This site uses cookies in accordance with our Privacy Policy.
1.4: Has my site been hacked? How to Check
Most customers that contact us for help with cleaning a hacked site have discovered their site is hacked because their browser is alerting them when they visit their own site, or their hosting provider took their site offline. This is disastrous because it means that your site has been infected long enough for the hackers to do damage. The damage they did caused a hosting provider to shut off the site or caused Google to detect that the site is hosting malware, SEO spam or a phishing attack.
This is why we encourage all of our customers to invest in security for their sites. You can use Wordfence (our own product) or one of the many alternative products out there, but it’s important that you have a way to be alerted when your files change, malware is detected or other suspicious activity occurs.
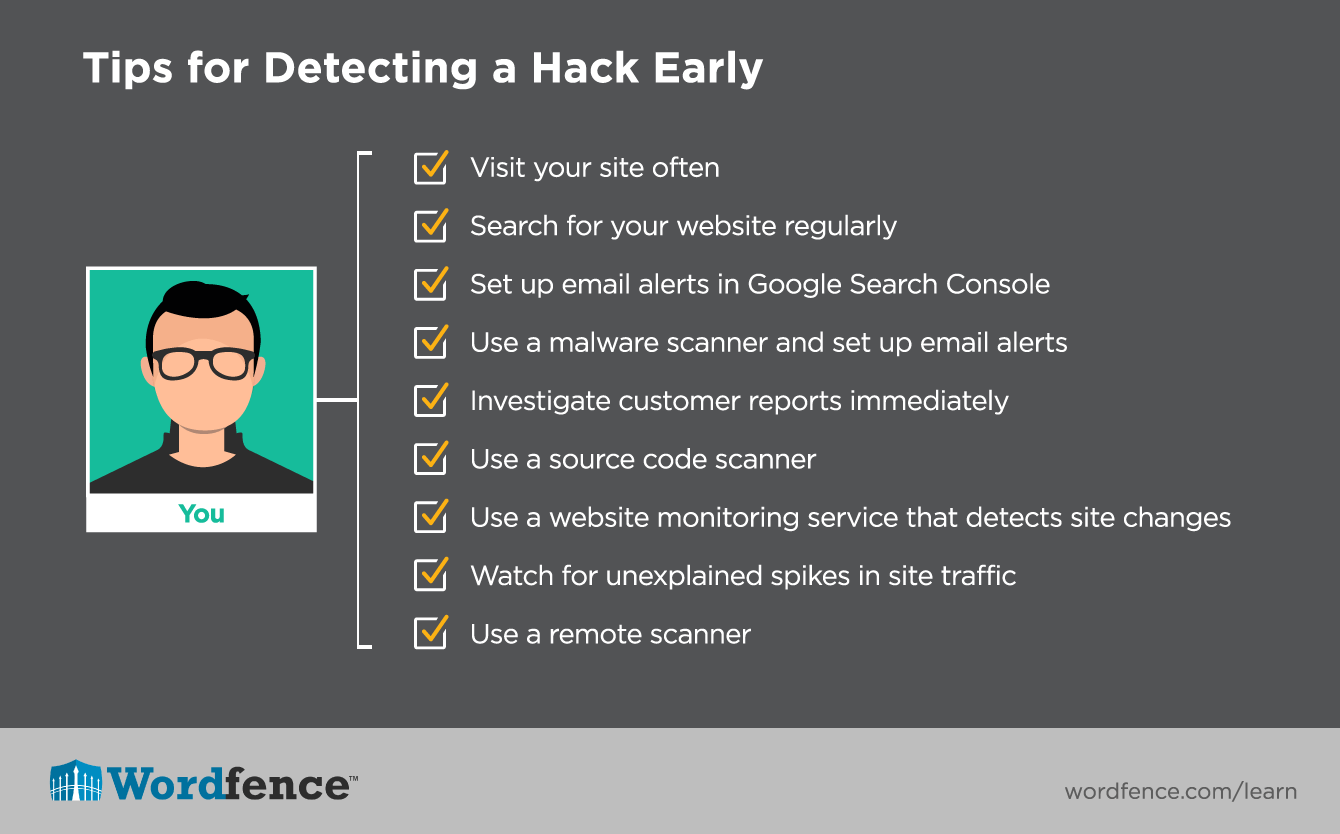
Let’s identify the various ways you can detect or discover that your site has been hacked.
