Hacking a WordPress Botnet
While analyzing some of the attacks we see on the Wordfence Web Application Firewall, we discovered code that an attacker was trying to upload that was part of a botnet. In case you’re not in the information security space, a botnet is a network of ‘bot’ or ‘zombie’ machines that is controlled from a central command and control or C&C server.
In the case of this botnet, it was controlled via a chat service called IRC or Internet Relay Chat. IRC is a popular way of controlling botnets because you can have all the ‘bot’ or zombie machines connect to the chat server and join a channel to receive broadcasts. This allows the botnet owner to simply sign into the chat server and broadcast commands to all the zombies which they run at the same time.
The code below shows a typical hack attempt where the attacker is trying to inject their botnet code into a targeted WordPress site. Wordfence blocks this attack and any attack that includes this botnet code.
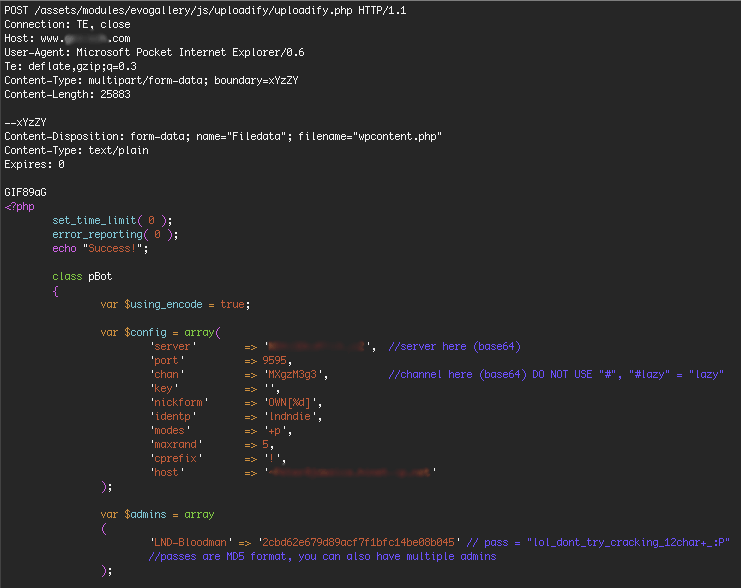
Once a WordPress site is compromised with this attack, the infected server connects to an IRC chat server, ready to receive commands and do the botnet owner’s bidding.
The owner might use those zombie WordPress sites to attack more sites. Or he might use them to launch a distributed denial of service or DDoS attack on someone, overwhelming them with traffic. He could also simply deface all the sites in his botnet with SEO spam.
The hashed password is shown next to LND-Bloodman’s username above. We’ve blurred the encoded command and control server IP address. The content length is over 25K so this is a reasonably long script.
The Wordfence team decided to analyze the botnet code and try to identify who was running the botnet.
Going After the Command and Control Servers
During our analysis of the malicious code, we found five IP addresses of IRC command and control servers (C&C servers) for this botnet. Two of them were down. Three were still up.
We created modified zombie code to connect to the C&C servers and do further analysis. Our code was designed to save all files it was commanded to download. It would also log all commands sent to it and not actually do anything malicious.
The botnet owner’s nickname/handle appears to be Bloodman.
One of the things we were hoping to get by doing this is Bloodman’s password that he uses to control his botnet. He had built his botnet zombie code so that whenever he sent a command to the zombies via the C&C server, it included a password.
The zombies would hash that password, compare the hash to what is stored in the code and if it matches, would know it’s Bloodman sending the command and would run the command.
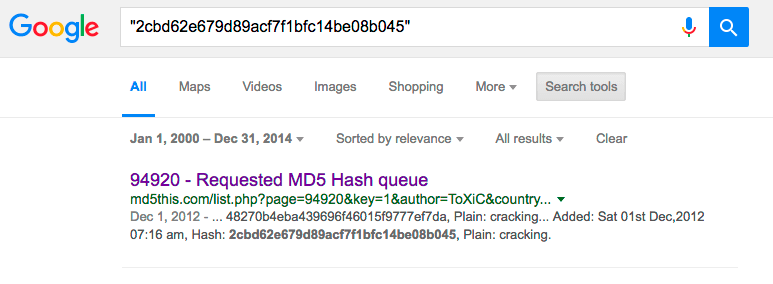
The hash we found in the code, as you can see in the above image, is:
2cbd62e679d89acf7f1bfc14be08b045
Googling this hash shows that the malware with this password has been seen before. A blogger saw an attack containing this hash in September last year.
The oldest Google result mentioning this hash is from December 2012 and is a request to crack the hash and turn it into the password which is still unsuccessful. This indicates with a high degree of certainty that Bloodman has been active and using this password since December 2012.
