The March 2017 WordPress Attack Report
Today we are releasing the WordPress Attack Report for March, 2017. You can also find the following previous attack reports on our blog: December 2016, January 2017 and February 2017.
This report contains the top 25 attacking IPs for the month of March and their details. It also includes charts of brute force attack activity and complex attack activity for the period. We also include the top themes and plugins that were attacked and which countries generated the most attacks for the period.
One of the more surprising data points in this report is the rise of Algeria as a source of attacks. After creating this report we dug a little deeper and will be releasing our additional findings regarding Algeria next week.
The Top 25 Attacking IPs
I’m including our usual explanation of how the table below works. If you’re familiar with our attack reports, you can skip down to the table below which contains the March data and read my comments that follow the table.
Brief introduction if you’re new to viewing these reports
In the table below we have listed the most active attack IPs for March 2017. Note that the ‘Attacks’ column is in millions and is the total of all attacks that originated from each IP. Further right in the table (you may have to scroll right) we break out the attacks into ‘brute force’ attacks and ‘complex’ attacks.
Brute force attacks are login guessing attacks. What we refer to as ‘complex’ attacks are attacks that were blocked by a rule in the Wordfence firewall.
We have also included the netblock owner, which is the organization, usually a company, that owns the block of IP addresses that the attack IP belongs to. You can Google the name of the owner for more information. A Google search for any of these IP addresses frequently shows reports of attacks.
The hostname included is the PTR record (reverse DNS record) that the IP address owner created for their IP, so this is not reliable data but we include it for interest. For example, we have seen PTR records that claim the IP is a Tor exit node, but it is clearly not, based on traffic.
We also include the country and a country flag. To the far right of the report we show the date in March when we started logging attacks and the date attacks stopped. For many of these IPs we logged attacks for the entire month. For some you can see there is a clearly defined attack ‘window’ where the IP started and stopped.
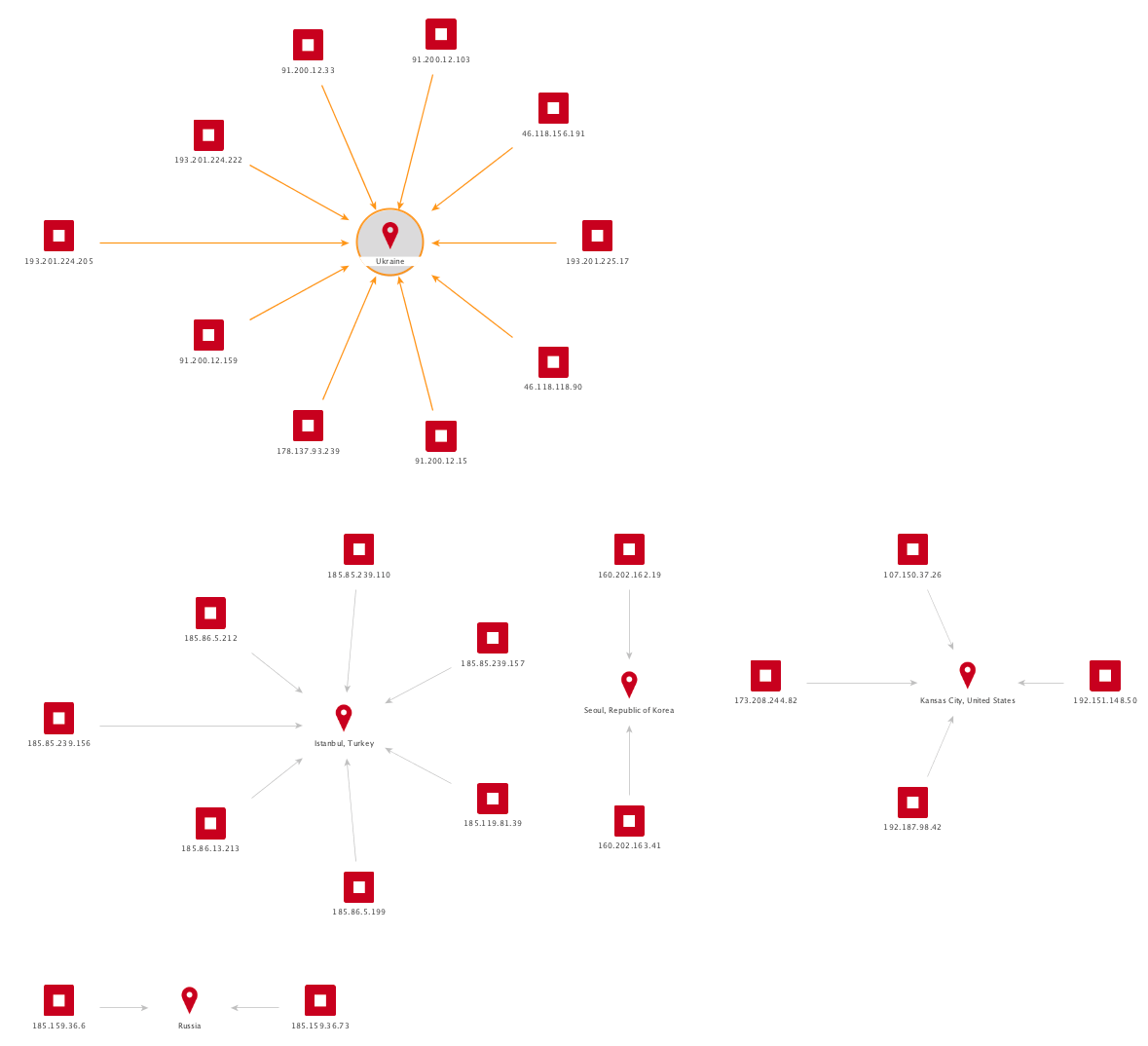
The Top Attacking IPs
