This site uses cookies in accordance with our Privacy Policy.
Discover which plan is right for you.
Join over 5 million secure WordPress site owners using Wordfence Free. Block attacks with the basic tools you need to keep your site safe. The Free version has a 30-day delay on firewall rules and malware signatures.
Real-time updates to firewall rules as new threats emerge, our comprehensive Real-Time Malware Signatures for the very best in malware detection, continuously updated Premium IP Blocklist blocks over 40,000 known threat actors, Country Blocking, Premium Support and more.
Wordfence Care includes the benefits of Premium with unlimited hands-on incident response and hands-on support. For business owners who value their time: If you have an incident, our world-class analysts take care of it.
For Mission Critical websites, Wordfence Response provides incident response 24 hours a day, 7 days a week and 365 days a year with a 1-hour response time and 24 hours time to resolution. If down-time has a financial impact, choose Wordfence Response.
Wordfence is the global leader in WordPress security.
The average WordPress site is attacked once every 24 minutes. 61 requests hit that site every day probing for weak and breached passwords, vulnerable plugins and themes, and other points of entry. Websites protected by Wordfence are shielded from those attacks with an average of 306M hits being blocked across our network every day.
96K
malicious IPs blocklisted in the past 30 days
9.2B
attacks blocked in the past 30 days
477
web application firewall rules
4,998
malware signatures in our real-time malware signature set
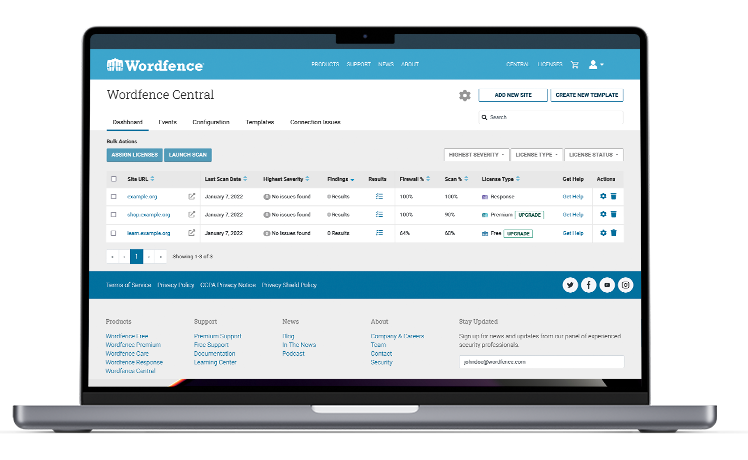
Manage all of your sites in one place with
Wordfence Central
Learn more >
The best kept secret in WordPress Security. Wordfence Central is Free for all Wordfence users including our Wordfence Free customers without any catch or upsell. Get an instantaneous view of the security posture of all your WordPress websites, configure Wordfence across a few or thousands of sites using templates, launch scans, manage licenses and view security events all from a Central Dashboard.
Breaking news from our blog
View all >
Wordfence Intelligence Weekly WordPress Vulnerability Report (July 15, 2024 to July 21, 2024)
📢 Did you know Wordfence runs a Bug Bounty Program for all WordPress plugin and themes at no cost to vendors?

10,000 WordPress Sites Affected by High Severity Vulnerabilities in BookingPress WordPress Plugin
10,000 WordPress Sites Affected by High Severity Vulnerabilities in BookingPress WordPress Plugin
Wordfence Intelligence Weekly WordPress Vulnerability Report (July 8, 2024 to July 14, 2024)
📢 Did you know Wordfence runs a Bug Bounty Program for all WordPress plugin and themes at no cost to vendors?

Wordfence Intelligence Weekly WordPress Vulnerability Report (July 1, 2024 to July 7, 2024)
📢 Did you know Wordfence runs a Bug Bounty Program for all WordPress plugin and themes at no cost to vendors?

7,000 WordPress Sites Affected by Privilege Escalation Vulnerability in ProfileGrid WordPress Plugin
📢 Did you know Wordfence runs a Bug Bounty Program for all WordPress plugin and themes at no cost to vendors?

$3,094 Bounty Awarded and 150,000 WordPress Sites Protected Against Arbitrary File Upload Vulnerability Patched in Modern Events Calendar WordPress Plugin
📢 Did you know Wordfence runs a Bug Bounty Program for all WordPress plugin and themes at no cost to vendors?
Wordfence Intelligence Weekly WordPress Vulnerability Report (June 24, 2024 to June 30, 2024)
📢 Did you know Wordfence runs a Bug Bounty Program for all WordPress plugin and themes at no cost to vendors?

WordPress Security Research: A Beginner’s Series
Learn How To Find WordPress Vulnerabilities Step-by-Step Welcome to the inaugural post of our WordPress Security Research Beginner’s Series!
Join the official Wordfence mailing list
Receive WordPress security alerts, news, and research in your inbox before it appears in the press.
Wordfence in the press
View all >Why choose Wordfence?
351M
total downloads
5M
sites with Wordfence
24/7
support, all year round
3,819
5-star reviews