If one can reverse this hash, you can simply sign into any IRC server that Bloodman is using and have immediate control of his botnet.
We connected to all three of his C&C servers and after watching and waiting for about 48 hours we hit the jackpot. He signed in and sent a command to the botnet. We captured his password. The first part of it is:
1x33x7.0wnz-your.************
We’ve intentionally starred out the rest of the password (which is long) to prevent anyone else from taking control of these botnets.
This allowed us to take control of his botnet if we wanted to. It turns out Bloodman also refers to himself as 1x33x7.
At this point we connected to one of the botnet servers:
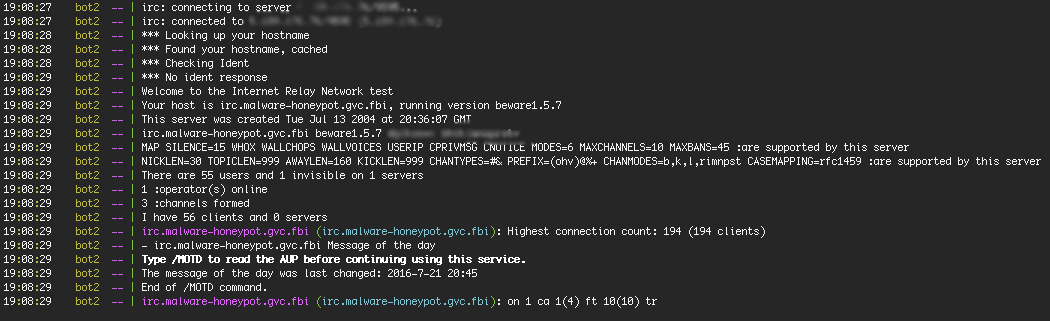
We’ve blurred out any IP addresses or identifying information. The server is named to look like some kind of FBI honeypot. Considering it’s actively hacking WordPress sites, we’re guessing it’s a joke on the hacker’s part.
Joining the channel #1x33x7 where all the bots hang out shows us the following when we ask for a list of users:

There are 31 infected machines shown excluding the three users. And there is also LND-Bloodman hanging out in the channel.
The format of the nicknames shows some information about the compromised system including what web server software it’s running.
Running IRC’s ‘whois’ command on a few of the zombies shows that some of them are FreeBSD unix boxes. Others are running Windows Server 2012 or Windows 8 – both identify as “Windows NT 6.2 Build 9200.”
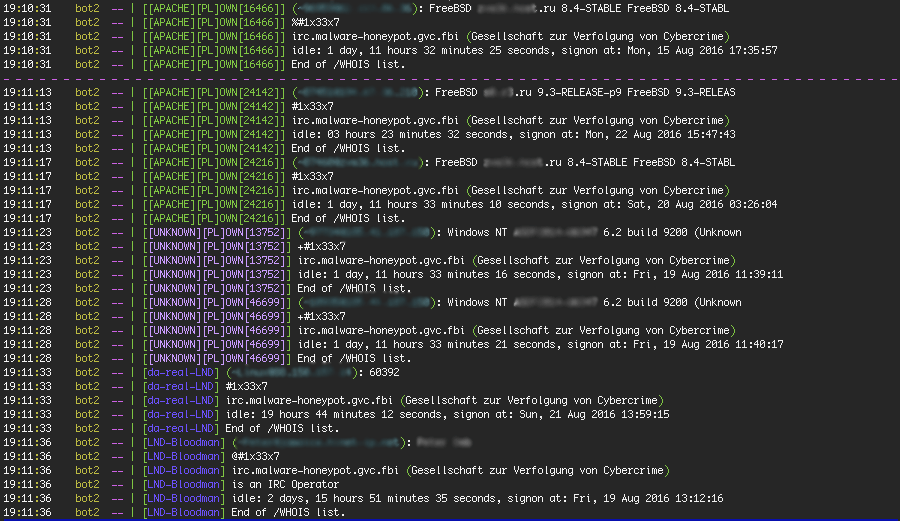
Running ‘whois’ on the two Bloodman accounts gave us two IP addresses and a possible email address with a first name.
At this point we have enough information to go ‘active’ and take control of the botnet and shut it down. The botnet has enough functionality for us to first delete any infected code and then kill the processes running on remote machines, thereby destroying the part of the botnet that is connected to this command and control server.
We chose not to shut down the botnet for two reasons:
Firstly the Computer Fraud and Abuse Act does not allow us to hack the hackers. So even though we had passively connected to this hacker’s command and control system, going active and changing the system could land us in some hot water with the FBI. We would rather observe and report because that is all the law allows unless you work for the military or a military agency in the United States.
