This site uses cookies in accordance with our Privacy Policy.
1.1: How to Protect Yourself from WordPress Security Issues & Threats
This document is designed to help you understand the basics of WordPress security. In it we’re hoping to give you a working knowledge of who is attacking your WordPress site, why they attack it, and how they try to get in. We also hope to give you a working security vocabulary so that you can more effectively communicate with your fellow system administrators and security professionals.
WordPress is the most popular publishing platform in the world. It runs over 34% of all websites worldwide. WordPress is also open source. What this means is that the code that runs WordPress is visible to everyone. Because it powers so many websites, it has become a target for hackers who want to infect or control websites.
Think about it this way: If you are a hacker and you want to infect as many websites as possible, you could try to find a security hole in the individual software that runs on each website, or you could find a security hole in the most popular software used by websites and infect them all. If a hacker can find a security hole in WordPress itself, or a popular theme or plugin used by WordPress, it allows them to very quickly infect a huge number of websites using automated attacks.
For this reason, finding a ‘zero day’ security hole in WordPress is sought after by hackers because it can lead to the ability to control a huge number of websites. A Zero Day Vulnerability is a vulnerability that the software vendor has had “zero days” to fix because they are not aware of the problem yet. It’s the best kind of security hole for a hacker because anyone who is running the newest version of a particular piece of software is guaranteed to have that security hole with no fix available.
Who is Attacking my WordPress Site?
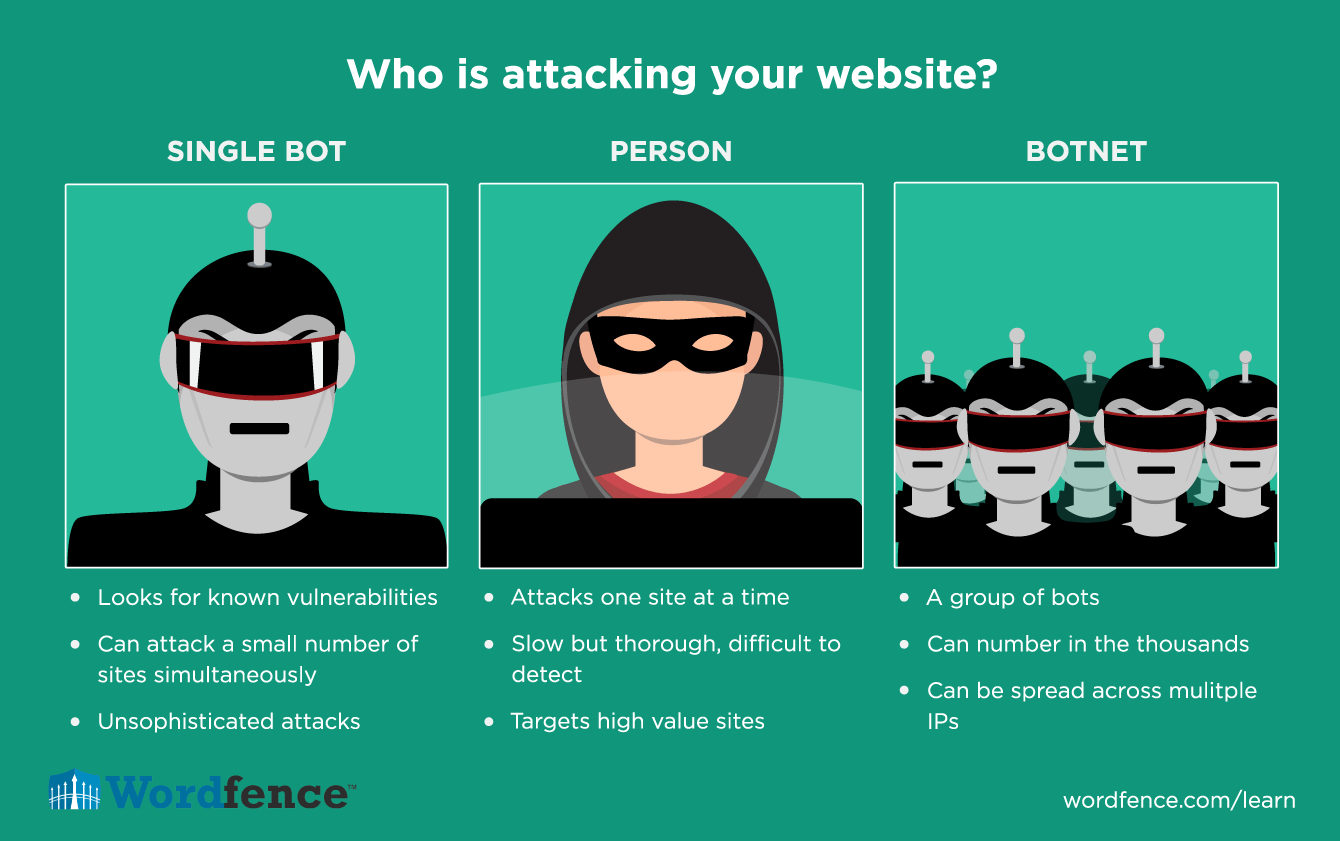
In general there are three entities that attack WordPress sites:
- Humans: This is a person sitting at a keyboard manually probing and attacking a website.