Our top two attacking IPs are in Russia and Ukraine respectively. Both of them are only launching complex attacks on WordPress. Our top IP has doubled its attacks from 7 million to 15 million attacks. Our second place IP went from 7 million to 12 million attacks per month.
The total number of complex attacks from the top 25 IPs went from 63 million in February to 85 million in March. The total brute force attacks from the top 25 IPs increased from 18 million in February to 32 million in March. This indicates an increase in how aggressively these top 25 IPs are attacking sites.
If we cluster the top 25 attacking IPs by country, it becomes apparent that Ukraine is by far the top source for attacks. We also have a surprisingly large number of top attacking IPs from Turkey in March.
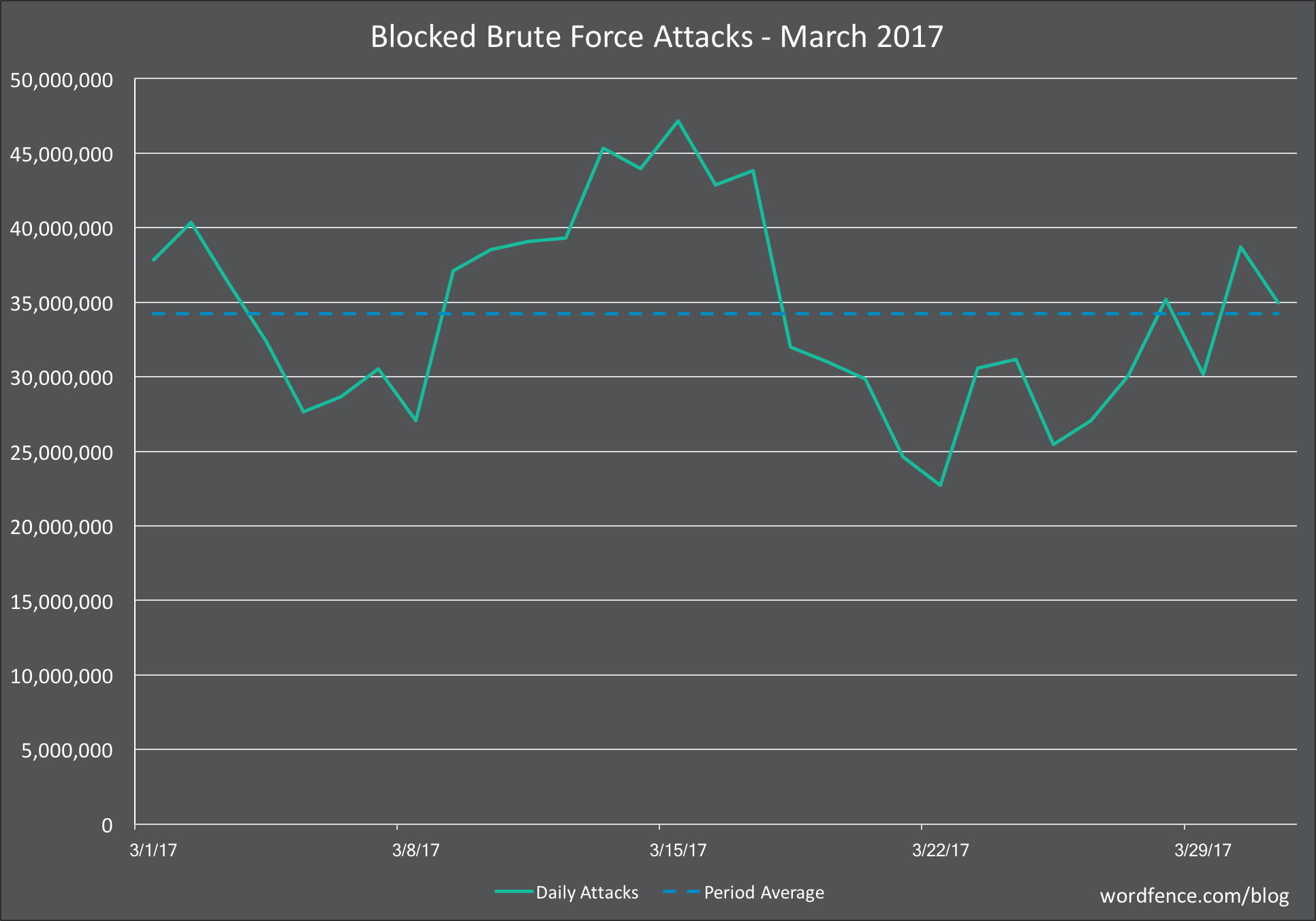
Brute Force Attacks on WordPress in March 2017
The chart below shows the brute force attack activity on WordPress sites that we monitor for the month of March.
We saw a slight increase in the average daily attacks from 30 million in February to 34 million in March. Not a big change, so in general the attack frequency and activity is fairly steady. In February we saw a huge sustained spike in activity towards the end of the month. We did not see that in March for brute force attacks.
