PSA: Wordfence Brand Being Actively Used in Phishing Campaigns
Earlier this week we became aware that malicious actors are using Wordfence brand image to run a phishing scam on WordPress and Wordfence users, posing as unknown login notifications from their own website while linking to a fake login page, clearly aiming to steal WordPress login credentials.
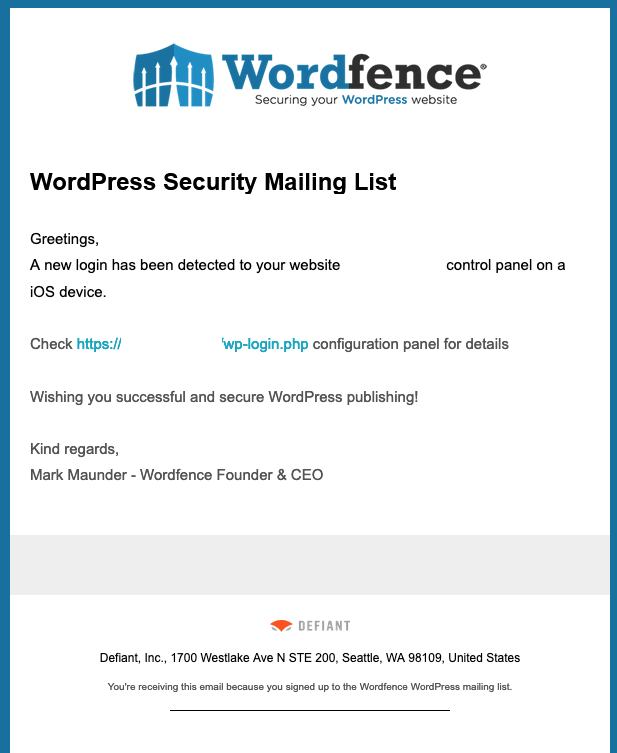
If you have received a suspicious email like this you may want to ensure it is legitimate by checking a couple of telltale signs:
- Wordfence notifications from your website will be sent from an email address matching your website (usually
wordfence[@]your-website-domain). - Messages sent through our mailing list are sent exclusively from list@wordfence.com, and will display an unsubscribe link at the end of the message.
- Wordfence login notifications from your website are not signed by our CEO and founder, Mark Maunder.
Details
This phishing campaign appears to be running via several custom domains, usually posing as Wordfence (or the Wordfence Team); for example:
- From: Wordfence <matteo.fish[@]germanrottweillerpuppies.net>
- From: Wordfence Team <jamir.bahhar[@]acmesecurityconcepts.com>
- From: Wordfence <thea.santana[@]iznacquisitions.com>
The most important thing to be aware of for WordPress site owners is that in this phishing campaign, the WordPress login link found in the email will not direct to their own site. We have seen these emails link to several legitimate, but vulnerable, websites as part of their campaign, using open redirect vulnerabilities to minimize the risk of being detected as spam/phishing messages by mail security software, as shown in the following screenshots:
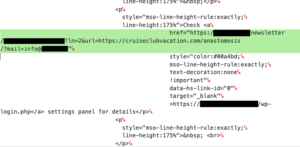
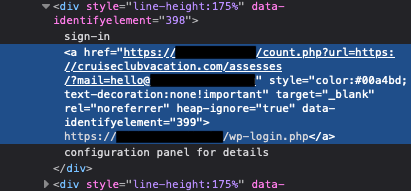
The links in these emails typically point to cruiseclubvacation[.]com in the samples we inspected. We have already notified both the vulnerable site owners (where possible) and/or reported the phishing campaign to the appropriate entities.
Conclusion
If you have received a message like this in the last few weeks, or suspect possible malicious activity against your website, we strongly recommend changing your WordPress password as soon as possible. Additionally, we recommend setting up Wordfence Login Security (also known as two-factor authentication) as additional protection.
Wordfence Login Security doesn’t even require a Wordfence Premium subscription – it comes standard with the free version of Wordfence, and is also available for download as a standalone plugin.
If you believe your site has been compromised via a phishing attempt or any other mechanism, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both these products include hands-on support in case you need further assistance.
We have a comprehensive video about the 2FA setup process should you like to know more:


Comments
9:32 am
the most common cause for this is that people do not set up email authentication/DMARC for their domain or do any domain alignment.
thus allowing anyone to spoof their domain.
You can read more about that here
https://michaels.me.uk/domain-alignment-managed-dmarc/
12:07 pm
Bravo, welcome to the club, transport, web hosts, postal services, all are victims one day or another of a campaign. We have received so many from these Mx servers which turn themselves off, whose ip changes in order to cover their trace. I've always had a hard time following in their footsteps.
12:21 pm
This would have been a great opportunity to bring up both DMARC and SPF.
These two important technologies to fight email compromise. Any email server that respected your DMARC or SPF records would not have delivered this email to an inbox. (Or should not anyway).
It's my considered opinion that if your email provider isn't supporting both of these technologies then you should ask them to start or seek out an email provider that does.
DMARC and SPF protect you, your clients/customers, your company and your brand!
6:20 am
Hi Kim,
We agree that both DMARC and SPF are very useful for preventing email spoofing. Unfortunately DMARC remains fairly complicated to configure, for the average site owner, and may not be practical for sites on shared hosting at all. SPF at least is fairly simple to setup and some hosts automatically configure it, but it's still not as common as it should be.
8:20 am
you could let at least paid users to upload some icon or a special phrase that you'd then include at the top of all your correspondence with them (with some note to not share that correspondence without removing that note) for identification it's coming from you
6:21 am
Hi George,
Thanks, this is an interesting idea. I can't promise that we'll implement it but I'll at least bring it up to our developers as a potential feature for a future release or product.