- A Single Bot: This is a single automated program or script that a hacker is using to attack many sites in an automated way.
- A Botnet: This is a group of machines running programs that are coordinated from a central “command and control” server (C&C server) that are attacking many sites in an automated way.
Human Attackers
Having an individual human manually attack your website is rare. We all like to think we’re special and that our site is interesting enough for someone to give us the kind of individual attention we deserve. The truth is that a very small percentage of websites are targeted individually and an even smaller number have a live human trying to break in.
However, if you are targeted by a person, the level of sophistication of the attack is far greater than when you are targeted by a robot. A human attacker is able to control the speed at which they gather information about your site to avoid tripping any intrusion detection. They can then try a few attacks while being careful to not alert you and the systems that protect your site. They see the results of each individual attempt and can make decisions about how to proceed based on these results.
Most attacks involving a live human target very important websites including defense contractors, sites that contain sensitive private data and those that are financially very lucrative to attack.
Bots and Botnets
Bots are programs written by hackers that target a large number of websites looking for vulnerabilities in well known software like WordPress. It is relatively easy to write a program that visits hundreds of thousands of websites quickly checking if they are running a version of WordPress with a known security hole and, when found, to hack into (exploit) the site using that security hole.
Bots can be an individual program running on a single machine or a large number of machines running multiple versions of the program all trying to hack into a huge number of sites in parallel – also called a “Botnet”.
The vast majority of attacks on WordPress websites are performed by robots. The good news is that these attacks are not as sophisticated as human attacks and are also more aggressive. This makes them easier to detect. The bad news is that if a zero day vulnerability emerges for WordPress or a well known theme or plugin, it can be exploited extremely quickly through these kinds of automated attacks leading to a large number of sites that are compromised.
Important to Note: Most attacks are performed by Bots or automated machines. Because bots are so fast and effective at attacking large numbers of sites, it is very important that you close known security holes on your WordPress website as quickly as you can.
Why are they attacking my WordPress Site?
The goal of an attacker is to gain control of your WordPress website at an administrative level. This means that they can read all files and data in the database on your website. It also means they can modify files, make changes to the database and change the way your website behaves and the content it serves. They want to be able to do this for some of the following reasons:
To send spam: To be able to send spam email from your website. Hackers can run scripts on your website that bulk email their targets once they control your site.
To host malicious content and avoid filters: Hackers may use your site to host content like pornography, illegal drug sales or other spam content. Hosting bad content on a domain that does not yet have a bad reputation helps them avoid spam and other online filters.
To steal your website data: To access and harvest the data on your website including your customer and member email addresses and names. Stealing thousands of email addresses of your website members provides hackers with new targets to send spam and malicious email to. You may also have other interesting data like personal member information that can be useful in identity theft and other malicious activities.
To Spamvertize: To use your website to redirect traffic to another malicious or spam website. Including their own website in spam emails will land those emails in the spam folder if the website is known to be malicious. By including your website address in spam emails instead, the emails avoid spam filters. Then when someone who receives spam clicks on the link to your site, they are redirected to the malicious website. This is called ‘spamvertizing’.
