$1,900 Bounty Awarded for Arbitrary Options Update Vulnerability Patched in Cookie Information | Free GDPR Consent Solution WordPress Plugin
On December 11th, 2023, during our Holiday Bug Extravaganza, we received a submission for an Arbitrary Options Update vulnerability in Cookie Information | Free GDPR Consent Solution, a WordPress plugin with more than 100,000+ active installations. This vulnerability could be used by authenticated attackers, with authenticated access, to update arbitrary options and leverage that for privilege escalation.
Props to Lucio Sá who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $1,900.00 for this discovery during our Bug Bounty Program Extravaganza.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on December 12, 2023. Sites still using the free version of Wordfence received the same protection on January 11, 2024.
We contacted the Cookie Information Team on December 12, 2023, but we didn’t get any response, so we escalated it to the WordPress.org Security Team on January 25, 2024. After that, the developer released a patch on January 29, 2024.
We urge users to update their sites with the latest patched version of Cookie Information | Free GDPR Consent Solution, which is version 2.0.23, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: Cookie Information | Free GDPR Consent Solution
Plugin Slug: wp-gdpr-compliance
Affected Versions: <= 2.0.22
CVE ID: CVE-2023-6700
CVSS Score: 8.8 (High)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Researcher/s: Lucio Sá
Fully Patched Version: 2.0.23
Bounty Awarded: $1,900.00
The Cookie Information | Free GDPR Consent Solution plugin for WordPress is vulnerable to arbitrary option updates due to a missing capability check on its AJAX request handler in versions up to, and including, 2.0.22. This makes it possible for authenticated attackers, with subscriber-level access or higher, to edit arbitrary site options which can be used to create administrator accounts.
Technical Analysis
Cookie Information | Free GDPR Consent Solution is a WordPress website security plugin that offers several features to become compliant with GDPR, including cookie pop-up, consent log, form integration, and more. The plugin’s form integration options are listed on the admin page.
<section class="wpgdprc-integrations">
<?php
$list = Integration::getList();
foreach ( $list as $key => $integration ) {
Template::render(
'Admin/Pages/Settings/Integrations/item',
[
'type' => $key,
'integration' => $integration,
]
);
}
?>
</section>
A predefined list contains the forms that can be integrated, which can be queried with the getList() function in the Integration class.
/**
* Lists all supported features/plugins
* @return array[AbstractIntegration|AbstractPlugin]
*/
public static function getList(): array {
return self::supportedWP() + self::supportedPlugins();
}
Examining the code reveals the integration can be activated with AJAX. The UpdateIntegration class extends AbstractAjax class, which classes contain the functions for the AJAX action.
/**
* Executes the AJAX request
*/
public static function execute() {
check_ajax_referer( Plugin::AJAX_NONCE, Plugin::AJAX_ARG );
if ( ! static::hasData() ) {
static::buildResponse([]);
return;
}
$data = static::validateData();
$data = static::sanitizeData($data);
static::buildResponse($data);
}
After validating and sanitizing the data, the execute() function in the AbstractAjax class calls the buildResponse() function, which is implemented in the UpdateIntegration class. Unfortunately, it was found that the nonce is publicly accessible and there is no capability check. This makes it possible for authentication attackers with subscriber-level permission to access the AJAX function.
/**
* Builds the AJAX response
* (security handling + data validation -if any- is done in the abstract class)
* @param array $data
*/
public static function buildResponse( $data = [] ) {
$meta_key = explode( '[', $data['name'] );
$success = false;
$data_value = $data['value'];
switch ( count( $meta_key ) ) {
case 1:
$meta_key = reset( $meta_key );
$settings = $data_value;
$success = update_option( $meta_key, $settings );
break;
Further examining the code reveals that although the integration is limited on the admin settings page, there are no restrictions on the option key, which is the $meta_key variable in the function. This makes it possible to update the options arbitrarily.
