Home Router Botnet Shut Down in Past 72 Hours. Who did it?
On April 11th, 3 weeks ago, we published a story discussing routers at a specific set of ISPs that have been hacked. These routers have been used to launch attacks on WordPress websites. The ISPs with compromised routers included Telecom Algeria, BSNL in India, PLDT in the Philippines and many more large ISPs around the world.
When we discovered this botnet over 3 weeks ago, we started monitoring attacks originating from those IPs. This allowed us to add the attacking IPs to the Wordfence Premium real-time blacklist to protect our customers.
Yesterday morning we noticed that there was a rapid drop-off in attacks from the ISPs we identified 3 weeks ago, that had targeted WordPress websites.
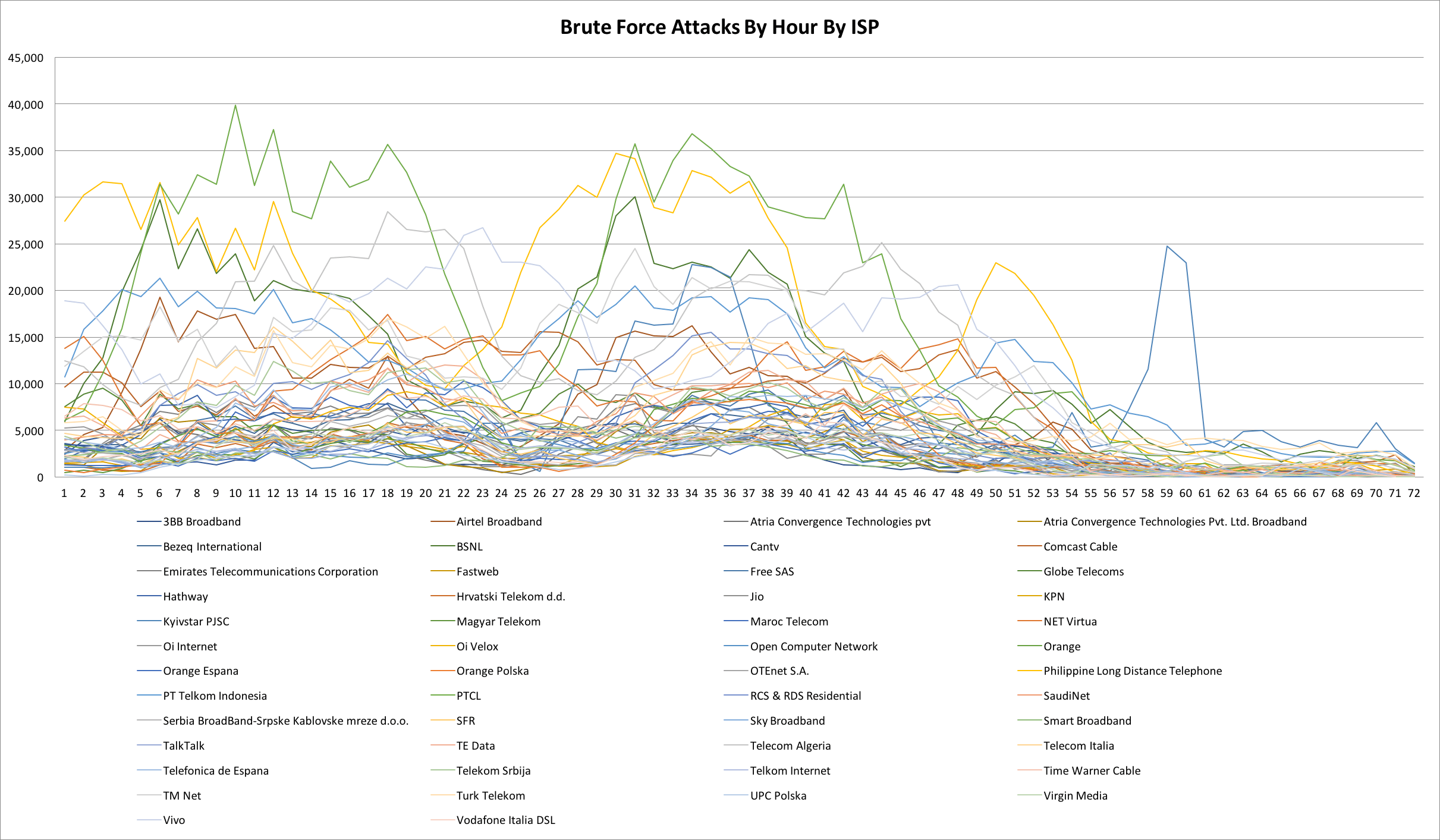
This is what the change in activity looked like from the top 50 ISPs from where these attacks were originating during a 72 hour period ending yesterday (Monday) evening. Click the chart for a larger version.
The chart above shows attacks per hour by ISP. This is the most recent 72 hour period, ending yesterday evening at approximately 5pm Pacific time. Each line is an Internet Service Provider from which these attacks were originating.
As you can see, starting at around midnight on Sunday night (April 30th) Pacific time, the number of attacks we are seeing from ISPs where we found vulnerable routers have dropped from peaks of 40,000 in some cases to peaks of just above 5,000 attacks per hour. In many cases the attacks drop to much lower levels and continue to decrease.