Secondly, we were concerned that we may not have all the information and we may actually do harm by trying to disinfect remote machines.
We don’t think that shutting down a single C&C server or even all three C&C servers and their respective bots would do much good. Bloodman would simply regroup and reinfect new sites with new C&C servers.
Attribution – Who is doing this?
To try to determine who controls this botnet, we started with both usernames that appear in the source code: Bloodman and 1x33x7. One of those usernames pointed us to a Twitter account. The Twitter account contains a german slogan “I am root” and various images of what is probably the botnet owner’s face.
The Twitter account links to a YouNow profile which is a live video broadcasting service – it uses the same username.
The YouNow profile linked to a YouTube account that uses the second username, which contains plenty of identifying information and a video of the botnet controller bragging about his botnet. He speaks German, likes to play with fireworks and we know what car he drives and have images of various German roads.
In addition to the open source intelligence above, we mined public data leaks and found a user profile on a hacker website that includes one of the usernames and the IP address the user last signed in from. That IP address is in Germany and belongs to Deutsche Telekom. Providing this to the authorities would probably reveal his full identity from ISP logs.
Conclusion
This is a small botnet with under 100 infected machines when you combine all the C&C servers together. This individual is launching under 2000 attacks per week. While they are inconvenient and consume resources, they are all blocked by the Wordfence Firewall.
We are working with net block owners to let them know about machines, particularly C&C servers that are on their network and are likely compromised.
We think that discussing the tactics, techniques and procedures of attackers, both small and large helps us all better understand what we are protecting our WordPress sites against and how to do a better job.

Comments
11:35 am
This was fascinating to read. Did you report him to the police in Germany?
Keep up the good work.
11:37 am
No we did not. Thanks for the feedback Jay. Will do.
12:03 pm
Um, why did it take a comment on this article for you to contact the authorities? It seems to me that once you'd reached the "anything else would be illegal" stage (I.E. taking control) the next logical step would be to turn the botnet information over to the appropriate agencies.
1:53 pm
Michael, you have to keep the context in mind: What the WordFence folks did here was the equivalent of carefully observing and documenting how a pickpocket operates. There are thousands, perhaps tens of thousands of "Bloodmans" out there.
What Wordfence learned (and shared) is far more valuable than going after this one guy, because his methods are probably shared by many others.
Should it be report and ideally, he would be pursued? Absolutely. I'm guessing that neither U.S. or German authorities will be greatly interested unless there's evidence Bloodman is causing significant financial or political damage. Just too many other, bigger hacks going on in the world.
4:31 pm
He was replying "will do" to the last part of the comment...which was "Keep up the good work".
5:22 pm
The "will do" was in response to "keep up the good work", not the "did you report him".
11:38 am
Great work you guys!
11:39 am
I'm curious if you were able to find anyone in law enforcement that was even mildly interested in pursuing this asshat?
11:43 am
Hi Scott,
It's an interesting debate. This isn't a big fish by any stretch of the imagination. It also requires significant effort on our part to reach out to german authorities, find the right person, hope they're interested, provide evidence in an ongoing investigation etc. I don't think this attacker is a big enough player to justify that level of effort, but I'd like to hear thoughts from the rest of the community.
Our approach is really to treat the symptoms by doing a very effective job of blocking any attacks guys like this launch and doing ongoing deep analysis of their TTP's.
Mark.
12:02 pm
What if you just, in a very thinly veiled highly hypothetical sense, elude to the fact he is connected with ISIS and this botnet is helping fund their cause? It's a theory, but I bet you several agencies and governments will drop everything to investigate! ;) (come now, trump makes more outrages claims than you would if you did and chose your words correctly)
12:33 pm
Even a small hacker can have other usernames that control other or larger botnets. or belong to a group that does. I'm sure the authorities would find out more but if you never give them a chance we will never know.
3:37 pm
Hi Mark. Thanks for the reply... and thanks for all your work on this one (and for sharing). One of my "day jobs" is helping to run an online classified ad website and trying to keep the scammers at bay. Catching any one of them would be relatively easy, but it has been impossible to find anyone in law enforcement that cares. They tell me that I would need to document at least $250,000 in losses to get their attention. In other words, they are not interested in pro-actively taking down a scammer... they have to wait until there are victims which have suffered huge losses. It's a sad situation.
Since you are open to public comment on this... I say... yes, go ahead and try... and document what you do and how it goes. I think the entire story, from beginning to end, should be told. It may be eye-opening. In other words, why let this be the end of the story. The process of contacting law enforcement, the (likely) pointing of fingers, the (likely) passing you from one place to another, etc., would all be as interesting to read as the first half of the story (in my opinion).
