This site uses cookies in accordance with our Privacy Policy.
1.6: Understanding Zero Day Exploits & Disclosures
This document introduces two foundational security concepts that are important for all WordPress website administrators to understand. As you secure your WordPress website, you will encounter zero day vulnerabilities and how they and other non-zero day vulnerabilities are disclosed. It’s important for you to understand the seriousness of zero day vulnerabilities and how they are normally disclosed so that you can quickly and effectively secure your site against them.
Zero Day: Origin of the Term and Detection
Origin of the Term Zero Day
In the 1990’s, there was a software piracy scene that was called the ‘warez’ scene. It was groups of people that shared commercial software illegally using modems. The scene still exists today but uses BitTorrent and other more modern technologies. Back then, modems were slow and transferring pirated software took a long time.
The software would be posted to bulletin boards for members to download. It would be categorized into ‘Days’. One Hundred Day would mean that 100 days have elapsed since the software was released to the public. ’30 Day’ would mean 30 days have elapsed, so software in this category was newer. The most sought after was ‘Zero Day’. This was software that had not yet been released to the public. Often this software was acquired by hacking into a company’s network and stealing their unreleased software, or by an insider who stole the software before release. For this reason the hacking and warez scenes were closely linked.
Modern Meaning of Zero Day
The modern security industry has borrowed the term ‘zero day’ from the 1990s warez scene to indicate a security hole in software, where the vendor of that software has had ‘zero days’ to fix the problem. So, for example if you have a ‘zero day’ vulnerability in Adobe Flash, it means that Adobe has not yet been made aware of the security problem and there are likely millions of people running a version of Adobe Flash that has this security hole.
Today when speaking in person to security professionals you’ll often hear them pronounce ‘zero day’ as 0Day which is pronounced ‘Oh Day’. So if you want to seem hip, make sure you stick with the correct pronunciation.
Important To Note: When you hear about a new Zero Day in WordPress or a theme or plugin, you need to pay careful attention. Immediately check to see if there is a fix available. If not you should consider disabling and removing the software that contains the Zero Day if this is feasible without stopping your operations. Then contact the vendor and ask them when a fix will be released. Once you’ve done that, keep a close eye on vendor announcements so that as soon as a fix for the Zero Day is released, you can apply it and know that your website is secure again.
Forever Day
A “forever day” vulnerability is one where the vendor won’t fix the vulnerability. This usually happens because the vendor or original author is no longer maintaining the software. They may no longer be in business or the author may have moved on and abandoned the project.
You can avoid ending up with Forever Day vulnerabilities in your systems by using software that is actively maintained.
