Unauthenticated Stored XSS Vulnerability Patched in Ultimate Member WordPress Plugin
On February 28th, 2024, during our second Bug Bounty Extravaganza, we received a submission for an unauthenticated stored Cross-Site Scripting (XSS) vulnerability in Ultimate Member, a WordPress plugin with more than 200,000+ active installations. This vulnerability can be leveraged to inject malicious web scripts.
Props to stealthcopter who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $563.00 for this discovery during our Bug Bounty Program Extravaganza. Our mission is to Secure the Web, so we are proud to continue investing in vulnerability research like this and collaborating with researchers of this caliber through our Bug Bounty Program. This demonstrates that we are not only committed to investing in making the WordPress ecosystem more secure, but also the entire web.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those using the free version of our plugin, are protected against any exploits targeting this vulnerability by the Wordfence firewall’s built-in Cross-Site Scripting protection.
We provided full disclosure details to the Ultimate Member Team on March 2, 2024, and received a response on March 4, 2024. The developer released a patch on March 6, 2024. We would like to commend the Ultimate Member Team for their prompt response and timely patch.
We urge users to update their sites with the latest patched version of Ultimate Member, which is version 2.8.4, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: Ultimate Member – User Profile, Registration, Login, Member Directory, Content Restriction & Membership Plugin
Plugin Slug: ultimate-member
Affected Versions: <= 2.8.3
CVE ID: CVE-2024-2123
CVSS Score: 7.2 (High)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:L/A:N
Researcher/s: stealthcopter
Fully Patched Version: 2.8.4
Bounty Award: $563.00
The Ultimate Member – User Profile, Registration, Login, Member Directory, Content Restriction & Membership Plugin plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the several parameters in all versions up to, and including, 2.8.3 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Technical Analysis
Ultimate Member is a WordPress membership plugin, which includes many premium features and functions. One such feature is the custom registration form, the other is the member directories, which lists the users on the website.
Unfortunately, insecure implementation of the plugin’s members directory list functionality allows for the injection of arbitrary web scripts. Examining the code reveals that the plugin includes members-list.php or members-grid.php template view files depending on settings, which contain underscore.js templates for user listing.
The WordPress defines its own interpolation tags, which is inspired by Mustache templating syntax.
Interpolate (unescaped): {{{ }}}
Interpolate (escaped): {{ }}
The user display name is displayed unescaped in the plugin template files:
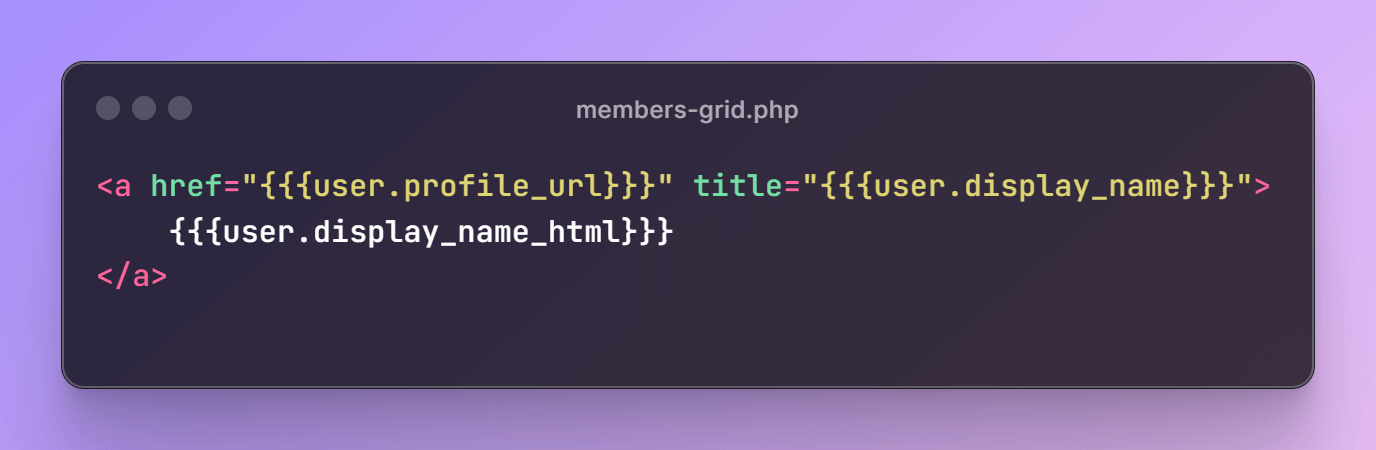
The view file receives the user data via AJAX from the ajax_get_members() function, which uses the build_user_card_data() function to compile the user data. No escape function is used for these functions either.