P.S. did not realize you a ham... me also! That is awesome!
- Scott
5:29 pm
Hi Mark,
From my personal experience I can tell you that contacting the national CERT team helps. They usually act like middlemen between authorities and the one reporting a crime. Or at least they do here in Romania.
11:40 am
It may be small-time, but guys like BloodMan can grow to be big problems if they aren't controlled.
Thanks for taking the time to write this article! A very interesting read, as I feel like I know individuals who like to play around like this and aren't aware they are also being watched. Looking forward to your next update
11:42 am
Sad that you are more cautious about getting into trouble with the FBI than tackling this scumbag! It seems that political correctness is the actual winner here and not the forces of right!
11:44 am
Ha! David take a look at the penalties the CFAA provides. They're severe. But yes, this is a very heated debate within the infosec community and I feel your frustration.
11:42 am
Always love ur blog posts where you detail such methods. Now matter how small, I hope you also reported this to German authorities, have a log and even confronted this so called 'hacker'. It would be more awesome if you can then show us some conversation you had with him (with translation of course). Want to know the mindset behind these (i know it's not always money)
I am surprised people still use IRC (esp this so called hacker..maybe he thought no one uses it thats why decided to use it cause its free to use a public server... But it is not private at all! Bad move on the hacker part.
Once again. Great post. Thanks
7:01 am
It's not a public server and IRC is still going quite strong ;)
IRC will never die, I think.
Faithfully,
-k0nsl
11:42 am
Fascinating and well played - keep this up.
11:44 am
Great job guys, thanks for making the Internet a safer place. Your plugin is amazing... Did you report the guy to the german authorities?
11:44 am
Awesome work as usual.
11:46 am
Excellent work and thanks for the report.
I'm also glad that Wordfence is on the job and I don't need to worry
about our sites being hacked.
11:46 am
Awesome Mark!
I found this fascinating too. What did you do in this event? Did you report what you found to the FBI or someone else?
11:48 am
Wow! Amazing work.
11:51 am
While I am not at any means a network guy, this was very interesting reading how you were able to trace this information. Thanks for all your hard work.
11:54 am
Nice post. Written well and very clear. Great job!
11:54 am
Fascinating! When I read that you didn't take control of the bot, I thought, "What's the hacker going to do, report you?" But, I understand and appreciate your integrity. Keep up the great work, and thanks for the protection!
11:58 am
Hmm ... I wonder if this is the bot that tried to access my site yesterday from various parts of the world?
You asked for thoughts on turning him in: I think you should report him. Yes, he may be a little fish, but little fish grow up to be big fish and get into lots of trouble. Nip it in the bud, so he knows he isn't invincible and that someone is watching him (because, hopefully, someone WILL be watching him after this).
11:55 am
My site was attacked by this botnet.
I have permanently block all attacking ip addresses. Attacking was from Worldwide, from many different countries
11:57 am
Awesome effort, great job! Too bad you can't hack the hackers...
11:58 am
Great work! Very interesting to read.
11:58 am
Interesting read! Please do more of this stuff :)
11:58 am
Thanks for this very interesting post!
If you want to report what you found to authorities, this would be the contact to the cybercrime department of Germany's Bundeskriminalamt (BKA - similar to FBI):
Phone: +49 611 55-15684
SO41-NKC@bka.bund.de
6:49 pm
You should contact them yourself and refer them to this article. I'm sure they would appreciate it. Wouldn't it be a shame if he was a person known to the authorities, but they didn't have enough information or evidence to nail him yet?
11:59 am
Jason Bourne works for Wordfence! Great work guys.
11:59 am
Wow, sounds like you all were having a bunch of fun chasing this down. Thanks for all the hard work.
11:59 am
Wow ! This was a comprehensive learning material. I wonder what benefit those hackers get from causing problems for others .. its negative behaviour.
12:00 pm
I was kind of hoping the story would end with a reverse code that would send Bloodman's motherboard into an endless loop of frantic confusion, melting into Picasso-esque picture of a phenolic board, with resistors dripping off the bottom edge. I guess the FBI won't let you do that, either, but I enjoyed the thought.
2:29 pm
Mike, I like the way you think!
Years ago a group of CB radio operators tracked down an asshole that was constantly interfering with user traffic with a high-powered (illegal) RF amplifier. That night a needle was driven through his antenna co-ax. When he keyed up he fried his amplifier.
He also received several not-so-veiled anonymous threats on his life and the well-being of his family, and his home address was repeatedly broadcast on all the channels.
His house and car was egged several times, and his tires were punctured.
... never heard from him again on the air ...
Legal? NOT AT ALL
Really friggin' effective, YES!