To attack other websites: Once your website has been compromised, a hacker can use your site to run bot attack scripts that hack into other websites. Your website may become part of a cluster of machines called a ‘botnet’ which is a large group of machines used for bulk malicious activity.
Important to Note: Once your site has been compromised it will very likely be used for malicious activity. This has a high probability of ruining your website reputation. It will be penalized in the search engine rankings and may be blocked by browser filters like Chrome and the Google Safe Browsing list. For this reason it is important to detect a hack early and fix it quickly.
How are they attacking my WordPress Site?
There are typically two stages of an attack on any target website. The first is reconnaissance, where the bot or human attacker is gathering information about your website. The second is exploitation, where the information gathered is used to try to gain access to the website.
Reconnaissance (or ‘recon’)
During this information gathering phase an attacker will want to learn useful information about your website that lets them know what vulnerabilities may exist that they can exploit. The most important two things they want to learn is what kind of software your website is running and what are the versions of that software.
The reason this is useful is that there are many databases available on the Net that list versions of software and the vulnerabilities associated with each. For example, if a hacker can determine that you are running WordPress and that the version of WordPress you are using is 4.2.2, then they know that your website has a critical cross-site scripting vulnerability that they can exploit. If they see you are running a newer version, they can save time by simply not even trying to exploit that vulnerability. They also avoid detection by not exploiting vulnerabilities that don’t exist on your server.
Hackers want to gather as much information about your website as possible before trying to hack in, but knowing what software you are running and which version you have of each piece of software is extremely valuable. For this reason, one of the things that a hacker will do when attacking a WordPress website is to ‘enumerate’ your themes and plugins. This gives them a list of your WordPress themes and plugins along with versions for each. From this list they can very quickly cross reference their list of exploits and determine if it is worth trying an exploit on one of your themes or plugins.
When attacking a WordPress site, it is also useful to know what other WordPress installations a website has. You may have done a ‘lazy’ backup of your site by simply making a copy of your entire WordPress directory into a subdirectory. This is accessible from the web and when you do this you usually don’t maintain the files in the backup directory. Those files are still executable from the web and can be hacked the same way any WordPress installation is targeted. You may have other WordPress sites running in subdirectories that are also targets. As part of reconnaissance, a hacker will try to find all WordPress installations on your website.
WordPress websites often host additional software like phpmyadmin which helps with database administration. These other applications also make great targets, especially if they are not being kept up-to-date with the latest security fixes. For this reason an attacker will try to find all other software that is running on your site including the version numbers.
Important to Note: Knowing what software your website is running and it’s version is extremely valuable to an attacker because it provides them with a list of targets to exploit. There are services, including Wordfence, that can help hide your software version and that may slow down an attacker. However, simply hiding your software versions is known as ‘security through obscurity’, and should not solely be relied upon to secure your site. The best way to keep your website secure is to ensure that you are not running vulnerable software by running a well maintained website.
Exploitation
Exploitation is the act of actually hacking into a website. When you consider that there are large databases of vulnerabilities listed by software type and version available online, and that these contain full technical detail on how to exploit a vulnerability, exploitation seems like the easy part of attacking a site. Finding sites to attack and identifying vulnerable software on the site that is exploitable, the reconnaissance phase, is most of the work.
When a WordPress site is attacked, there are several main entry points or attack ‘vectors’ that are used:
- Your login page: This is the most common form of attack targeting WordPress. This is where most password guessing attacks or ‘brute force’ attacks take place. Attackers have automated bots that try to guess your website password by repeatedly trying to sign-in on your WordPress login page.
- PHP code on your site: This is the second most common form of attack targeting WordPress. Attackers will try to exploit vulnerabilities in PHP code running on your WordPress site. This includes the code in WordPress core, your themes, your plugins and any other application you are running. The way PHP code is exploited is wide and varied.
- Privilege escalation: Another popular vector an attacker might use is to gain access to your site using a normal user account with no privileged access. If you have registration enabled on your website, they can simply register to get an account. Privilege escalation involves using the access granted by that account and a software flaw to gain a higher level of access like ‘admin’.
