Ukraine Universities Hacked As Russian Invasion Started
Note: This article has been updated to reflect that the hosting provider “Njalla”, which routed the malicious traffic involved in this attack, is based in Sweden, not in Finland, although IP geolocation data indicates that the specific server that the traffic transited may be based in Finland. We have also updated the post title to reflect this change.
The Wordfence team has identified a massive attack on Ukrainian universities that coincided with the invasion of Ukraine by Russia, and resulted in at least 30 compromised Ukrainian university websites. We have identified the threat actor behind the attack, who is part of a group called the Monday group, which the members refer to as “theMx0nday”. The group has stated publicly that they support Russia in this conflict.
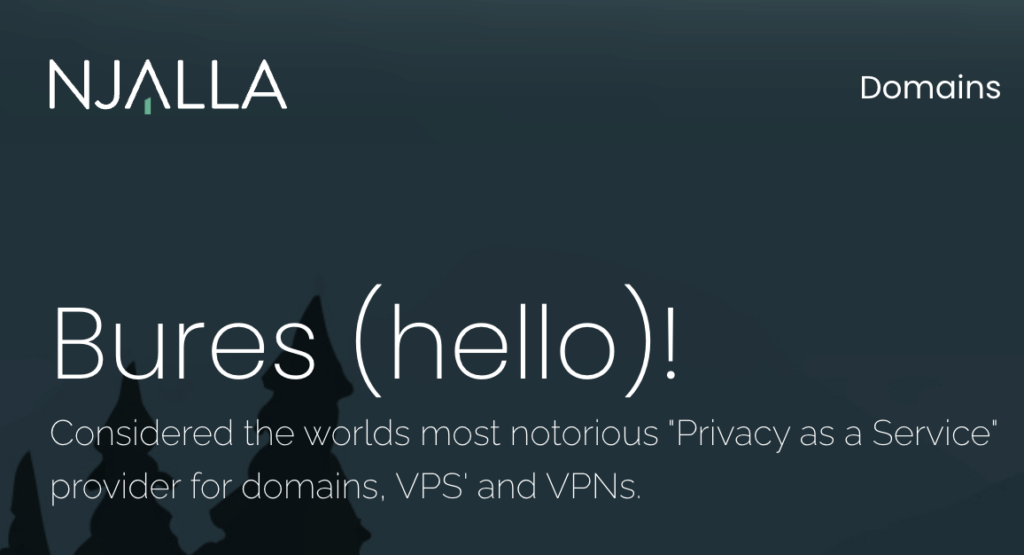
The threat actor is based in Brazil. The majority of attacks transited an internet service provider called Njalla who claim they are “Considered the worlds most notorious ‘Privacy as a Service’ provider for domains, VPSs and VPNs”. Njalla is a Swedish-based hosting provider and is run by Peter Sunde, who is the co-founder of Pirate Bay. The specific Njalla server that the traffic was routed through appears to be based in Finland, based on IP geolocation data, although Njalla claims their servers are based “In secret locations in Sweden”.
Wordfence protects over 8,000 websites in Ukraine. In addition to the more than 300 universities we protect in Ukraine, we also protect private, government, military, and police websites. This gives us insight into attacks targeting Ukraine. In this post, we explain how we arrived at the conclusions above, and we provide supporting data, explanations, and visuals.
We are also taking the step of activating our real-time threat intelligence on all sites on the Ukrainian .UA top-level domain (TLD) until further notice. This is normally only available to our paid customers. The vast majority of sites using Wordfence use the free open source version. These sites will benefit from this change by receiving a commercial-grade IP blocklist, real-time firewall rules, and real-time malware detection. Ukrainian site operators do not need to take any action to receive this live threat feed. We deployed the change minutes ago and over 8,000 sites with a .UA extension will update over the next 24 hours with the newest threat intelligence. You can find more details about this change at the end of this article.