Why did the attacks stop?
The data indicates that this is a botnet that was acting in a coordinated fashion and attacking WordPress sites that we protect. In the past 72 hours, the attack frequency dropped simultaneously across hundreds of ISPs in many countries.
One possibility is that the individual or group controlling the botnet stopped attacking WordPress and that resulted in a rapid decrease in attack volume over a 24 hour period.
Another possibility is that the command and control servers of the botnet were taken offline by a coordinated effort involving security services in multiple countries.
It is worth noting that earlier this month, INTERPOL worked with investigators in Indonesia, Malaysia, Myanmar, Philippines, Singapore, Thailand and Vietnam to identify almost 9,000 command and control servers and just under 270 hacked websites. They produced reports for authorities in each country which allowed local enforcement to take action against the compromised systems.
This kind of coordinated action by INTERPOL is encouraging. It helps protect the global online community and creates a safer internet.
This is great news!
This reduction in attacks originating from hundreds of ISPs around the world is great news. Attacks on WordPress sites around the world have been reduced.
The attacks originating from these ISPs were also resulting in their IP addresses being blacklisted by Wordfence and other services like SpamHaus. That resulted in the customers of those ISPs suffering because certain websites and services would block them. By reducing these attacks, this ensures those ISP customers have full internet access again.
We will continue to monitor the situation
It is unclear whether this reduction in attacks is a permanent change or just a temporary respite. We will continue to monitor the situation and if attacks increase again, the Wordfence algorithms will react very rapidly and will add offending IPs to the Wordfence Premium blacklist in a matter of minutes to protect our WordPress site owners.
As new data emerges, we will publish it here. As always, I encourage you to share your thoughts in the comments below and I will be around to reply if needed. If you haven’t already, please consider joining our mailing list.

Comments
9:08 am
I wonder if this operation has something to do with it? http://www.ktva.com/anchorage-fbi-doj-announce-effort-disrupt-kelihos-botnet-infecting-thousands-computers-902/
9:34 am
Hi TJ,
Interesting, thanks for sharing. That article is from earlier last month - around the 11th, so I think that was an op that completed before that date. My guess is if there is an op to take down the botnet, we'll hear about it a couple of weeks from now.
Mark.
10:43 am
Actually they had just started the operation on the 8th and had to work with local ISPs to contact the infected clients and get them cleaned out. On the 11th they had blocked most of the offending domains. https://www.justice.gov/opa/pr/justice-department-announces-actions-dismantle-kelihos-botnet-0
9:22 am
This is awesome news and I can actually see the results, first hand, on one of my own small groups of 4 WP sites. I went from having 104 lockout notifications (login bot attacks that have been blocked) on Sunday to 37 on Monday and now only 8 so far on Tuesday mid-morning.
Thank GOODNESS that the attacks have lessened, at least for now.
Your news/info is always very helpful and informative! Thanks WF!
9:33 am
Glad to help!!
9:46 am
OR... those behind the coordinated attack found the vulnerability they were looking for, and shut down to avoid being tracked down. This scenario could be employed by a government that wanted a way to get past Wordfence, et. al. , and then selectively breach targeted websites without being noticed.
9:52 am
We also have noticed a reduction - the levels of attacks were getting too much. Had to reduce the notifications from our server - because there were too many!
A combination of WordFence and server security seems to keep us safe. Fingers crossed!
10:02 am
Thanks so much for all your efforts. I have noticed a big decline in attacks. I just recently ventured into the world of WP and WC and am still learning my way around. So glad to have WF in my corner for the peace of mind that it gives me, knowing my site is protected and I am notified of any irregular activities immediately. As soon as my original costs to starting my site have been offset, I will purchase the premium product from you.
10:04 am
I would be interested to know if any of the Wordpress sites they compromised begin to be leveraged together to hack something else or if they are just being sold individually. I'm curious what value these attackers are getting out of such a massive effort.
10:18 am
That is good to know. Keep up the good work you are doing.
12:12 pm
Thanks for your great work! It is a creepy world out there. Thanks for keeping us safe.
3:48 pm
Did the bots part of this botnet yse port 81 scans to propagate? Or am I just mixing up my botnets.
8:37 pm
No. We think it was using a vulnerability on port 7547. See the link to the related post above.
4:58 pm
Great to see that the number of attacks are reduced now. Wordfence is really helpful in identifying and fixing these kind of attacks. Thanks for keeping our websites safe.
6:32 pm
You guys rock!
4:37 am
I scan my 60+ WordPress sites dayly and I noticed a significant reduction in the number of blocked ip's starting yesterday (may 2nd). Typical numbers of blocks were 30-40 per site per day, today I see only 2.
9:49 am
I can confirm my Wordpress site has seen blocked attacks caught by wordfence drop from average 100 per day to around 20 in the last few days. I have been running a black list based on previous attacks that catches most of them - I recommend moving \wp-login to something else to stop most automatic brute force attacks!
Thanks - Keep up the good work!
11:11 am
Very very happy !
10:45 am
Today there is a massive attack on NHS and other business. Could this be the missing bot network, re-hacked by hostage encrypters? I think a yes