Reactive Ways You May Discover Your Site Has Been Hacked
Even the most alert system administrators aren’t able to monitor their site 100% of the time. The best monitoring tools have a delay between each site check or scan. So you may find that you discover that you have been hacked from an outside source. Let’s review some of the ways you may discover a site you own has been hacked. We are discussing these because they are all sources of data you can use to proactively monitor your site health.
Google Chrome (or another browser) Alerts You To The Hack
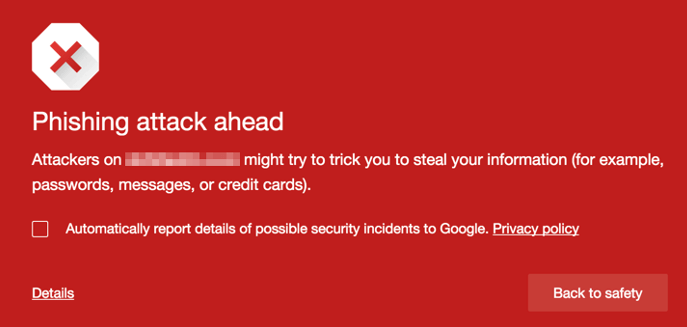
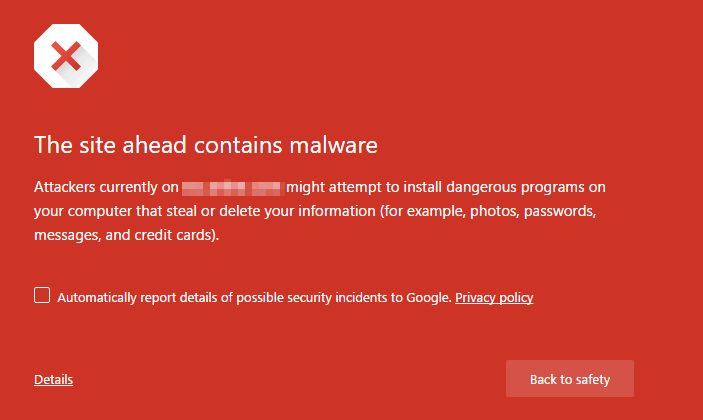
If one of your visitors (or you) see one of the following warnings in Chrome, your site has likely been hacked and infected with malware.
The above warning indicates that your site has been used in phishing campaigns. A victim is emailed a URL that contains a link to your website. A hacker is using your website to host malware that tricks the victim into taking some action that the hacker wants when they visit your site.
The above warning indicates that your site is hosting malware. A hacker has gained access to your site, installed malware on the site and is infecting machines belonging to your site visitors.
Your Hosting Provider Takes Your Site Offline Because it is Hacked
In this case your host may have received reports from site visitors that your site has been hacked, their own automated security tools may have alerted them or they may have received alerts from automated systems outside their own company. In either case, they will usually immediately take your site offline.
Note that some hosting companies have a policy of immediately formatting a server or hosting account that is infected. They do this to prevent the infection spreading to other customers even after the site is offline. This is another reason why it is important to have backups or your website.
Your host will usually notify you via email that your site has been taken offline.
Google Search Results Flag Your Site as Hacked or Harmful
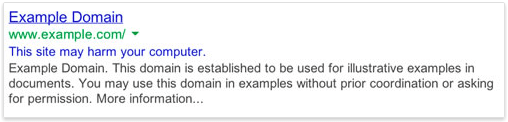
If you, or one of your site visitors notice the following in the search results that include your site, it has likely been hacked.
Google often simply removes hacked sites from search results. But in some cases the site may still be listed, but will be flagged with a message saying that “This site may be hacked” or “This site may harm your computer”. When you click through to the website using Chrome, the browser will provide one of the warnings above. User’s using a different browser may receive no warning, which is why the warning is also included in the search results.
“This site may be hacked” means that Google detected something out of the ordinary on your site, such as unusual changes to existing pages or adding new ones with SEO spam or redirects. These sites do not typically display the standard Google malware warning page.
“This site may harm your computer” means that Google has detected malware on the site and if you visit the site, you do so at your own risk and you will see the Google malware warning if you click through which is meant to alert you that the site is currently unsafe.
