Unauthenticated Stored Cross-Site Scripting Vulnerability Patched in WP-Members Membership Plugin – $500 Bounty Awarded
🎉 Did you know we’re running a Bug Bounty Extravaganza again?
Earn over 6x our usual bounty rates, up to $10,000, for all vulnerabilities submitted through May 27th, 2024 when you opt to have Wordfence handle responsible disclosure!
On February 21st, 2024, during our second Bug Bounty Extravaganza, an Unauthenticated Stored Cross-Site Scripting vulnerability was reported to us in the WP-Members Membership Plugin, which is installed on over 60,000 sites. The vulnerability allows threat actors to inject arbitrary JavaScript via the X-Forwarded-For header, used by the plugin for logging purposes. When viewed by an administrator, the malicious code is executed in the context of the administrator’s browser session and allows for the creation of malicious administrator users as well as changes to an affected site’s settings which could lead to a complete site takeover.
Kudos to Webbernaut who responsibly disclosed this vulnerability to us through our Bug Bounty Program. Their find was rewarded with a $500 bounty. Our mission is to Secure the Web, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure, which ultimately makes the entire web more secure.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those using the free version of our plugin, are protected against any exploits targeting this vulnerability by the Wordfence firewall’s built-in Cross-Site Scripting protection.
Our initial outreach to RocketGeek took place on February 23rd, 2024. We received a reply and disclosed details on the same day. Version 3.4.9.2, released on March 7th, 2024, protected against further exploitation of this vulnerability, but did not prevent existing injected payloads from firing. A fully patched version addressing this issue was made available shortly thereafter on March 7th.
We recommend that site owners upgrade their WP-Members Membership plugin to the latest patched version, which is 3.4.9.3.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: WP-Members
Plugin Slug: wp-members
