The July 2017 WordPress Attack Report
This post is a continuation of the WordPress Attack Report series we’ve been publishing since December 2016. Reports from previous months can be found here:
This report contains the top 25 attacking IPs for the month of July and their details. It also includes charts of brute force and complex attack activity for the same period. We also include the top themes and plugins that were attacked and which countries generated the most attacks for this period.
The Top 25 Attacking IPs
The next section is our standard explanation of how the table below works. If you are familiar with our attack reports, you can skip down to the table below this section, which contains the data for July along with some commentary.
Brief Introduction (If You Are New to Viewing These Reports)
In the table below, we’ve listed the most active attack IPs for July 2017. Note that the “Attacks” column is in millions, and is the total of all attacks that originated from each IP. Farther right in the table (you may have to scroll right) we break down the attacks into “brute force” attacks and “complex” attacks.
Brute force attacks are login-guessing attacks. (You can learn more about how brute force attacks work in our Learning Center article about them.) What we refer to as “complex attacks” are attacks that were blocked by a rule in the Wordfence firewall.
We have also included the netblock owner, which is the organization (usually a company) that owns the block of IP addresses that the attack IP belongs to. You can Google the name of each owner for more information. A Google search for any of these IP addresses frequently shows reports of attacks.
The hostname included is the PTR record (reverse DNS record) that the IP address owner created for the IP, so this is not reliable data, but we still include it for interest. For example, we have seen PTR records that claim an IP is a Tor exit node, when, based on traffic, it is clearly not.
We also include the city and country, if available. To the far right of the report, we show the date in July when we started logging attacks and the date the attacks stopped.
The Top Attacking IPs
The total attacks from the top 25 attacking IPs decreased slightly from 133 million in June to 124 million in July.
Brute force attacks made up an amazing 87% of total attacks for July, up from 67% in June. Complex attacks accounted for 13% of the volume.
As usual, the list is dominated by Ukraine and Turkey followed by the United States.
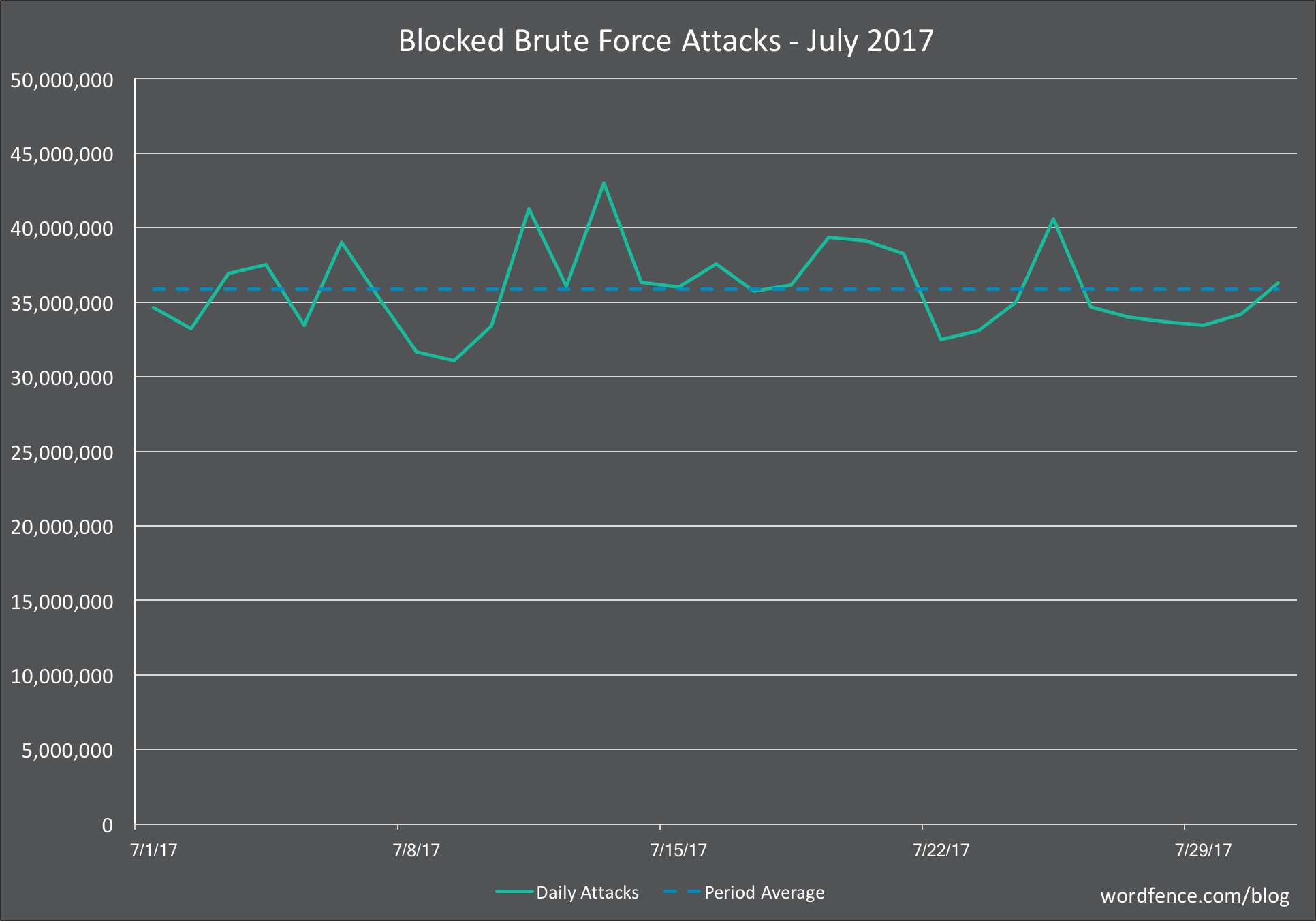
Brute Force Attacks on WordPress in July 2017
In the chart below, we show the number of daily brute force attacks on the sites we monitor for the month of July.
The average number of daily brute force attacks increased 21% from last month, which was up substantially from May. Daily attack volumes were incredibly stable throughout the month, with no big peaks or valleys. It’s almost like the attackers went on vacation and left their malicious bots running on autopilot.
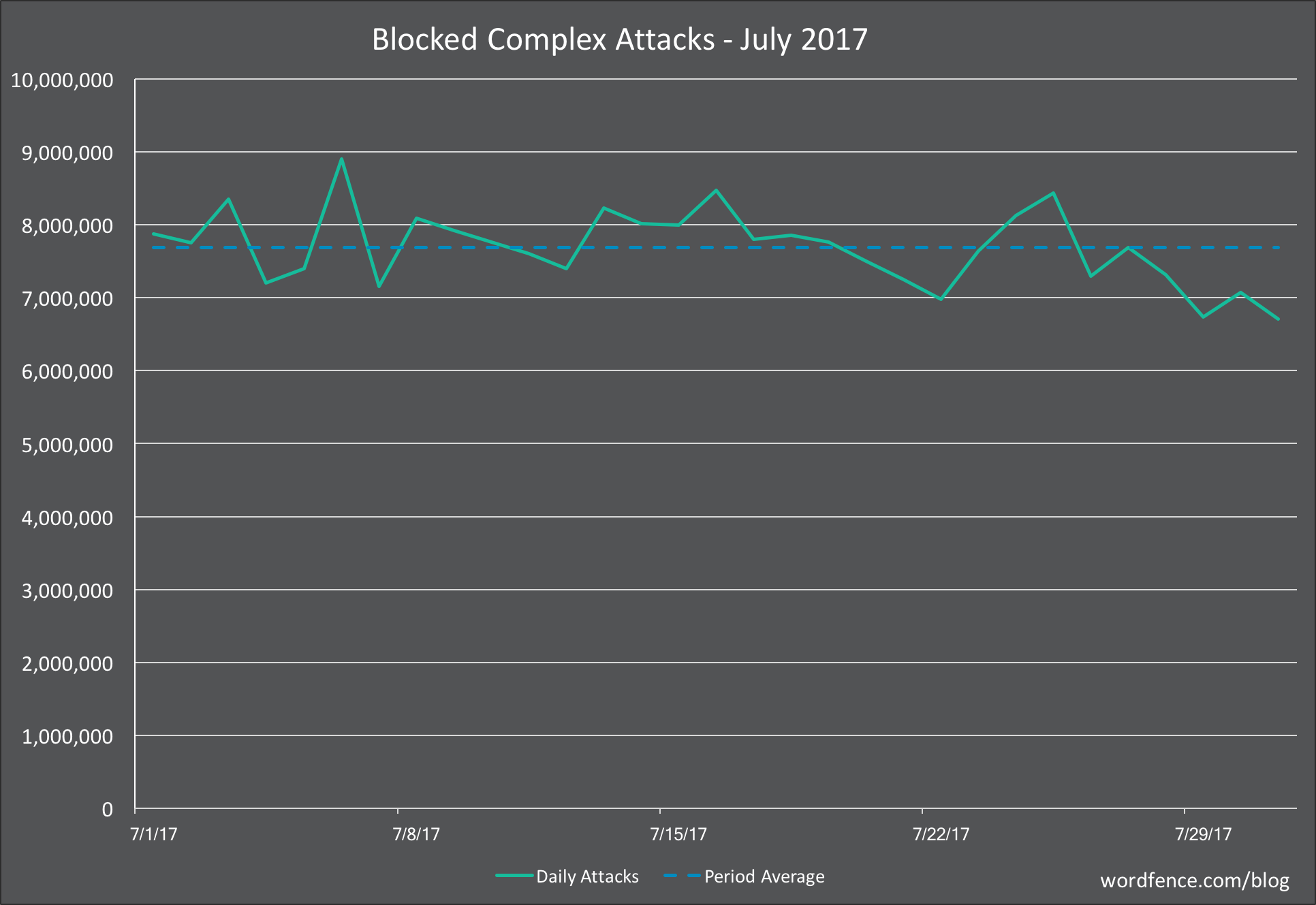
Complex Attacks on WordPress in July 2017
In the graph below, we show the daily complex attacks (attacks that attempt to exploit a security vulnerability) for July.
Average daily attack volume for July was up 6% from June for the sites that Wordfence protects at 7.2 million. As with brute force attacks, daily volume was incredibly stable.
Attacks on Themes in July 2017
The table below shows the total number of attacks on WordPress themes. We identify each theme using its slug, which is the directory where it is installed in WordPress.