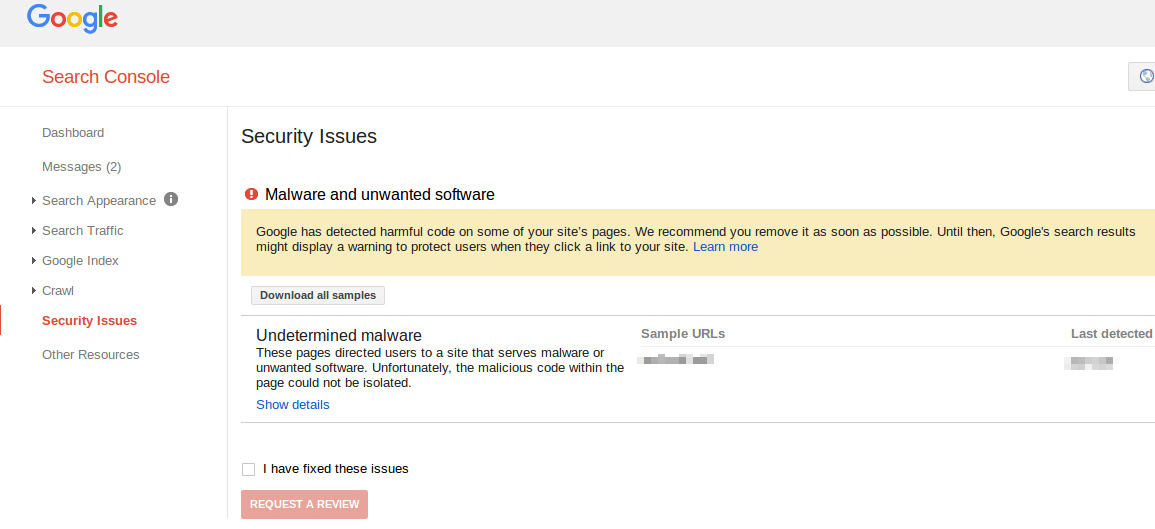
Google’s Search Console Alerts you to Malware on Your Site
Google “Search Console” used to be called “Google Webmaster Tools”. If you run a website you should immediately set up Google Search Console if you have not already. It will alert you to problems Google may encounter when indexing your site and will provide you with stats showing your site visits via search.
Search Console can email you alerts about your site including if it detects that your site is infected with malware. Go to “Search Console Preferences” and enable email alerts there. This will notify you immediately when Google detects malware on your site and you may be able to fix the problem before they start displaying warnings.
If you are signed in to Search Console, visit the “Security Issues” panel and if you see a warning similar to the one below, it indicates that your site is infected.
Your Malware Scanner Alerts you to an Infection or Hack
If you’re using Wordfence or another malware scanner, you may receive an alert that you have been infected. This is the preferred method of discovering a hack because it usually has the shortest time between getting infected and discovery.
You will usually receive this alert via email, so it is important to keep a close eye on alerts from your websites. Don’t develop a blind spot because you receive too many alerts. You can adjust which alerts you are emailed in your monitoring software.
A Customer Contacts You About Your Site Being Hacked
Your site visitors view your site more often than you do. If you have several thousand visits a day and your site is visibly hacked, it is likely that a customer may contact you before you are alerted or Google detects the hack. Immediately let your customer know that you are taking action. You should also consider taking your site offline.
Proactive Ways To Detect A Hack Before Google or Your Customers Notice
Use a Source Code Scanner
Infections are often well hidden and not visible to outside visitors. You can use a source code malware scanner like Wordfence to detect if your site is hacked. The scanner will systematically inspect all of your PHP and other source code for malware patterns and alert you to the presence of any malware.
Source code scanners use several mechanisms to detect a hack. The primary method of detection is looking for known malware signatures or patterns that match malware code. Newer infections are not detected using this method, so another method that more sophisticated scanners use is to compare your source code with a known good version of the same code. For example, Wordfence will compare your WordPress core, theme and plugin source code against a known good version of the same files and alert you to any changes. This method catches newer infections where a detection signature may not yet exist. Doing a manual scan with a source code scanner is a highly effective way to detect and remove a hack.
