This site uses cookies in accordance with our Privacy Policy.
3.9: Understanding Social Engineering Attacks
Social engineering is the practice of using non-technical means, usually communication via phone or another means, to attack a target. An example of a social engineering attack is when a hacker calls up a company, pretends they’re from the internal IT department and starts asking an employee for sensitive information that will help them gain access to the network.
Social engineering may not sound effective and what we’re hoping to demonstrate in this article is that it is extremely effective as a method of attack and that companies need to take this form of attack as seriously as any other attack method.
There are two main phases of a social engineering (SE) attack. The first phase is the reconnaissance phase where the SE will gather intelligence on their target. This helps them instill confidence in their target that the SE is who they claim to be and the target will trust the SE. The second phase is the attack phase where the SE will call the target up and start the attack.
Reconnaissance – Gathering Open Source Intelligence (OSINT)
During the reconnaissance phase, the SE will gather as much information on their target as possible. In the social engineering CTF competition at DefCon 22 the teams were given 3 weeks to gather intelligence. The following is a list of some of the tools used by the contestants to gather OSINT:
- Google – Simply Googling the company, searching the employee directory, Googling employee names and digging gradually deeper yields a mountain of information.
- Maltego – Maltego is made by Paterva and is a powerful tool to gather, combine and analyze OSINT on a target. Maltego provides a way to import or add data. It also provides transforms that can gather additional data using electronic methods. It’s an excellent platform to gather and analyze OSINT.
- Whois – Whois will tell you who owns a domain. If a company is being targeted, the administrator for the company domain is frequently listed with their telephone number or a number for the IT department.
- Twitter, Facebook, LinkedIn, FriendFinder and other social sites or sites with public profiles can reveal a wealth of knowledge about an individual or a company. Company employees may reveal details about the company structure, schedule, colleague names and more.
- Google Images – A little known feature of Google images is the ability to drag a profile photo into a Google image search. If you can find a public profile photo for an individual, try dragging it into Google Image search. It may reveal other public profiles that provide even more OSINT.
- PiPl.com – This service can be a little scary. Try searching for your own name with or without your location. Then click on the result that is you. You will be amazed at how much data pipl.com managed to aggregate. This is a neat shortcut for social engineers gathering OSINT.
- Shodan – Shodan is an incredibly powerful network search engine. It goes around indexing what services are listening on network ports and logs their banner. It can provide, for example, a list of Cisco routers listening on a particular port on a company’s IP address range. Note that you need to sign-into Shodan (free registration) to gain access to the more useful filters.
- TinEye – A reverse image search that is also useful to search for profile photos matching an existing photo. It reveals user profiles around the Net.
- Archive.org – Also called WayBackMachine, is one of our favorite tools. It allows you to see previous versions of a website, often going back several years. This can provide previous employee names that are no longer with the company, or intelligence on site upgrades or changes that can be useful OSINT.
- Monster.com, GlassDoor, Indeed and other employment related websites can provide a wealth of information in their job descriptions. You can learn about what hardware and software a company is using, what level of security clearance their employees have and more.
These are just some of the OSINT tools that social engineers use to gather data on a target.
Exploitation – The Social Engineer Attacks!
The kinds of OSINT a social engineer will look for are below with a few quotes illustrating how the information might be used:
- Employee names: “Hi, can I speak to Bob Simmonds?”
- Their colleague names: “Hi Bob, this is Mary from IT. I just got off the phone with Matt Smith.”
- What their colleagues are doing: “Matt is off sick today….”
- Staff desk locations: “…but I’m sure you know that since you guys share a cubicle.”
- New technology rollouts at a company: “I wanted to find out how that new workstation is working out for you.”
- What technology they’re using: “I know Windows 10 isn’t everyone’s favorite, but hopefully the new Office version is helping you?”
At this point you’re convinced you could only be talking to an internal IT employee because they already know so much. You’re probably going to share information freely with this person.