We saw a lot of movement in the top 25 this month when compared to June. The biggest mover on the list was the ‘clockstone’ theme, coming out of nowhere to take the #3 spot in the rankings. Digging into the details the attacks are all malicious file upload attempts, attempting to exploit a vulnerability that has been public knowledge since August of 2014. Furthermore, the theme appears to no longer be supported by the author. The attacks targeting this plugin originated from 1336 unique IPs during the month, suggesting that the attacker (or attackers) are using a botnet to launch the attack. The top 10 IPs were responsible for just over two thirds of the attacks.
Another big mover on the list is the ‘sealight’ theme, moving up 32 places to number 12 on the list. Looking at the detailed attacks they are all attempting to exploit a very well known vulnerability in TimThumb, which was discovered in 2011. The vulnerability impacted many WordPress themes, apparently including the ‘sealight’ theme. The attacks on this theme originated from 130 IP address, with the top 10 account for 75% of attacks.
The last big mover on the list that we looked into was the ‘typebased’ theme, which moved up 26 places to number 17. This is another theme that appears to no longer be supported or available for download. Looking at the the attacks they are all trying to exploit the same TimThumb vulnerability that the attacks on the ‘sealight’ theme are targeting. Attacks came from 136 unique IP addresses during the month, with the top 10 accounting for over 68% of the total.
Attacks on Plugins in July 2017
The table below shows the total number of attacks on WordPress plugins. As with themes, we identify each plugin by its unique slug, which is the unique installation directory where the plugin is installed.