$data_array = array(
'card_anchor' => substr( md5( $user_id ), 10, 5 ),
'id' => $user_id,
'role' => um_user( 'role' ),
'account_status' => um_user( 'account_status' ),
'account_status_name' => um_user( 'account_status_name' ),
'cover_photo' => um_user( 'cover_photo', $this->cover_size ),
'display_name' => um_user( 'display_name' ),
'profile_url' => um_user_profile_url(),
'can_edit' => $can_edit,
'edit_profile_url' => um_edit_profile_url(),
'avatar' => get_avatar( $user_id, $this->avatar_size ),
'display_name_html' => um_user( 'display_name', 'html' ),
'dropdown_actions' => $dropdown_actions,
'hook_just_after_name' => preg_replace( '/^\s+/im', '', $hook_just_after_name ),
'hook_after_user_name' => preg_replace( '/^\s+/im', '', $hook_after_user_name ),
);
The attacker can provide a name with a malicious script during registration as an unauthenticated user.
As always, Cross-Site Scripting vulnerabilities can be used to inject code that can add new administrative users, redirect victims to malicious sites, inject backdoors into theme and plugin files, and so much more. Combined with the fact that the vulnerability can be exploited by attackers with no privileges on a vulnerable site, this means that there is a high chance that unauthenticated attackers could gain administrative user access on sites running the vulnerable version of the plugin when successfully exploited. As such, we strongly recommend that you verify that your site is running the most up to date version of the plugin immediately.
Disclosure Timeline
February 28, 2024 – We receive the submission of the stored Cross-Site Scripting (XSS) vulnerability in Ultimate Member via the Wordfence Bug Bounty Program.
March 1, 2024 – We validate the report and confirm the proof-of-concept exploit.
March 2, 2024 – We send over the full disclosure details.
March 4, 2024 – The vendor acknowledges the report and begins working on a fix.
March 6, 2024 – The fully patched version of the plugin, 2.8.4, is released.
Conclusion
In this blog post, we detailed a stored Cross-Site Scripting (XSS) vulnerability within the Ultimate Member plugin affecting versions 2.8.3 and earlier. This vulnerability allows unauthenticated threat actors to inject malicious web scripts into pages that execute when a user accesses an affected page. The vulnerability has been fully addressed in version 2.8.4 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Ultimate Member.
All Wordfence users, including those running Wordfence Premium, Wordfence Care, and Wordfence Response, as well as sites running the free version of Wordfence, are fully protected against this vulnerability.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.

Comments
9:28 am
Only $500?
I know the install count for the plugin isn't in the millions but its used on a lot of business and organization sites where an attacker would have a goldmine of data with access. And the vuln is very easy to exploit with no account.
This amount isn't very motivating to researchers to look for vulns in plugins used by high value target websites but with a low install count.
The amount should be closer to $2000
12:24 pm
Hi John,
It is difficult to objectivity determine high-value target usage of a plugin at the scale we process vulnerabilities, and it would be difficult for researchers to always know which would qualify in all cases. Rather we rely on install count which is a metric that researchers have access to.
We run the Wordfence Bug Bounty Program to invest in the WordPress community and help make it safer. We do not develop and are not directly associated with the vast majority of plugins we offer bounties on. We’ve built our Bug Bounty Program to be sustainable and to provide what we view as fair payouts to reward researchers for their work while benefiting the community.