Ask Wordfence: Should I Permanently Block IPs That I See Wordfence Blocking?
This is the fifth installment in a new series we started last month called Ask Wordfence. You can access previous posts here.
Today’s question comes from Brooke in Harrisonburg:
When I see IPs blocked by firewall, or blocked for trying to log in, is there a benefit to permanently blocking them, one by one, or is it enough that Wordfence just blocks them each time?
This great question is likely shared by a broad audience. We know that the blocking features in Wordfence are incredibly popular. In short, there is a potential benefit to permanently blocking these IPs, but there are also risks associated with it.
To help you decide how you want use blocking as part of your security strategy, we’ve pulled together a number of factors you should consider.
The Amount of Attacking IPs Can Be Overwhelming
In our monthly WordPress attack report for October, we reported that we had added 123,277 IPs to the Wordfence real-time IP blacklist during the month. That’s over 4,000 per day and 166 per hour. It is literally impossible for a site owner to keep up with the massive, ever-changing list of IP addresses that attack WordPress sites. By manually blocking even 1,000 malicious IP addresses, you are barely making a dent.
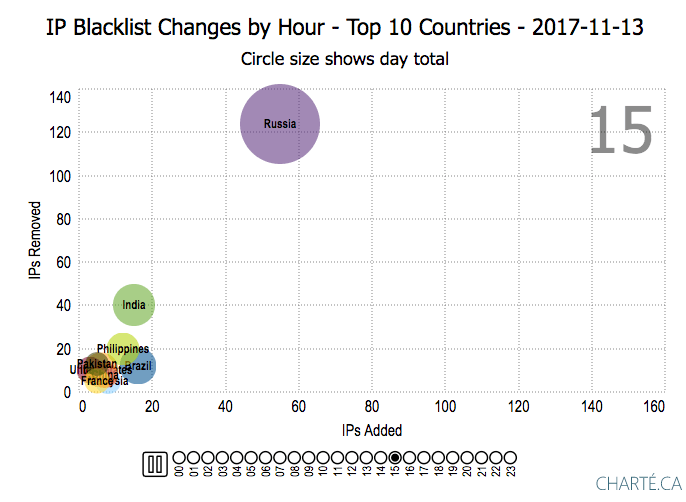
To visually illustrate the scale of the challenge we created this motion chart, which shows the total number of IPs we added and removed for just the top 10 countries this past Monday, by hour.
Attackers Cycle Through IPs Quickly
One of the most important factors to consider when developing your blocking strategy is how long IPs continue to attack. It varies dramatically by IP address. 91.200.12.91, for example, was the top attacking IP in our WordPress Attack Report in both September and October and was number 24 on the list in August. On the other side of the spectrum, many IPs stop attacking after just a few hours. Back in September we did a deep dive on the Wordfence real-time IP blacklist and found that the average IP address spends just 10 hours on the list.
The criminals that attack WordPress websites know that the IPs they use are going to be blocked by site owners and blacklists. In an effort to avoid being blocked, they regularly cycle through different IP addresses.
Attackers Don’t Reuse IPs as Often as You Might Think
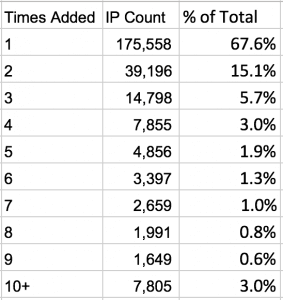
In the blacklist deep dive we mentioned in the previous section, we also looked at how often attackers reuse IPs. We found that, for the most part, they used an IP address just once, with less than a third being used twice or more. The table below shows the breakdown of the number of times we added IPs to the Wordfence real-time IP blacklist during the month of August.
Many Attacking IPs Actually Belong to Other Attack Victims
As we’ve discussed above, attackers need access to lots of IP addresses. Being criminals, they generally don’t solve that problem by going out and paying for them. Instead they find ways to take over the IPs of victims who have clean reputations. As we wrote last week, in many cases it is your clean reputation that makes you a target.
One source of clean and fresh IPs that we see attacking WordPress websites is hacked home routers. You might remember our posts earlier in the year about a large home router botnet being used for WordPress brute force attacks. The IPs belonged to a long list of ISPs from around the globe, and each one represented an unsuspecting victim’s home.
Putting It All Together
Blocking IPs manually is generally an ineffective security tactic. Attackers generally cycle through IPs quickly and tend not to reuse them. Attacking IPs often belong to victims, so you risk blocking real users who want to access your website.
Blocking large groups of IPs, like entire countries, is a popular approach many site owners use. But there are significant risks and headaches associated with blocking legitimate requests from online services like Google Adwords, search engines and service providers. If you can overcome those challenges, however, this can be a very useful layer of security for some site owners.
Let Wordfence Do the Work For You
Wordfence Premium includes an IP blacklist that we update in real time. We add thousands of IPs to the list each day, staying a step ahead of attackers as they cycle through IPs in their attempts to evade IP-level blocks. We also remove thousands of IPs each day, minimizing the impact of blocking IPs that belong to the unsuspecting victims’ routers and other devices. The most you’ll pay for Premium is $99 per year, which means you can enable 24/7 real-time blocking at scale for less than 30 cents per day. Considering how much time is typically involved in manually trying to manage your own IP block list, we think that’s a great value.