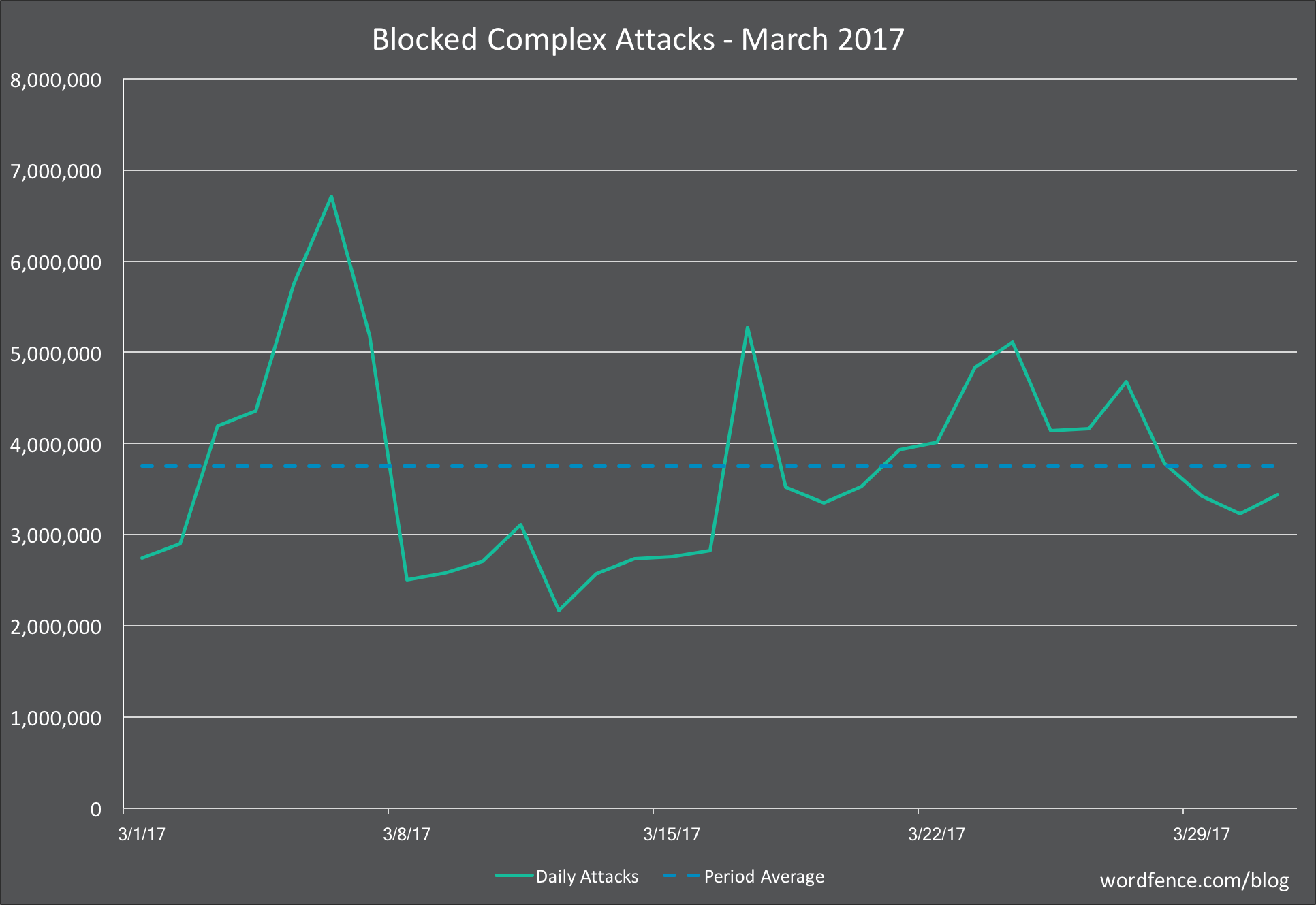
Complex Attacks on WordPress in March 2017
The graph below shows complex attacks (attacks that try to exploit a vulnerability) for the month of March 2017.
The average daily attacks increased from 3.4 million in February to 3.8 in March. In February the attack graph was fairly constant throughout the month. March saw a huge spike early in the month which quickly subsided.
Once the spike subsided, we saw a sustained period of relative calm with only 3 million attacks per day and then a gradual pick-up later in the month.
Attacks on Themes in March 2017
The table below shows the total number of attacks on WordPress themes. We identify each theme using it’s ‘slug’ which is the directory in which it is installed in WordPress.
There is some movement in the rankings, but for the most part the same themes are being targeted.
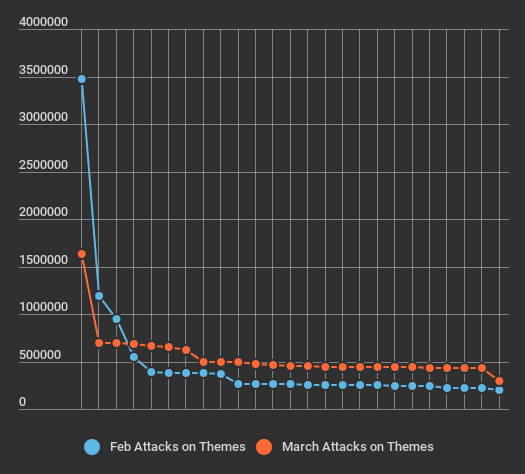
One interesting change we noted is that for the month of March, the attacks are more spread out. Below we generate a graph showing the “long tail” of attacks on themes. We have created a distribution from left to right of the most attacked themes to the least attacked. It creates a curve which is commonly known as a “long tail” among statisticians.