As with any Arbitrary Options Update vulnerability, this can be used for complete site compromise by setting the default registration role to administrator. Once an attacker has edited the site options to create an administrative account on the WordPress site, they can then manipulate anything on the targeted site, just like a normal administrator would. This includes the ability to upload plugin and theme files, which can be malicious zip files containing backdoors, and modifying posts and pages which can be leveraged to redirect site users to other malicious sites.
Wordfence Firewall
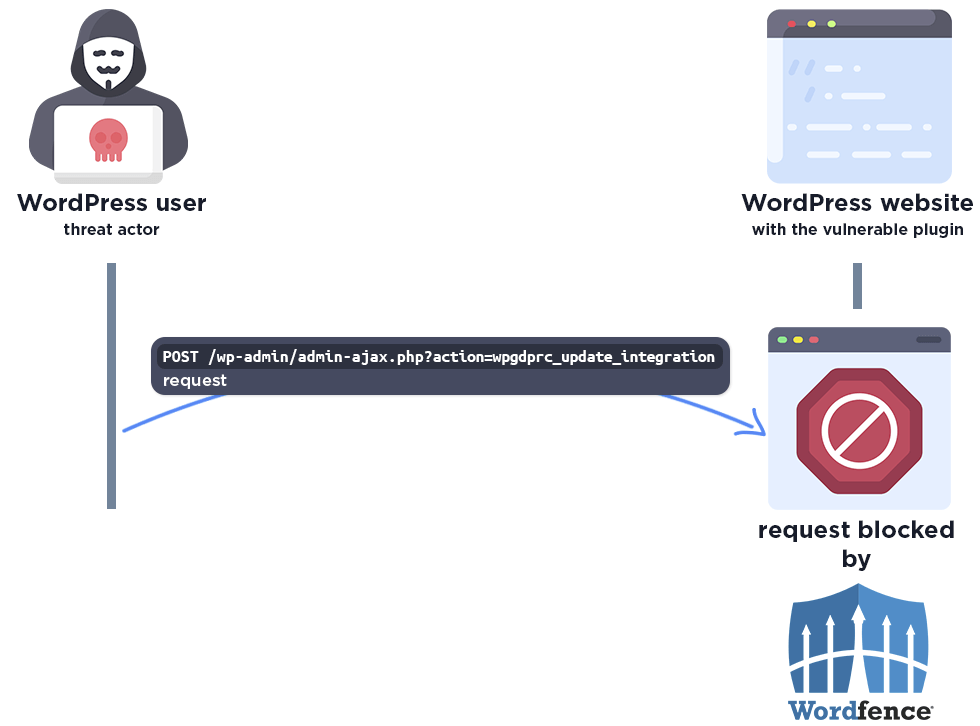
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious AJAX action and blocks the request if it does not come from an existing authorized administrator.
Disclosure Timeline
December 11, 2023 – We receive the submission of the Arbitrary Options Update vulnerability in Cookie Information | Free GDPR Consent Solution via the Wordfence Bug Bounty Program.
December 11, 2023 – We validate the report and confirm the proof-of-concept exploit.
December 12, 2023 – We initiate contact with the plugin vendor asking that they confirm the inbox for handling the discussion.
December 12, 2023 – Wordfence Premium, Care, and Response users receive a firewall rule to provide protection against any exploits that may target this vulnerability.
January 11, 2024 – Wordfence Free users receive the same protection.
January 25, 2024 – We escalate the vulnerability to the WordPress.org Security Team and send over the full disclosure details.
January 26, 2024 – The WordPress.org Security Team acknowledges the report.
January 29, 2024 – The fully patched version of the plugin, 2.0.23, is released.
Conclusion
In this blog post, we detailed an Arbitrary Options Update vulnerability within the Cookie Information | Free GDPR Consent Solution plugin affecting versions 2.0.22 and earlier. This vulnerability allows authenticated threat actors with subscriber-level permissions or higher to edit arbitrary site options which can be used to create administrator accounts. The vulnerability has been fully addressed in version 2.0.23 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Cookie Information | Free GDPR Consent Solution.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on December 12, 2023. Sites still using the free version of Wordfence received the same protection on January 11, 2024.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.


Comments