2:49 pm
Hey guys, as always thanks for your input. Just want to reemphasize that we don't condone witch hunts and in fact we actively discourage anything like that. I think I mentioned that in last week's post.
I think the trick here is to get the data out in a way that exposes bad behavior, gives the community the information it needs to protect itself and then see it's dealt with in the proper way. Bruce, while I can understand the temptation to do that kind of thing, let me share a similar story where an offender was dealt with properly.
I'm a radio ham and have been for several years now. For a while there was a guy on 14Mhz who was behaving really badly. The FCC went after him, triangulated him and fined him $3500 late last year. That's more money than a new amplifier costs and the penalty if he is a repeat offender will be much worse.
http://www.arrl.org/news/florida-ham-agrees-to-penalty-for-failure-to-identify
As always, thanks all for your comments. Sorry to be the boring voice of reason.
Much appreciate the input.
Regards,
Mark.
3:27 pm
This was a fascinating article. I'm glad we ( you and others that understand it all) were able to get some good information from the operation. I am confused and a bit concerned why things in the virtual world are sooo different from the real world. If I witnessed a crime and was able to learn how it was plotted, planned and executed that could be really helpful to stop others, but I'm not sure it would be ok to just let the crook walk away free from consequence. Isn't the new idea... See something, say something. Well, again thanks for sharing the article it was very interesting.
4:06 pm
Very well put Mark.
Once again you and your team are outstanding.
12:01 pm
Fascinating
12:03 pm
Fascinating read.
I hope you muster up the time to report this to the German authorities of the FBI since they are the ones whose penalties are restricting you.
If they do nothing that is on them but at least a report has been made.
I believe that is the responsible thing to do.
Then, when he gets better at his craft, there is a paper trail to maybe nail him for something significant.
Big criminals start small.
12:03 pm
Thank you guys for what you've done. I'm not sure whether it was this guy but one of my websites had ver 700 attacks in a day - fortuately, Wordfence stopped it but it was quite scary.
12:06 pm
Really interesting read. Almost thought I was in a Jason Bourne movie for a second. Keep up the good work and thanks for your protection.
12:08 pm
Great work once again to you and your team....your service have made life easier to do business online...Thanks for the time you take to do these research...
12:09 pm
im 35. is it too late for me to become anti hacker? i also want to protect and serve internet "dummies"! where do i start? can anyone take me in as their forever loyal student?
12:13 pm
Your mission if you choose to accept it: http://overthewire.org/wargames/natas/
10:49 pm
Thanks Mark!
8:34 am
That's actually a very cool learning exercise! Unfortunately I only made it to Level 2. LOL!
12:17 pm
We have a saying in the industry: Try harder. This is where it comes from (which includes more useful learning material for you) https://www.offensive-security.com/when-things-get-tough/
12:10 pm
I would encourage you to make some kind of report to appropriate authorities in Germany, the USA, wherever.
All of the most dangerous and predatory hackers started small. I may be that this person is only playing around and will never be a real threat, but you never know. If his identity and MO is in a police database, it may be helpful in minimizing some future attack that does real damage.
12:13 pm
I'm sure the NSA has a job for you!!
12:15 pm
Mark, try contacting the local chapter of the Association of Certified Fraud Examiners in Germany. They are very active in fighting cybercrime and will likely know how to reach the proper authorities. They might even do it for you.
Vlbeler Landstrasse 255
Frankfurt / Main, 60388
Phone: +49 61967695401
E-mail: roki-kilian@t-online.de
Website: www.acfe.de
1:39 pm
YAY! Exactly. Rather at least trying than doing nothing. Even just a small fish can grow big. Those guys have to learn straight from the start. I quite often report just little attempts to any abuse email address. I do not mind whether they will ever do anything about the script kiddies and others, but at least I reported it.
Without reporting, surely nothing will happen.
12:17 pm
Spending your time learning more about the bot networks and the hackers and perhaps learning ways frustrate or defeat their efforts seems like a much better use of your time than trying to provide users with lists of IP addresses to manually block bots. There are just too many of them. The software to create bot networks is readily available on black sites.
I'm not sure where I saw it but I watched a video of a group that tracked a hacker back to his FB account and actually had pictures of the Russians who were doing the hacking.
12:18 pm
I am continually amazed at how many failed login attempts I receive each day for our business website. I can't imagine the benefits of being able to hack our site. Then again, I'm certain there must be something in it for the other people. This is a really interesting read. I am continually pleased with the protection your company provides. Thanks.
12:32 pm
I used to be quiet involved in online fraud, 419 scammers etc. I remember one conversation with Law enforcement where they practically pleaded with me NOT to give them information as I was not a "registered source" and I could not be.
