service vDOS was hosted across four of Verdina’s servers. The service was also known for allowing IP spoofing, which made “stresser” services like vDOS possible. Hacking forum users have pointed out Verdina specifically as an example of hosts that were forced to stop spoofing in order to retain their allocated IP address space.
The company’s connection to Belize also appears to be exclusively a bureaucratic one. The corporate address listed in Verdina’s Terms of Service, 1 Mapp Street, Belize City, Belize, suggests a relationship with International Corporate Services, a financial firm designed to help you create your very own non-resident corporation in Belize.
We’re continuing to investigate activity associated with Verdina’s IP address space.
Testing The Host Server
As we detailed in the whitepaper, WP-VCD’s C2 sites rotated through new domain names frequently. We included more than a hundred in our report, but it’s safe to assume there have been more than that. What we didn’t know, due to their use of a CDN, was whether the attackers were rotating servers behind the scenes as well. With one domain name now pointing to one server, we needed to test if that server could be linked to previously used C2 domains.
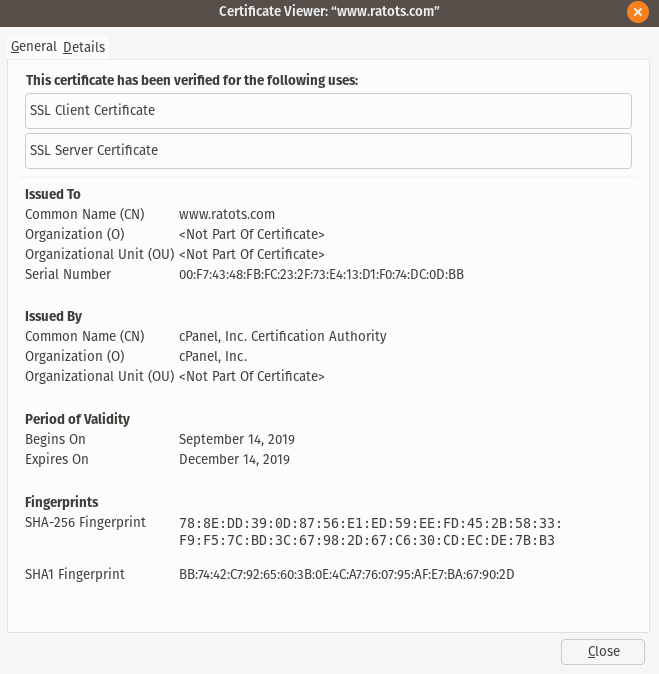
For example, the C2 domain active at the time of this writing is www.trilns.com (Note the www. in the address, these domains have always required the www. subdomain to resolve). An HTTPS request to 94.156.175.170 for the hostname www.trilns.com will receive a valid TLS certificate for the domain, which was generated by the cPanel server running the site. Since the server administrator would need to intentionally generate each certificate, we could test the server for the existence of certificates associated with earlier C2 domains.
In our testing, we were able to confirm the presence of valid cPanel certificates for all of the command and control domains we tested, even those not actively used in years. We also confirmed that this server hosts ins.spekt.pw, a domain used as part of WP-VCD’s viral marketing campaign.
SEO-Heavy Download Sites Still Behind Cloudflare
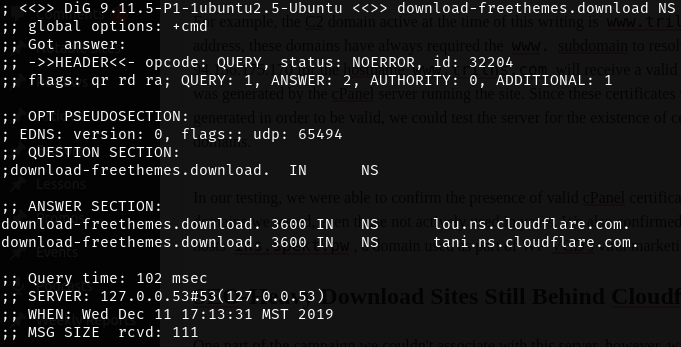
One part of the campaign we couldn’t associate with this server, however, was the distribution of infected plugins and themes. While an old, broken version of vestathemes.com could be found on 94.156.175.170 with an expired certificate, we determined that server wasn’t the current host of it or the other sites in the distribution network like downloadfreethemes.co and freenulled.top. We also hadn’t found the origin server behind the site hosting the actual infected zip files, download-freethemes.download.
Each of these sites, entry points for unknowing WordPress administrators to infect themselves with WP-VCD, were still protected by Cloudflare’s CDN. It is unclear at this time why Cloudflare intervened with warning pages on the C2 domains but not the sites reached by human visitors.
…But We Found Them Anyway
The C2 server at 94.156.175.170 broadcasts its hostname as vesta.vestathemes.com. With that in mind, we searched Shodan for other hostnames or service banners associated with the vestathemes name. Two different addresses were calling themselves server2.vestathemes.com: 94.156.175.192 and 94.156.175.193.
Using the same tests as before, we determined that 94.156.175.192 is the origin IP behind the nulled content distribution network. This includes the SEO-boosted domains advertising the infected plugins and themes, as well as download-freethemes.download, the site the zips are actually downloaded from.