Overall Attack Patterns As The Kinetic Russian Invasion Started on 24 February
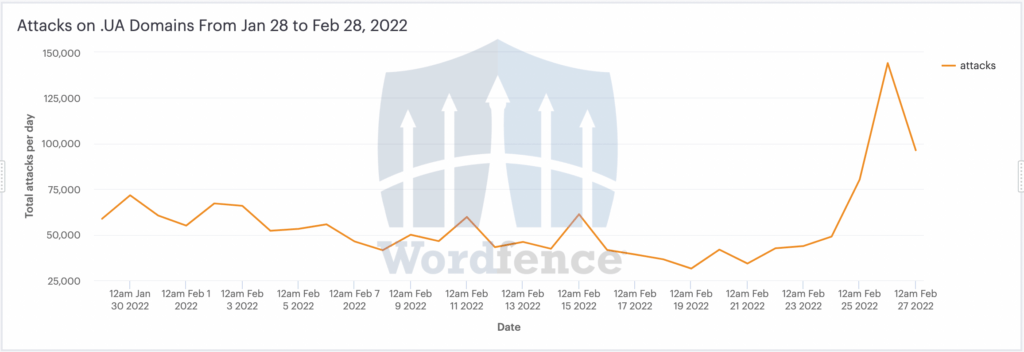
The Russian invasion of Ukraine started on February 24th. The chart below shows the overall number of exploit attempts on websites that we protect, with the .UA Ukrainian TLD before and after the invasion. This data set includes 8,320 .UA websites. We will use the term “attack” in this blog post to indicate a sophisticated exploit attempt. This does not include simple brute force attacks (login guessing attempts) or distributed denial of service traffic. It only includes attempts to exploit a vulnerability on a target WordPress website, which are the sites that Wordfence protects.
The peak above is just over 144,000 attacks on February 25th, one day after the kinetic attack started. The peak is roughly three times the number of daily attacks from earlier in the month across the Ukrainian websites that we protect.
Examining The Spike In Attacks Targeting Ukraine
Wordfence protects a broad range of websites in Ukraine, including commercial, local and national government, military, police, academic and private websites. This allows us to sample attack data across a broad range of sectors. We compiled a list of websites that had received at least double the number of attacks from the day before the invasion started, until Monday, February 28th, which is a window of about 5.5 days, compared to the entire 27 days before the attack started. That’s about a 10X increase in the average daily number of attacks.
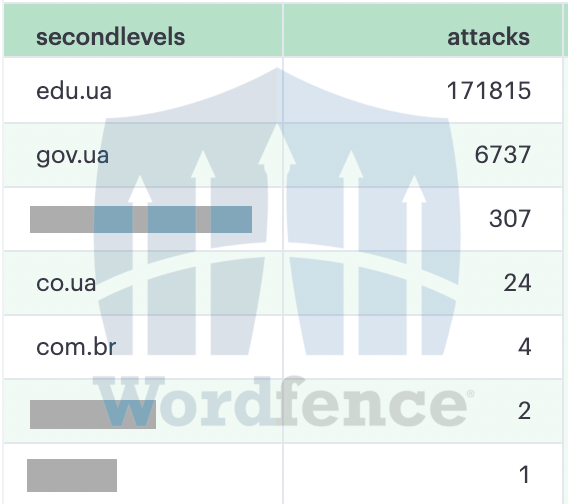
Out of the 8,320 UA websites that we protect, we found a list of 383 websites where attacks had increased dramatically following the invasion. Out of those 383 websites, 229 were sites ending in “EDU.UA”. In other words, academic websites and universities in Ukraine.
An attacker was making a concerted effort to attack universities in Ukraine, and they started immediately after the Russian invasion started.
How Big Was The Attack Targeting Ukrainian Universities?