Use a Monitoring Service That Includes Site Changes
We use a monitoring service on our websites that alerts us to downtime. It includes a service that tells us if a page has changed more than a certain percentage. Many of our pages don’t change at all or may only have a minor change like a date or copyright year. We monitor these pages and are alerted if more than a very small percentage of the page changes.
WebsitePulse provides a service that includes content monitoring as does Pingdom. In general these are paid services, but they can be an effective way to get alerted if you have been hacked within minutes.
Most good services include the ability to monitor from multiple locations. We recommend you enable this because a hacked site does not always serve malware. It frequently targets only certain users based on location, time of day, traffic source or other parameters. Monitoring multiple pages from multiple locations can improve detection.
Monitor Site Traffic and Watch For Spikes
If your site traffic spikes dramatically you should immediately perform a source code scan and verify that you have not been hacked. Hacked sites frequently see a dramatic spike in traffic.
One cause of a traffic spike may be that your site is being included in a spamvertizing campaign. A hacker will send out spam and include a link to your site which either hosts malware or redirects traffic to another malicious site. Hackers do this to avoid spam detection. Your site is a “clean” domain and is not known to host malware when it is first infected. By including a link to your site instead of their own known malware hosting site, hackers avoid spam detection. This results in a dramatic spike in your site traffic.
In addition to javascript based traffic monitoring tools like Google Analytics, you should also monitor your site traffic for “bot” traffic which is not usually logged by Google Analytics. You can use Wordfence’s live traffic feature or another server based traffic monitoring tool. Your hosting provider may include charts that show server traffic or bandwidth usage.
Visit your Site Regularly
If you notice any changes or any strange text injected into your pages, you should immediately perform a scan on your site to check for an infection. PHP errors are also a common sign that you may be infected and these often appear at the very top of your page, often above the content.
As a routine, simply visit a few pages on your own site as a sanity check at least once a day.
Use a Remote Scanner
Remote scanners look at the “rendered” version of your website. That means they look at the HTML that your site produces instead of the site source code. This may detect a hack if the hacker has chosen to include malware in the HTML they are serving, to the current site visitor and on the page that is being viewed.
Hackers will frequently include code that only displays malware to certain visitors at certain times and matching certain criteria. For this reason it is possible that a remote scanner will miss an infection because the malware is simply not active at that time or the infected code is not displaying the malware to the scanner when the scanner checks the site. However, remote malware scanners can catch a variety of unsophisticated infections and it is worth using them as an additional tool.
Here are a few file viewing tools and remote scanners that may help you detect an infection:
- VirusTotal has a URL scanning feature that checks your site response against a huge number of virus databases and will let you know if you triggered any of them.
- SpamHaus maintains various lists. You can use this page to check your site hostname and IP address against the various SpamHaus lists. If your site does appear, it has been flagged for being included in spam emails or for hosting malware. Both indicate your site has been hacked.
- You can use this link to check the status of your site on the Google Safe Browsing list. Simply replace ‘wordfence.com’ at the end of the URL with your site’s own hostname. Don’t forget the ‘www.’ if your site is prefixed with that. The page will tell you if your site is flagged by google for phishing or hosting malware. It will also tell you your site history and what happened when Google last scanned your site.
- urlquery.net does a very useful analysis of your site response including checking if your site response triggered the Snort and Suricata intrusion detection systems, showing files captured, blacklists your site is on, and breaking down the response into HTTP transactions and what they were.
- aw-snap.info includes a file viewing tool that highlights script tags, iframes and other detectable code injections and lets you view your HTTP headers which can help you see malicious code and server side redirects in your site response. It will also allow you to switch between different types of user agents and search bots which will often uncover hidden injections that only display for certain user agents and or search bots.
Conclusion
This article has given you several tools to proactively monitor your site for a hack and we have also discussed ways you may reactively discover that you have been hacked. We encourage you to also use the ‘reactive’ section as part of your toolkit. For example, regularly sign into Google’s Search Console to check your site status, look at your own site in the search results to ensure that everything is in order and visit your own site frequently in Google Chrome where you will notice browser warnings.
Maintaining a healthy and hack-free website does not need to be hard work, but developing a healthy routine of checks will help you catch problems early and fix them before any damage occurs.