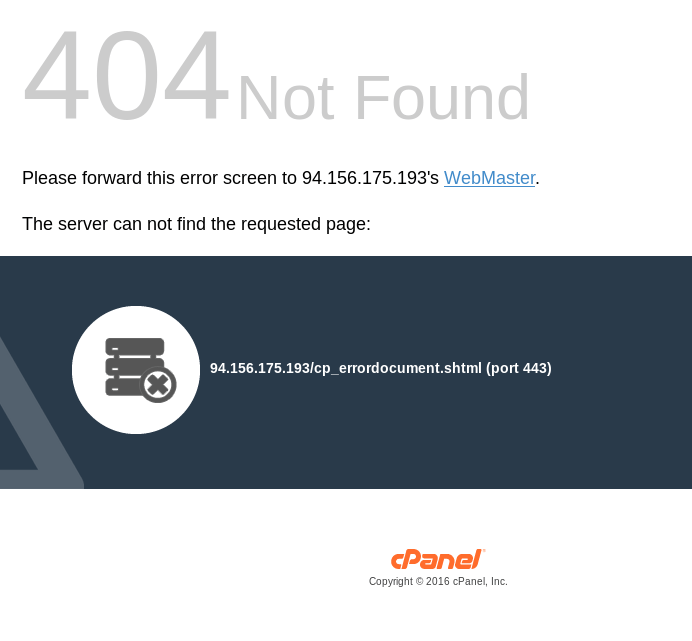
The remaining address, 94.156.175.193, is still under investigation. We have not affirmatively associated this server with any outward-facing activity. However, navigating directly to either IP address and forcing a cPanel 404 page reveals a mailto: link for x1ngbox@gmail.com. Those who read the WP-VCD whitepaper will recognize this as the primary email address associated with the WP-VCD campaign.
Tips For Remaining Vigilant Against Scams
- Be responsible with the third-party code you add to your website. While WP-VCD is simple enough to avoid by steering clear of nulled plugins and themes, recent history has shown that even ostensibly-legitimate developers are capable of adding questionable code to their products.
- If you are not personally handling the development of your website, ensure you fully trust the people you’ve assigned the task. Less-than-reputable “gig” developers, who claim to offer full custom site builds for a price that’s too good to be true, frequently cut corners that will cost you headaches at minimum. Even if they’re not intending to infect your website, they’re still interested in cutting costs by getting commercial themes for free, and they’re not sticking around your site long enough to make sure it’s clean.
- As a general rule, never trust a page you didn’t intend to visit. WP-VCD and other recent attack campaigns have been identified injecting malvertising scripts. These scripts redirect a site’s visitors to unwanted locations. These pages attempt to trick you into giving them what they want. This includes phishing for logins with claims like “You must log in to your Google account to view this content”, or prompting you to engage in a tech support scam by claiming your device is corrupted or infected. They’ll also ask mobile users for permission to receive push notifications, which can be used to send further spam notifications.
- Periodically visit your sites from new devices and locations without logging into them. WP-VCD’s malvertising code attempts to hide itself from administrators by storing a cookie on their device and logging the IP address they connected from. That way, even if the admin logs out, it can still hide until they clear their cookies and connect from a new IP address. This technique is not unique to WP-VCD, and can be useful in identifying other malicious activity that would have otherwise gone unnoticed.
- If your site was a victim of WP-VCD or another malware infection, you should inform your users as quickly as possible. Responsible site ownership means being forthright about the fact that your site’s visitors may have encountered dangerous code. Plus, depending on the way browsers cache your site, some of your visitors may still see an infected version for a while after you’ve cleaned it. Giving your users a heads-up isn’t just the ethical thing to do, it demonstrates to them that their security is a priority.
Conclusion
The actors behind the WP-VCD campaign have shown that they are quick to respond when infrastructure changes are necessary. It’s possible that new changes are forthcoming in the wake of the campaign’s recent information leakage. It’s hard to say how this campaign may evolve further over time. Continuing trends in the detection of new WP-VCD infections suggest that the campaign is going as strong as ever.
Preventing your site from falling victim to WP-VCD is simple: don’t install nulled plugins or themes. Not only does it take money from the folks who built the content, but sourcing code from untrustworthy sources has clear negative implications for the health of your website.
Because awareness is the most effective defense against infecting your own site, you can help spread this defense across the WordPress ecosystem. Share the WP-VCD whitepaper, inform, and educate less technical users so they’re empowered against the malicious actors that prey upon a lack of awareness. WordPress is stronger because of the community, and our educational efforts make us all stronger.
If you’re curious for more detail about WP-VCD and haven’t read it already, check out our report: WP-VCD: The Malware You Installed On Your Own Site.


Comments
2:58 pm
I appreciate these updates even though I only understand about half of it. I'm a stone mason not a tech guy. You guys protect my site and I'm glad you do because I would be lost at sea if one of these campaigns got in there. Thanks so much!
11:16 pm
Thank you so much for this informative article.
I clean more than 100s of website which was infected by this malware