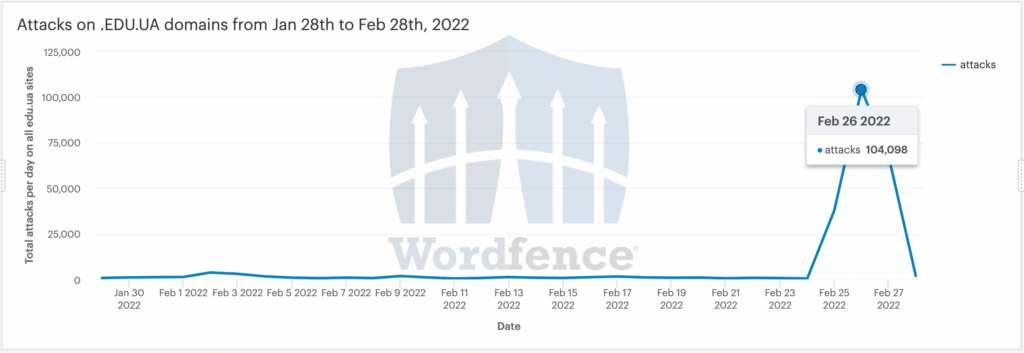
We protect a total of 376 .EDU.UA websites in Ukraine. The chart below shows attack activity across all those sites until Feb 28th. This only shows sophisticated exploit attempts.
Most of the month showed a few hundred attacks per day across all .EDU.UA sites that we protect. Starting February 25th, we saw a spike that peaked at over 104,000 attacks in a single day targeting these academic websites.
To put this in perspective we saw:
- 479 attacks on Feb 24th
- 37,974 attacks on Feb 25th
- 104,098 attacks on Feb 26th
- 67,552 attacks on Feb 27th
Which IP Addresses Launched This Attack?
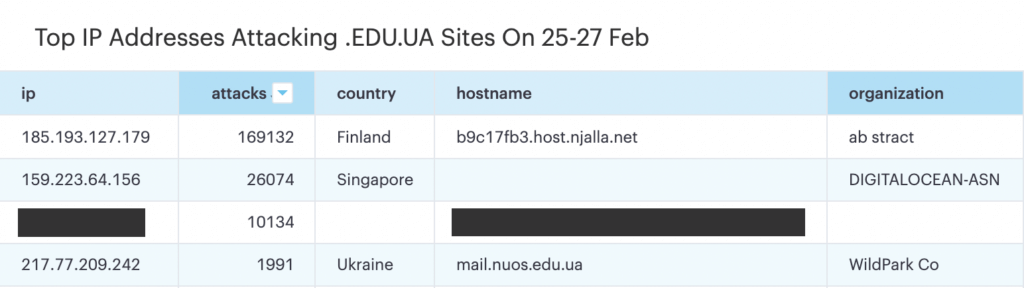
The top attacking IP addresses targeting EDU.UA sites during our two-day window as the invasion of Ukraine started are:
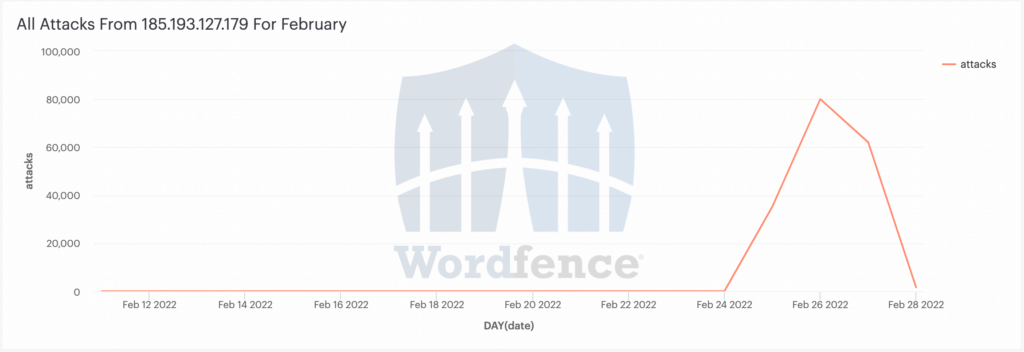
- 185.193.127.179 with 169,132 attacks
- 159.223.64.156 with 26,074 attacks
- x.x.x.x with 10,134 attacks [Redacted for a technical reason]
- 217.77.209.242 with 1991 attacks
Note: The last server in the list is a .EDU.UA server, and appears to be a compromised machine targeting other EDU.UA sites.
We logged over 7,000 IP addresses during this period, but every single one, other than the four above, logged less than 100 attacks each. The four IP addresses above were by far the biggest offenders. And 185.193.127.179 logged over 6 times the number of attacks versus the second-highest offender.