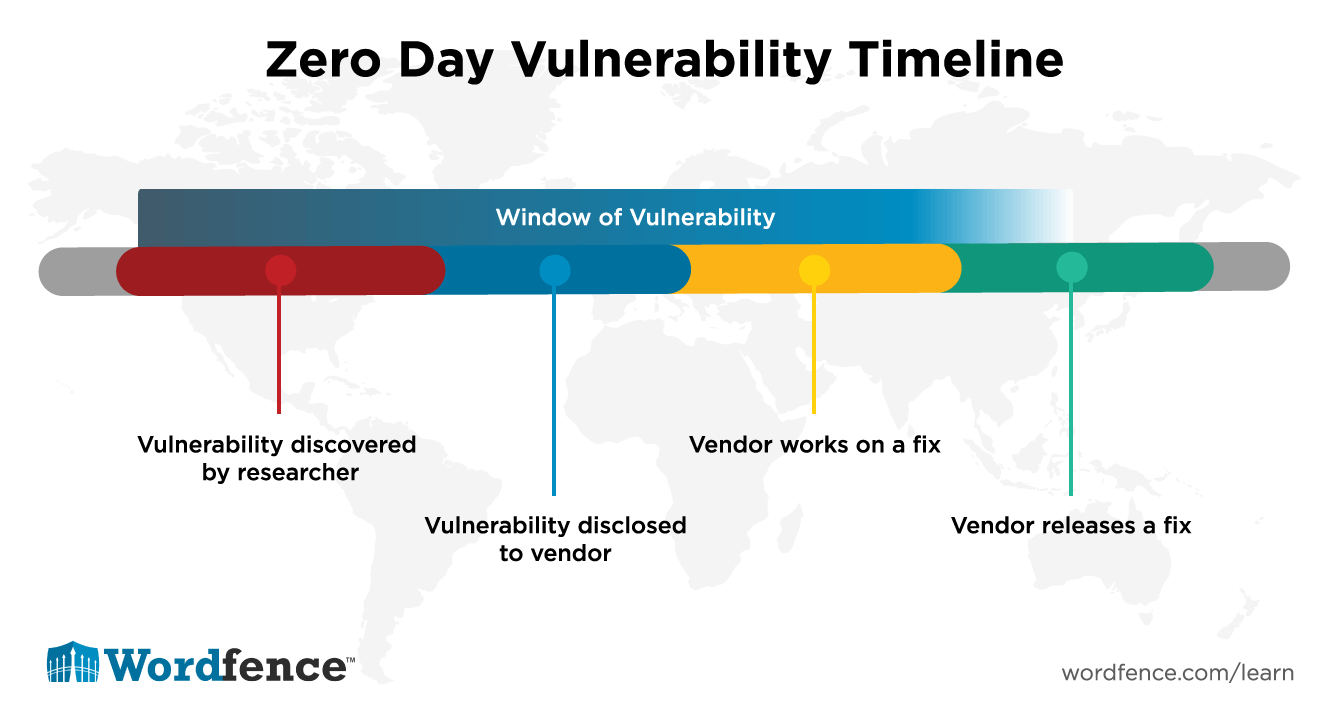
Window of Vulnerability (WoV)
The Window of Vulnerability is the time between when a vulnerability becomes known to an individual, a group or the general public and when a fix is released by a vendor. The way vulnerabilities are discovered, disclosed and fixed varies between platforms and communities, but in general the sequence of events is as follows:
- A vulnerability is discovered by a researcher or malicious actor. WoV Starts at this point because the vulnerability is known and no fix is available. The vulnerability starts being a Zero Day at this point.
- The vulnerability is disclosed to the vendor or the vendor discovers its existence through other means. At this point the vulnerability stops being a Zero Day because the clock now starts on the number of days the vendor has had to fix the issue. The WoV is still open.
- The vendor may or may not publicly acknowledge that it is a valid security problem.
- The vendor works on developing a fix.
- The vendor releases the fix either as a regularly scheduled update (e.g. Microsoft’s “patch Tuesday”), or releases an emergency release containing the fix to their customers. At this point the WoV ends because customers start patching the product.
Military and Intelligence Hoarding of Zero Day Vulnerabilities
Zero Day vulnerabilities are not always reported by researchers. The Stuxnet worm, which targeted industrial control systems in Iran’s Uranium enrichment infrastructure exploited four separate Zero Day vulnerabilities. The Office of Personnel Management breach in 2014 used a Zero Day to gain access and this hack has been attributed to China.
Zero Day vulnerabilities are the equivalent of digital weapons in a Cyber War scenario. Stockpiling Zero Days is useful if you need a large toolkit to attack target networks. The United States National Security Agency has been accused by the Electronic Frontier Foundation of hoarding Zero Day vulnerabilities.
Protecting against Zero Day Vulnerabilities
While Zero Day vulnerabilities are more serious than known vulnerabilities, there are various methods one can use to protect against them.
- Signature based defense: This technique uses pattern matching to identify patterns in known vulnerabilities. This technique does not do a good job of identifying specific code in Zero Day vulnerabilities. However it can identify known attacks like SQL injection that target products suffering from a Zero Day vulnerability. While a vendor may not be aware of the existence of a vulnerability in their product, making it a Zero Day, a firewall may be able to protect against the attack because the specific attack type, whether SQL injection, XSS or another type, may be known.
- Statistical techniques: These learn what normal activity looks like on a network. They will then alert if traffic or behavior deviates from that normal profile. For example, if an email user on a protected network receives a message from someone who has never contacted them in the past, with a file attachment and that attachment calls a Flash function that is rarely used, the statistical algorithm might flag the email for further inspection.