Affected Versions: <= 3.4.9.2
CVE ID: CVE-2024-1852
CVSS Score: 7.2 (High)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:L/A:N
Researcher/s: Webbernaut
Fully Patched Version: 3.4.9.3
Bounty Award: $500.00
The WP-Members Membership Plugin plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the X-Forwarded-For header in all versions up to, and including, 3.4.9.2 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page which is the edit users page. This vulnerability was partially patched in version 3.4.9.2 and fully patched in version 3.4.9.3.
Technical Analysis
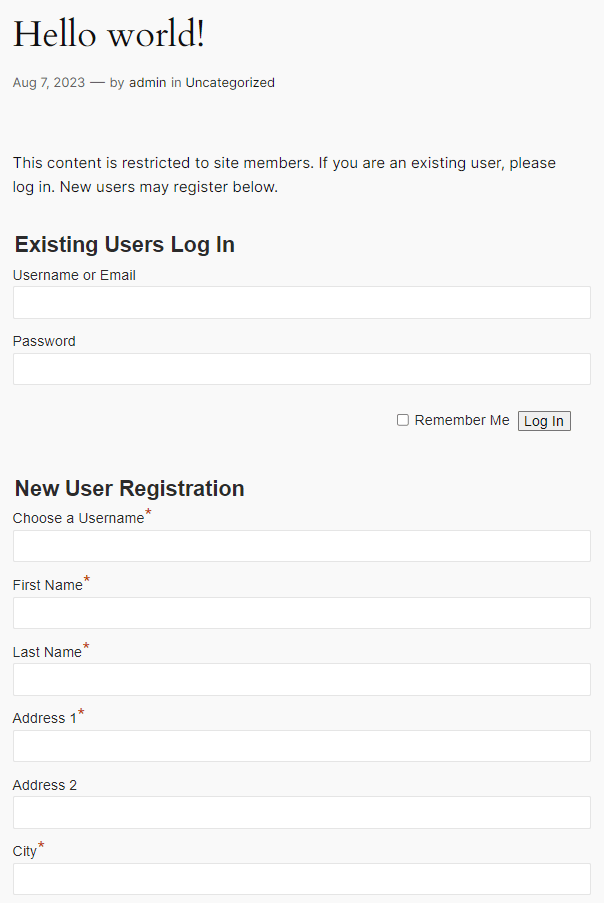
WP-Members offers content restriction and custom registration features that help site owners monetize their content. During the initial setup it is possible to restrict access to posts as well as pages and enable user registration. When trying to view a page, a visitor would see something similar to the following screenshot:
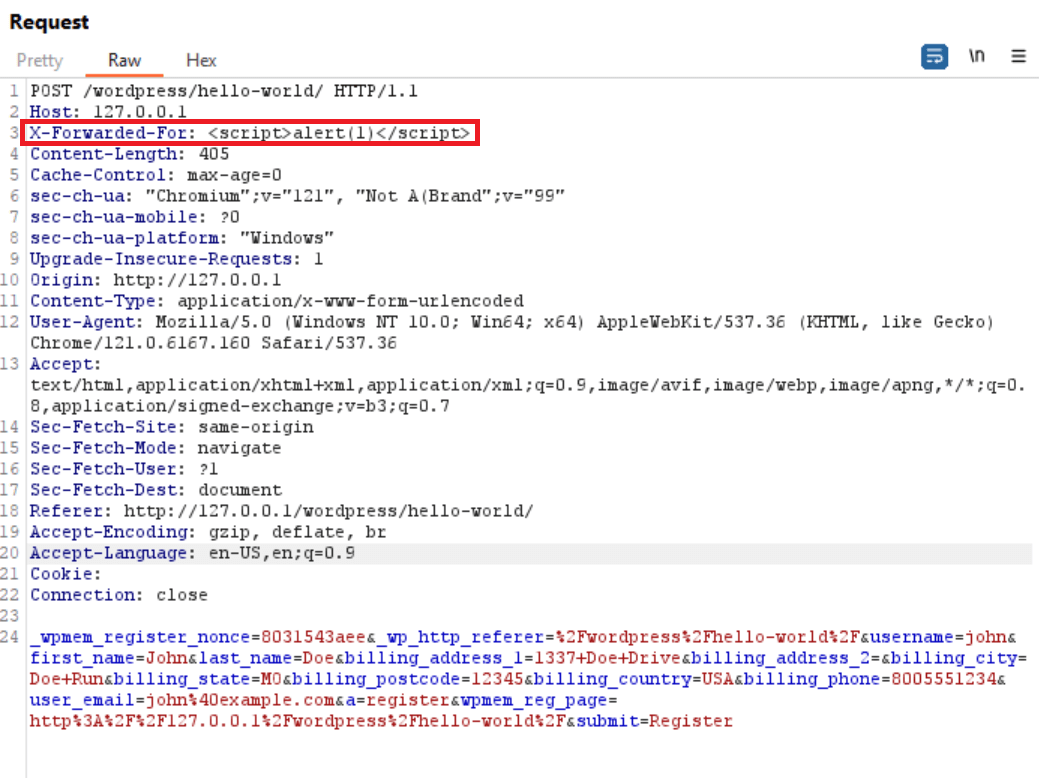
In order to exploit this Cross-Site Scripting vulnerability, an attacker could intercept their registration request after filling out and submitting the registration form using a proxy of their choosing and modify the raw request to contain an X-Forwarded-For header set to a malicious payload enclosed in script tags as shown in the following screenshot:
Once this request is forwarded to the server, an unsuspicious-looking user account is created with the details provided by the attacker:
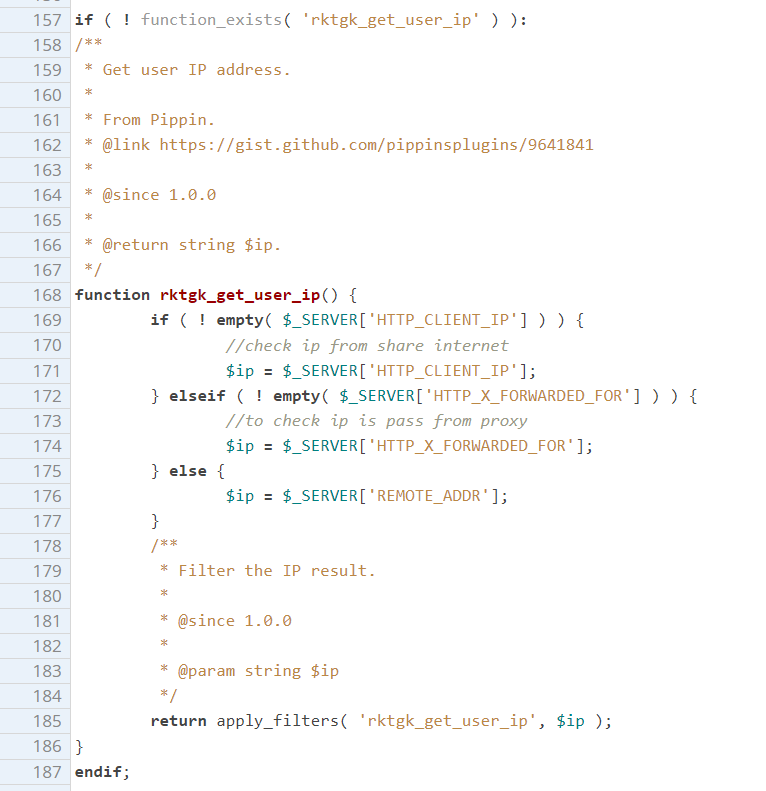
The plugin stores the IP address of users who used its registration form in their profile. This is accomplished using the following code:
The rktgk_get_user_ip function determines whether the request contained an HTTP_CLIENT_IP or HTTP_X_FORWARDED_FOR header. If either header is present, the function utilizes that value as the user’s IP instead of the REMOTE_ADDR variable and then returns the provided value as the IP address. Due to the fact that HTTP headers can be manipulated, and the input was not sanitized, a user could supply any value including a malicious web script that will be stored as the user’s IP.