Who Is Behind 185.193.127.179?
Njalla is the hosting provider for 185.193.127.179 and is run by Peter Sunde, who is the co-founder of Pirate Bay. Njalla say openly on their home page that they are
“Considered the worlds most notorious “Privacy as a Service” provider for domains, VPS’ and VPNs.”
Peter Sund says on his blog that he is “worried of the centralisation of power to the EU”. According to his Wikipedia entry, Mr Sunde was arrested in 2014 on charges related to The Pirate Bay case and served two-thirds of his 8-month sentence.
Njalla is a service provider for VPNs, which makes it possible that the attack may have come from one of their customers, a hacked server belonging to one of their customers, or from a VPN exit node. We suspect their VPN was used as an exit node to mask a threat actor, which we describe below.
The vast majority of attacks from 185.193.127.179 were targeted at educational institutions in Ukraine, with over 171,000 attacks targeting EDU.UA sites. They went after a few government sites and three individual websites (redacted).
They launched 24 attacks against companies in Ukraine and four attacks against companies in Brazil. The Brazil connection will become clear below.
This IP was not attacking before the invasion of Ukraine by Russia. Then ramped up for three days during the invasion, specifically targeting universities in Ukraine. Then dropped back down to zero.
The Attacks Are Compromising Universities
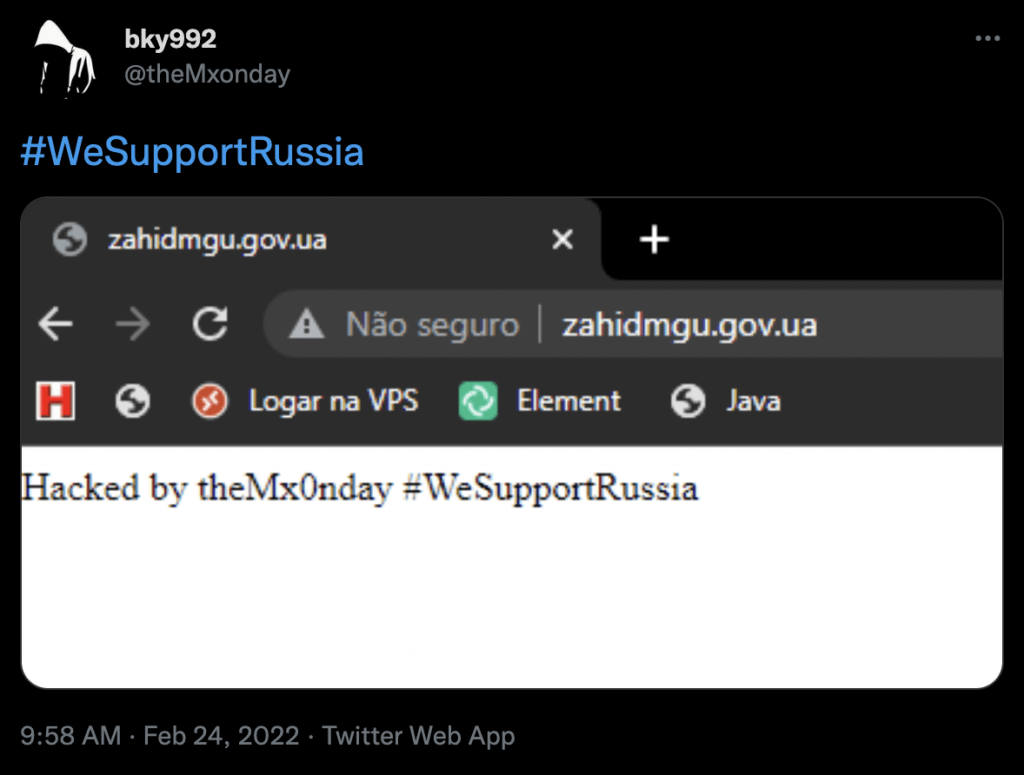
In our analysis of malware payloads attempting to target EDU websites, we saw information that provided us with the name of the group targeting these sites.