The top 25 list for plugins also changed a lot toward the bottom, with six plugins month weren’t on the list in June. We looked into the details of the biggest mover on the list, ‘wp-pagenavi’, which moved up 38 spots to number 11. The surge in attacks are attempting to exploit the TimThumb vulnerability we discussed in the theme section. We couldn’t find reference to the plugin including TimThumb, but given that the TimThumb vulnerability in question is over 5 years old now it would be difficult to say for sure.
The next biggest mover on the list was ‘wp-rocket’, a caching plugin that is running on over 260k sites according to their website. The surge in attacks are attempts to exploit a Local File Inclusion vulnerability that was fixed and publicly announced in June when version 2.10.4 was released. Attacks originated from over 89k unique IP addresses, with the top 10 accounting for just under 50% of the total.
Attacks by Country for July 2017
The table below shows the top 25 countries from which attacks originated in the month of July on WordPress sites that we monitor.
The top 3 countries remained the same, with very little movement throughout the list.
Conclusion
That concludes our July 2017 WordPress attack report. We were disappointed to see attack volume up yet again in July and hope to see that trend reverse itself again in August.

Comments
9:11 am
As always, I'm soooo glad I run Wordfence. You guys keep us all sane & safe, thanks! I've been following Mark's posts with a close eye and as a long term WP webmaster I am amazed almost every time with all the insight we get from you guys. Thanks again!
9:35 am
Since the router spam-bots came back online a few months ago I am seeing a HUGE increase in Wordpress brute force login attempts. It was nice while there was that short lull but now they have returned in full force. I have 5-6 sites that get hammered with over 100 login attempts daily. Annoying but thankfully Wordfence has so far kept me secure and safe.
I always appreciate hearing what is really going on in the "hack attack world" so your monthly posts are both interesting and informational.
The urgent updates re: plugin/theme/WP security issues are extremely important to hear about and are greatly appreciated.
Keep up the excellent work Wordfence team!!
2:22 pm
Why don't you change your login URL? They can't try to login if they can't find your login page! I also set Wordfence to automatically block anyone who tries to login with any of these as usernames: admin, administrator, webmaster, developer, the site's domain name; and I set a cool down of 30 minutes if logins fail more than a handful of times. I hope this helps - cheers!
3:07 pm
Unfortunately most brute force attacks don't come in via your login page. They arrive via XMLRPC. So changing your login URL doesn't help with this.
See: https://www.wordfence.com/blog/2017/01/xmlrpc-wp-login-brute-force/
9:38 am
I've definitely noticed an increase in malicious file upload attempts this month. It's fantastic to know that Wordfence is doing so much to stop these attacks being successful as it was a malicious file upload that took our site offline for almost a week whilst we cleaned up the mess. I've learnt such a lot from the blog and it means I'm much more confident keeping the site secure whether that's by moving files to non-default locations or just ensuring plugins are still supported and up to date. Thanks so much and keep up the good work!
10:31 am
I am seeing a massive increase from Thailand the last few days and good old Ukraine, but Wordfence is keeping everything safe, keep up the good work guys, without Wordfence I would not use wordpress at all.
7:17 pm
I am the author for wp-pagenavi, I just want to clarify that the plugin has never use TimThumb before because there is no need to.
I know there are themes that bundled wp-pagenavi with it and probably those are the ones with TimThumb as it is included in the theme.
2:17 am
I've noticed a big change in login attempts on my site - up to about three weeks ago they were mostly a couple of attempts from random sites that didn't try again, often a number of sites around the world at about the same time. At the beginning of August I saw attacks that made more attempts, usually 5 or 6, and I began to see the same sites try on successive days. Most attacks are via wp-login (which was removed ages ago) and not by xmlrpc ( about 50:1). I have \wp-login flagged in Wordfence to block, but it seems only some wp-login attempts are blocked - including all the new multiple ones, but not solitary ones - not sure why?
I always permenently block any IP that I see make a login attempt - its only recently that I've seen many IPs that come back. If you look at the patterns you can see which IPs are probably slaves to the same botnet. There is definitely a new net in August with me on their radar!