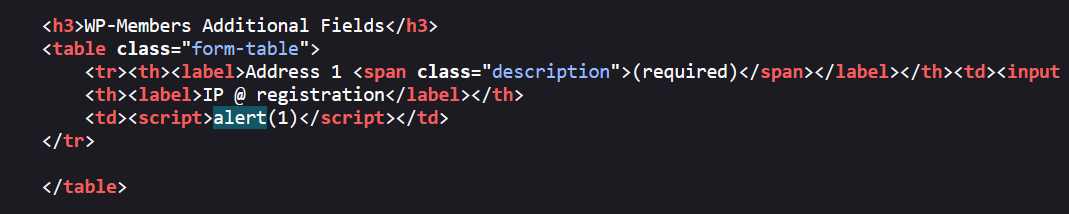
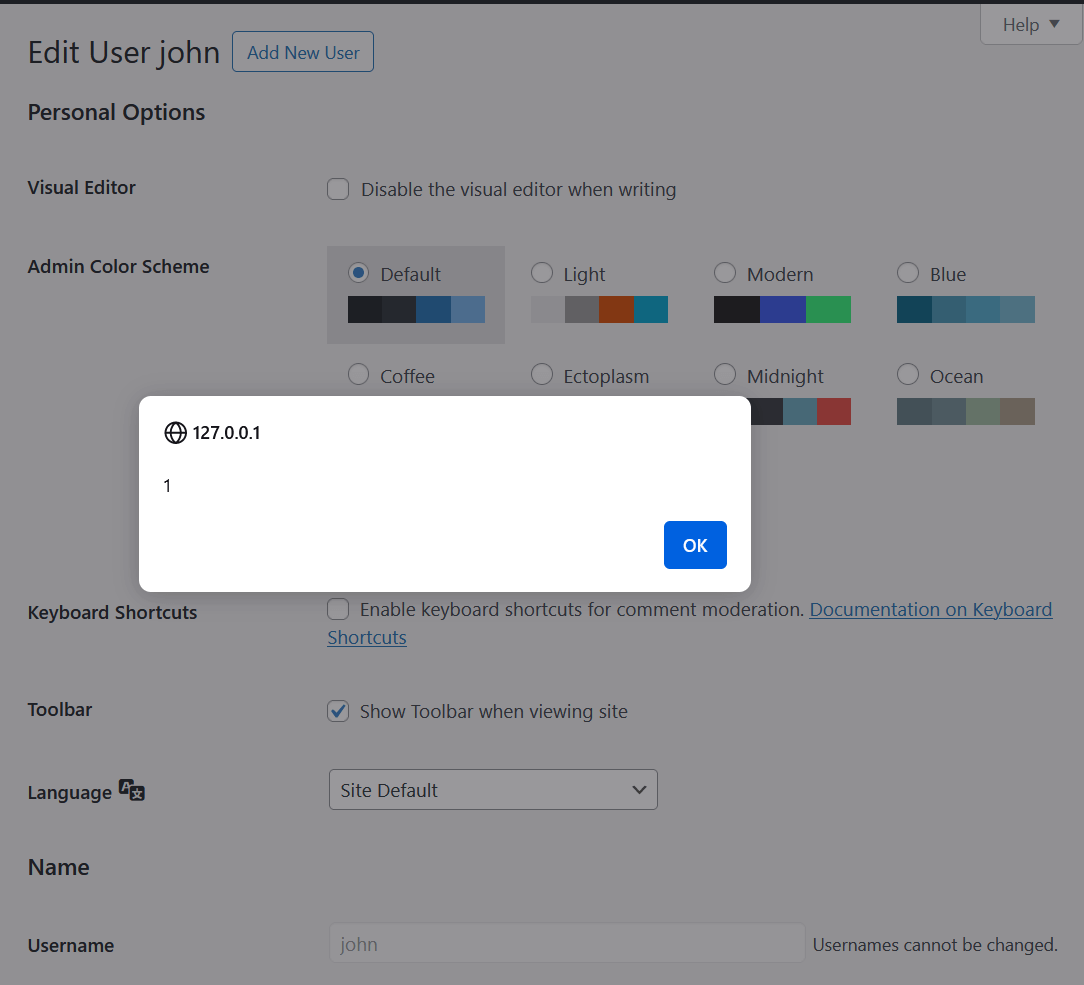
If an administrator decides to edit or view this user account, the following injected JavaScript will be present in the generated source code upon page load:
As a result this payload will fire:
It is important to understand that this malicious code will be executed in the context of an administrator’s browser session and can be used to create malicious user accounts, redirect site visitors to other malicious sites and perform other malicious actions.