Any information I gave would be inadmissible in court.
If WF were to do one thing out of line, it would be impossible to convict the scammer.
I have a lot of respect for WF especially after the last weeks episode with the dodgy WP plugin maintainer. I do believe that the best way to combat this is "slowly slowly catchy monkey". This might not give you fast results but it will give you longlasting ones.
That said I would love to have burned the feckers machine!
12:36 pm
Sounds like a lost episode of Mr. Robot! :)
12:38 pm
I also ask, have you reported this guy to the FBI and US Military Intelligence? I would also send a report to the RCMP in Canada. The more agencies that know about this slug the better.
Kudo's to gaining access to his server(s).
I have also noticed that Germany has been one of the high number of hack attempts on my client websites. Likely it was him.
12:45 pm
For all who are critical about Mark not authorizing a takedown, he is absolutely right to be cautious, legally and ethically. It's easy to act tough about how you would handle it, when it's of no consequence to you. The fact that he shared the process and evidence is to be commended.
It's not a question of political correctness (a term that gets bantied about on political grounds a lot here in the State's these day), it's about balancing the good you can do without crossing the line of legal liability, your business policies and interests, and the bigger picture. Believe me, we go down that road more often than I'd like here. Mark, you and your team rock. Kudos from ours to yours ?
12:46 pm
I am one of your premium members and I totally appreciate these type of reports. I am writing an ebook to educate my audience on what is truly happening with our websites. A lot of what I know now came from working with your plugin which is amazing.
I acknowledge you guys for the work you do! Superb!
P.S. I posted the article on my Facebook Fan Page but your page here did not count it. Check it?
12:49 pm
I've restricted access to /wp-login/ by modifying the .htaccess file. I wanted to share:
order deny,allow
Deny from all
# whitelist
allow from ##.##.###.## (YOUR IP)
1:18 pm
Umm, Dan, did you raecd the first line in the post above? Protecting wp-login does not do ANYTHING in this case as he is uploading his code to the evoplugin. This is only one of many (old) compromised plugins.
I see this all the time bots trying to upload stuff to plugins. One mildly helpful solution is to block access after 1 or a few 404's, cause they are trying known vulnerable plugins.
1:06 pm
Thank you for sharing this article and congratulations for your excellent work!
1:11 pm
Wow! :o
Great work, Wordfence!
1:17 pm
As always, fantastic work guys!! We love to read your in depth description of attacks. Thank you for your work.
1:19 pm
This was fascinating. Two of my sites have been under attack for weeks, and as I was reading this report more notifications came in. It occurred to me that both are running the Deep Focus theme, so I am going to change them and see if it stops.
I was hacked many years ago and 1500 malicious files (some bank information phishing files) were imbeded. Not fun. They gained account access as well and sent out a 100k webmail blast to email addresses in France through a proxy in Houston, and got my account shut down. The web host actually accused me of doing it, so I moved right afterward.
All I can say is that I'm very grateful for the work you guys are doing on Wordfence now, and for the continued updates on what you're doing.
Cheers
John
1:43 pm
Great work guys, however:
You went all that way, waited 48 hours, monitored it, investigated etc and then telling me that the effort of reporting it was not worth it because of a small fish... ???
Well, a small fish will grow big eventually.
Why not at least trying to report? Better than doing nothing. You know, you can write to German authorities in English ;-) Even if you do not find the correct person, chances are that eventually it will end up with the right one.
1:58 pm
Nice work. Appreciate you sharing this story and commend you on the effort. Thank you.
1:58 pm
Awesome work! Although I do agree with those who believe that this hacker should be 'dealt to'. I prescribe to the old adage of 'a stitch in time, saves nine'. These parasites need to be exposed and held legally accountable before they get better at their 'trades' and cause even more damage. 4 years of 'criminal activity/nuisance' is no passing fancy and the resources already expanded to counter his actions must surely be reason enough for legal enforcement to be involved. If there, isn't such an avenue in place, then we (You who work behind the scenes on this type of work) should be lobbying our Governments to set something up.
2:07 pm
I wouldn't worry about reporting this guy. I would continue to learn all you can. Little guys communicate with other hackers. They learn on the same hacker boards. They teach each other. I run numerous websites, and am constantly amazed at the number of hacker attempts I receive every day from all of my little websites that have nothing to do with anything important.
We are in a digital war, and the combatants are not allied with countries, they are allied with others of the same ilk. We need to continue research, share our research, and block enough to make it unprofitable.
Take out this one and 50 others will slide into their place. There are a lot more of us than either the government or the ilk. If I were a better programmer, I would spend my time doing what wordfence is doing. But I would turn their bot on themselves any time I got the chance.