As you an see, spending as much time gathering OSINT on a company before contacting them can make a SE attack far more effective. The techniques that SE’s use when attacking vary. One effective technique we’ve seen is where the SE was calling up a major Fortune 500 company and pretending to be evaluating staff performance. They took an authoritarian role but were also friendly. The employee was incredibly cooperative and ‘helpful’.
Social Engineering is Very Effective
Some of the data below is from the PDF that was released in 2014 by social-engineer.org reporting on DefCon 22’s social engineering capture the flag (CTF) competition. If you ever get a chance to attend one of these events, it is impressive watching a social engineer work their way into a company’s network in real-time. The report is long (29 pages) but contains a wealth of information demonstrating how effective social engineering is. We’ve included some of the data from that report below to illustrate how effective social engineering is.
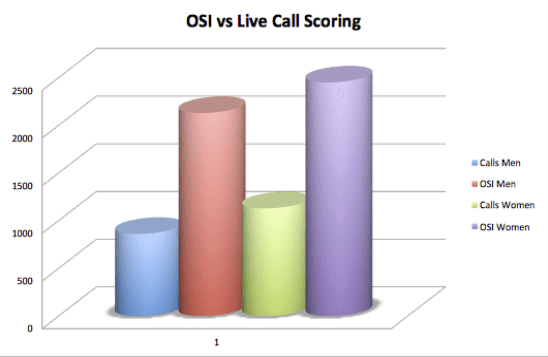
The data seems to indicate that women tend to be more effective at social engineering voice calls than men. At the 2014 DefCon Social Engineering capture the flag competition, women outshone men by a notable margin on calls:
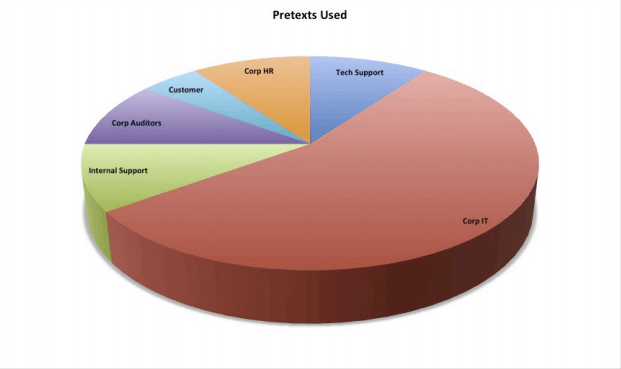
Some of the pretexts (who the SE claims to be) are shown below with the most popular ones indicated in the pie chart:
As you can tell from the chart above, the majority of pretexts are a social engineer claiming to be some form of internal IT support.
So how effective is social engineering? First, lets understand what information the SE’s at DefCon 22 were trying to get from the companies they targeted. Then we’ll look at which companies divulged information and how much.
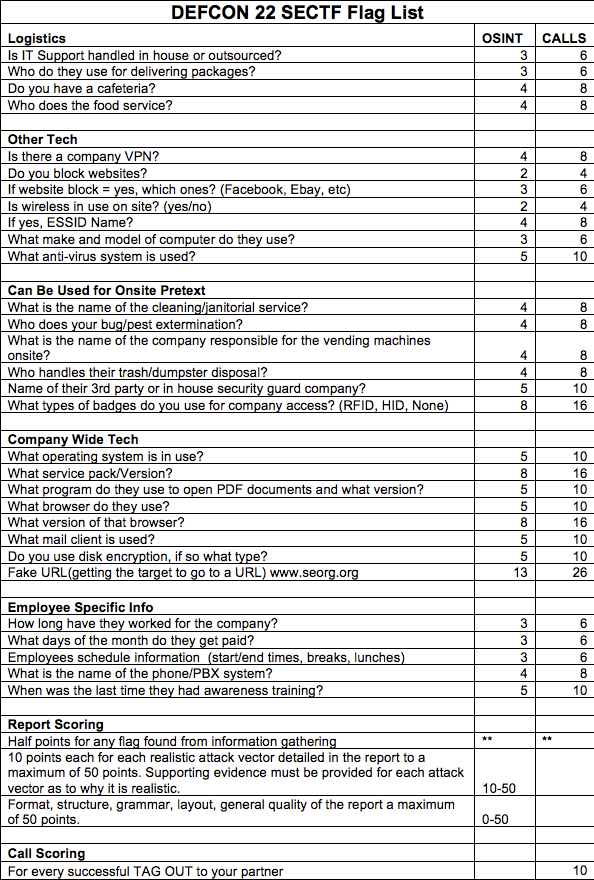
The capture the flag contest at DefCon 22 used a point system where points were allocated for gathering open source intelligence (OSINT) and for gathering information from a live phone call. Here is a table showing the information they were targeting and how many points were allocated for each method of gathering:
A “tag out” above means that the social engineer transferred the target employee to another social engineer.