Wordfence Firewall
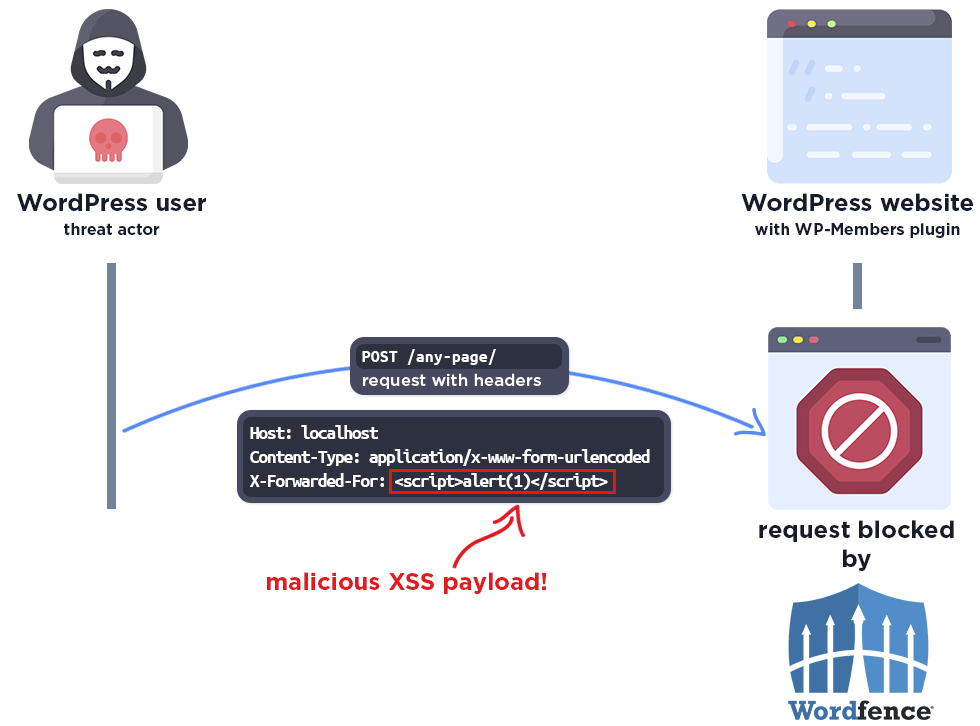
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
Disclosure Timeline
February 21, 2024 – We receive the submission of the Cross-Site Scripting vulnerability in the WP-Members Membership Plugin through the Wordfence Bug Bounty Program.
February 23, 2024 – We validate the vulnerability report and confirm the provided proof of concept.
February 23, 2024 – We initiate contact with the plugin vendor asking them to confirm an appropriate inbox for vulnerability discussion.
February 23, 2024 – The vendor confirms an appropriate inbox.
February 23, 2024 – We send the full disclosure details. The vendor acknowledges receipt and starts working on a patch.
March 7, 2024 – Version 3.4.9.2 partially addresses this issue. We inform the vendor that existing injected payloads can still cause issues and may fire when viewing profiles of users who registered with this plugin.
March 7, 2024 – Version 3.4.9.3 is released, which fully patches this vulnerability.
Conclusion
In today’s blog post we discussed a Cross-Site Scripting vulnerability via the X-Forwarded-For header in the WP-Members Membership plugin that affects versions up to, and including, 3.4.9.2. This vulnerability allows unauthenticated attackers to inject malicious JavaScript payloads into the database. The vulnerability has been fully patched in version 3.4.9.3.
We encourage WordPress users to verify that their sites are updated to the latest version of the WP-Members Membership plugin.
All Wordfence users, including those running Wordfence Premium, Wordfence Care, and Wordfence Response, as well as sites running the free version of Wordfence, are fully protected against this vulnerability.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.



Comments