As you can see, for the month of March, the long-tail flattens out because we are seeing attacks more evenly distributed across themes, rather than focusing on a smaller number of frequently attacked themes.
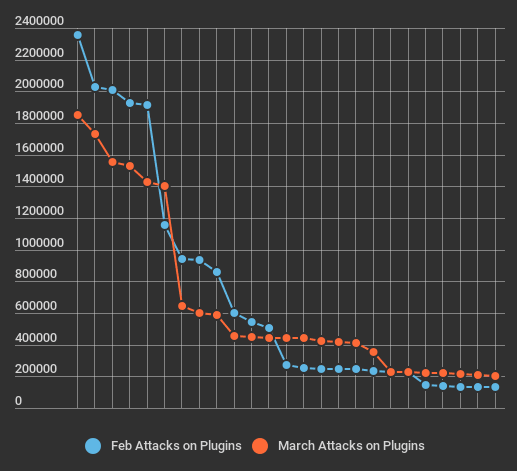
Attacks on Plugins in March 2017
The table below shows the attacks we saw on plugins across the sites Wordfence protects. As with themes, we identify each plugin by its unique ‘slug’ which is the unique installation directory where the plugin is installed.
The list of plugins being targeted has had some shuffling around, but as you can see, all plugins in the list are well known targets of attack that are generally in the top 50 attacked plugins for WordPress.
If we look at the long-tail distribution for plugins we can see that the attack distribution has not changed much and is still roughly the same as February.
Attacks by Country for March 2017
The table below shows the top 25 countries that attacks originated from in the month of March on WordPress sites that we monitor. The most surprising thing in this list is the sudden appearance of Algeria as an attack source. In our previous report, Algeria was ranked way down at 60 for total attacks.
We will be posting a follow-up post which explains why Algeria has suddenly jumped in the country rankings. We dug a little deeper and found some very interesting data that we will be including in a report which we expect to release next week.
Conclusion
I hope you’ve enjoyed this overview of the WordPress attack landscape. If you are in the threat intelligence field, I encourage you to grab this data and incorporate it into your own analysis. I know some of you already have and have shared your findings with us privately and I very much appreciate that.
We will be publishing a follow-up to this report describing why Algeria has risen in the attack ranks some time next week.

Comments
9:16 am
As always, thank you very much for all your work on this.
9:35 am
Very informative post, Mark. I have just had about 30+ mails from wordfence in the last couple of hours with the message Exceeded the maximum number of login failures which is: 20.
Would it be of any use to you if I compiled the IP addresses for you?
Best
Brendan
9:35 am
Thanks Brendan. We have excellent data on the kinds of attacks we're seeing across the surface that we protect. So I think we're all set.
9:41 am
Very interesting report. I have some difficulties to understand why people or machine are attaking sites with no value (ID card no, visa, accounting info, etc...). What so ever, Your plugin does a tremendous work. It saves me hours of work by not beeing obliged to reinstall a whole site. Thank you so much - Thierry (Belgium).
9:53 am
Thanks Thierry.
9:44 am
Are the top attacking IPs automatically blocked in my Wordfence, or should I be adding them to my blocked IP list?
9:52 am
If you are premium then the top attacking IPs are automatically blocked. In fact the list we use is several thousand IPs long and expanding. It's part of the new Premium IP blacklist feature we launched a few weeks ago.
10:39 am
Mark: That's great. I am premium. Do I need to do anything on my end to make sure the blacklist feature is active on my site, or it is automatic? Thanks!