2:15 pm
Nice work, Mark... Fully concur with the view of getting to the operation when it is small...
Potentially, does this work (and publishing it) increase the likelihood of attacks focused on WordFence?
2:23 pm
No. But they may try to DDoS our site in which case we'd work with the authorities and employ our own DDoS mitigation which we've used in the past.
2:20 pm
Thanks for the great work and article, guys! It reminded me of Cliff Stoll's book "The Cuckoo's Egg" about his experiences tracking a hacker in 1986.
2:25 pm
Sometimes keeping an eye on the little fish and his activities (and progression, and ideas) is more valuable than slapping him down and making the other fish dive deeper and get sneakier/smarter. There are always bigger fish, and this actually keeps us safer this way. Good job Mark, et al! And thank you for all that you do.
2:30 pm
Some fantastic work, we did similar with a locky virus which seemed to trim elements of text from a sentence and then combining it with another command from another string of words. The commands made no sense but there is extreme lengths some of these people go to, to hide their dirty work and that's what is worrying.
3:27 pm
Thanks for the sleuthing. I wish that there were more actions you could take against this reprobate.
3:31 pm
Great work there.
3:31 pm
Great detective work. Fascinating reading. Once again, thanks so much for the great service you folks perform.
3:37 pm
Awesome sleuthing Mark. You guys do such a great job. One of my sites was suddenly under a brute force attack a week or so ago - I hadn't yet implemented one of my other smaller (but effective) strategies or included all of WF's options that I have available to me there - when I did, it was smooth sailing again.
Thanks for all you do! ❤️
4:16 pm
Nice job! This guy seems to be a script kiddie wannabe because he didn't even cover his tracks well at all. He should have never linked his aliases to any personal accounts or went bragging on youtube. The fact that his system had glaring security flaws that allowed his info to get sniffed is funny as well. I can't even respect this person as a "hacker", just probably a teenager thinking they are cool playing the role of a "hacker".
4:34 pm
Excellent article guys!!!!!!!!!!! keep up the great work :)))))
4:47 pm
Hi, thanks for reporting this. Like many previous posts I also believe this should be reported to appropriate authorities (although I concede that there may be actions you've undertaken that you did not describe in your post).
I recommend reading "The Cuckoo's Egg" by - from memory - Clifford Stoll. The technology used is now well dated, but the process he used to track down a hacker and the potential impacts of the hacking activity make for a compelling read.
5:55 pm
Apologies to Terry (about 10 replies up) who'd already mentioned "The Cuckoo's Egg".
4:51 pm
Keep in mind that some of these bot networks have connections to organized crime. If you go too public with what you are doing you could be putting yourself or your employees in danger. Ask John Horton.
6:21 pm
Reading this was awesome. Maybe a little tweet or message to this guy on his profile pages will have him poop his pants LOL
6:38 pm
I tweeted this article to @Interpol_Cyber
6:55 pm
Heh if you fu****s [starred by mod] will choose to delete every post that is bad 2 your plugin.... sooner or later you'll run into some one that will unleash a hail storm against your plugin. What you Give... or Deny... is What You Get!
6:58 pm
Do not try to fu** [starred by mod] with people like only sweet and nice post... are posted on your article. You can sensor out shit... on your blog 4 sure... but people GET PISSED BOUT THAT! AND MAY DO SOME RESEARCH INTO YOUR SHIT THAT YOU WILL NOT LIKE SO MUCH!
6:30 am
I research some basic literacy education first, if I were you ;-)
10:38 am
Now that is some collection of words. Do you provide a cypher anywhere? Or is that really all you have to work with?
7:22 pm
Great work and article. Thanks for doing what you do.
Cheers.
8:41 pm
The main takeaway here is that every site owner should be updating with security patches at least once a week. It would seem that some people aren't even trying, and perhaps like Microsoft no longer supporting windows 95, 98, etc. sites running an outdated OS should be taken offline by the network hosting company. Just a thought.
11:58 pm
A note to those that are frustrated by not being able to do anything: one of my sites was pretty heavily infiltrated by cialis spam last year. It took me a while to notice. After cleaning up the site, I continued to get spam links from at least 20 other sites in the spammer's network every so often. Each time I discovered a new link, I checked the sites and sent them a note showing pages on their sites that they did not know existed and introducing them to Wordfence and another similar service (I didn't want to be perceived as a spammer myself). Five or six of the sites got back with very embarrassed but grateful messages. So the spammer's network was at least partially dismantled, and the number of spammy links with medical keywords pointing to my site was reduced. It took a bit of time, but my messages were cut'n'paste after the first and I had the feeling I was doing something.