- Behavior based defense: There are various ways to implement this technique, but a common implementation relies on a ‘honeypot’. A honeypot is a machine that is purposely made less secure and is used to detect the presence of hackers when they target that machine with weak security. In this case the honeypot is monitored for any unusual changes. For example, before an email attachment is allowed into a network being protected, it will be allowed onto a honeypot machine and will be monitored. If it appears to infect that machine, it is flagged for further inspection.
- Hybrid techniques: These use a combination of statistical, behavior and traditional signature based algorithms. They are more effective because they avoid weaknesses in any single detection technique.
You can read more about Zero Day detection techniques at sans.org where they’ve published a PDF on the subject (2014).
Vulnerability Disclosure: How it Works
Security holes in software and network devices are discovered by:
- Security researchers: These are people who work for large and small businesses and who work on their own.
- Malicious hackers: They tend to not disclose vulnerabilities to the public because they want to use them to gain access.
- Vendors themselves: The individuals and companies who make software will often find a security hole in their own products and release a fix.
The way the public is told about vulnerabilities is called ‘disclosure‘ or ‘vulnerability disclosure‘. It is a controversial subject and is constantly being debated. Most vulnerabilities that are disclosed publicly are discovered by security researchers. The steps they take to disclose a vulnerability to the vendor (software maker) and then the public are usually as follows:
- The researcher discovers the vulnerability. At this point the WoV time-frame begins. The vulnerability is also known as a Zero Day at this point.
- The researcher contacts the vendor privately and lets them know that they have a security problem and supplies the details. At this point the vulnerability is confidential and it stops being a Zero Day. However, the WoV is still open.
- The vendor and researcher will then agree that the vendor has a certain amount of time to fix the vulnerability before the researcher releases details to the public. This can range from a few days to several months. They may also agree to an open time-frame where the researcher will only let the public know when the vendor says they’re ready.
- The vendor will then release a fix to their customers. For example, Microsoft will release a new version of Internet Explorer which contains a security fix. At this point the WoV closes because a fix is now available to customers who use the software.
- Once the fix has been released and the customers have had enough time to upgrade, the researcher will release full details of the vulnerability to the public.
You might ask why a researcher would want to release the full details of a security hole or vulnerability to the public at all. Security researchers make their living through consulting and selling security products and services. Doing security research costs them time and resources. They need to be compensated for this investment and by announcing to the world that they discovered an important vulnerability it helps market their products and services. Releasing full technical details of a vulnerability by a researcher illustrates the great work that they’re capable of and helps them cover their expenses, make a living and helps fund future research.
Important to Note: You can see the newest announced vulnerabilities by subscribing to email lists like ‘Full Disclosure’. Sometimes vulnerabilities are not shared with a vendor and are simply released to the public as a Zero Day. When this happens you are in a situation where an active Zero Day is ‘in the wild’ (known to hackers) and a fix is not available. Deal with these as you would with any Zero Day vulnerability (see above). Researchers may also not give vendors much time to fix a vulnerability before announcing it to the public. In this case you need to immediately upgrade to the newest version of the affected software as soon as a fix is released to minimize risk to your website.
Where WordPress Vulnerabilities are Disclosed
The most prolific source of WordPress vulnerability disclosure is the “Full Disclosure” mailing list. It’s also the most likely place to find a Zero Day disclosed without vendor notification. If you are a WordPress site admin concerned with security, I would encourage you to subscribe, but be forewarned that the list is noisy and does include vulnerabilities for many other platforms and applications besides WordPress. Use your email filters accordingly.
US-CERT runs the National Cyber Awareness System and has several mailing lists you can choose from. I would encourage you to subscribe to Bulletins at a minimum which includes a weekly vulnerability summary.
You can also subscribe to our WordPress Security Mailing List where we announce serious vulnerabilities.
Exploit-DB is a web based database of vulnerabilities and you can often find newer WordPress vulnerabilities published there.
WPVulnDB.com contains a collection of WordPress core, plugin and theme vulnerabilities from around the Web.
The BugTraq Mailing list hosted by securityfocus.com (Now owned by Symantec) is legendary in the security industry. It has been around since 1993 and is an excellent source for the newest vulnerability disclosures. You can subscribe by emailing bugtraq-subscribe@securityfocus.com.