10:50 am
Make sure you have enabled "Preemptively block malicious IPs" at the bottom of the Firewall page. It should be enabled by default. You can find the docs here:
https://docs.wordfence.com/en/WAF?utm_source=plugin&utm_medium=pluginUI&utm_campaign=docsIcon#Advanced_Configuration
8:35 am
Thank you!
9:58 am
Informative article as usual!
As this is the March 2017 report, to avoid confusion you may wish to update the month in the "The Top 25 Attacking IPs" section and following sub-section's text from February to March.
Thank you for all the hard work you and the Wordfence team put into protecting our WordPress sites!
10:40 am
Thanks. Fixed.
10:35 am
Since the top two attacking IPs are producing 24% of the total attempts each month and are coming out of Russia and Ukraine is there any reason to believe they are perhaps state sponsored since it would seem those IPs are not changing or being shut down and continue to operate month after month?
10:41 am
No I don't think you can make that attribution connection. I think it's more indicative that the hosting provider/ISP that owns that network is what is known as a bulletproof host.
11:12 am
Thanks for the contribution, last month I received several attacks on my web, since then I installed the plugin and hope to have no more problems. I will be attentive to your updates Thanks
11:25 am
Wordfence is the most valuable plugin I use for my WordPress sites, bar none. These reports are insightful, so thank you for all the work you do!
11:26 am
Thanks Jocelyn!
12:00 pm
This is a technical point not strictly germane to the topic, but your tables in this post don't display for me unless I turn on 3rd party cookies. IMHO this is not the best way of doing things (I mean the table software, not you). For security reasons I prefer to turn off 3rd party cookies in my browser. You may be surprised to know that almost everything in the internet works fine without them. I'm not so impressed with table display software requiring 3rd party cookies to function - the devs either need to turn them off altogether, or alter them to make the cookie be set by wordfence.com to become a first-party cookie.
On a positive note, a huge thanks for the wonderful security plug-in.
12:46 pm
Someone always tries to ask this question in one form or another, just as Andrew did this week and unfortunately for me I'm left wanting / unsatisfied so let me try asking in a different way:
Mark, from your lofty, overarching, (WordFence as a whole), and highly educated/informed point of view, with no need for specifics & thus in general, what percentage of all of these aforementioned attacks (say just mentioned here, ifor the month of March) would you say are broadly considered state actors and/or spillover from their activities?
Again, this is in general & solely out of my own curiosity, so from any origin, across any ip range, either directly from a state actor or one of their many private consultantancy group (think tanks, analysts, etc) working on behalf of / in conjunction with / really just not independent of said state, or even as spillover albeit rogue groups or cells acting on their own terms albeit as it may align with any such state (this would be like a tight knit group of anonymous or mIRC chat group aligning with a state on their own accord and NOT an ISIS/ISIL group which, unfortunately, in this context should be considered a state actor).
2:21 pm
Any intelligence analyst who isn't lying will tell you they think in terms of levels of confidence rather than certainty.
We have certain characteristics that may it more likely that an attacker may be a state actor. One of them is level of sophistication. In the Algeria attacks we see a level of sophistication that is much higher than regular attacks. More on that next week. But it could just be a kid with a 200 IQ in their bedroom, or it could be a state actor that is using the attacks as part of a broad reaching (to quote DHS/FBI) campaign of influence or military campaign of some sort.
Attribution is hard. I'm tempted to say it's impossible but I do think it's possible in some cases. Level of confidence is a great way to think about this and using "Nothing is 100% certain" as a departure point in your thinking is helpful.
Mark.
12:47 pm
Appreciate your hard work and analysis. Your illustration guide us protect from future attacks. Thanks for sharing.
1:12 pm
What is it about these themes and plugins that put them on the list? Are they built less secure than similar themes and plugins, or is it that they are widely used and therefore are subject to more intrusion attempts?
2:18 pm
Developers occasionally write vulnerabilities. It happens to any dev who ships enough code. Sometimes users take a long time to upgrade. That is why they are targeted - because the themes or plugins became popular and there are a lot of old sites out there running old vulnerable versions still.