It's scary the number of sites out there that are either dead but still running, or have owners that are completely unaware of these issues and the basic rules of "hygiene" on the web. A number of the sites were either community, religious or charity sites. Sad.
12:12 am
As usual another great article and a great job! My sites get a lot of rogue traffic from Germany. Maybe this traffic is orchestrated by LND-Bloodman...
Thanks for keepin' the bad guys out!
12:18 am
Have you guys reported it to the FBi cyber division?
12:29 am
great article, really enjoyed this, well done! if i was this guy i would not brag about what i am doing, not even try and publish my activities to social media.
1:05 am
Really interesting article. It's captivating to read about hackers side of the biz. Thanks for your work !
1:45 am
Nice work. Highly appreciated.
2:21 am
I'm sure there are members of law enforcement that monitor this blog. They're probably now aware of the situation and may decide it requires some attention.
2:40 am
Thanks for taking the time to put up the post, really insightful info.
Great post, and great plugin. Keep up the good work!
2:45 am
I've read all the article and I'm impressed how things move around the internet and it's very hard to observe what's in fact behind.
3:38 am
Great job wordfence!!!
It's a great knowing some one out there cares
thank you for sharing
Awesome article to felt like I was there
Cheers
4:07 am
The main takeaway here is that criminals can mess around all they want with computers, even become known, and probably experience no consequences except possible monetary enrichment and possibly the satisfaction of of their criminal impulses.
I was delighted to read that Wordfence was being proactive, until I finished reading and found out this was just more of the same letting hackers run roughshod wherever they pleased, only now we know the guys name. Or perhaps we don't.
W
4:59 am
Awesome read thank your for this great article and keep up the great work.
5:10 am
Excellent article, the level of analysis was fascinating, you would like to think that zero tolerance should be the underlying attitude to these actions but this article shows some perspective on the practical challenges facing the police: http://www.thelocal.de/20140603/internet-crime-in-germany-at-a-record-high
8:35 am
I have to say, an article like this (and more specifically the ensuing discussion about legality and the lack of consequences for a hacker like this) illustrates why I stand behind Wordfence on issues like the recent Plugin injecting spammy links into site code intentionally. The sad fact is that almost none of the hackers that do things like this will ever face any real world consequences for doing so. The argument that there are "bigger fish to fry" is absolutely absurd; if someone breaks into your house and steals something from you, the police don't get to say "sorry, there are murderers out there, we have bigger fish to fry..."
That being said I am not naive to the fact that enforcement issues in a case like this are a sketchy at best. Many times something that to most of us would seem illegal in fact skirt the law quite intentionally. Technology progresses at such a rate that it is difficult if not impossible to legislate against the next type of attack because we often don't even know what it will be.
It may be disheartening, it may be frustrating, it may be "unfair," but the fact of the matter is that if you plan on using the internet to any significant degree and especially if you are the webmaster and/or designer of one or more sites, you are responsible for your own security within that space. This is why we need services like Wordfence; because most of us need a little help, and even if our "bodyguard" isn't legally allowed to tackle our attackers, they can at least point them out and tell us what's going on.
Keep up the good work guys. The more we all know the better able we are to protect ourselves!
2:07 pm
Mark thank you for sharing this, I really appreciate it, now we know a little more about the other side
4:44 pm
A top read that! Well done guys, you are certainly on the ball.
10:48 am
Thanks for this article. I see a lot of people suggesting the legal (law enforcement) route.
Actually, have most of you looked at the news lately? The extent to which law enforcement is being stretched and the limits government has placed in front of those wanting to be protected, has resulted in an ineffective worldwide system.
There comes a time when people like those running Wordfence do a greater service by exposing the tactics of people wishing to do harm, and providing insights which may spark the interest of someone who may come up with a way to even better protect websites and content from harmful intent.
Fact of the matter is, regardless what were to happen if the authorities were notified, the result would very likely be that one person may receive a penalty and then return to do exactly what he was doing before. And he would be laughing all the while.
I prefer to see what is happening so I can show my own clients why it is so important to keep their sites and servers up to date.
Thanks again for this article. Very interesting read.
6:46 pm
Thanks Wordfence for this article.
But is fully disagree on not reporting to the law enforcements.
If this hacker is successful with his attack, how small he is the damage for the admin/company/organizations can be huge.
Also what is the border when to do reporting and when not.
For me personally every non ethical hacker they should cut of there hands. I was hacked a few years ago, before I started to use Wordfence. My sites are clean but I still suffering form this hack.
4:06 pm
Very interesting read. Thanks for sharing!
12:44 am
What an interesting read. Thanks for sharing the whole story and showing us the code. Its very intriguing to see how you catch these guys. Thanks for another great post.
10:45 am
Great work, guys, in tracing this weasel and his evil network!