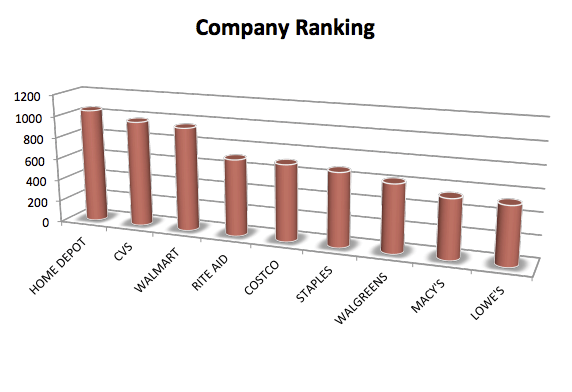
Now that you have an idea of what information was being gathered, lets look at how the major corporations being targeted in DefCon 22’s Social Engineering CTF competition did:
Some major brands were targeted in this competition. A higher score above means that the company gave away more information to the social engineer. This illustrates just how vulnerable companies are to social engineering attacks.
How to Protect Yourself From Social Engineering Attacks
Now that you understand how effective these attacks can be, lets look at a few key ways to protect yourself.
If someone calls you, claims to be someone you trust and appears to already know a lot about their subject, don’t trust them without verifying who they are. Sometimes this can be challenging because it is difficult to say no to a live human being on the phone. The social engineer knows this and may play on your emotions. They may tell you that they’re almost at the end of their shift and they just need to “wrap this up” before they can go home to their kids. Don’t fall for it.
An excellent tactic if someone calls you is to offer to call them back. Don’t accept a direct line. Ask them for their name and their main switchboard number (or front-desk) and an extension. Ask them if there is any other information they can offer that will help you verify who they are. Then hangup and research the number they give you before you call it. Do a google search of the number. You can also try WhitePages reverse phone lookup.
If the number and any other information they give you checks out, instead of immediately calling them back, search for the company’s main number yourself and call them directly. Ask them if they have been trying to contact you. Remember that the best social engineers have dedicated numbers with automated recordings that sound legitimate. So a bit of paranoia helps in this case.
A few more tips:
- Never provide a password over the phone. No company will ever ask you for this and if they do, stop doing business with them.
- Ask yourself “why” the person you’re speaking to called you. If they’re claiming to do some task that involves you disclosing information, refuse and refer them to your superior. Explain that you’re concerned about security. Anyone who objects to this concern should not be trusted.
- Trust but verify. Politely refuse to provide information until you have 100% verification of who you’re talking to. Banks, insurance companies, IT departments and Accounting firms are all very sensitive to security and someone who really needs information from you will give you a way to verify who they are.
Conclusion
Social engineering attacks are very effective because humans (that’s us) are usually the weakest and most exploitable link in a secure network. Between 2012 and 2013 social engineering attacks doubled from 2.4 million phone fraud attacks in 2012 to 2.3 million attacks in the first-half of 2013 – and the rate continues to increase in 2015. It is clearly important to develop policies and procedures in your organization to protect you and your staff from this kind of growing attack.