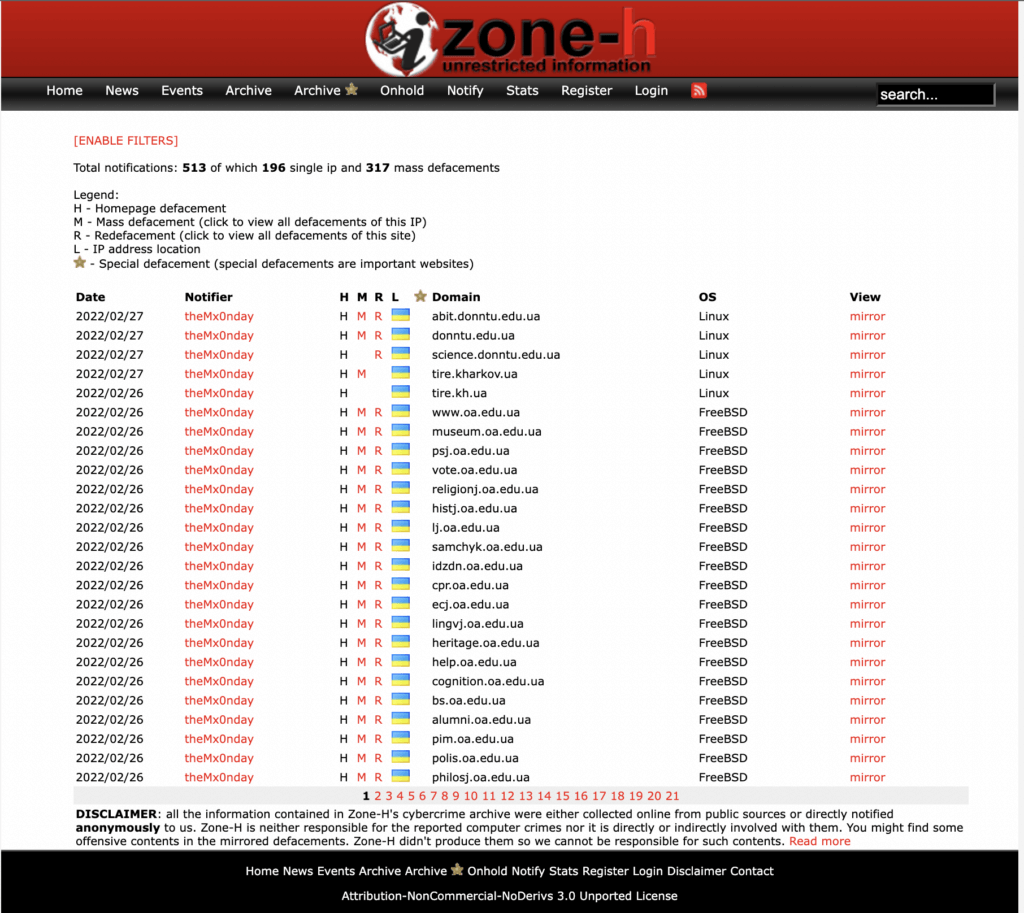
The group goes by “theMx0nday” and in this post, we will refer to them as the “Monday” group. The website Zone-H.org provides an archive of defaced websites. Once we had the threat actors handle, we could search ZoneH for sites that were related and had been hacked. We found this:
A huge list of compromised EDU.UA websites attributed to the Monday group, dated the 26th of February, right after we saw a spike in attacks targeting EDU.UA websites.
As you can see below, the defaced EDU.UA sites listed on ZoneH abruptly start on the 26th. As the invasion started, this threat actor made the decision to specifically target Ukrainian universities.