- Old or unmaintained web applications: You may be doing a great job of keeping your WordPress website secure and in this case an attacker will look for other older and unmaintained web applications on your website that are vulnerable. If they can gain access via these applications, they can modify your WordPress files and infect your website, even though you have kept WordPress itself secure.
- XMLRPC Service: This service can allow an attacker to perform password guessing attacks. It has had other vulnerabilities in the past that allow attackers to target other websites via your site. However, it is important to not disable this service or you may lose important site functionality.
- Access via Temporary Files: When editing files on your website using tools like ‘vim’, temporary files may be created that contain sensitive login information. For example, editing the ‘wp-config.php’ file may create a temporary file that contains your database login credentials that is public. Attackers look for these files in the hope of finding sensitive information that will help them gain access.
- Source Code Repository Config Files: The ‘git’ and ‘Subversion’ source control tools create directories and files that can contain sensitive information. If you leave these files publicly accessible an attacker can use the data in the files and directories to gain access to your site or to help with recon. There have also been cases where a website owner will store their source code on GitHub or another publicly accessible repository and this is a gold mine for attackers looking for sensitive info to help with recon or exploitation.
- Attacks via shared hosting: Most low-cost website hosting plans place websites in shared environments. The security in these environments vary and among reputable web hosts is generally good. However, you may be in a shared environment where it’s possible to create permissions on your website files that gives someone else on the same machine ‘read’ or ‘read and write’ access to those files. If this occurs and someone who has access to your shared environment is malicious, they can use the ‘read’ permissions to read files like your ‘wp-config.php’ file and gain access to your database and all your member data. They can use ‘write’ permissions to drop malicious code or files onto your website which will then be executed and give them full access to your site and its data.
- Attacks via the Web Server and Operating System: Your file permissions and PHP code may be secure, but your web server itself may have vulnerabilities that can be exploited, like the Heartbleed vulnerability. You may also have vulnerabilities in the operating system that hosts your web server and website, like the ShellShock vulnerability. In a shared or managed hosting environment it is usually the responsibility of your hosting provider to keep these systems patched. You usually don’t have access to patch them yourself. However, if you are running a self-hosted website on a provider like Linode, then it is your responsibility and in addition to maintaining all your PHP code and web applications, you need to ensure that your operating system and all of its services are secure.
Important to Note: The number of ways an attacker can gain access to your website may seem overwhelming. Don’t let it be. To run a secure website, make sure that you know every version of every software and service running on your website. Then make sure that there are no known vulnerabilities in your software and services by keeping your site well maintained and keeping abreast with the newest security alerts and updates.
How to Protect Yourself
This article has given you an introduction to security with some basic concepts and has outlined who is attacking your WordPress website, why they attack and how the attacks are carried out.
It is probably clear at this point that to best protect yourself from attacks, it is very important to keep your website up-to-date and to keep abreast of the newest WordPress related vulnerabilities. This will allow you to update your site as soon as possible when a new vulnerability emerges. In cases where a zero day is announced, you will know to contact the vendor and work closely with them to find out when a fix will be released and apply that fix.
Intrusion detection and prevention software like Wordfence for WordPress also helps protect against common attacks. Wordfence also detects if your site has been compromised and, as you have learned, early detection is key to help preserve your online reputation. Wordfence also protects against common PHP attacks so that, even if you are running a vulnerable plugin and haven’t had a chance to upgrade yet, Wordfence will prevent that vulnerability from being exploited.
Here are a few key rules to observe to keep your site secure:
- Use strong passwords for all user accounts.
- Choose a reputable hosting provider where websites on shared servers are isolated from each other.
- Keep WordPress core, your themes and plugins up-to-date.
- Use an intrusion detection and prevention system like Wordfence as an additional layer of security.
- Remove all old and unmaintained web applications including old backups of the site from your website.
- Ensure there are no sensitive temporary files lying around on your web site.
- Ensure there are no subversion, git or other repository files publicly accessible.
We hope this article has served as a helpful introduction to WordPress security. If you would like to learn more, please visit the rest of our articles on WordPress security and how to run a secure website.