Comments
10:29 am
Nice infographic. I manage several sites and frequently use country blocking (Premium) while under attack. Is there a way to unblock selected IPs from affected countries without unblocking the entire country?
10:32 am
Hi Ames,
Thanks so much for the kind words and for being a valued Wordfence customer. :) While we can't provide support via blog comments, we'd love to help you out with your questions, so please do send in a Premium support ticket via the support portal, and we'll be happy to answer any questions you have!
10:31 am
Great article on "to manually block or not to manually block". We had an interesting occurrence between January 2017 and March 2017. We host about 27 websites and all of them also have a web maintenance & security agreement with us. During those three months our entire VPS server was targeted by hackers specifically from France. It caused our server and all of our sites to go down about 20 times during these 3 months. The only solution that worked for us was using our Control Panel IP Blocker and we blocked every IP range that kept coming up in our Wordfence report. We don't even do business in France..but of course they were probably just victims as we were. However, within 2 weeks that issue stopped in its tracks. Since then we've cleared out our IP Blocker and have not had another issue since March 2017. Our web hosting company had no clue why only France. Thanks again for a great article.
10:47 am
I always block foreign countries, I do not do business with any of them, and don't care if they can see my sites or not, other than generating a bit of stat traffic, it is of no value to let Russians to visit my sites. But obviously, others might do business with Russia, seems to be in the news a lot lately
11:07 am
Its kinda terrible, but I tend to feel the same way. I don't block all foreign countries, but I have blocked Russia and Turkey because they do seem to test the fence on my site a lot and I figure, eh, odds are I am never doing business with them.
10:55 am
Is blocking whole countries worthwhile? What happens if they use a VPN? They can be in any country and pretend to be in another.
1:38 pm
Hi David, blocking whole countries can be worthwhile as long as you are certain it won't break anything or block anything important like search engines. Attackers definitely utilize VPNs and other proxies to hide their locations, so you're not blocking people in a given country, just IPs that map to it.
10:59 am
This is fine for Wordpress sites but what about other domains (e.g., vBulletin or Xenforo forums, HTML sites)?
Any plans to develop the Wordfence plugin for other platforms?
6:39 am
Not at this time. But watch this space.
12:33 pm
Hi , we have paid for Wordfence Premium for some fo the sites we manage. Reading todays article about IP Blocking, the realtime IP blacklist in the Premium looks a great feature. We are wondering what if any performance hit the sites will take, presumably the website has to go away and check the visitors IP address against the large IP blacklist for every visit ?
Thanks very much
1:32 pm
Hi Adrian, enabling the IP blacklist will not slow down your site. Check the section titled "Will this slow down my site?" in this blog post: https://www.wordfence.com/blog/2017/03/wordfence-ip-blacklist/.
1:51 pm
I was wondering about the efficiancy (machine resources of wordfence blocking, its being blocked at the php level), is there any benefit in creating a log of blocked IP addresses which could be passed into iptables using something like fail2ban. This coud be automated, and the blocked ip addresses would be blocked much earlier. A time limit would unblock the address later, and if still bad wordfence would update the log to ensure it was again banned by iptables.
6:38 am
Wordfence is incredibly fast, especially when blocking using the IP blacklist.
1:51 pm
Its obvious someone can't manually filter these rouges and the ip they use, that is where a plugin like Wordfence comes to play.
2:18 pm
While I tend to "not blocking" individual IP addresses, I may do so if I see repeated attacked over weeks or months - particularly if from a specific IP block or region.
I have a question however.... Sometimes, an IP address (or range) will hit the login page 1000's of times within a few hours (brute force attacks). In such a case, I'll put an IP block in the .htaccess file to avoid performance problems, server bandwidth usage, etc. In such a case, is blocking the IP address a good or bad idea?
Thanks,
Rob
6:07 pm
We blocked Russia using htaccess and eliminated 90% of hack attacks overnight. When Wordfence reports a blocked IP we do IP block at cpanel to hopefully avoid attacks on other sites on our servers.
Would rather take the risk of blocking an innocent party than give a hacker a chance.
Also given that such an overwhelming number of computers hacked being due to owner negligence or incompetence, I don't feel any regret for removing them from our environment.
3:08 am
I think that this is an "it depends" kind of situation. Certain netblocks are obvious repeat offenders -- I have blocked 91.200.12.0/24 and am very glad that I do. (I don't think it's any coincidence that the example IP in the blog post came from that block). As I also use Cloudflare, this block prevents those known bad guys* from even reaching my server - so that also saves on server load -- those guys never stop. (* See https://www.wordfence.com/blog/2017/03/jersey-shore/)
But only a relatively few IP's fit that category. It's worth looking for patterns over time. The data provided in this blog is a valuable source of information in that respect.
3:26 am
Me for myself, i blocked all IPs from Russia permanently. I'm not interessted in readers from there, since there are so many attacks coming from there.
6:07 am
I have blocked ranges of IP's only to find the next time they come at out site, they've added an IP address to the range I already blocked. They just keep adding new IP's to the range.
This is maddening. So I block the new range again with the added IP. They buy or get IP's by the thousands.