Attacker Motivations
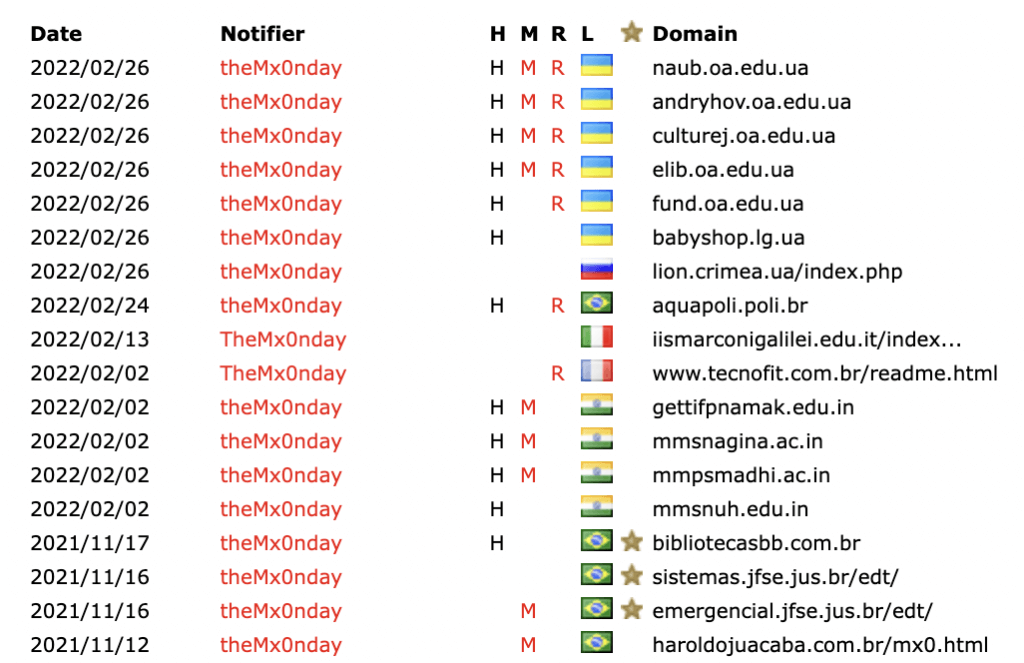
You’ll notice the Brazilian sites listed on ZoneH in the above screenshot, credited to the Monday group. Recall, we saw a few hits targeting Brazil from the Njalla IP address above.
The archive on ZoneH of the defaced page for National University Ostroh Academy, which is a well known University that dates its heritage back to 1576, looks like this. This image is partially redacted to avoid promoting threat actors.
We have retained the handle son1x in the above image because this threat actor has a history of stealing sensitive data. In October last year, this threat actor defaced the website of the Indonesian Cyber and Code Agency (BSSN), and in November, the same attacker stole Indonesian police personnel records. This threat actor also goes by “son1x777” on a now-suspended Twitter account.
The group this threat actor belongs to, the Monday group, has a Twitter account that expressed support for Russia, days before the Russian invasion started and before they started hacking Ukrainian universities.
The Monday group has historically targeted a large number of Brazilian sites. They embed a Brazilian rap video in the HTML of the sites they deface. Their Twitter account is in Portuguese. From this, we can infer that they are based in Brazil and are Brazilian.
The Full Attack Path
We have determined that the threat actor is based in Brazil. They used a range of IP addresses to launch an attack on Ukrainian universities as the Russian invasion of Ukraine commenced. The majority of attacks were routed via Njalla, based in Sweden. Njalla claims that their servers are “In secret locations in Sweden” although the specific exit node appears to be in Finland, based on IP geolocation data. Njalla is backed by Peter Sunde who is the co-founder of The Pirate Bay and prides himself in masking the identity of his customers. The attacks compromised at least 30 Ukrainian university websites, which are listed in ZoneH, with evidence of the compromises.
Wordfence Is Deploying Real-Time Threat Intelligence to Ukrainian Websites

The National University Ostroh Academy is one of the affected schools that suffered a hacked website.
Effective immediately, we are providing real-time firewall rules, real-time malware signatures, and our IP blocklist to all websites under the .UA top-level domain protected by Wordfence.
Normally our real-time threat intelligence is only available to our Premium, Care and Response customers at a minimum cost of $99 per year per website. We are doing this to assist in blocking cyberattacks targeting Ukraine. This update requires no action from users of the Free version of Wordfence on the UA top-level domain. We are activating this live security feed for UA websites automatically until further notice. Within the next few hours, over 8,000 Ukrainian websites running the free version of Wordfence will automatically become far more secure against attacks, like these, that are targeting them.