11:46 am
Actually there's another attack on plug-ins I've come across, they hack the author's account and post a malicious plug-in update, had it happen a couple of months ago, fortunately Wordfence detected the malicious code immediately.
1:24 pm
Mark, a feature for your next update if possible, is to install a feature to block certain bots: ie) yandex (Russia) and msnbots which are attacking my site 24/7. The msn bots seem to come from the USA and contain our URL with some pornographic links- is it possible that these hackers can "mimic" the msnbot?
It these two search bots are added to the .htaccess file via the wordpress admin - that would be a great idea. If we can keep adding their ranges -that would be very helpful to be able to edit the .htaccess files directly from Wordpress admin area.
Very good information, and excellent security from you guys.
6:56 am
Put me on the list of those who'd like this feature very much, too.
Yandex, msn, any bot actually that has suspicious referrer data, should be blocked.
Even Yandex, I believe, if it does a real webspider-like scan of a site, should not contain pornographic sites, and other malicious sites, as their referrer data.
So, yes, we'd very much like to be able to easily block those.
Thank you
1:29 pm
I've just installed Wordfence so this is my first report. I found it crazy interesting - sadly that probably says more about me than you :) I even read bits out to everyone within earshot.
Looking forward to you ditching the dirt on Algeria. Thanks, and keep digging on our behalf.
5:47 pm
Thanks again for your incredibly detailed report. The amount of activity is unbelievable. I've enjoyed using your basic plugin. I'm seriously considering subscribing to Premium, for my own piece of mind. At this point, I need to block certain countries.
Great work!
12:21 am
Hi, please, all you are using wordpress, request them to change the install procedure of wordpress, to personalize all administrative urls from beginning.All sites are attacked from those IPs no matters what generator they use. By me, Ukraine should not have acces to internet anymore. One of the master who control the attacks is in "under net ua network" and the php source code they use is posted free on the internet. Don't trust no IP does not load/execute js, fsok to die if 80 is a must.
6:58 am
Mark, thanks for your elegant way of dealing with questions that are alluding to politics. Indeed, anyone who studies internet security issues should know that attribution is incredibly difficult and obviously impossible in many if not most cases. That's a huge problem in one sense, but also reflects how a person if they so desire can utilize the internet and maintain their personal privacy. So like a lot of things it's a two-edge sword.
Indeed, just because an attack is sophisticated doesn't mean it came from a state actor. Last time I studied on it, I learned there were entire business enterprises in Russia, Ukraine, Romania etc. devoted entirely to criminal hacking, these businesses employ thousands of people and sometimes are the main source of income for an entire town!
On to more practical matters. I assumed you already had all those bad IPs in your Premium block list. But are you blocking attacks on the plugin and theme URLs or should we end users manually add those into our "Immediately Block" list or in to the Wordfence firewall?
Thanks.
7:02 am
What Lakeside said.
I seem to get a huge amount of bandwidth sucking traffic from bots that appear to be from msn, yandex, and even Google. Would be a wonderful thing if Wordfence could put some effort into clarifying which of these are real, which are fake, and to give us specific tools to block the fake ones. Perhaps at least a blog post from you guys?
8:08 am
Going through the motions at the moment.My site has been under full on brute force attack for just under 24 hrs. No respite in sight. Thanks to wordfence. The first instance was from a Chinese IP scanning author 1,2,3 and so forth, then a failed login on wp-login.php with "admin" then i knew knew to keep an eye on developments.
Next was a full scale attempts at login with countless IPs from all corners of the earth.Now, my domain has a close resemblance to a high ranking UK GOV administrative agency.From my observation, i'm seeing a trend.
I'm not what you'd call a techie and i possibly did go overboard and renamed the wp-login.php.Shortly after, the requests were being made to XMLRP.php so i disabled that for external IPs.
I've trolled through the net and read up on everything there is to read.Needless to say i'm a complete noob at this. I'm however an analyst.
Now, as i stated, there is a trend. Cyber warfare? Absolutely!
Mark, with your recent data, how long has the longest attack carried on for? Thanks in advance.