The malicious IP addresses involved in this attack are included in our blocklist, which will completely block access to WordPress and other PHP applications installed alongside WordPress. The list is updated in real-time as attackers rotate through fresh IP addresses. We also regularly deploy new firewall rules and malware detection to block and detect emerging attacks and malicious activity. Instead of our usual 30-day delay for free customers, Ukrainian websites will start receiving these security updates in real-time, until further notice.
Again, this requires no action from Ukrainian users of the free version of Wordfence, and does not require any payment or personally identifiable information from them. They will simply become more secure over the next few hours.
This is the first time in the history of our company that we are taking this action. We are doing it as a response to the crisis that has unfolded in Ukraine.
#WeSupportUkraine
Mark Maunder – Wordfence Founder & CEO
This post was written by Mark Maunder with significant contributions from the Wordfence Threat Intelligence Team.



Comments
4:46 pm
Thank you very much!! #wordfence
5:15 pm
This is why I use and recommend Wordfence. Timely, responsible and ethical.
5:29 pm
Thanks Travis. More to come.
9:29 pm
As a technical Project Manager, this is why I recomment Wordfence in the Security & Protection plan for our customers. Way to go !
9:46 pm
Thank you for doing this!
10:08 pm
Peter Sunde is a Swedish entrepreneur and his company Njalla claims their servers are in Sweden: https://njal.la/servers/
2:01 am
Thanks Markus. The article has been updated to reflect that the company is based in Sweden, although the IP geolocation data on that server indicates it may be in Finland.
Regards,
Mark.
10:41 pm
Please, FACT CHECK! Attacks DOES NOT originate from Finland. Also Finland is NOT tolerant about cyber attacks, nor Finland (as country) is NOT linked to hosting Pirate Bay. (Notice, Finland is not Sweden).
... Yes, that IP address is registered in RIPE to postal address that is located in Finland, that does not originate addresses to Finland anyway. While tracing AS paths to that AS39287, you can see there is Malmo in quite many times.
Also one simple net tool can confirm my findings: https://ipinfo.io/AS39287
.. Just look "Peers" and "Upstreams", there is 2 companies (that ends AB). AB is swedish thing as LLC, or in Finland OY ... So all findings is that VPN Company njal.la is NOT Located in Finland, but is located in Sweden.
1:59 am
Thanks Sami. I've updated the article and title to reflect that Njalla is based in Sweden, and that they say their servers are in Sweden. The IP geolocation data we have indicates that the specific server that the traffic transited may be based in Finland, so I have kept that information in the article.
In writing this, we had to parse a lot of data, and so we relied on the IP geolocation data entirely to determine the location of the transit node. I did visit the Njalla website, but I missed the fact that the company is in Sweden, not in Finland. Thanks for pointing this out.
Regards,
Mark.
6:34 am
I looked up 185.193.127.179 and it is linked to abstract.fi Bouvet Island, ISP AB Stract
11:32 pm
Bravo! The right move!
12:03 am
Great initiative. Thank you for this.
6:29 am
Thank you for this. I have reported these IP addresses to www.abuseipdb.com
7:28 am
Articolo molto interessante
8:30 am
Thank You! You are a class act.
11:50 pm
According to Finnish Transport and Communications Agency Traficom (https://www.traficom.fi/en/communications/fi-domains/fi-domain-name-search) abstract.fi is registered to an address in Helsinki Finland. Domain Registrar is Sarek Oy (sarek.fi). Name behind that company is among others Peter Kalevi Sunde Kolmisoppi > https://www.finder.fi/IT-konsultointi+IT-palvelut/Sarek+Oy/Helsinki/yhteystiedot/3331616
Sarek Oy has the same postal address with stract ab (abstract.fi) and the same persons are board members in both of the companies Sarek Oy and stract ab
https://www.finder.fi/Taiteellinen+luominen/stract+ab/Helsinki/yhteystiedot/3307187
4:38 am
Thanks Mark for your insightful article!
9:35 am
Thank you for the great work you do!